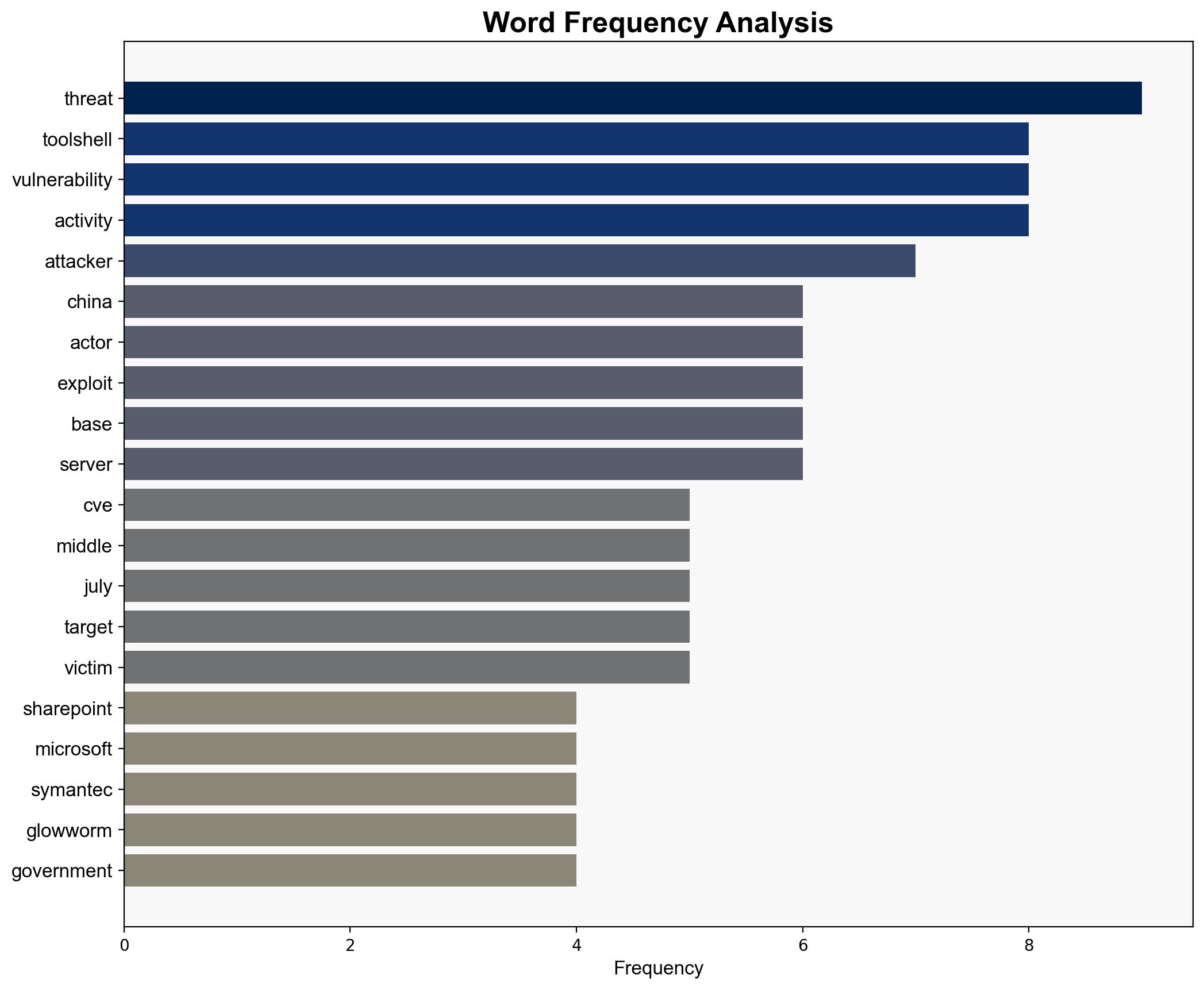
China-linked hackers exploit patched ToolShell flaw to breach Middle East telecom – Securityaffairs.com
Published on: 2025-10-24
Intelligence Report: China-linked hackers exploit patched ToolShell flaw to breach Middle East telecom – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that China-linked threat actors are conducting a coordinated cyber-espionage campaign targeting Middle Eastern telecommunications through the exploitation of the ToolShell vulnerability. This campaign is likely driven by strategic interests in gathering intelligence and maintaining long-term access to critical infrastructure. Confidence level: High. Recommended action: Enhance cybersecurity measures and international cooperation to monitor and mitigate further intrusions.
2. Competing Hypotheses
1. **Hypothesis A**: China-linked threat actors are exploiting the ToolShell vulnerability as part of a broader espionage campaign targeting telecommunications in the Middle East to gather intelligence and maintain covert access.
2. **Hypothesis B**: The exploitation of the ToolShell vulnerability by China-linked actors is opportunistic, aiming to disrupt telecommunications services in the Middle East for economic or political leverage rather than long-term espionage.
Using the Analysis of Competing Hypotheses (ACH) 2.0, Hypothesis A is better supported due to the pattern of targeting government and financial institutions, suggesting an intelligence-gathering motive. The use of sophisticated tools and persistence techniques aligns with long-term espionage rather than short-term disruption.
3. Key Assumptions and Red Flags
– **Assumptions**: The attribution to China-linked actors is based on known tactics, techniques, and procedures (TTPs) and previous activity patterns. It assumes that the identified tools and methods are exclusively used by these actors.
– **Red Flags**: The overlap in activity with other threat actors like Glowworm could indicate misattribution or collaboration. The rapid exploitation post-patch release suggests pre-existing knowledge or insider information.
– **Blind Spots**: Limited visibility into the full scope of affected entities and potential undisclosed vulnerabilities being exploited.
4. Implications and Strategic Risks
The exploitation of the ToolShell flaw poses significant risks to regional stability and cybersecurity. The potential for cascading threats includes compromised communications infrastructure leading to intelligence leaks and economic disruptions. Geopolitically, this could escalate tensions between China and affected nations, prompting retaliatory measures or increased cybersecurity alliances.
5. Recommendations and Outlook
- Enhance network monitoring and incident response capabilities in telecommunications sectors.
- Foster international collaboration for threat intelligence sharing and coordinated defense strategies.
- Scenario Projections:
- Best Case: Strengthened defenses prevent further intrusions, and diplomatic engagement reduces tensions.
- Worst Case: Continued exploitation leads to significant data breaches and geopolitical conflict.
- Most Likely: Ongoing cyber-espionage with intermittent disruptions, prompting gradual improvements in cybersecurity posture.
6. Key Individuals and Entities
– Broadcom Symantec Threat Hunter Team (reporting entity)
– Microsoft (vulnerability disclosure)
– China-linked threat actors (attributed group)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus