CISA Includes New Vulnerabilities for Prettier, Vite, Versa, and Synacor in Known Exploited Vulnerabilities L…
Published on: 2026-01-23
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
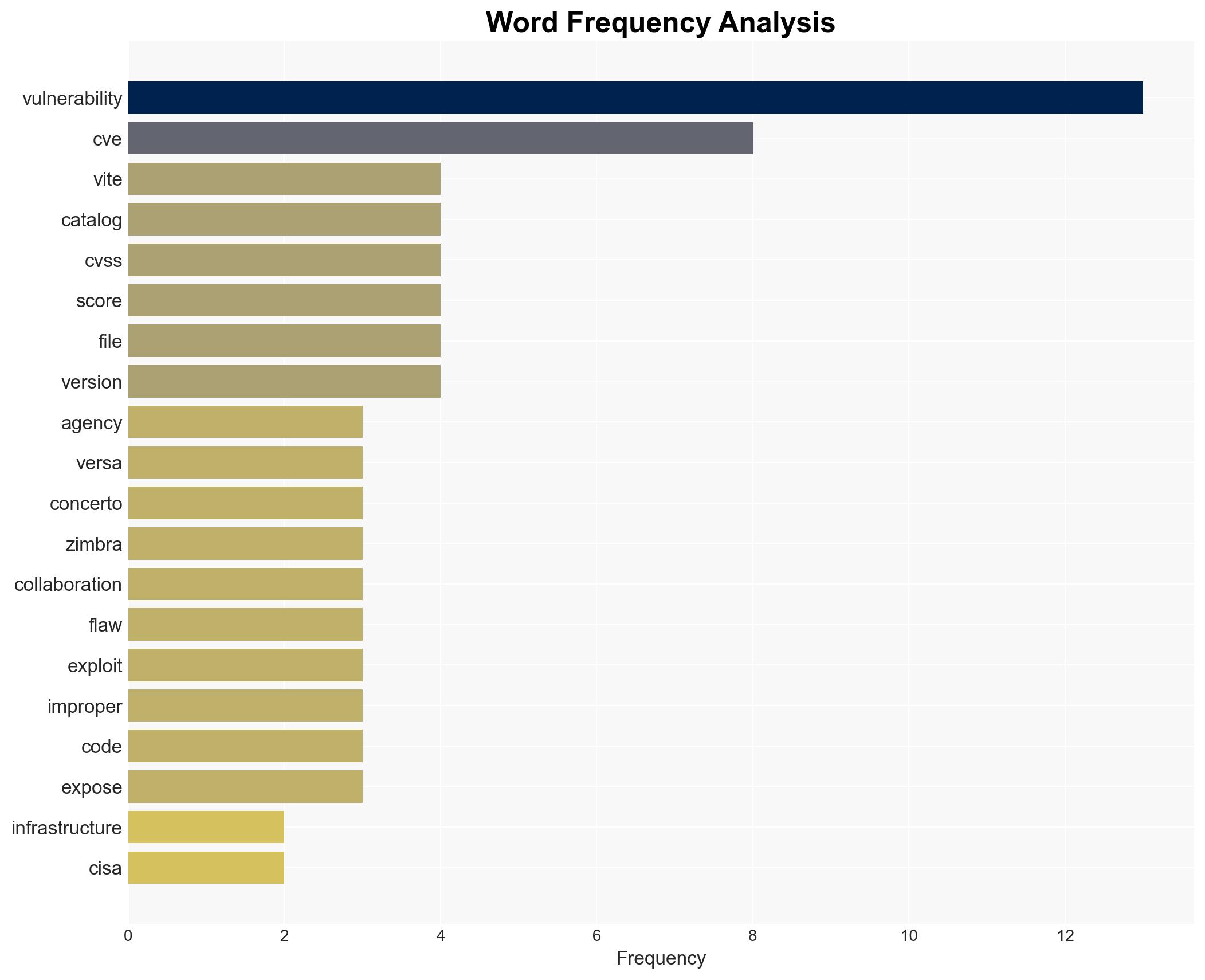
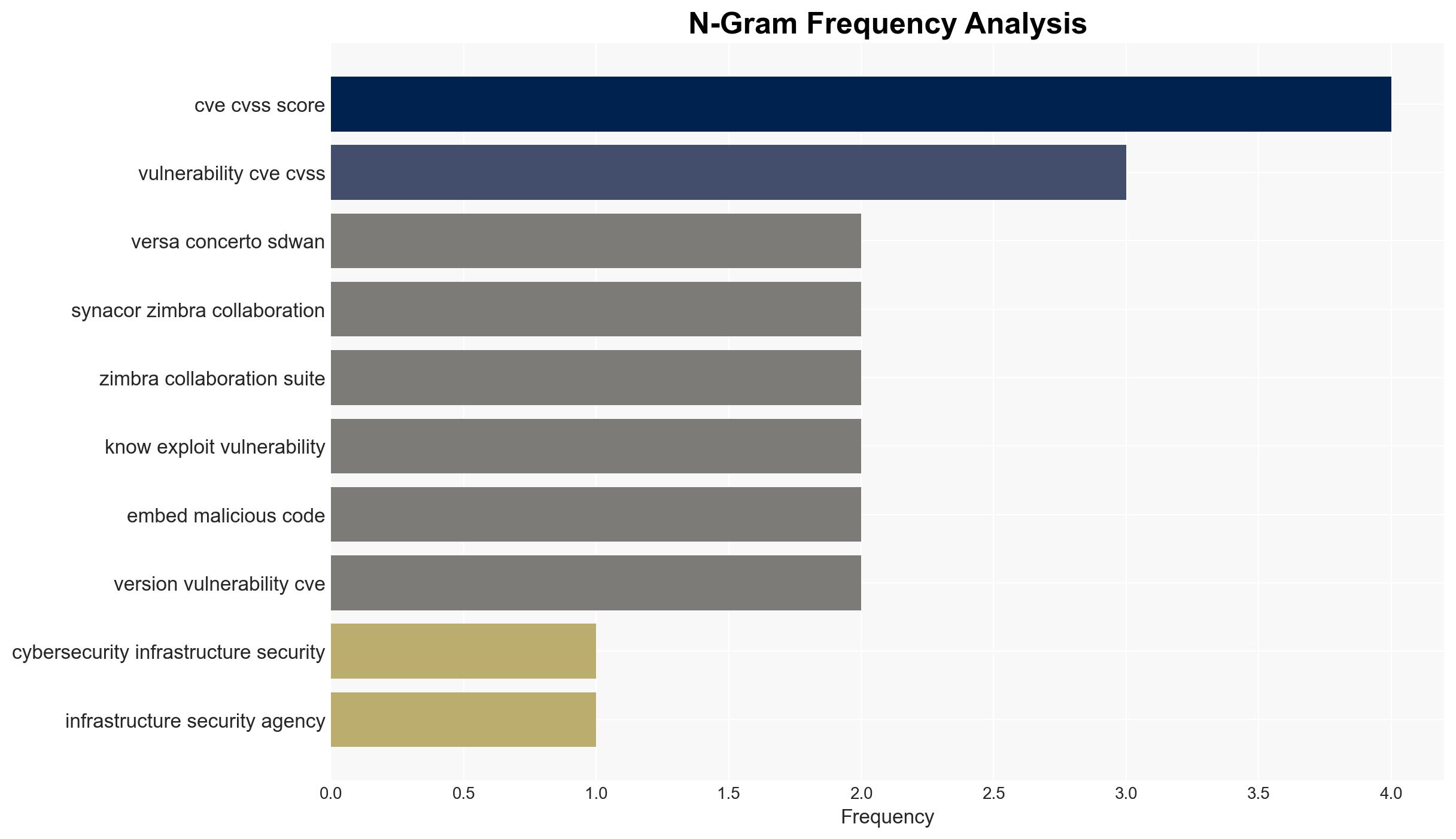
Intelligence Report: US CISA adds Prettier eslint-config-prettier Vite Vitejs Versa Concerto SD-WAN orchestration platform and Synacor Zimbra Collaboration Suite flaws to its Known Exploited Vulnerabilities catalog
1. BLUF (Bottom Line Up Front)
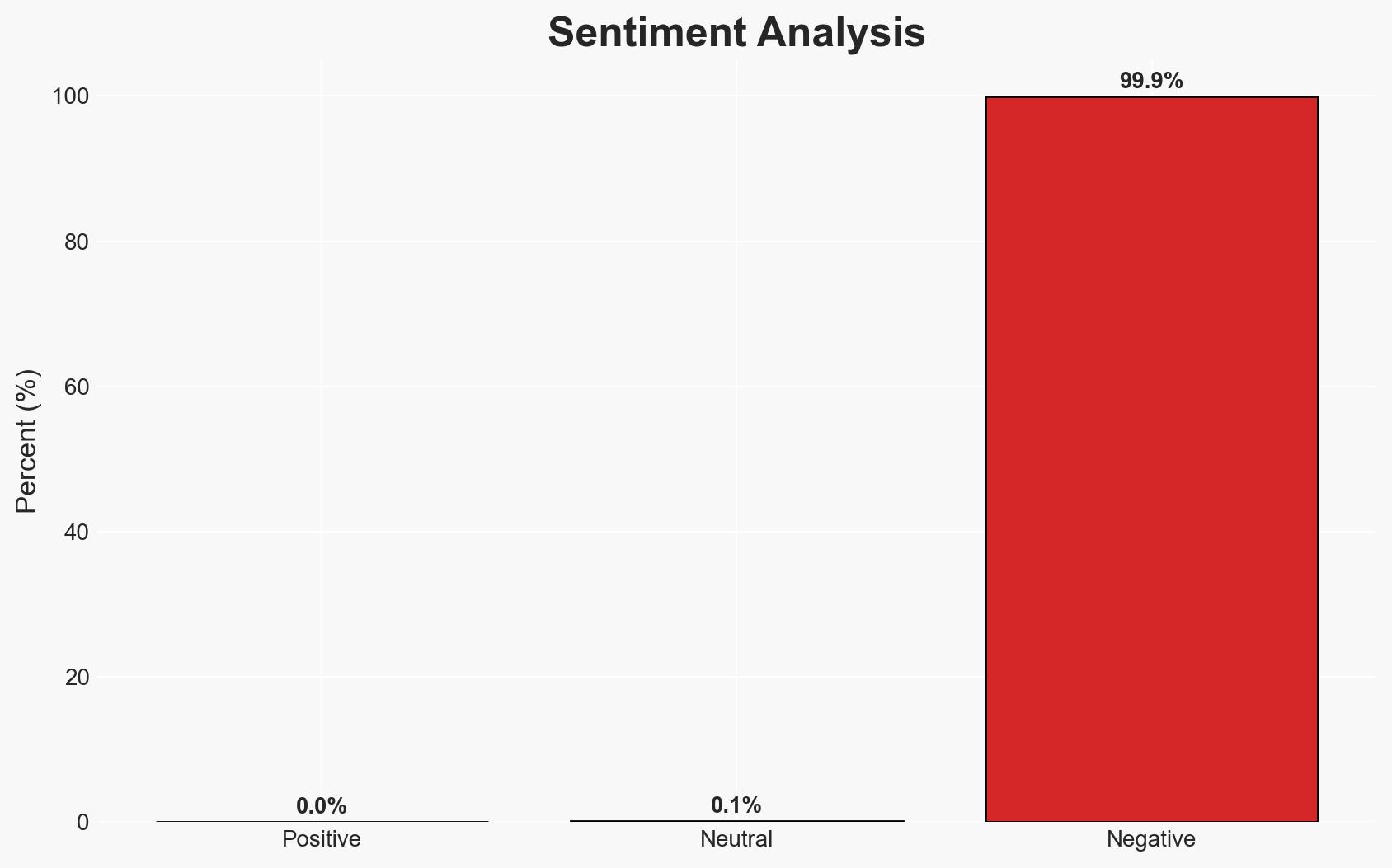
The addition of multiple software vulnerabilities to the CISA Known Exploited Vulnerabilities catalog highlights significant risks to both federal and private sector networks. The vulnerabilities, particularly those with high CVSS scores, pose a serious threat of unauthorized access and data breaches. The most likely hypothesis is that these vulnerabilities are being actively exploited by threat actors, necessitating immediate remediation efforts. Overall confidence in this assessment is moderate, given the explicit inclusion in the CISA catalog.
2. Competing Hypotheses
- Hypothesis A: The vulnerabilities are being actively exploited by cybercriminals or state-sponsored actors to gain unauthorized access to sensitive systems. This is supported by their inclusion in the CISA catalog and the high CVSS scores of some vulnerabilities. However, specific attribution to actors is not provided, creating uncertainty.
- Hypothesis B: The vulnerabilities are not yet widely exploited, and their inclusion in the catalog is a precautionary measure to prevent future exploitation. This is contradicted by the urgency of the CISA directive for federal agencies to address these vulnerabilities.
- Assessment: Hypothesis A is currently better supported due to the explicit action by CISA and the high-risk nature of the vulnerabilities. Indicators such as increased reports of breaches exploiting these vulnerabilities could further support this hypothesis.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerabilities are technically feasible to exploit; threat actors have the capability and intent to exploit these vulnerabilities; CISA’s inclusion in the catalog is based on credible threat intelligence.
- Information Gaps: Specific details on the exploitation methods and the identity of threat actors exploiting these vulnerabilities are missing.
- Bias & Deception Risks: Potential bias in threat reporting due to reliance on vendor-provided information; possibility of misinformation or exaggeration by threat actors to create panic.
4. Implications and Strategic Risks
The exploitation of these vulnerabilities could lead to significant data breaches and unauthorized access to critical systems, impacting national security and economic stability. Over time, this could erode trust in digital infrastructure and lead to increased regulatory scrutiny.
- Political / Geopolitical: Potential for increased tensions with nations suspected of harboring or sponsoring cyber actors exploiting these vulnerabilities.
- Security / Counter-Terrorism: Heightened risk of cyber-attacks on critical infrastructure, necessitating increased vigilance and defensive measures.
- Cyber / Information Space: Potential for widespread exploitation leading to data leaks and information warfare tactics.
- Economic / Social: Possible economic disruptions due to compromised business operations and loss of consumer trust.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Federal and private entities should prioritize patching the identified vulnerabilities and enhance monitoring for signs of exploitation.
- Medium-Term Posture (1–12 months): Develop partnerships for threat intelligence sharing and invest in cybersecurity resilience measures.
- Scenario Outlook:
- Best: Rapid patching and defensive measures prevent significant exploitation, maintaining system integrity.
- Worst: Widespread exploitation leads to major data breaches and operational disruptions.
- Most-Likely: Some exploitation occurs, but timely remediation mitigates major impacts.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, vulnerabilities, CISA, network security, threat intelligence, software flaws, federal agencies
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us