CISA mandates federal agencies to address critical BeyondTrust vulnerability within three days
Published on: 2026-02-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: CISA gives feds 3 days to patch actively exploited BeyondTrust flaw
1. BLUF (Bottom Line Up Front)
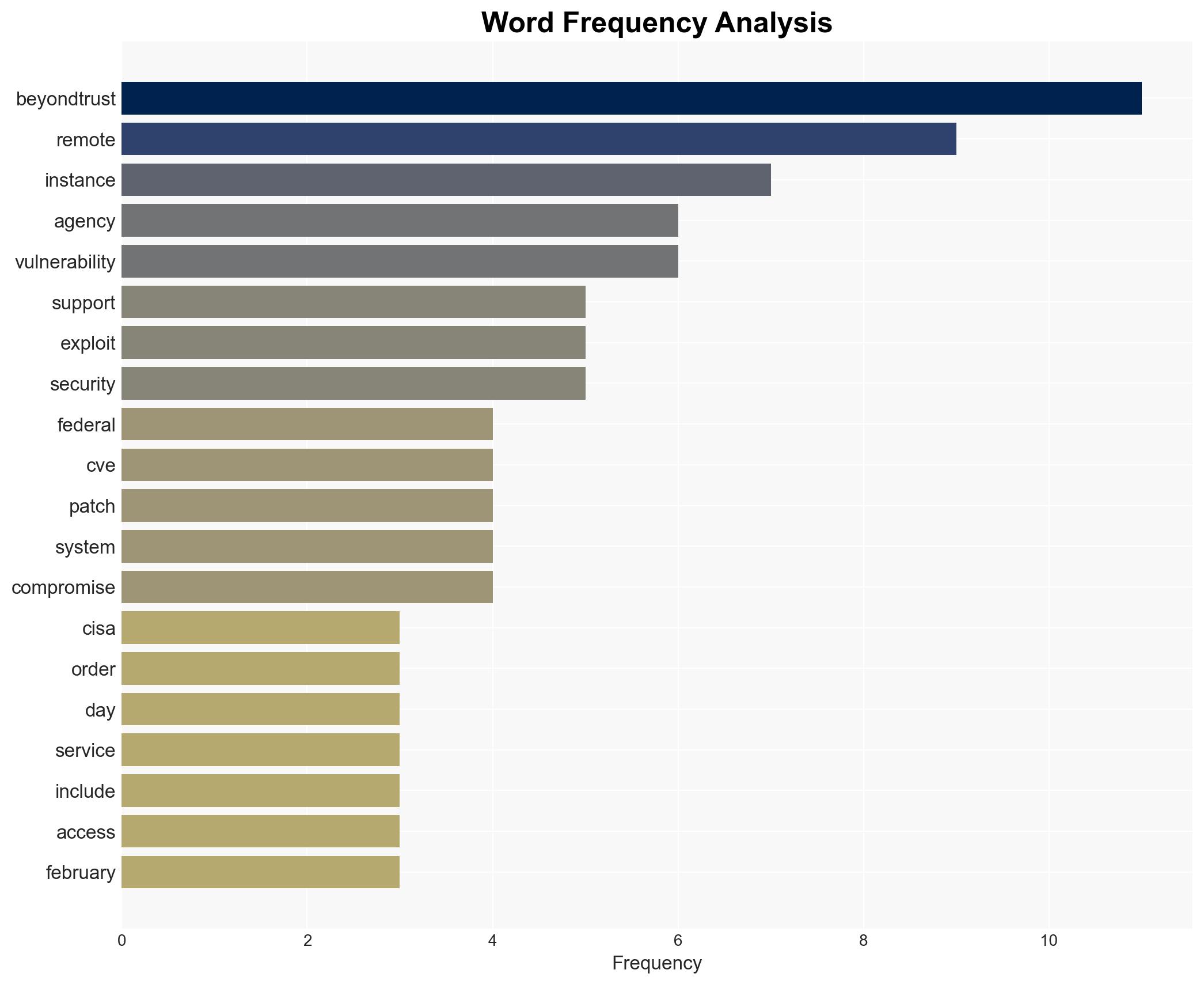
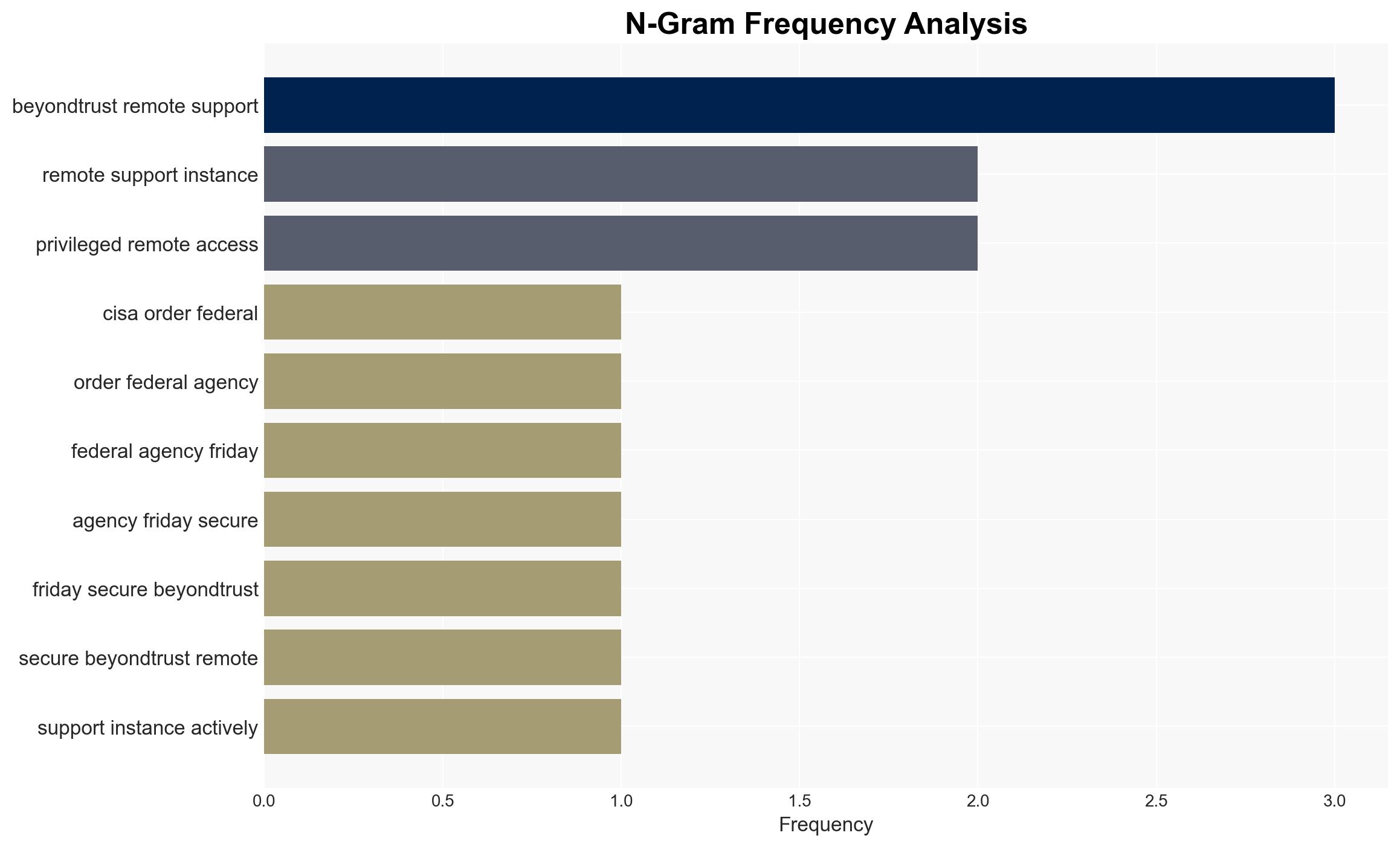
The Cybersecurity and Infrastructure Security Agency (CISA) has mandated federal agencies to patch a critical vulnerability in BeyondTrust software within three days due to active exploitation. This vulnerability poses significant risks to federal systems and potentially affects a wide range of organizations globally. The most likely hypothesis is that state-sponsored actors are exploiting this flaw to gain unauthorized access to sensitive systems. Overall confidence in this assessment is moderate, given the current evidence and historical context.
2. Competing Hypotheses
- Hypothesis A: State-sponsored actors, such as those linked to the Silk Typhoon group, are exploiting the BeyondTrust vulnerability to conduct cyber-espionage. This is supported by historical incidents involving BeyondTrust vulnerabilities and the strategic value of targeting federal systems. However, specific attribution to a state actor remains uncertain.
- Hypothesis B: Independent cybercriminal groups are exploiting the vulnerability for financial gain, such as through ransomware or data exfiltration. While this is plausible given the widespread exposure of the vulnerability, there is less direct evidence linking current exploitation to financially motivated actors.
- Assessment: Hypothesis A is currently better supported due to the strategic nature of the targets and historical precedent of state-sponsored exploitation of similar vulnerabilities. Indicators that could shift this judgment include evidence of financial transactions or communications linked to known cybercriminal groups.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerability remains unpatched in a significant number of systems; state-sponsored actors prioritize federal targets; BeyondTrust’s patching process is effective for SaaS but slower for on-premise deployments.
- Information Gaps: Specific attribution of current exploitation activities; detailed impact assessments of compromised systems; effectiveness of patch deployment across all affected entities.
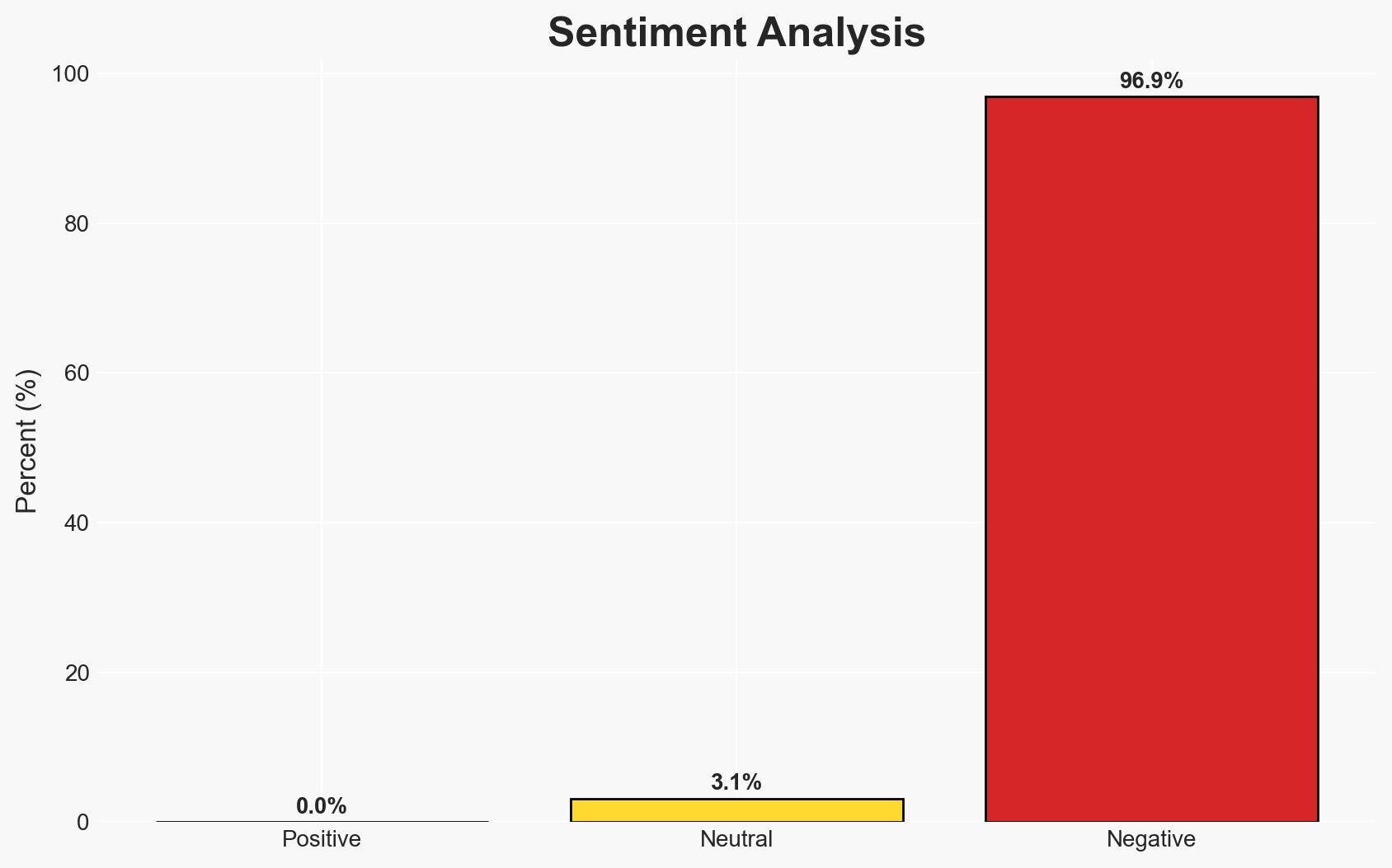
- Bias & Deception Risks: Potential over-reliance on historical patterns of state-sponsored activity; confirmation bias in attributing attacks to known actors without conclusive evidence; possible underreporting of successful patching efforts.
4. Implications and Strategic Risks
This development could lead to increased tensions between the U.S. and suspected state actors, particularly if attribution is confirmed. It may also prompt a reassessment of cybersecurity protocols and vendor relationships across federal agencies.
- Political / Geopolitical: Potential diplomatic fallout if state-sponsored attribution is confirmed, leading to sanctions or retaliatory measures.
- Security / Counter-Terrorism: Heightened alert levels and resource allocation towards cyber defense; potential for increased cyber threat activity targeting other critical infrastructure.
- Cyber / Information Space: Increased scrutiny on cybersecurity practices and vendor software vulnerabilities; potential for misinformation campaigns exploiting the incident.
- Economic / Social: Potential financial impact on BeyondTrust and its customers; broader implications for trust in cybersecurity vendors.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Ensure all federal agencies comply with CISA’s patching directive; enhance monitoring of BeyondTrust systems for signs of compromise; engage with BeyondTrust for additional support and guidance.
- Medium-Term Posture (1–12 months): Strengthen partnerships with cybersecurity vendors to improve vulnerability management; invest in training and awareness programs for federal IT staff; consider diversification of cybersecurity tools and vendors.
- Scenario Outlook:
- Best Case: Rapid patch deployment mitigates immediate threats, and no significant breaches occur.
- Worst Case: Widespread exploitation leads to significant data breaches and operational disruptions.
- Most-Likely: Some breaches occur, but are contained with minimal long-term impact, leading to improved cybersecurity practices.
6. Key Individuals and Entities
- BeyondTrust
- CISA (Cybersecurity and Infrastructure Security Agency)
- Silk Typhoon (Chinese state-backed cyberespionage group)
- Ryan Dewhurst (watchTowr head of threat intelligence)
- Hacktron (vulnerability discoverer)
7. Thematic Tags
cybersecurity, state-sponsored threats, vulnerability management, federal agencies, BeyondTrust, cyber-espionage, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us