CISA Directs Federal Agencies to Eliminate Outdated Edge Devices to Mitigate Cybersecurity Risks
Published on: 2026-02-06
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: CISA Orders Removal of Unsupported Edge Devices to Reduce Federal Network Risk
1. BLUF (Bottom Line Up Front)
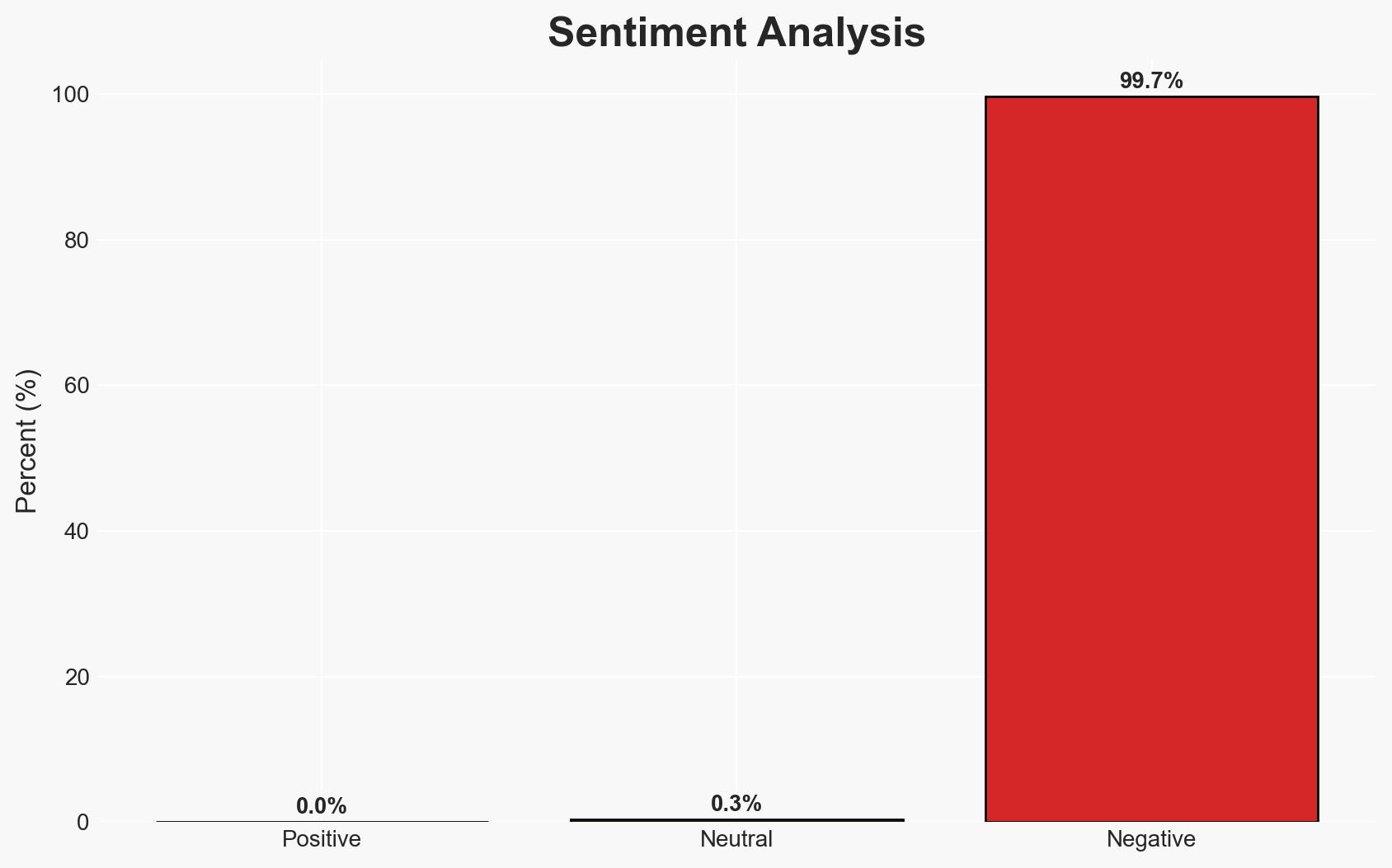
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has mandated the removal of unsupported edge devices from federal networks to mitigate risks from cyber threats, particularly those posed by state-sponsored actors. This directive affects Federal Civilian Executive Branch (FCEB) agencies and aims to enhance network security by reducing technical debt. The overall confidence in this assessment is moderate, given the potential for implementation challenges and evolving threat landscapes.
2. Competing Hypotheses
- Hypothesis A: CISA’s directive will significantly reduce vulnerabilities in federal networks by ensuring all edge devices are up-to-date and supported. This hypothesis is supported by the proactive measures outlined, such as lifecycle management and decommissioning of unsupported devices. However, uncertainties include the agencies’ capacity to comply within the specified timelines and the evolving nature of cyber threats.
- Hypothesis B: The directive may have limited impact due to potential non-compliance or delays in implementation by FCEB agencies. While the directive is comprehensive, the scale of the task and resource constraints could hinder timely execution. Additionally, adversaries may adapt their tactics to exploit other vulnerabilities.
- Assessment: Hypothesis A is currently better supported due to the structured approach and clear timelines provided by CISA, which are likely to drive compliance. Key indicators that could shift this judgment include reports of non-compliance or significant delays in implementation.
3. Key Assumptions and Red Flags
- Assumptions: Agencies have the necessary resources to comply with the directive; state-sponsored actors will continue targeting unsupported devices; CISA’s end-of-support list is comprehensive and accurate.
- Information Gaps: Detailed compliance status of individual agencies; specific threat actor capabilities and intentions regarding federal networks.
- Bias & Deception Risks: Potential underestimation of adversary adaptability; reliance on self-reported compliance data from agencies.
4. Implications and Strategic Risks
This development could enhance the overall cybersecurity posture of federal networks, but its success depends on effective implementation and adaptation to evolving threats.
- Political / Geopolitical: Strengthened cybersecurity could deter state-sponsored cyber operations against U.S. federal networks, potentially reducing geopolitical tensions in cyberspace.
- Security / Counter-Terrorism: Improved network security may decrease the likelihood of successful cyber intrusions by hostile actors, enhancing national security.
- Cyber / Information Space: The directive may set a precedent for similar actions in other sectors, influencing broader cybersecurity practices.
- Economic / Social: Enhanced cybersecurity could protect sensitive economic data, but resource allocation for compliance may strain agency budgets.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Agencies should prioritize cataloging and reporting unsupported devices to CISA; CISA should provide support and resources to ensure compliance.
- Medium-Term Posture (1–12 months): Develop partnerships with OEMs for timely updates and support; invest in training and resources to maintain compliance.
- Scenario Outlook:
- Best: Full compliance leads to a significant reduction in vulnerabilities, deterring adversaries.
- Worst: Non-compliance and resource constraints result in continued vulnerabilities and successful cyber intrusions.
- Most-Likely: Partial compliance with gradual improvement as agencies adapt to new requirements.
6. Key Individuals and Entities
- Madhu Gottumukkala, Acting Director, CISA
- Federal Civilian Executive Branch (FCEB) agencies
7. Thematic Tags
cybersecurity, federal networks, state-sponsored threats, asset management, compliance, CISA, edge devices
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us