Chinese hackers reportedly infiltrated phones of UK prime ministers’ aides, compromising sensitive communicat…
Published on: 2026-01-27
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: China-linked group accused of spying on phones of UK prime ministers’ aides for years
1. BLUF (Bottom Line Up Front)
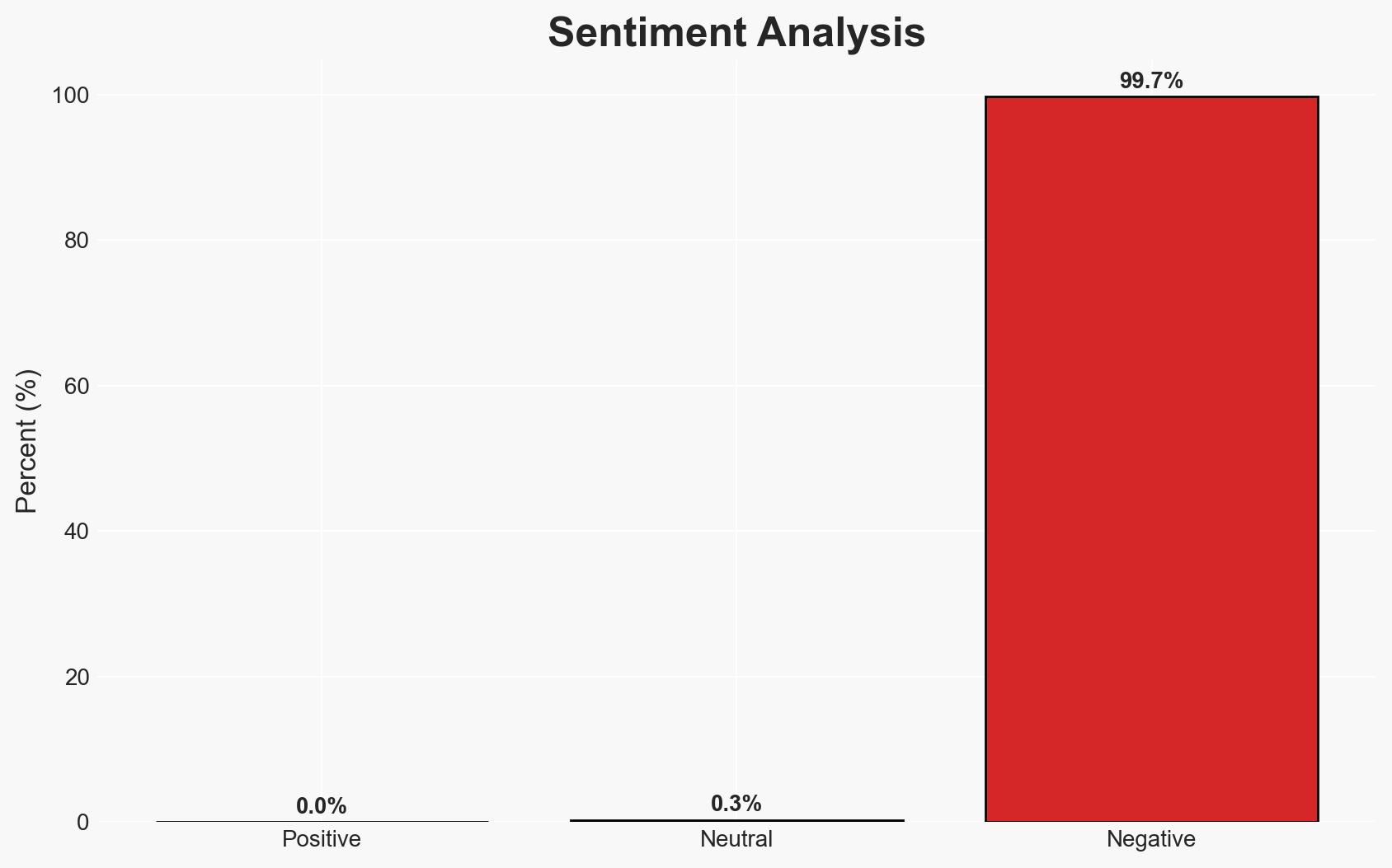
The Chinese state-linked group, Salt Typhoon, is accused of infiltrating the phones of senior UK government aides, potentially compromising sensitive communications since 2021. This activity, if confirmed, represents a significant breach of UK national security. The most likely hypothesis is that Salt Typhoon conducted these operations to gather intelligence on UK political dynamics. Overall confidence in this judgment is moderate due to limited direct evidence of device access and potential geopolitical motivations.
2. Competing Hypotheses
- Hypothesis A: Salt Typhoon, a Chinese state-linked group, conducted espionage on UK government aides’ phones to gather intelligence on political activities. This is supported by the group’s known capabilities in telecom intrusions and the timing of the breaches. However, the lack of direct evidence on the prime ministers’ devices remains a key uncertainty.
- Hypothesis B: The reported breaches are exaggerated or misattributed, possibly as part of a broader geopolitical narrative against China. Contradicting evidence includes China’s denial and the timing of the allegations coinciding with diplomatic engagements.
- Assessment: Hypothesis A is currently better supported due to the alignment of Salt Typhoon’s known methods with the reported activities. Indicators such as further technical evidence or corroborative intelligence from other nations could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The group had the capability and intent to conduct such operations; the reported breaches align with Salt Typhoon’s known methods; UK intelligence assessments are accurate.
- Information Gaps: Direct evidence of access to the prime ministers’ devices; comprehensive technical analysis of the breaches; motivations behind the timing of the disclosure.
- Bias & Deception Risks: Potential confirmation bias in attributing activities to China; geopolitical motivations influencing public disclosures; possible misinformation from involved parties.
4. Implications and Strategic Risks
This development could strain UK-China relations and influence global perceptions of China’s cyber activities. It may prompt increased cybersecurity measures and diplomatic tensions.
- Political / Geopolitical: Potential escalation in diplomatic tensions between the UK and China, influencing trade and diplomatic engagements.
- Security / Counter-Terrorism: Heightened alertness to cyber threats within government and critical infrastructure sectors.
- Cyber / Information Space: Increased scrutiny on telecom security and potential shifts in cyber defense strategies.
- Economic / Social: Potential impacts on UK-China trade relations and public perception of government cybersecurity efficacy.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive forensic analysis of affected devices, enhance monitoring of government communications, and engage in diplomatic dialogue with China.
- Medium-Term Posture (1–12 months): Strengthen cybersecurity infrastructure, foster international cooperation on cyber threats, and develop resilience measures against state-sponsored espionage.
- Scenario Outlook:
- Best: Diplomatic resolution and strengthened cybersecurity cooperation.
- Worst: Escalation of tensions leading to economic and diplomatic fallout.
- Most-Likely: Ongoing diplomatic negotiations with incremental cybersecurity improvements.
6. Key Individuals and Entities
- Salt Typhoon (Chinese state-linked group)
- Boris Johnson (Former UK Prime Minister)
- Liz Truss (Former UK Prime Minister)
- Rishi Sunak (Former UK Prime Minister)
- Keir Starmer (Current UK Prime Minister)
- MI5 (UK Security Service)
- Chinese Foreign Ministry
7. Thematic Tags
cybersecurity, cyber-espionage, UK-China relations, national security, telecommunications security, geopolitical tensions, state-sponsored hacking, intelligence gathering
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us