CISA concludes 10 Emergency Directives in significant simultaneous retirement following successful action imp…
Published on: 2026-01-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: CISA retires 10 emergency cyber orders in rare bulk closure
1. BLUF (Bottom Line Up Front)
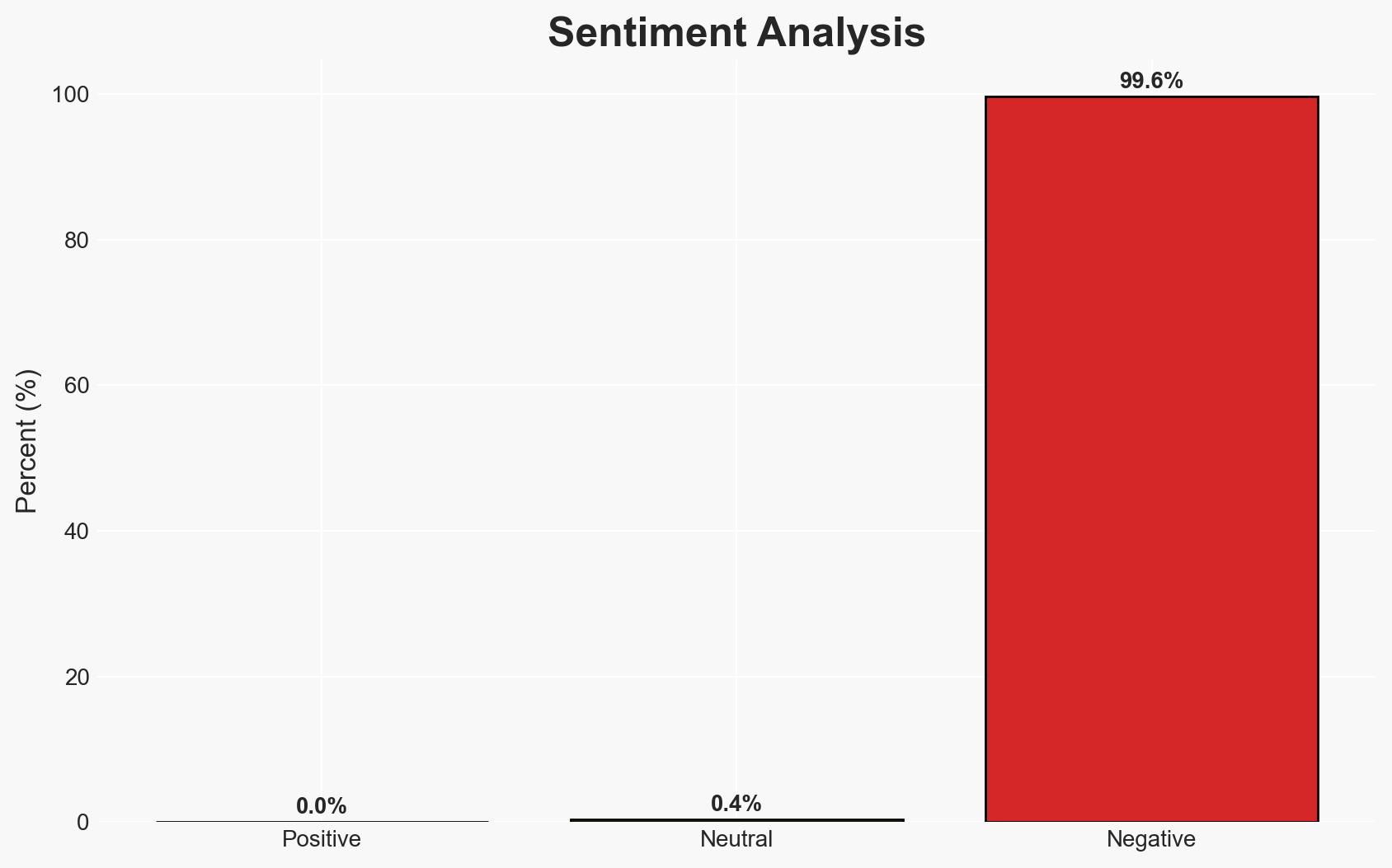
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has retired 10 Emergency Directives, consolidating their requirements under Binding Operational Directive 22-01. This move suggests a strategic shift towards a more streamlined approach to managing cyber vulnerabilities. The decision affects federal civilian agencies, which must now adhere to the updated directive timelines. Overall confidence in this assessment is moderate, given the lack of detailed information on the implementation status across all agencies.
2. Competing Hypotheses
- Hypothesis A: CISA’s retirement of the directives indicates successful mitigation of the vulnerabilities and a matured threat management process. Supporting evidence includes the comprehensive review and consolidation under BOD 22-01. However, uncertainties remain regarding the uniformity of implementation across all agencies.
- Hypothesis B: The retirement of directives may be a response to resource constraints or political pressure to demonstrate progress, rather than a reflection of actual risk mitigation. This is contradicted by the structured nature of BOD 22-01, but the lack of transparency on specific agency compliance levels leaves room for doubt.
- Assessment: Hypothesis A is currently better supported due to the structured integration into BOD 22-01 and the use of the Known Exploited Vulnerabilities catalog. Indicators that could shift this judgment include reports of non-compliance or new vulnerabilities emerging from the retired directives.
3. Key Assumptions and Red Flags
- Assumptions: CISA’s review process was thorough and accurate; federal agencies have the capacity to comply with BOD 22-01; the KEV catalog is comprehensive and up-to-date.
- Information Gaps: Specific compliance levels of individual agencies; detailed timelines for vulnerability patching under BOD 22-01; potential new vulnerabilities not covered by the KEV catalog.
- Bias & Deception Risks: Potential optimism bias in CISA’s assessment of directive completion; lack of independent verification of agency compliance; possible underreporting of vulnerabilities by agencies.
4. Implications and Strategic Risks
This development could lead to a more efficient and responsive cyber defense posture but also risks complacency if vulnerabilities are not adequately monitored. The streamlined approach may influence broader cybersecurity policy and agency cooperation.
- Political / Geopolitical: Potential for increased confidence in U.S. cyber defense capabilities, but also scrutiny if vulnerabilities are exploited.
- Security / Counter-Terrorism: Enhanced focus on known vulnerabilities may improve threat response but could divert attention from emerging threats.
- Cyber / Information Space: Consolidation under BOD 22-01 may lead to improved information sharing and faster patch deployment.
- Economic / Social: Improved cybersecurity could bolster economic stability, but failure to manage new threats could undermine public trust.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct an independent audit of agency compliance with BOD 22-01; enhance monitoring of the KEV catalog for emerging threats.
- Medium-Term Posture (1–12 months): Develop partnerships with private sector cybersecurity firms; invest in training for agency IT staff on new directive requirements.
- Scenario Outlook:
- Best: Full compliance with BOD 22-01 leads to reduced cyber incidents.
- Worst: New vulnerabilities emerge, overwhelming agency capabilities.
- Most-Likely: Gradual improvement in cyber defense with occasional setbacks due to emerging threats.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
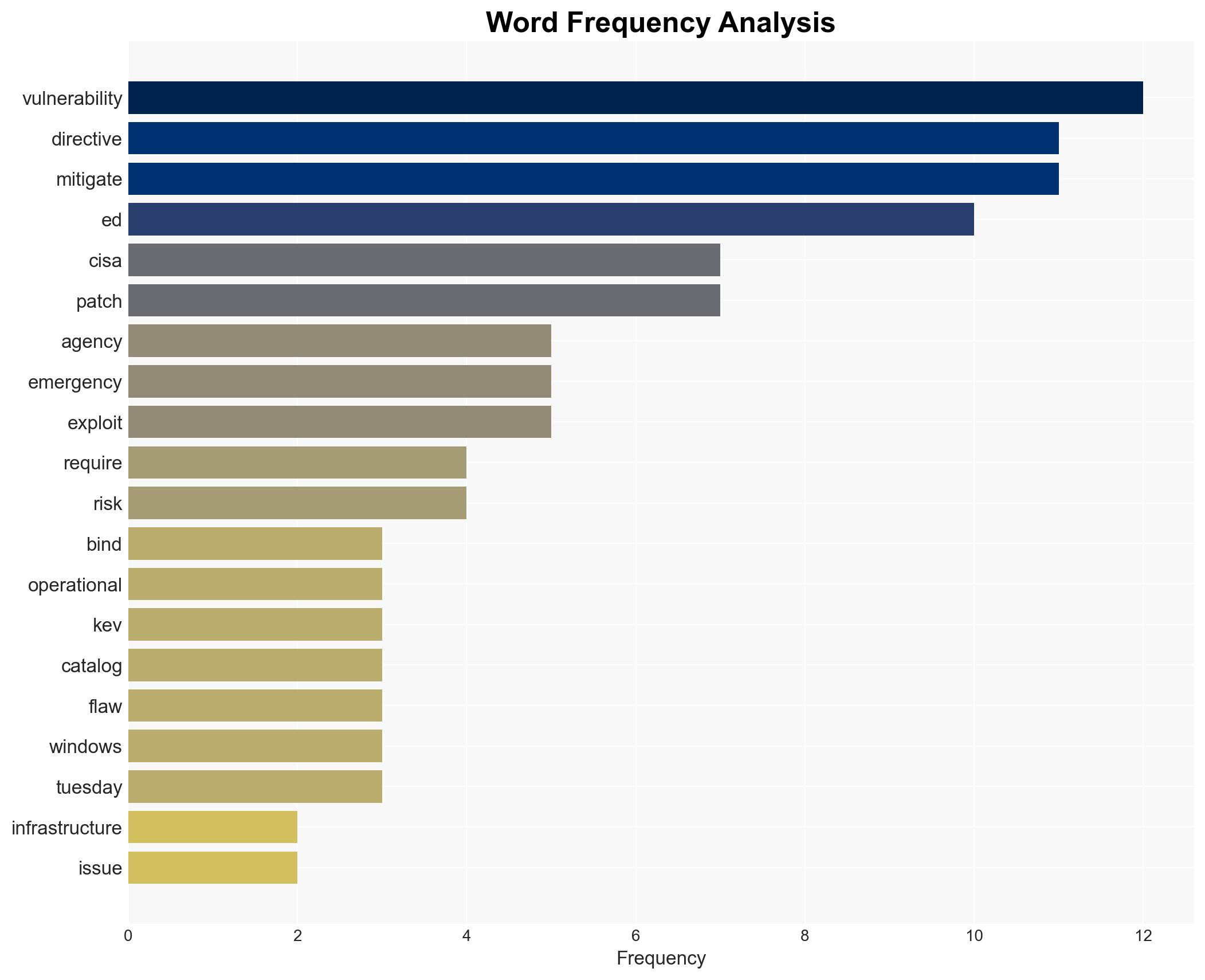
cybersecurity, federal agencies, vulnerability management, CISA, emergency directives, Binding Operational Directive, Known Exploited Vulnerabilities
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us