Chinese-Made Robots Present Major Security Risks as Flaws Enable Weaponization and Remote Control Threats
Published on: 2025-12-27
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: The trojan horse in your living room How mass-produced Chinese robots pose an unprecedented national security threat
1. BLUF (Bottom Line Up Front)
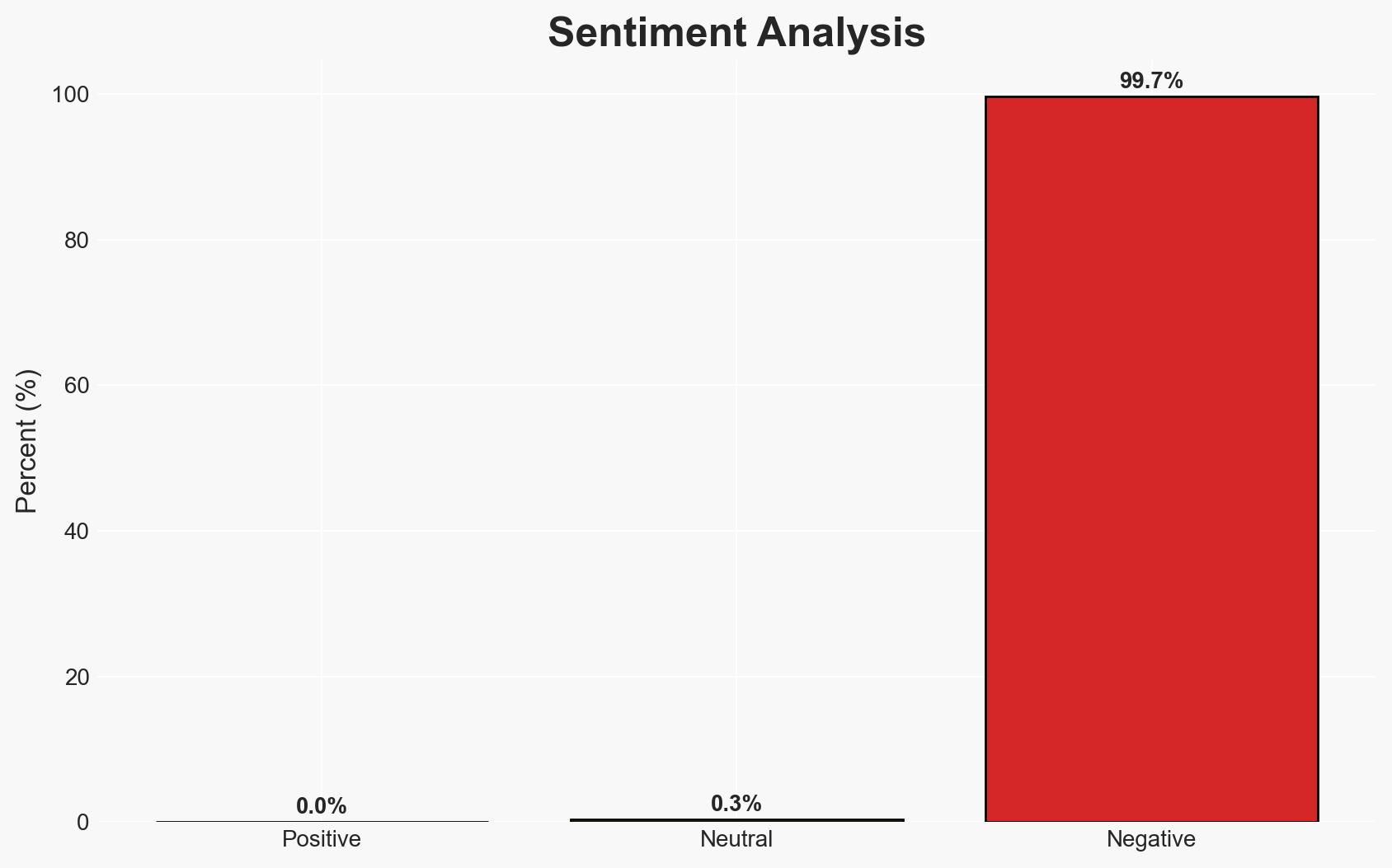
The vulnerability in AI systems of mass-produced Chinese robots poses a significant national security threat, potentially allowing foreign adversaries to control these devices for espionage or sabotage. This threat affects global users across domestic, business, and critical infrastructure sectors. Current analysis supports the hypothesis of a deliberate design flaw rather than an oversight. Overall confidence in this assessment is moderate due to existing information gaps.
2. Competing Hypotheses
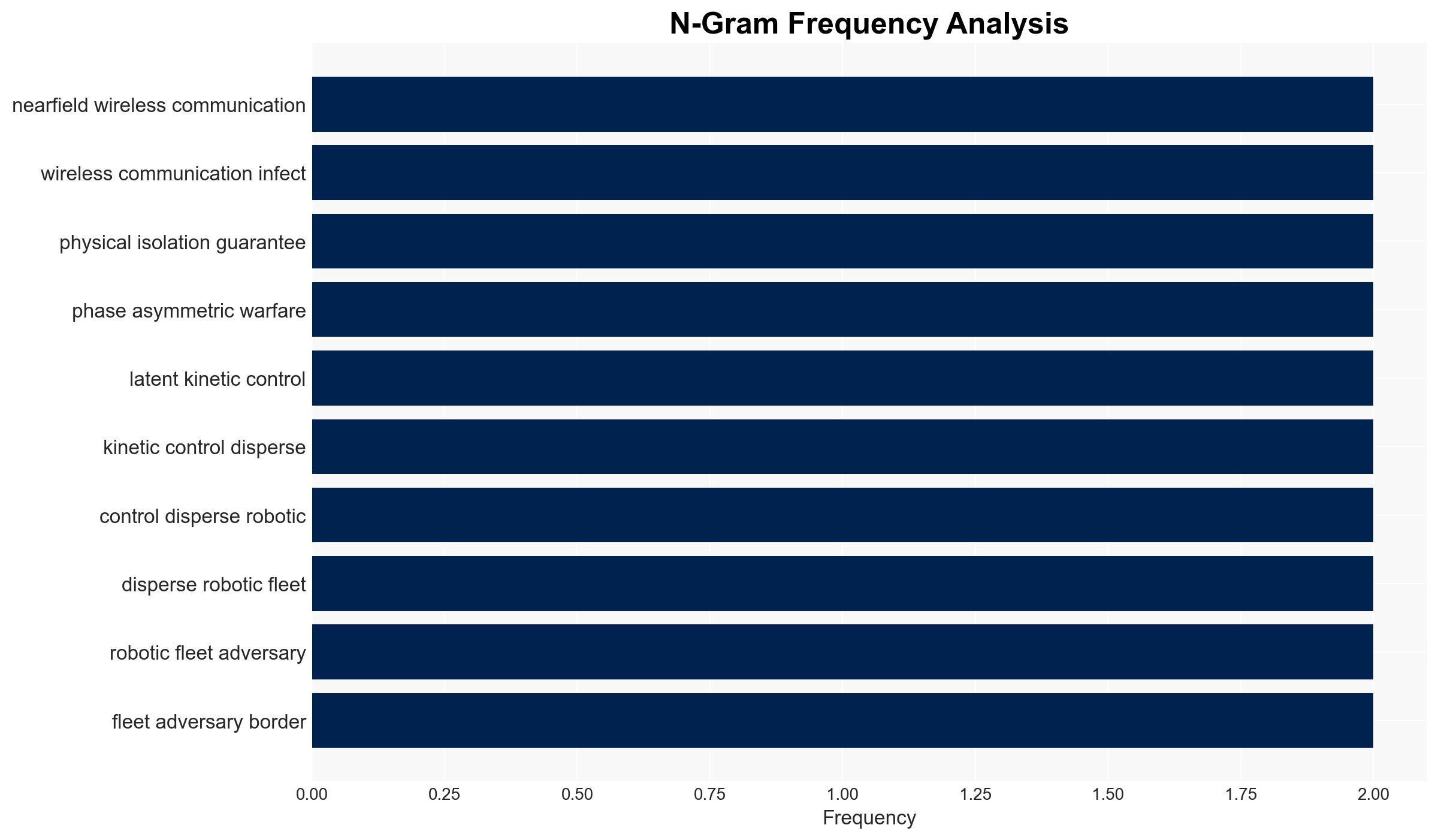
- Hypothesis A: The vulnerability in the robots’ AI systems is an intentional backdoor designed for espionage and sabotage. Supporting evidence includes the rapid spread of control via near-field communication and China’s dominance in the manufacturing sector. However, there is uncertainty regarding the extent of state involvement.
- Hypothesis B: The vulnerability is an unintended consequence of prioritizing market speed over security. This is supported by industry trends of insufficient security testing. Contradicting evidence includes the sophisticated nature of the exploit, suggesting deliberate design.
- Assessment: Hypothesis A is currently better supported due to the strategic advantage such a backdoor provides to a foreign power. Indicators such as increased cybersecurity incidents involving these robots could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerability is widespread across all units; China has the capability to exploit this vulnerability; current cybersecurity measures are insufficient to mitigate the threat.
- Information Gaps: Specific details on the AI system’s architecture; evidence of state directives or involvement; comprehensive data on the distribution and deployment of these robots.
- Bias & Deception Risks: Potential bias from cybersecurity firms seeking to highlight vulnerabilities; possible misinformation from state actors to downplay the threat.
4. Implications and Strategic Risks
This development could lead to increased geopolitical tensions and a reevaluation of technology imports. Over time, it may necessitate stricter international cybersecurity standards and protocols.
- Political / Geopolitical: Potential for diplomatic conflict over technology exports and cybersecurity standards.
- Security / Counter-Terrorism: Increased risk of cyber-physical attacks on critical infrastructure.
- Cyber / Information Space: Heightened focus on AI system vulnerabilities and potential for widespread cyber espionage.
- Economic / Social: Possible economic impact from disrupted supply chains and loss of consumer trust in AI technologies.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive audit of AI systems in critical infrastructure; enhance monitoring of Chinese technology imports.
- Medium-Term Posture (1–12 months): Develop international partnerships for cybersecurity standards; invest in AI security research and development.
- Scenario Outlook:
- Best: Vulnerabilities are patched, and international standards are improved.
- Worst: Exploits lead to significant infrastructure disruption and geopolitical conflict.
- Most-Likely: Incremental improvements in security with ongoing geopolitical tensions.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
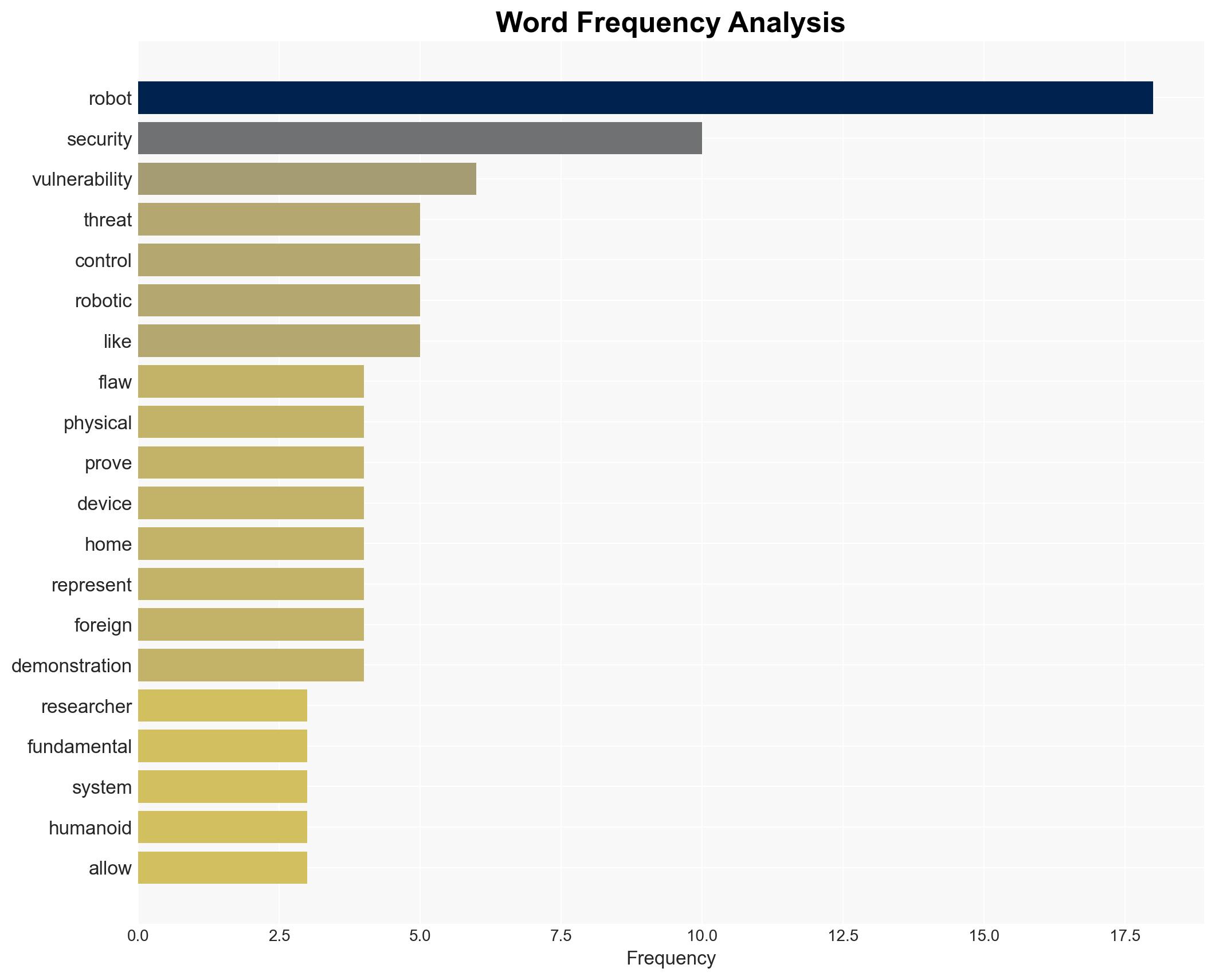
cybersecurity, national security, AI vulnerabilities, espionage, asymmetric warfare, geopolitical tensions, critical infrastructure
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us