Chinese Salt Typhoon Hacking Campaign Likely Breached Australian Critical Infrastructure, Expert Warns
Published on: 2026-01-01
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Salt Typhoon Chinese hacking campaign likely infiltrated Australian critical infrastructure expert warns
1. BLUF (Bottom Line Up Front)
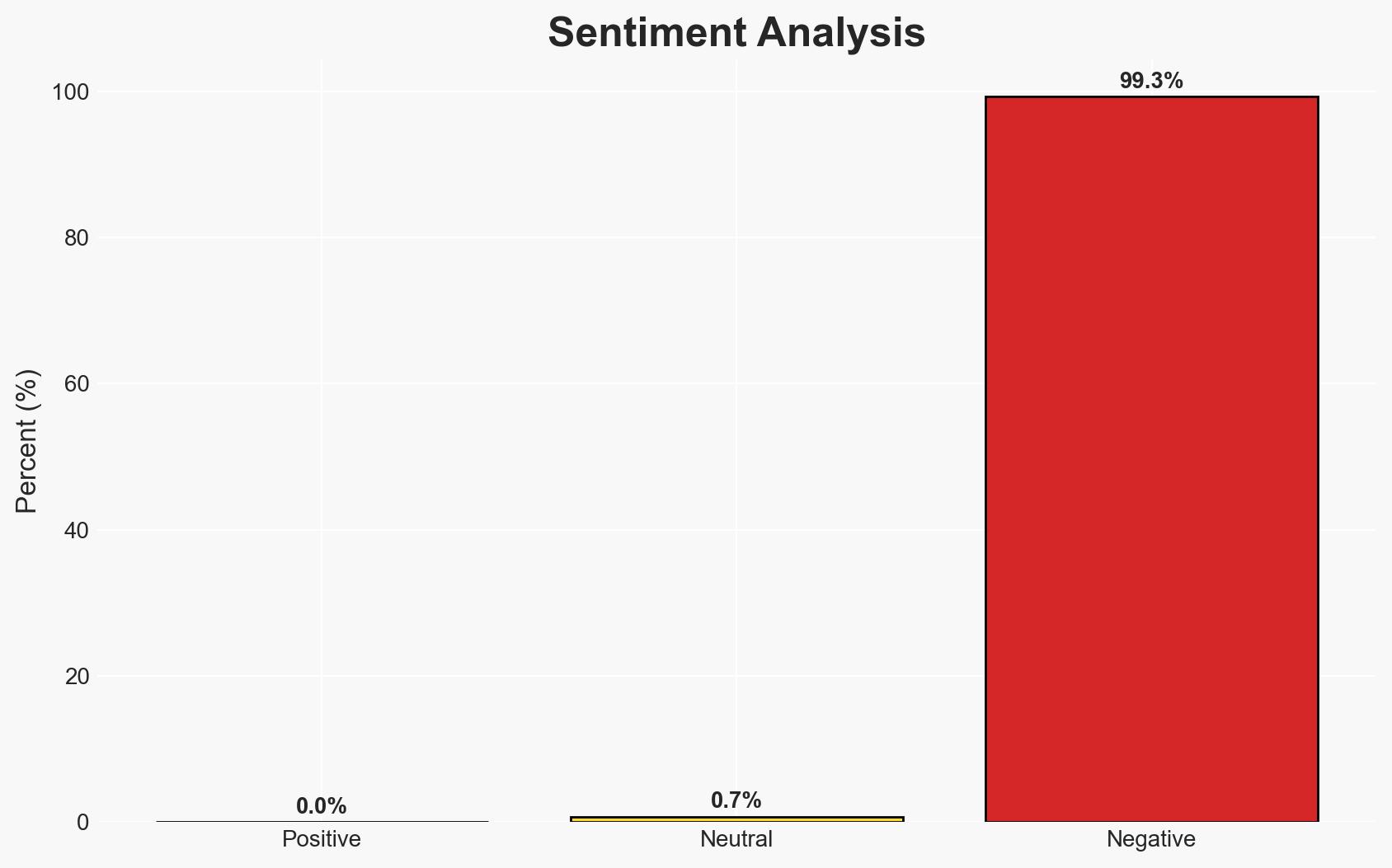
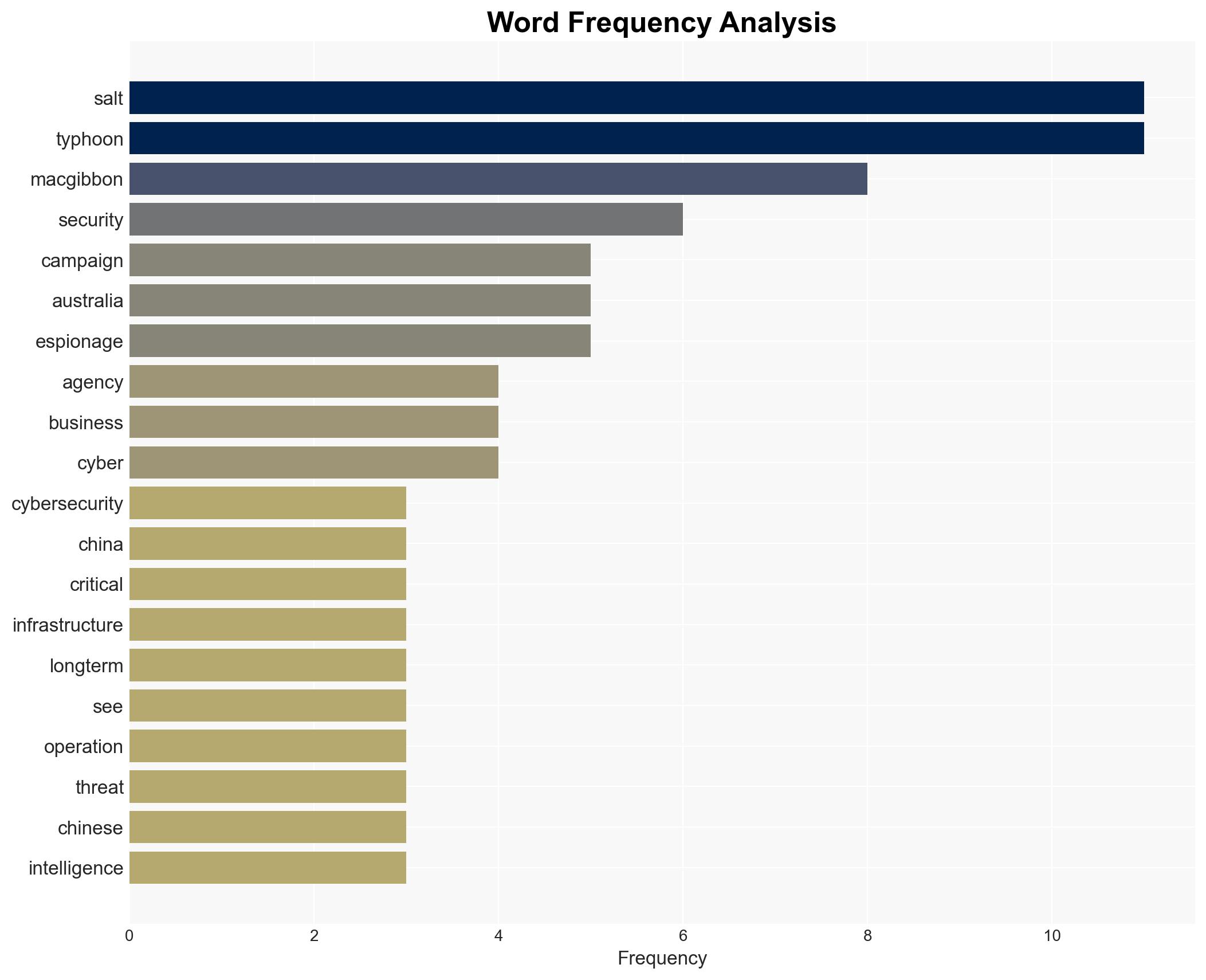
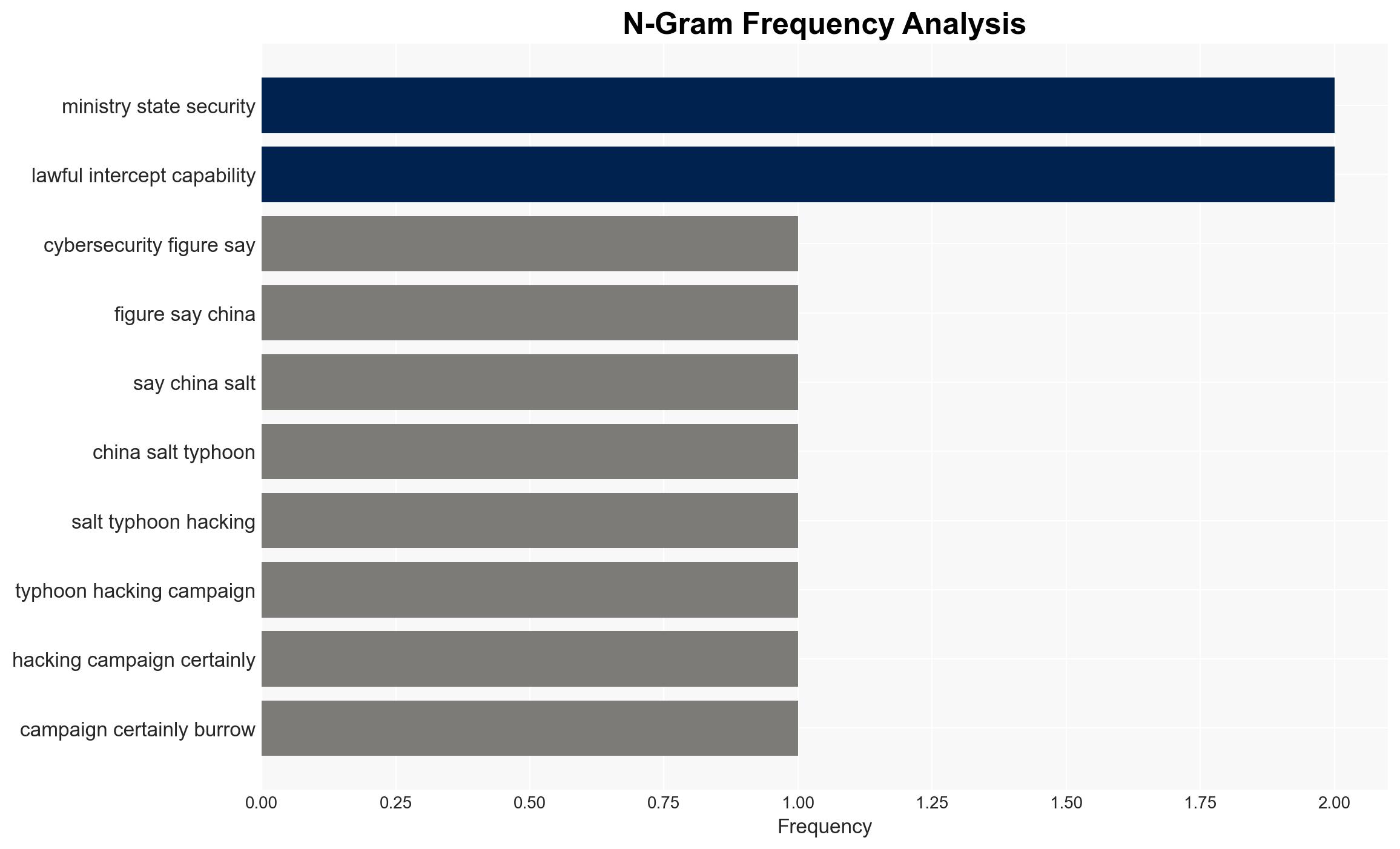
The Salt Typhoon hacking campaign, attributed to Chinese state actors, is highly likely to have infiltrated Australian critical infrastructure, posing significant espionage and security risks. This operation, characterized by its stealth and persistence, potentially affects multiple sectors in Australia and New Zealand. Overall, there is moderate confidence in this assessment due to the lack of direct public evidence but strong circumstantial indicators.
2. Competing Hypotheses
- Hypothesis A: Salt Typhoon has successfully infiltrated Australian critical infrastructure. This is supported by expert analysis and the campaign’s known capabilities and objectives. However, there is no direct public evidence of such infiltration, creating uncertainty.
- Hypothesis B: Salt Typhoon has not infiltrated Australian critical infrastructure, and the perceived threat is overstated. This is supported by the absence of confirmed breaches in public records, but contradicted by the campaign’s extensive activity in other countries.
- Assessment: Hypothesis A is currently better supported due to the campaign’s known methods and objectives, and expert assessments indicating a high likelihood of infiltration. Confirmation of breaches or increased detection capabilities could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Salt Typhoon is state-sponsored by China; the campaign targets critical infrastructure for long-term espionage; current detection capabilities are insufficient to identify all breaches.
- Information Gaps: Specific evidence of infiltration in Australia; detailed technical indicators of compromise; insights into Australia’s current detection and response capabilities.
- Bias & Deception Risks: Potential bias from sources with vested interests in cybersecurity; risk of deception from Chinese state actors to obscure true capabilities and intentions.
4. Implications and Strategic Risks
The Salt Typhoon campaign could significantly alter the security landscape, prompting increased tensions and defensive measures. It may also drive policy changes and international cooperation against cyber threats.
- Political / Geopolitical: Potential escalation in cyber diplomacy and sanctions against China; increased strain on Australia-China relations.
- Security / Counter-Terrorism: Heightened alert levels and resource allocation to cyber defense; potential for increased cyber-attacks as retaliation or diversion.
- Cyber / Information Space: Enhanced focus on cybersecurity infrastructure and capabilities; potential for misinformation or disinformation campaigns.
- Economic / Social: Possible disruptions to critical services; increased public concern over cybersecurity and privacy.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of critical infrastructure networks; conduct threat assessments and penetration testing; increase intelligence sharing with international partners.
- Medium-Term Posture (1–12 months): Develop and implement robust cybersecurity frameworks; invest in advanced detection and response technologies; strengthen public-private partnerships in cybersecurity.
- Scenario Outlook:
- Best Case: No confirmed breaches; improved defenses deter future attempts.
- Worst Case: Significant breaches discovered, leading to major disruptions.
- Most Likely: Incremental detection of breaches; gradual improvement in cybersecurity posture.
6. Key Individuals and Entities
- Alastair MacGibbon, Chief Strategy Officer at CyberCX
- Australian Signals Directorate
- Beijing’s Ministry of State Security
- People’s Liberation Army
- Microsoft (naming convention for threat groups)
7. Thematic Tags
cybersecurity, cyber-espionage, critical infrastructure, national security, China, intelligence, Australia
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us