Chinese E-Cigarettes Linked to Espionage and Criminal Financing, Warn Senate Republicans
Published on: 2026-02-05
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Chinese smart vapes exposed as Trojan horses for CCP espionage and cartel cash
1. BLUF (Bottom Line Up Front)
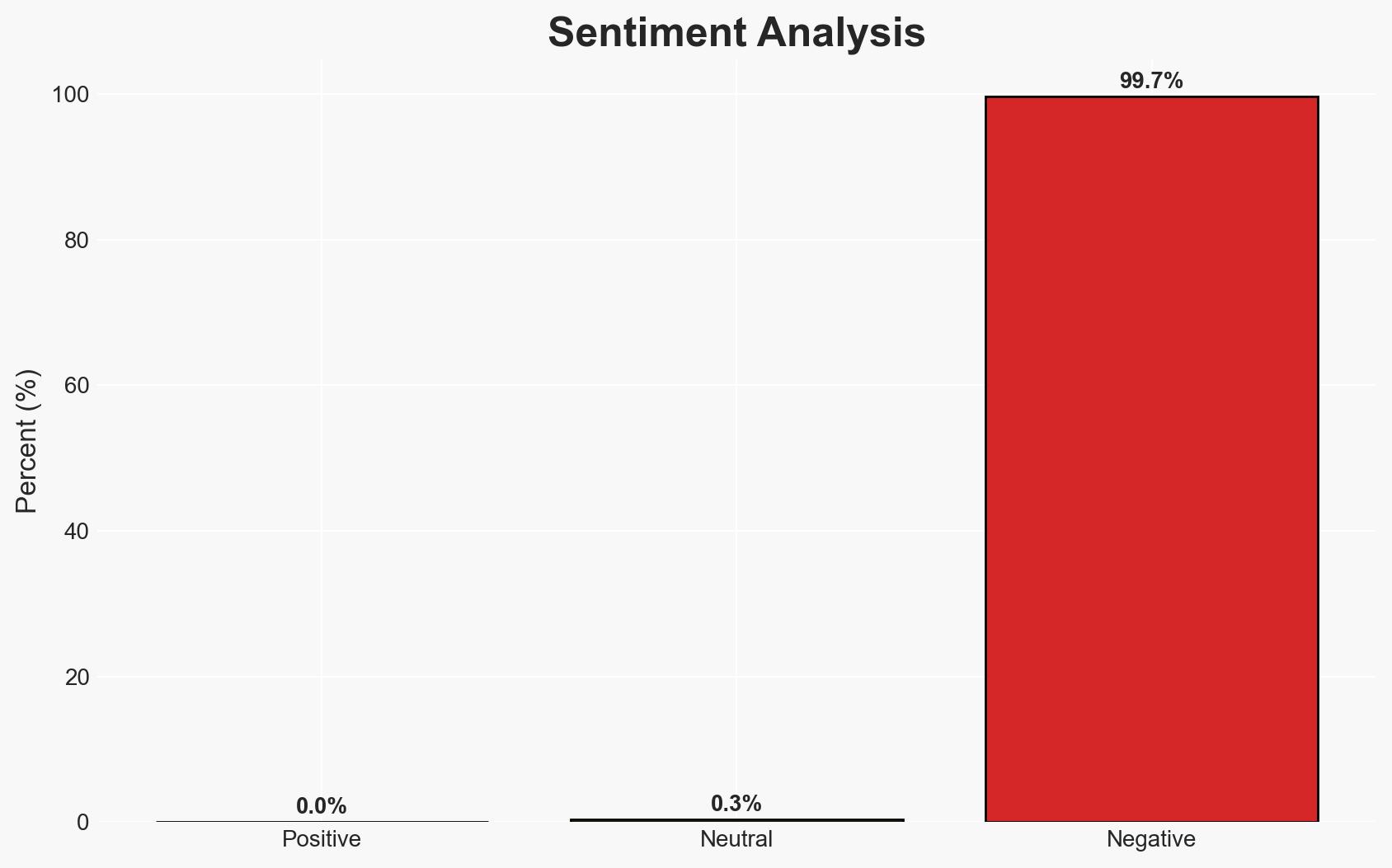
The infiltration of Chinese-made smart vapes into the U.S. market represents a significant national security threat, potentially enabling Chinese espionage and financial support for military ambitions, while laundering cartel profits. This affects U.S. citizens, including military personnel, and poses a complex challenge requiring an aggressive enforcement strategy. Overall confidence in this assessment is moderate due to existing information gaps and potential biases in reporting.
2. Competing Hypotheses
- Hypothesis A: Chinese smart vapes are deliberately designed as espionage tools by the CCP to harvest data and support military funding. This is supported by the interconnectedness of Chinese industry and state intelligence services, and the devices’ technical capabilities. However, the extent of CCP’s direct involvement remains uncertain.
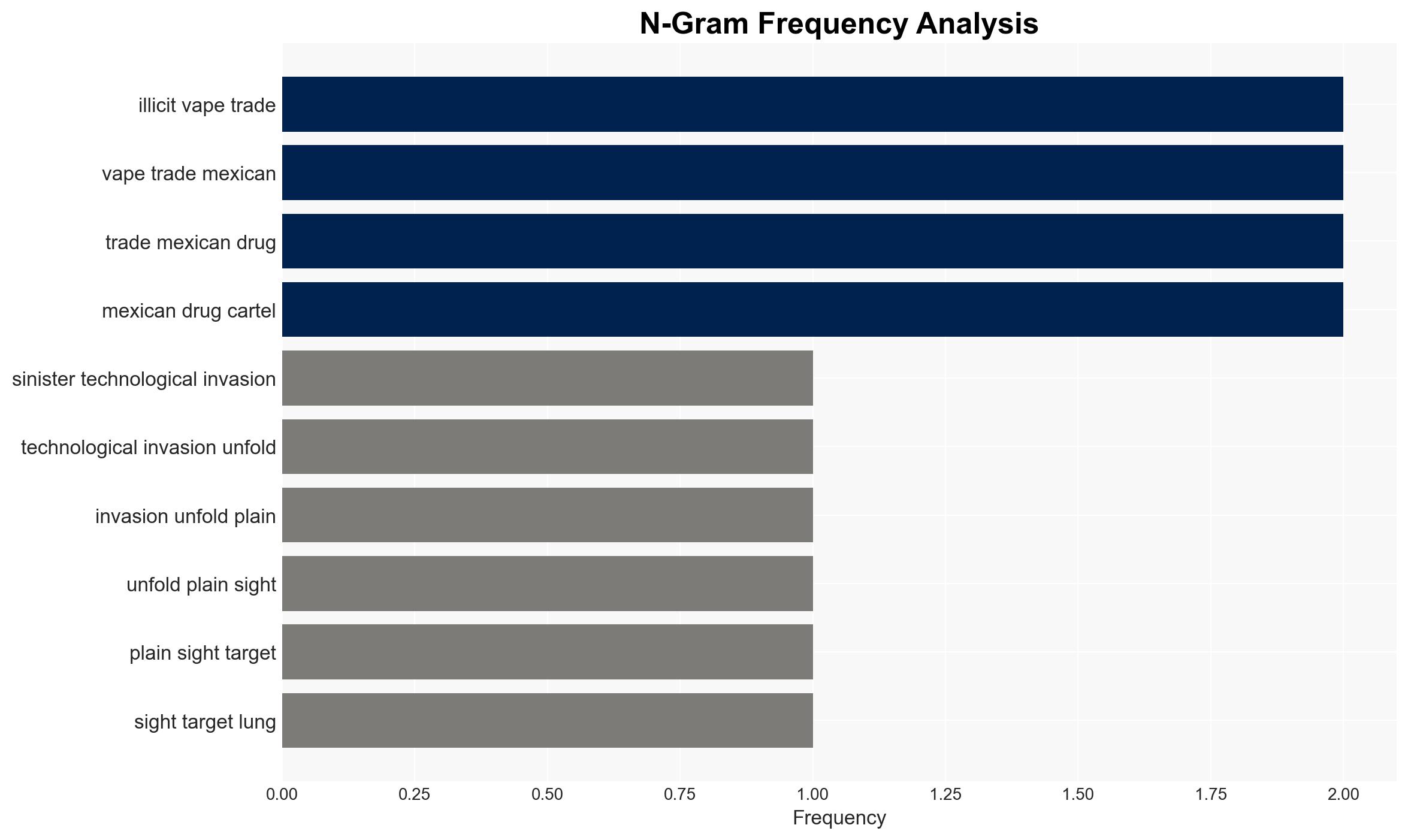
- Hypothesis B: The primary motive behind the distribution of these vapes is economic, driven by profit from illicit trade, with espionage being a secondary or incidental capability. This hypothesis is supported by the established link to cartel money laundering activities but lacks direct evidence of CCP strategic intent.
- Assessment: Hypothesis A is currently better supported due to the strategic alignment of the vapes’ capabilities with known CCP objectives. Indicators that could shift this judgment include concrete evidence of CCP directives or a lack of further technological exploitation evidence.
3. Key Assumptions and Red Flags
- Assumptions: The CCP has the capability and intent to exploit consumer electronics for espionage; Mexican cartels are actively involved in laundering funds through vape sales; U.S. military personnel are targeted users.
- Information Gaps: Direct evidence of CCP directives regarding the vapes; detailed technical analysis of the devices’ capabilities; comprehensive data on the scale of distribution and usage.
- Bias & Deception Risks: Potential bias from political sources emphasizing national security threats; risk of overestimating technical capabilities without independent verification; possible deception by involved parties to obscure true intentions.
4. Implications and Strategic Risks
This development could exacerbate U.S.-China tensions, influence public perception of Chinese technology, and necessitate enhanced cybersecurity measures. It may also impact U.S. economic interests and social trust in consumer electronics.
- Political / Geopolitical: Potential for increased diplomatic friction and calls for trade restrictions or sanctions against China.
- Security / Counter-Terrorism: Heightened threat environment requiring vigilance against espionage and illicit financial flows.
- Cyber / Information Space: Increased focus on securing personal devices and mitigating malware threats.
- Economic / Social: Possible consumer backlash against Chinese products; impact on public health due to vaping concerns.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Implement targeted import controls on suspect devices; enhance public awareness campaigns; initiate technical audits of devices.
- Medium-Term Posture (1–12 months): Develop international partnerships to address cross-border cyber threats; invest in domestic technology alternatives; strengthen regulatory frameworks.
- Scenario Outlook: Best: Effective mitigation and international cooperation reduce threat. Worst: Escalation of U.S.-China tensions and widespread device exploitation. Most-Likely: Ongoing challenges with incremental improvements in security posture.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
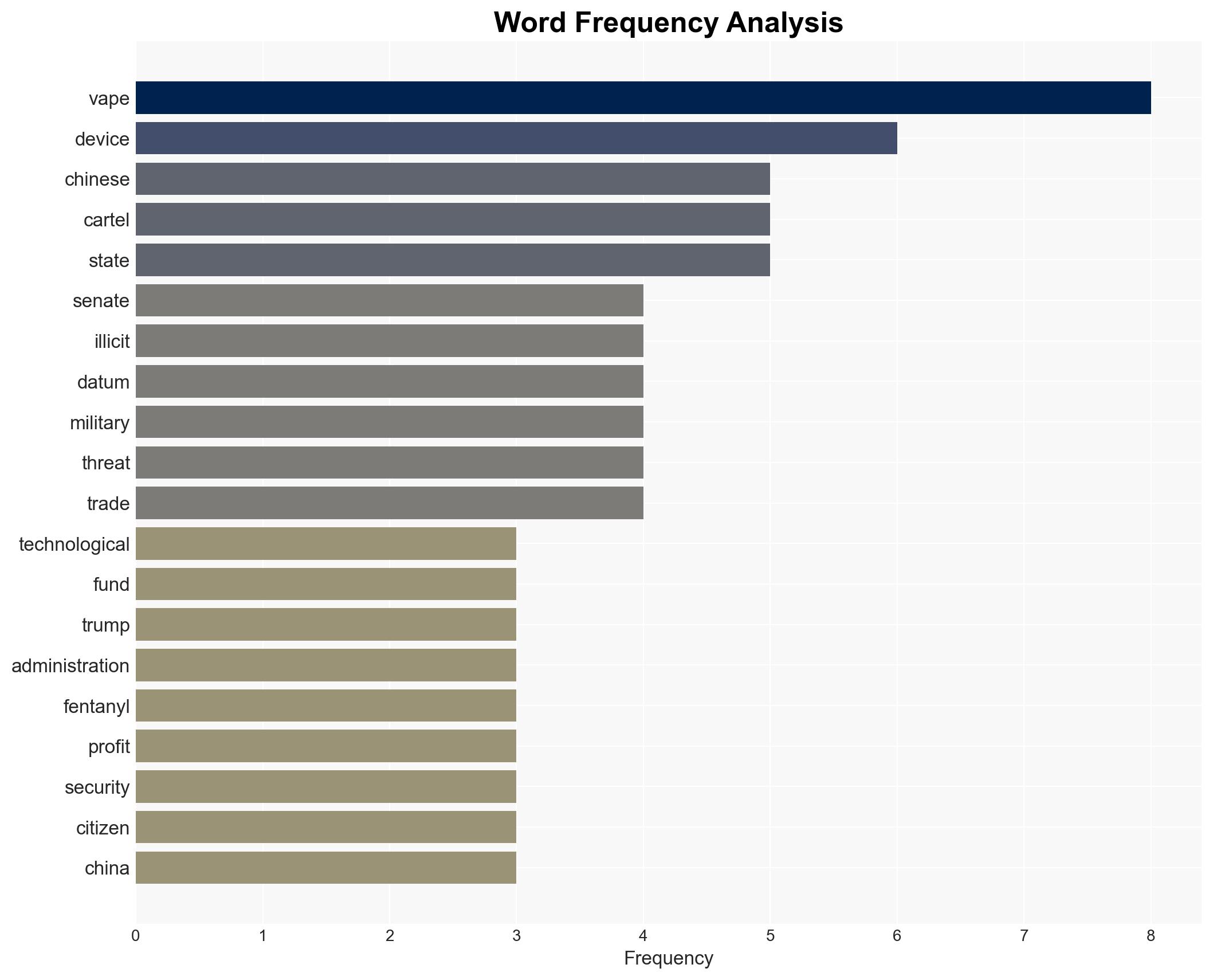
cybersecurity, national security, cyber-espionage, trade-based money laundering, U.S.-China relations, cartel operations, consumer electronics security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Cross-Impact Simulation: Simulate cascading interdependencies and system risks.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us