CISA mandates federal agencies to address critical Gogs vulnerability or discontinue its use immediately
Published on: 2026-01-13
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Federal agencies told to fix or ditch Gogs as exploited zero-day lands on CISA hit list
1. BLUF (Bottom Line Up Front)
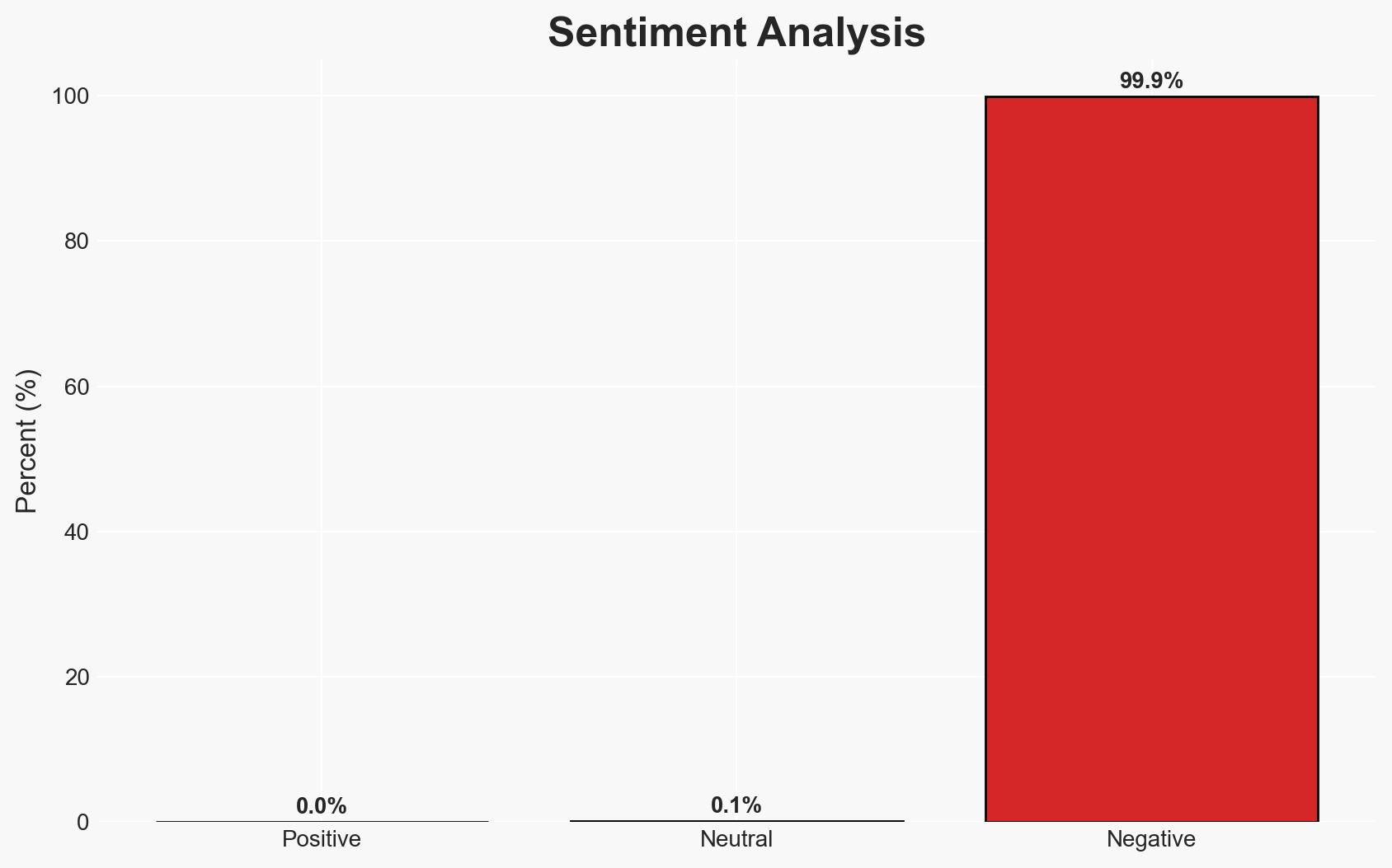
A high-severity vulnerability in the Gogs Git service has been added to CISA’s Known Exploited Vulnerabilities list, prompting federal agencies to either secure or discontinue its use. The vulnerability is actively exploited, posing significant risks to federal systems. The most likely hypothesis is that the attacks are opportunistic rather than state-sponsored, with moderate confidence due to limited attribution data.
2. Competing Hypotheses
- Hypothesis A: The exploitation of the Gogs vulnerability is primarily conducted by opportunistic cybercriminals seeking to exploit easy targets. This is supported by the lack of specific attribution and the widespread nature of the attacks. However, the absence of detailed threat actor profiles introduces uncertainty.
- Hypothesis B: The attacks are orchestrated by a state-sponsored group, potentially from Asia, exploiting the vulnerability for strategic gains. This hypothesis is supported by the use of Supershell C2, which may indicate a higher level of sophistication, but lacks direct evidence linking it to state actors.
- Assessment: Hypothesis A is currently better supported due to the broad and opportunistic nature of the attacks and the absence of concrete attribution to state actors. Key indicators that could shift this judgment include credible attribution to a specific group or evidence of targeted attacks against strategic assets.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerability remains unpatched, Gogs instances are widely exposed, and threat actors are leveraging the flaw for remote code execution.
- Information Gaps: Specific threat actor attribution, detailed impact assessments on federal systems, and the timeline for a permanent fix from Gogs.
- Bias & Deception Risks: Potential over-reliance on open-source threat intelligence, which may be incomplete or biased. Risk of misattribution due to shared tools among different threat actors.
4. Implications and Strategic Risks
The ongoing exploitation of the Gogs vulnerability could lead to significant disruptions in federal operations and compromise sensitive data. The situation may evolve with broader implications for cybersecurity practices and international cyber norms.
- Political / Geopolitical: Increased tensions if state-sponsored involvement is confirmed, potentially affecting diplomatic relations.
- Security / Counter-Terrorism: Heightened alert levels and resource allocation to mitigate potential breaches in federal systems.
- Cyber / Information Space: Potential for increased cyber espionage activities and information leaks, undermining trust in digital infrastructure.
- Economic / Social: Possible economic impacts due to increased cybersecurity spending and potential disruptions to critical services.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Federal agencies should implement CISA’s mitigation strategies, enhance monitoring of Gogs instances, and prepare incident response plans.
- Medium-Term Posture (1–12 months): Develop partnerships for threat intelligence sharing, invest in cybersecurity training, and advocate for timely patch management practices.
- Scenario Outlook:
- Best: Rapid patch deployment by Gogs and effective mitigation by agencies prevent further exploitation.
- Worst: Prolonged exploitation leads to significant data breaches and operational disruptions.
- Most-Likely: Continued opportunistic attacks with gradual improvements in security posture as mitigations are applied.
6. Key Individuals and Entities
- Wiz Security Researchers
- CISA (Cybersecurity and Infrastructure Security Agency)
- Federal Civilian Executive Branch (FCEB) Agencies
- Gogs Developers
- Yaara Shriki (Wiz Researcher)
7. Thematic Tags
cybersecurity, zero-day vulnerability, federal agencies, threat mitigation, cyber-espionage, information security, vulnerability management
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us