CISA Includes Critical BeyondTrust RS and PRA Vulnerability in Known Exploited Vulnerabilities List
Published on: 2026-02-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: US CISA adds a flaw in BeyondTrust RS and PRA to its Known Exploited Vulnerabilities catalog
1. BLUF (Bottom Line Up Front)
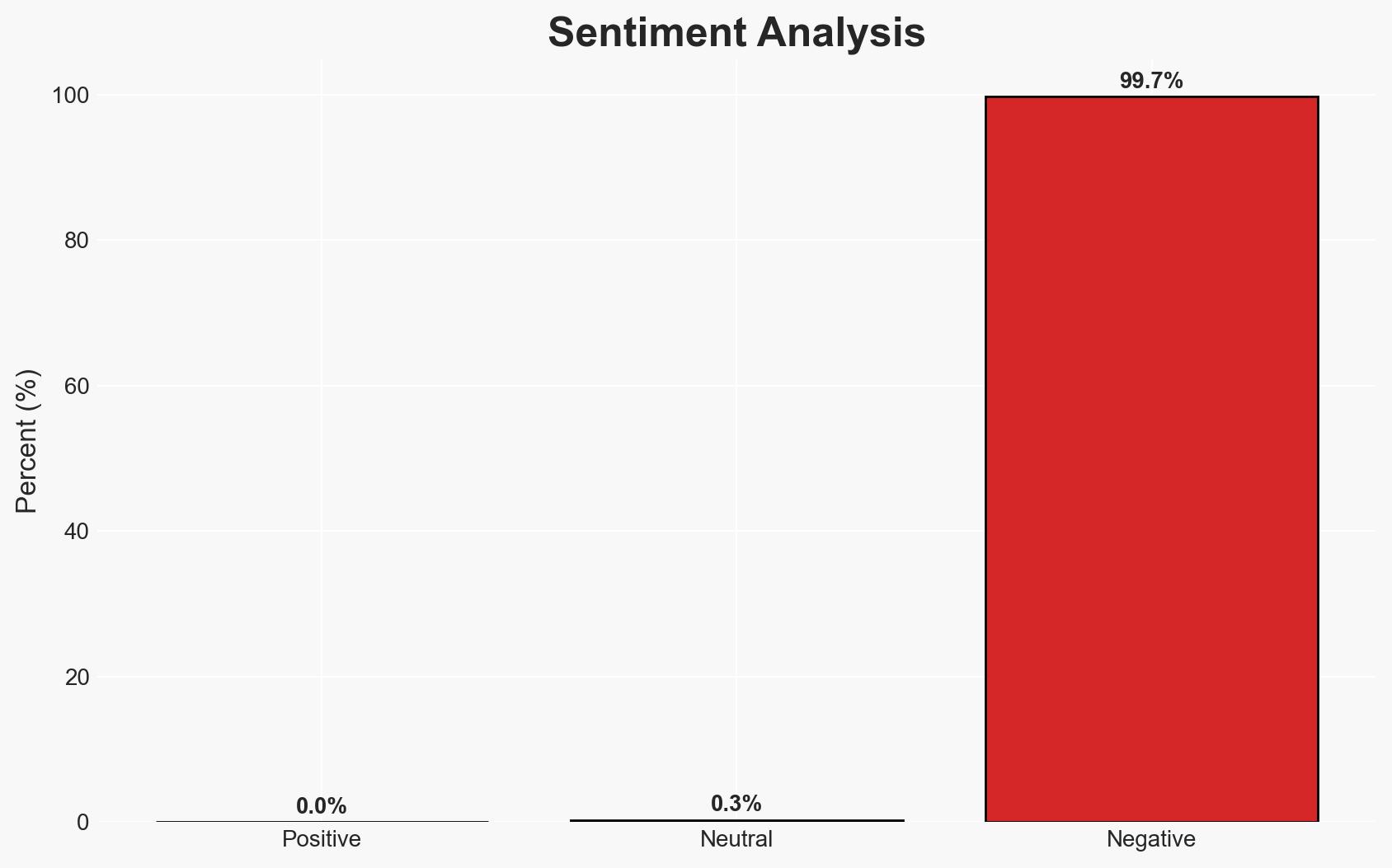
The U.S. CISA has identified a critical vulnerability in BeyondTrust RS and PRA products, which could allow unauthenticated remote code execution. This flaw, CVE-2026-1731, poses significant risks to large organizations across various sectors. The rapid exploitation following the release of a proof-of-concept indicates a high threat level. Overall, there is moderate confidence in the assessment that immediate patching is crucial to mitigate potential system compromises.
2. Competing Hypotheses
- Hypothesis A: The vulnerability will lead to widespread exploitation due to the high number of exposed systems and the critical nature of the flaw. Supporting evidence includes the rapid reconnaissance activity observed and the high CVSS score. Key uncertainties involve the speed and extent of patch deployment by affected organizations.
- Hypothesis B: The impact will be limited due to effective and timely patching by organizations following CISA’s advisory. Supporting evidence includes the availability of patches and the advisory’s dissemination. Contradicting evidence includes the initial rapid exploitation attempts and the potential for delayed patching in some sectors.
- Assessment: Hypothesis A is currently better supported due to the observed rapid exploitation attempts and the potential for significant impact if systems remain unpatched. Indicators that could shift this judgment include reports of widespread patch adoption and a decrease in exploitation attempts.
3. Key Assumptions and Red Flags
- Assumptions: Organizations will prioritize patching based on CISA’s advisory; threat actors will continue exploiting the vulnerability as long as unpatched systems exist; the vulnerability’s impact is proportional to the number of exposed systems.
- Information Gaps: The current patch adoption rate across affected sectors; detailed attribution of the threat actors involved in the exploitation attempts.
- Bias & Deception Risks: Potential over-reliance on initial exploitation reports; possible underestimation of organizations’ patching capabilities and response times.
4. Implications and Strategic Risks
The exploitation of CVE-2026-1731 could lead to significant disruptions across affected sectors if not mitigated promptly. The vulnerability’s exploitation could interact with broader cybersecurity threats, increasing the overall risk landscape.
- Political / Geopolitical: Potential for increased tensions if state-sponsored actors are involved in exploiting the vulnerability.
- Security / Counter-Terrorism: Elevated threat environment due to potential for data breaches and system compromises.
- Cyber / Information Space: Increased cyber threat activity and potential for misinformation campaigns leveraging the vulnerability.
- Economic / Social: Potential economic impact on affected sectors due to service disruptions and data breaches.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Organizations should prioritize patching affected systems, monitor for exploitation attempts, and enhance network defenses.
- Medium-Term Posture (1–12 months): Develop resilience measures, including regular vulnerability assessments and strengthening incident response capabilities.
- Scenario Outlook:
- Best: Rapid patch adoption leads to a decrease in exploitation attempts.
- Worst: Widespread exploitation results in significant data breaches and service disruptions.
- Most-Likely: Mixed patch adoption results in continued but contained exploitation attempts.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, vulnerability management, remote code execution, CISA advisory, patch management, threat intelligence, critical infrastructure
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us