Chinese and Iranian Hackers Exploit React2Shell Vulnerability, Targeting Over 50 Organizations, Google Reports
Published on: 2025-12-15
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: China Iran are having a field day with React2Shell Google warns
1. BLUF (Bottom Line Up Front)
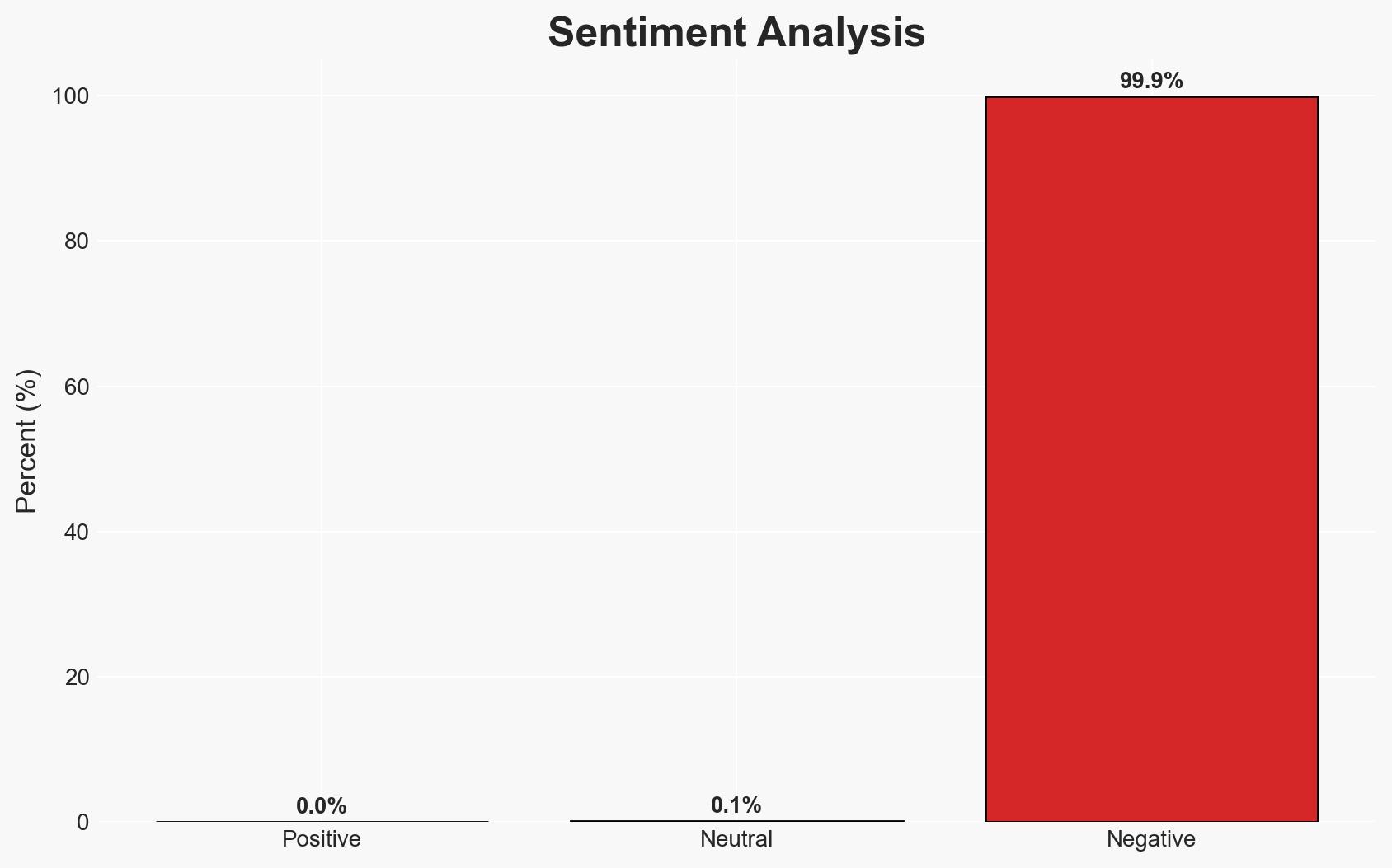
The exploitation of the React2Shell vulnerability (CVE-2025-55182) by Chinese and Iranian actors, alongside financially motivated criminals, poses a significant cyber threat to multiple sectors globally. The most likely hypothesis is that state-sponsored espionage groups are leveraging this flaw for strategic intelligence gathering and infrastructure disruption. The overall confidence level in this assessment is moderate due to incomplete details on Iranian actors’ activities and potential deception indicators.
2. Competing Hypotheses
- Hypothesis A: State-sponsored actors from China and Iran are primarily exploiting React2Shell for intelligence and strategic disruption. Evidence includes the rapid exploitation by known Chinese groups and the targeting of cloud infrastructure, but details on Iranian activities remain sparse.
- Hypothesis B: The primary motivation behind exploiting React2Shell is financial gain through cryptocurrency mining and other cybercriminal activities. This is supported by the deployment of XMRig miners and discussions in underground forums, though the involvement of state actors suggests a broader strategic intent.
- Assessment: Hypothesis A is currently better supported due to the involvement of multiple state-sponsored groups and the strategic targeting of cloud infrastructure. Indicators such as the deployment of sophisticated backdoors and tunneling tools could shift this judgment if more evidence of financial motivations emerges.
3. Key Assumptions and Red Flags
- Assumptions: State-sponsored groups have the capability and intent to exploit React2Shell for strategic purposes; the vulnerability remains unpatched in critical systems; financial motivations are secondary for state actors.
- Information Gaps: Specific activities and objectives of the Iran-linked actors; full scope of affected sectors and geographic regions; potential undisclosed vulnerabilities being exploited.
- Bias & Deception Risks: Potential bias in attributing activities to state actors without conclusive evidence; manipulation of threat intelligence by adversaries to mislead attribution.
4. Implications and Strategic Risks
The exploitation of React2Shell could lead to increased geopolitical tensions and a heightened cyber threat landscape. The involvement of state-sponsored actors suggests potential for strategic disruption beyond immediate financial gains.
- Political / Geopolitical: Escalation in cyber operations could strain international relations, particularly involving China and Iran.
- Security / Counter-Terrorism: Increased risk of cyber attacks on critical infrastructure, necessitating enhanced defensive measures.
- Cyber / Information Space: Potential for widespread dissemination of exploit tools and techniques, increasing the threat to unpatched systems.
- Economic / Social: Disruption of services and potential financial losses for affected organizations, impacting economic stability.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urgently patch vulnerable systems, enhance monitoring of network traffic, and share threat intelligence across sectors.
- Medium-Term Posture (1–12 months): Develop resilience measures, strengthen international cyber cooperation, and invest in cybersecurity capabilities.
- Scenario Outlook:
- Best: Rapid patching and international cooperation mitigate the threat, reducing impact.
- Worst: Unpatched systems lead to significant disruptions and geopolitical tensions.
- Most-Likely: Continued exploitation with moderate disruptions, prompting increased cybersecurity measures.
6. Key Individuals and Entities
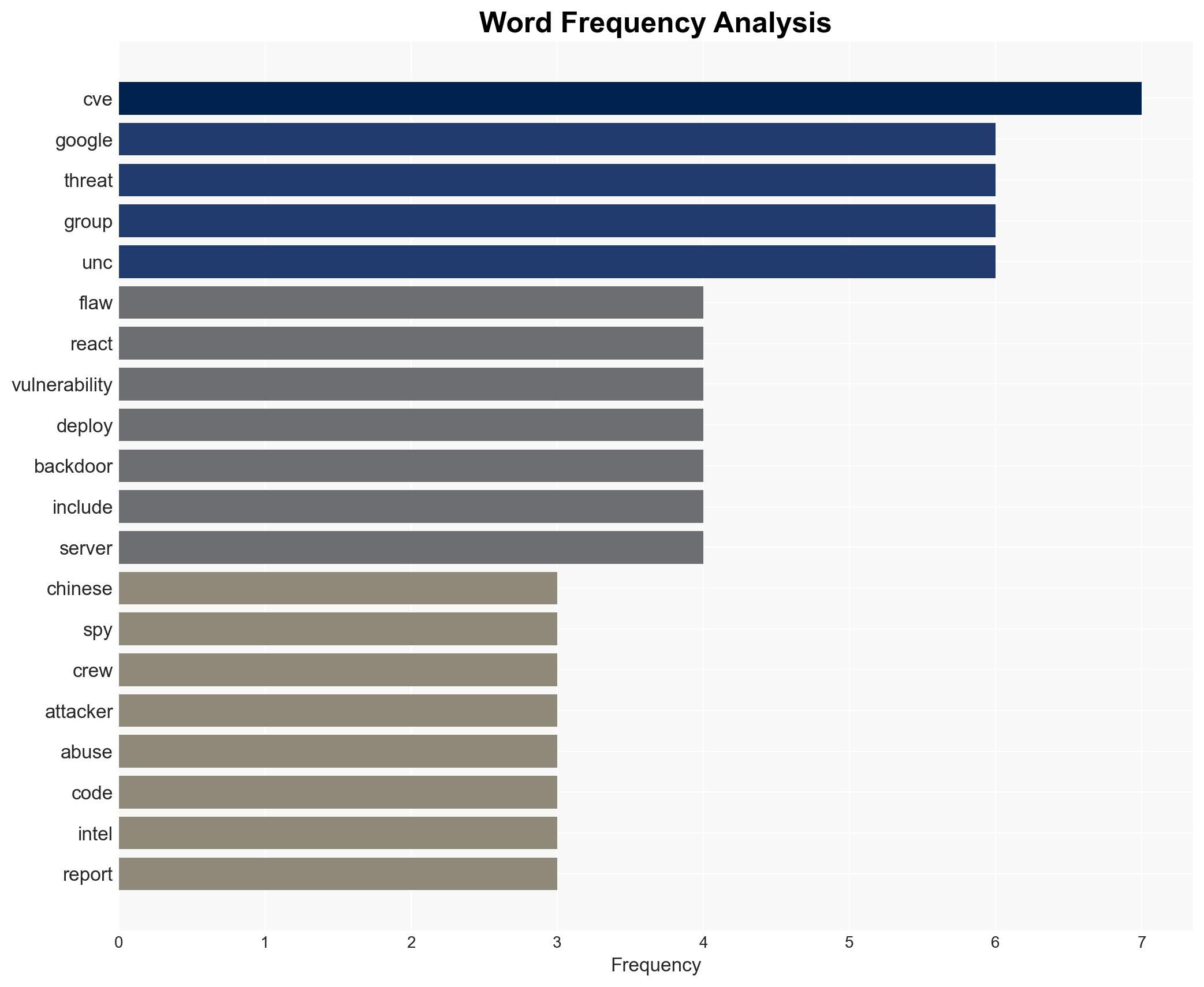
- Earth Lamia, Jackpot Panda, UNC6600, UNC6586, UNC6588, UNC6603, UNC6595
- Not clearly identifiable from open sources in this snippet for Iran-linked actors.
7. Thematic Tags
cybersecurity, cyber-espionage, state-sponsored attacks, vulnerability exploitation, international relations, threat intelligence, cloud infrastructure
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Forecast futures under uncertainty via probabilistic logic.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us