Chinese Hackers Exploit Western Telecom Surveillance Laws to Access Sensitive Communications of Officials
Published on: 2026-02-02
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Chinese hackers weaponized Western spy laws against them in a massive telecom breach
1. BLUF (Bottom Line Up Front)
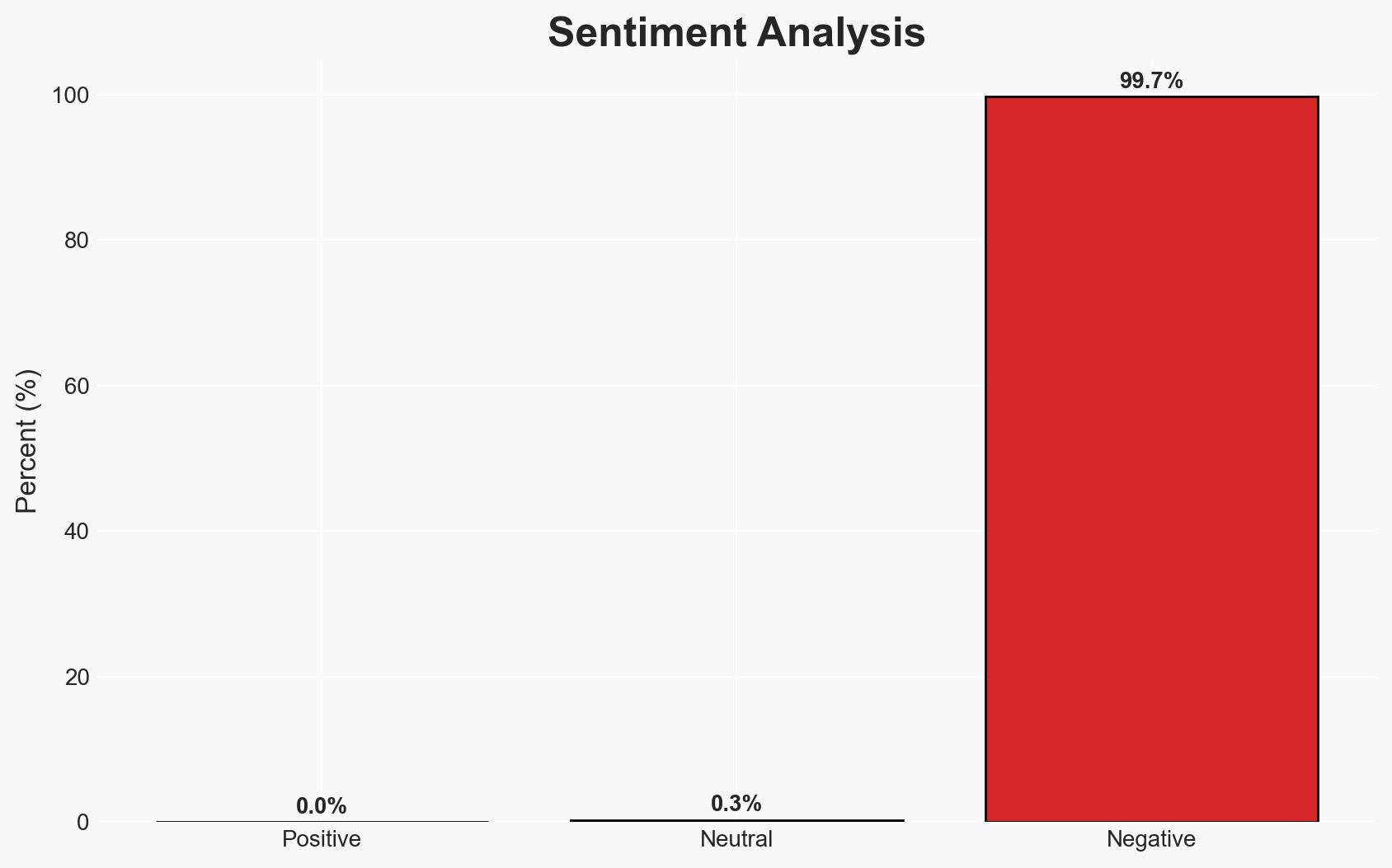
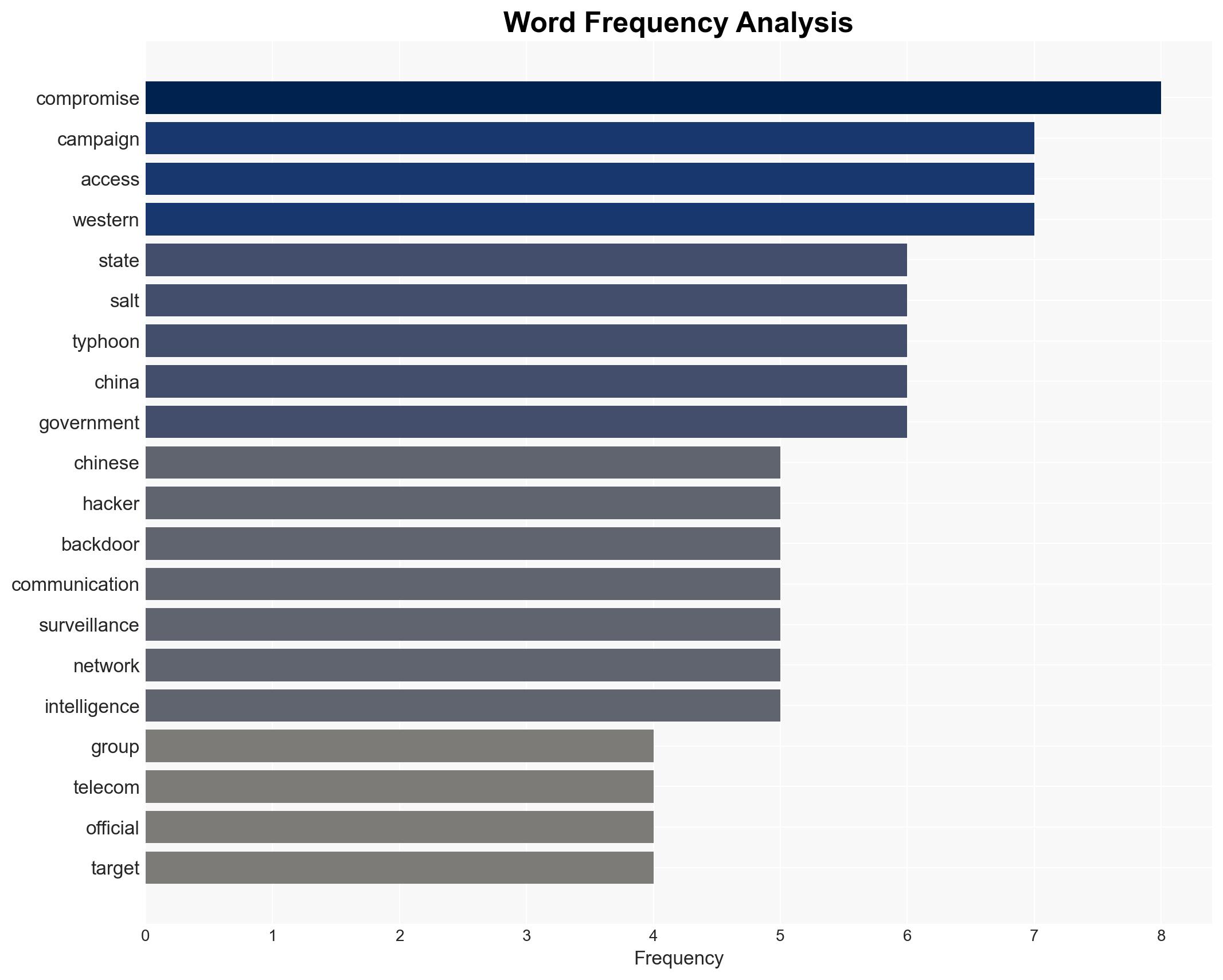
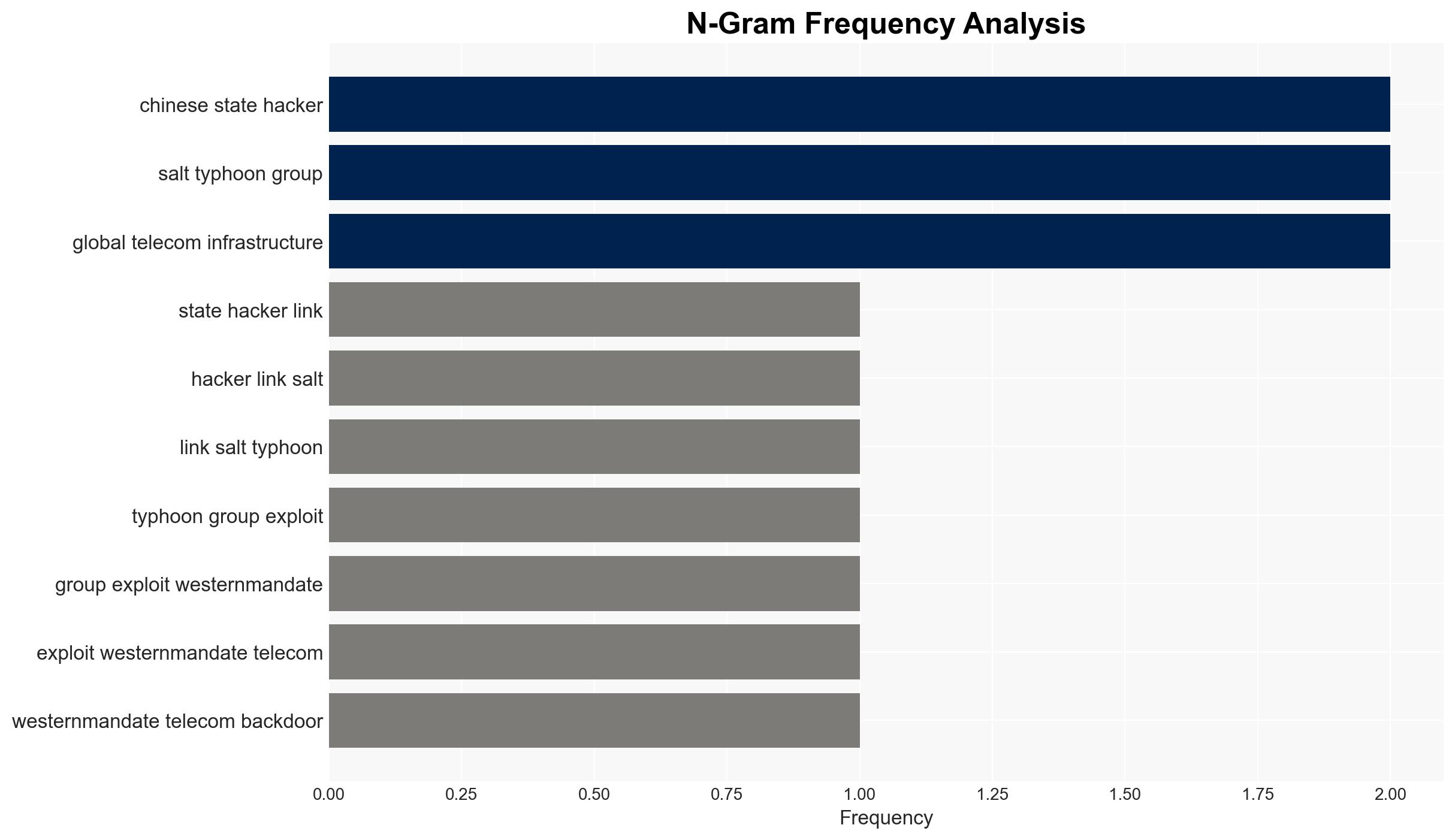
Chinese state-affiliated hackers, identified as the Salt Typhoon group, exploited Western-mandated telecom surveillance backdoors to conduct a multi-year espionage campaign against senior officials in the UK and US. This breach highlights a critical vulnerability in Western surveillance policies. The most likely hypothesis is that the breach was a deliberate, state-sponsored operation aimed at gaining strategic advantage. This assessment is made with moderate confidence due to the complexity and scale of the operation.
2. Competing Hypotheses
- Hypothesis A: The breach was a state-sponsored operation by China, leveraging telecom backdoors to gain intelligence on Western political figures. This is supported by the systematic targeting of high-level officials and the use of sophisticated cyber techniques. However, the full extent of Chinese state involvement remains uncertain.
- Hypothesis B: The breach was conducted by an independent hacking group with potential ties to Chinese state actors, aiming to sell or leverage the information for financial gain. This is less supported due to the strategic nature of the targets and the lack of evidence indicating financial motives.
- Assessment: Hypothesis A is currently better supported due to the strategic selection of targets and the alignment with Chinese state interests. Indicators that could shift this judgment include evidence of financial transactions or communications indicating non-state actor involvement.
3. Key Assumptions and Red Flags
- Assumptions: The breach was primarily motivated by state-level strategic interests; Western surveillance laws were the primary vulnerability exploited; Salt Typhoon is directly linked to the Chinese Ministry of State Security.
- Information Gaps: The specific methods used to maintain access over multiple years; the full scope of data accessed and its current use; confirmation of the exact role of Chinese state actors.
- Bias & Deception Risks: Potential confirmation bias in attributing the breach solely to Chinese state actors; risk of deception in the attribution of the Salt Typhoon group.
4. Implications and Strategic Risks
This development could lead to increased scrutiny and potential overhaul of Western surveillance policies, impacting international relations and domestic security protocols.
- Political / Geopolitical: Potential escalation in cyber tensions between China and Western nations; increased diplomatic friction over cybersecurity policies.
- Security / Counter-Terrorism: Heightened vulnerability of Western intelligence operations; potential for compromised counter-terrorism efforts.
- Cyber / Information Space: Increased cyber defense measures and potential for retaliatory cyber operations; heightened focus on securing telecom infrastructure.
- Economic / Social: Potential economic repercussions from strained international relations; public concern over privacy and data security.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive audit of telecom infrastructure for vulnerabilities; enhance monitoring of telecom networks for unusual activities.
- Medium-Term Posture (1–12 months): Develop resilience measures to mitigate future breaches; strengthen international partnerships for cyber defense collaboration.
- Scenario Outlook:
- Best: Successful mitigation of vulnerabilities and strengthened international cyber cooperation.
- Worst: Continued exploitation of telecom backdoors leading to further intelligence breaches.
- Most-Likely: Incremental policy changes and improved cyber defenses, with ongoing geopolitical tensions.
6. Key Individuals and Entities
- Salt Typhoon group
- Chinese Ministry of State Security
- UK Prime Ministers Boris Johnson, Liz Truss, Rishi Sunak
- US political figures (specific names not clearly identifiable from open sources in this snippet)
7. Thematic Tags
cybersecurity, cyber-espionage, telecom security, Chinese state actors, Western surveillance policy, intelligence breach, geopolitical tensions
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us