Chinese Surveillance Technology Threatens Tibetan Refugees in Nepal Amid Global Expansion Efforts
Published on: 2025-12-20
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: US tech enabled China’s surveillance empire Tibetan refugees in Nepal pay the price
1. BLUF (Bottom Line Up Front)
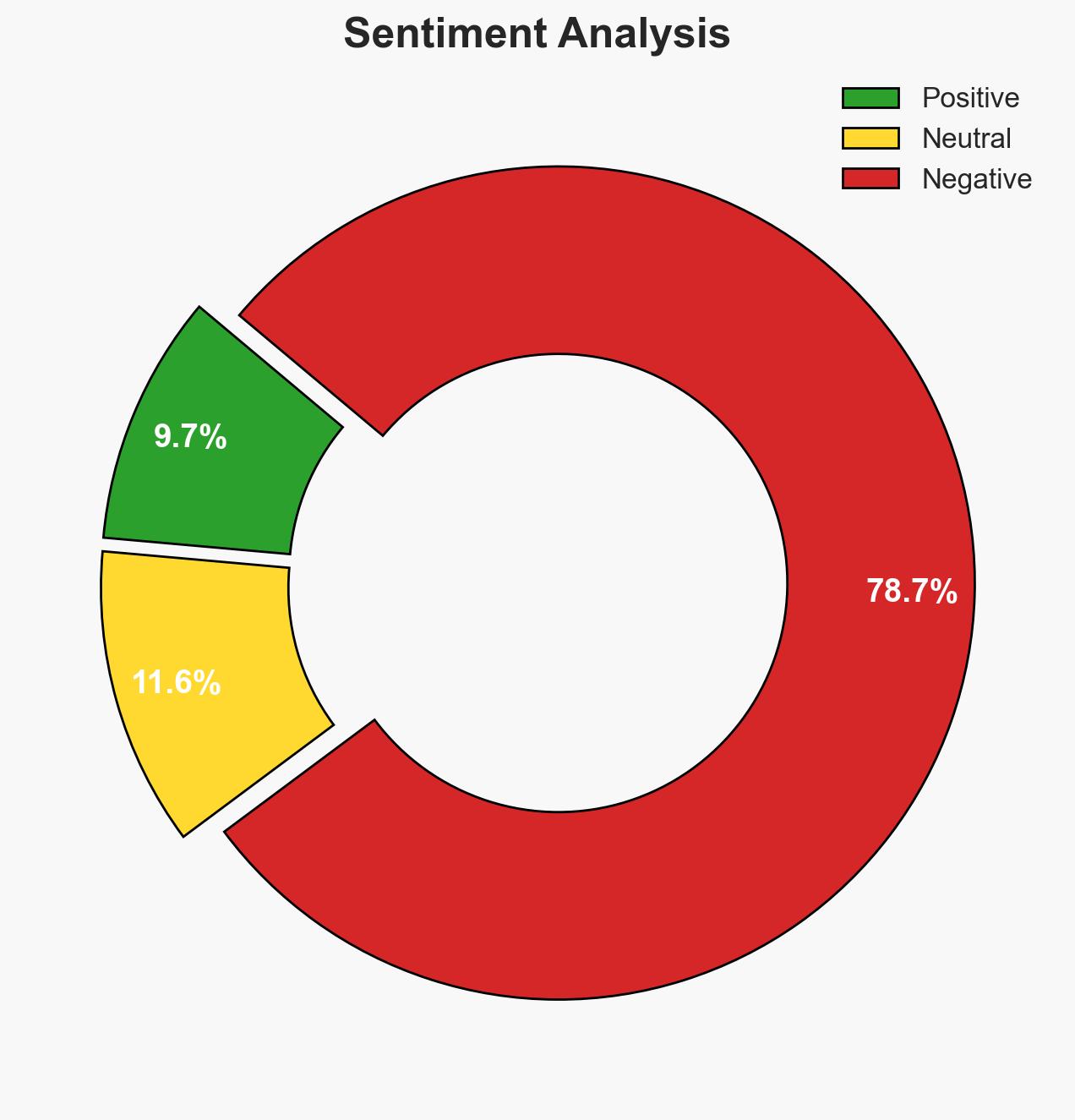
China’s deployment of surveillance technology in Nepal, enabled by US-developed tech, is significantly impacting Tibetan refugees and the Free Tibet movement. This development underscores China’s global influence strategy through digital authoritarianism. The situation presents moderate confidence in the hypothesis that China’s surveillance capabilities are expanding globally, leveraging US technology.
2. Competing Hypotheses
- Hypothesis A: China is using US-developed technology to expand its global surveillance capabilities, targeting Tibetan refugees in Nepal as part of a broader strategy to suppress dissent. This is supported by the widespread deployment of Chinese surveillance tech in Nepal and other countries. However, the extent of US tech involvement remains partially unclear.
- Hypothesis B: The surveillance technology in Nepal is primarily a result of local government initiatives to enhance security, with China’s involvement being coincidental rather than strategic. This hypothesis is less supported due to the global pattern of Chinese tech exports and strategic interests in suppressing Tibetan activism.
- Assessment: Hypothesis A is currently better supported due to the alignment of China’s strategic interests in controlling Tibetan activism and the global pattern of deploying surveillance technology in politically sensitive regions. Key indicators that could shift this judgment include evidence of local government initiatives independent of Chinese influence.
3. Key Assumptions and Red Flags
- Assumptions: China is strategically exporting surveillance technology to suppress dissent; US tech firms are indirectly enabling this through technology sharing; Nepal’s government is complicit or unable to resist Chinese influence.
- Information Gaps: Detailed data on the contractual agreements between Chinese firms and the Nepalese government; specific roles of US tech companies in these deployments.
- Bias & Deception Risks: Potential bias in sources highlighting US tech involvement to deflect from local governance issues; Chinese firms’ statements may be deceptive regarding their role in human rights abuses.
4. Implications and Strategic Risks
The deployment of Chinese surveillance technology in Nepal may lead to increased suppression of Tibetan activism and broader geopolitical tensions. It could also influence other nations to adopt similar technologies, impacting global human rights and privacy norms.
- Political / Geopolitical: Potential escalation in US-China tensions over technology transfer and human rights issues; increased Chinese influence in South Asia.
- Security / Counter-Terrorism: Enhanced surveillance capabilities may suppress legitimate dissent but could also drive underground movements, complicating counter-terrorism efforts.
- Cyber / Information Space: Expansion of Chinese digital infrastructure could lead to increased cyber vulnerabilities and influence operations.
- Economic / Social: Economic dependencies on Chinese technology may grow, affecting local economies and social cohesion, particularly in regions with significant refugee populations.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase monitoring of Chinese tech deployments in Nepal; engage with local stakeholders to assess the impact on Tibetan communities.
- Medium-Term Posture (1–12 months): Develop resilience measures for at-risk populations; strengthen partnerships with regional allies to counterbalance Chinese influence.
- Scenario Outlook:
- Best: International pressure leads to reduced surveillance and improved human rights conditions.
- Worst: Expanded surveillance leads to further suppression and regional instability.
- Most-Likely: Continued surveillance with intermittent international scrutiny and limited local resistance.
6. Key Individuals and Entities
- Amazon Web Services (AWS)
- Hikvision
- Dahua
- Sheena Greitens, University of Texas at Austin
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, surveillance, China, US technology, Tibetan refugees, global influence, human rights, digital authoritarianism
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us