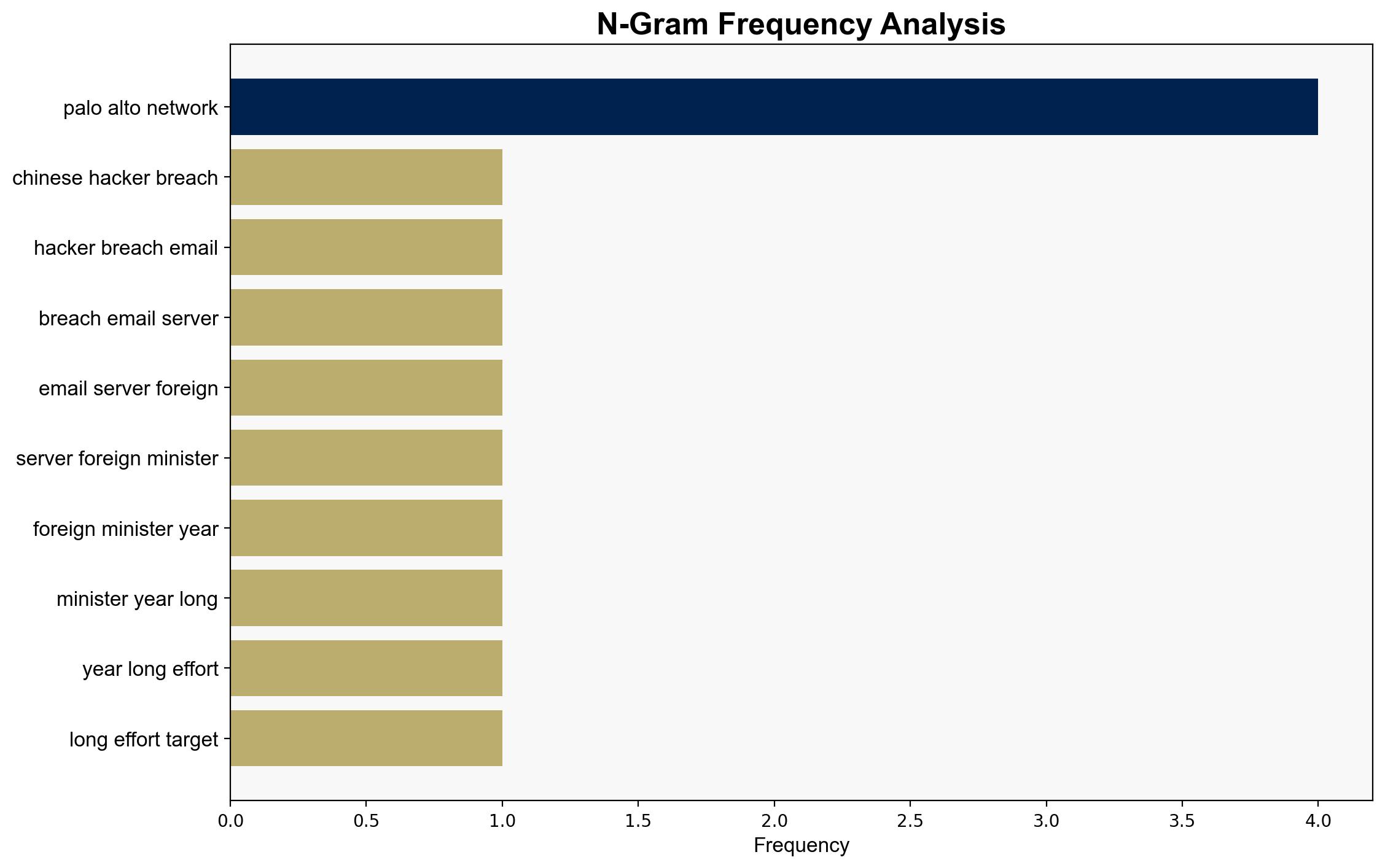
Chinese Hackers Breached Foreign Ministers Email Servers – Insurance Journal
Published on: 2025-09-30
Intelligence Report: Chinese Hackers Breached Foreign Ministers Email Servers – Insurance Journal
1. BLUF (Bottom Line Up Front)
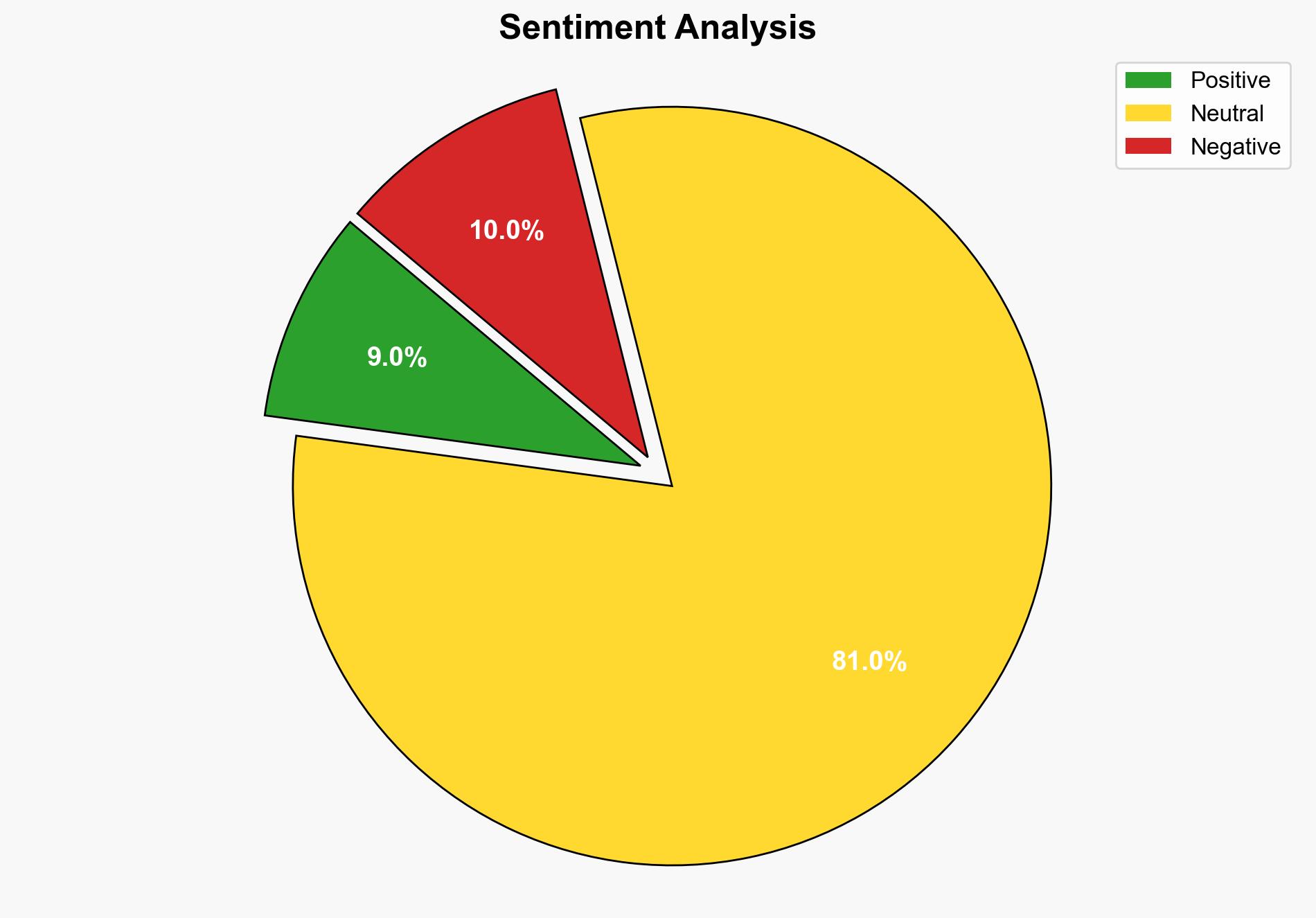
The most supported hypothesis is that the cyber breach was a state-sponsored espionage operation aligned with China’s geopolitical interests. This assessment is based on the targeted nature of the attack, the specific keywords searched, and the timing with geopolitical events. Confidence level: Moderate. Recommended action: Enhance cybersecurity measures across diplomatic channels and increase intelligence sharing among affected nations.
2. Competing Hypotheses
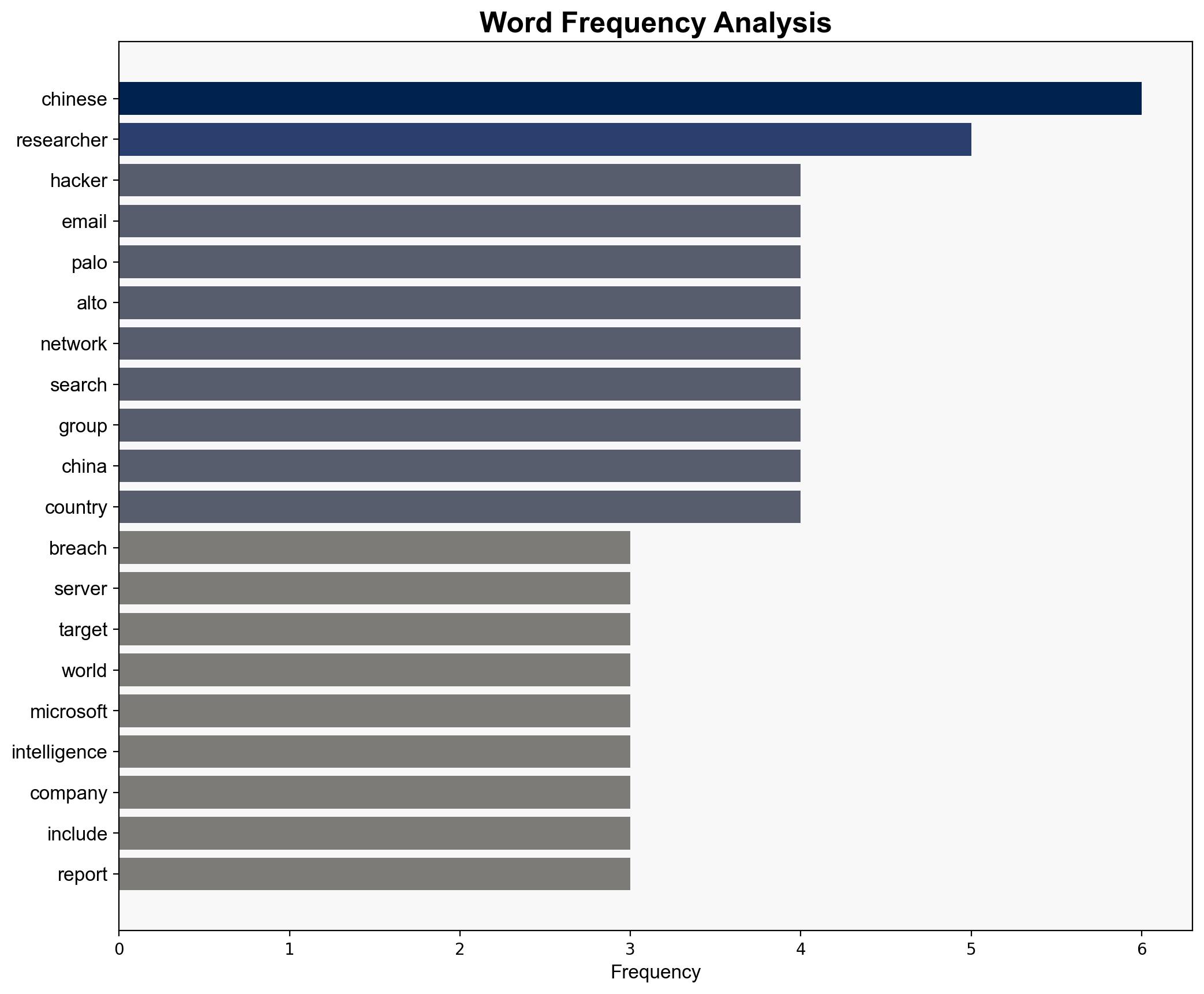
1. **State-Sponsored Espionage by China**: The breach was conducted by a Chinese state-sponsored group, Phantom Taurus, aiming to gather intelligence on diplomatic communications relevant to China’s geopolitical strategies, particularly in relation to the China-Arab Summit and other significant events.
2. **Independent Cybercriminal Group**: The breach was carried out by an independent cybercriminal group, possibly with indirect ties to Chinese interests, seeking to sell sensitive information to the highest bidder or leverage it for financial gain.
3. Key Assumptions and Red Flags
– **Assumptions**: The assumption that the timing and keyword targeting directly indicate state sponsorship. The belief that the technical sophistication of the attack implies state-level resources.
– **Red Flags**: Lack of direct evidence linking the breach to the Chinese government. The potential for misattribution due to the complexity of tracing cyberattacks.
– **Blind Spots**: The possibility of other state actors using Chinese proxies to mask their involvement.
4. Implications and Strategic Risks
The breach highlights vulnerabilities in diplomatic communication systems, posing risks to national security and international relations. If state-sponsored, it could escalate tensions between China and affected countries, potentially leading to retaliatory cyber operations or diplomatic fallout. The breach also underscores the need for robust cybersecurity frameworks to protect sensitive information.
5. Recommendations and Outlook
- Enhance cybersecurity protocols and conduct regular audits of email servers, particularly those handling sensitive diplomatic communications.
- Foster international cooperation for intelligence sharing and joint cybersecurity initiatives to preempt similar threats.
- Scenario Projections:
- Best Case: Strengthened international cybersecurity collaboration prevents future breaches.
- Worst Case: Escalation of cyber conflicts leading to broader geopolitical tensions.
- Most Likely: Continued cyber espionage activities with periodic diplomatic protests.
6. Key Individuals and Entities
– Xi Jinping
– Peng Liyuan
– Lior Rochberger
– Liu Pengyu
– Assaf Dahan
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus