CISA identifies ongoing exploit risk in ASUS Live Update vulnerability after seven years
Published on: 2025-12-19
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: CISA warns ASUS Live Update backdoor is still exploitable seven years on
1. BLUF (Bottom Line Up Front)
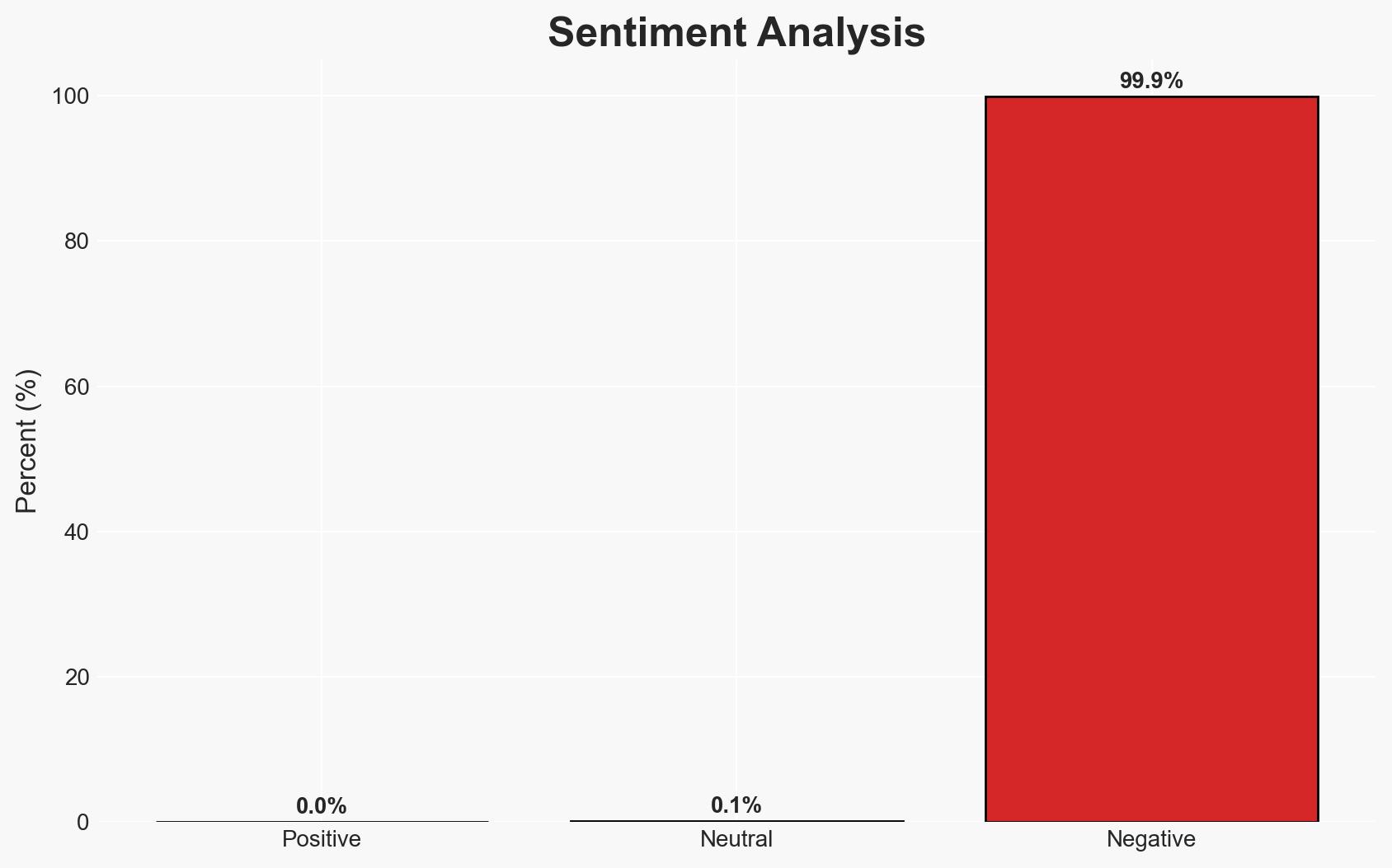
The CISA’s addition of the ASUS Live Update vulnerability to its Known Exploited Vulnerabilities catalog indicates ongoing exploitation risks, affecting users of ASUS devices. This vulnerability, linked to past state-sponsored attacks, remains a critical threat due to its widespread use and the potential for targeted exploitation. Overall confidence in this assessment is moderate, given the historical context and current exploitation signals.
2. Competing Hypotheses
- Hypothesis A: The vulnerability is actively being exploited by state-sponsored actors to target specific high-value individuals or organizations. This is supported by historical evidence of targeted attacks using the ASUS Live Update tool and the CISA’s urgent classification. However, the lack of recent specific attack data creates uncertainty.
- Hypothesis B: The vulnerability is primarily a residual risk from past incidents, with limited current exploitation. While the CISA’s classification suggests active threats, the discontinuation of support for the tool and the small number of initially targeted devices may limit current exploitation scope.
- Assessment: Hypothesis A is currently better supported due to the CISA’s action and historical precedent of state-sponsored exploitation. Key indicators that could shift this judgment include new reports of widespread exploitation or confirmation of limited current attacks.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerability continues to be exploitable despite discontinued support; state-sponsored actors have the capability and intent to exploit this vulnerability; users have not universally updated to secure versions.
- Information Gaps: Specific details on recent exploitation incidents; the extent of current user exposure to the vulnerability; confirmation of actor identities exploiting the vulnerability.
- Bias & Deception Risks: Potential over-reliance on historical data; source bias from CISA’s urgent classification; possible underreporting of exploitation due to limited visibility.
4. Implications and Strategic Risks
This development could lead to increased scrutiny on supply chain vulnerabilities and drive policy changes regarding software update mechanisms. The ongoing risk of exploitation may necessitate enhanced cybersecurity measures across affected sectors.
- Political / Geopolitical: Potential diplomatic tensions if state-sponsored exploitation is confirmed, particularly involving Chinese actors.
- Security / Counter-Terrorism: Heightened threat environment for targeted sectors, requiring increased vigilance and response capabilities.
- Cyber / Information Space: Risk of further supply chain attacks and exploitation of similar vulnerabilities in other widely-used software.
- Economic / Social: Potential economic impacts from compromised systems, particularly if critical infrastructure is affected.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urge ASUS users to update to secure versions; increase monitoring for exploitation indicators; engage with ASUS for further mitigation strategies.
- Medium-Term Posture (1–12 months): Develop partnerships for information sharing on supply chain vulnerabilities; invest in resilience measures for critical systems.
- Scenario Outlook:
- Best: Vulnerability is mitigated through widespread updates, reducing exploitation risk.
- Worst: State-sponsored actors exploit the vulnerability extensively, causing significant disruptions.
- Most-Likely: Continued targeted exploitation with moderate impact, prompting ongoing mitigation efforts.
6. Key Individuals and Entities
- ASUS
- CISA
- MITRE
- Potential Chinese state-sponsored actors (historically linked)
7. Thematic Tags
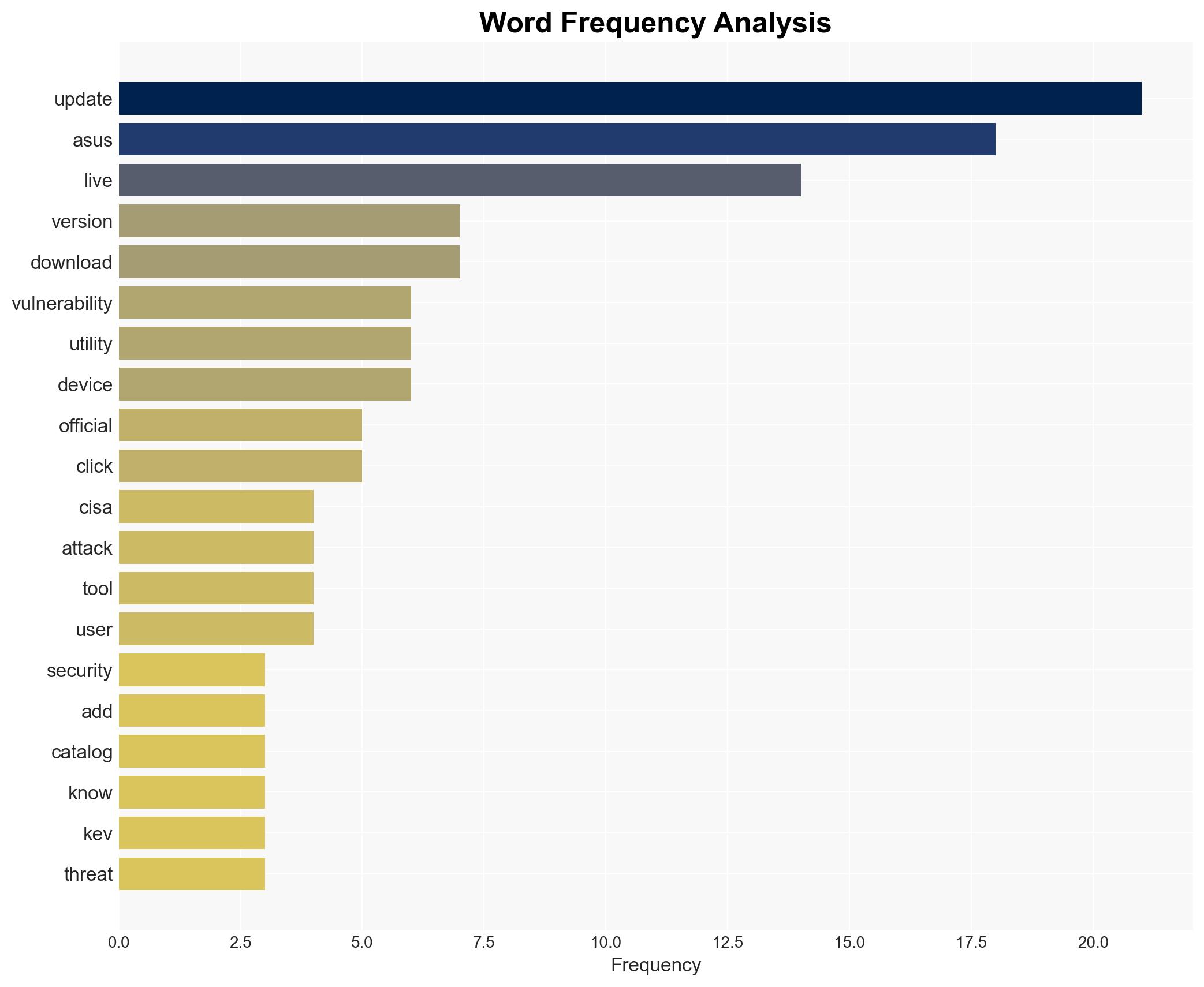
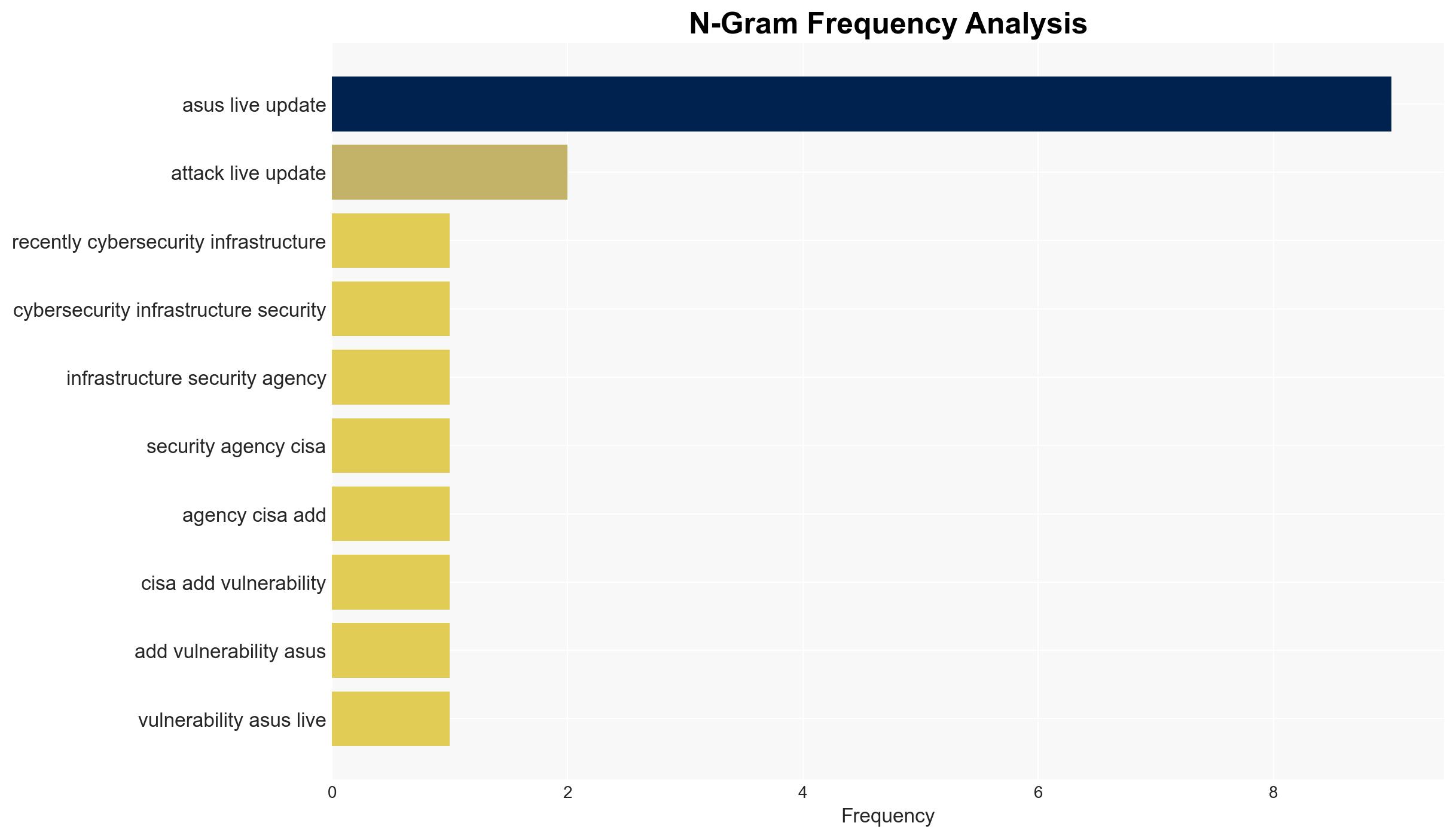
cybersecurity, supply chain, state-sponsored attacks, vulnerability management, ASUS, CISA, cyber-espionage
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us