CISA mandates federal agencies to address critical MongoDB vulnerability amid active exploitation threats
Published on: 2025-12-30
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: CISA orders feds to patch MongoBleed flaw exploited in attacks
1. BLUF (Bottom Line Up Front)
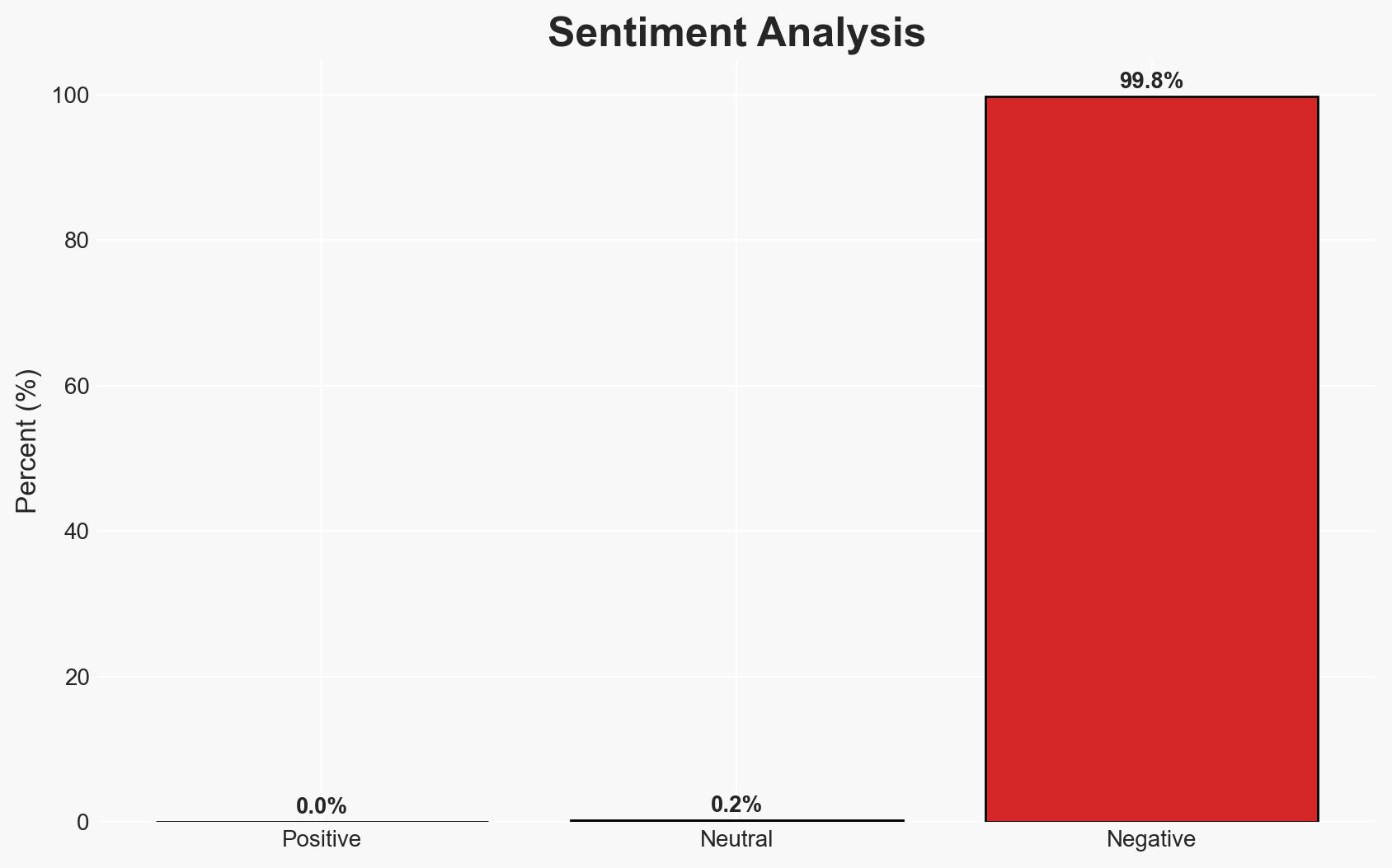
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has mandated federal agencies to address the MongoBleed vulnerability (CVE-2025-14847) due to its active exploitation, posing significant risks to sensitive data. The vulnerability affects a substantial portion of cloud environments, with 42% of systems potentially exposed. Immediate patching is required to mitigate risks. Overall confidence in this assessment is moderate, given the current data.
2. Competing Hypotheses
- Hypothesis A: The MongoBleed vulnerability is primarily being exploited by opportunistic cybercriminals seeking financial gain through data theft. This is supported by the low complexity of the attack and the availability of a proof-of-concept exploit. However, the specific actors exploiting the vulnerability remain unidentified, creating uncertainty.
- Hypothesis B: State-sponsored actors are exploiting the MongoBleed vulnerability to gather intelligence on U.S. federal agencies. This hypothesis is less supported due to the lack of direct evidence linking state actors to the exploitation activities, although the strategic value of the data could attract such interests.
- Assessment: Hypothesis A is currently better supported due to the nature of the exploit and the typical behavior of cybercriminals targeting exposed systems. Indicators such as attribution to known state actors or strategic targeting patterns could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerability is being actively exploited by multiple actors; patching will effectively mitigate immediate risks; the data exposed is of high value to threat actors.
- Information Gaps: Specific attribution of the threat actors exploiting the vulnerability; detailed impact assessment on compromised systems; effectiveness of mitigation measures post-patching.
- Bias & Deception Risks: Potential bias in overestimating the threat due to the high-profile nature of the vulnerability; reliance on vendor-provided data which may not be fully transparent.
4. Implications and Strategic Risks
The exploitation of the MongoBleed vulnerability could lead to significant data breaches, impacting national security and public trust in government cybersecurity measures. The situation may evolve with increased exploitation attempts or discovery of additional vulnerabilities.
- Political / Geopolitical: Potential diplomatic tensions if state-sponsored exploitation is confirmed; increased scrutiny on U.S. cybersecurity posture.
- Security / Counter-Terrorism: Enhanced threat landscape requiring increased vigilance and resource allocation for cybersecurity defenses.
- Cyber / Information Space: Potential for increased cyber operations targeting similar vulnerabilities; heightened awareness and patching activities across the sector.
- Economic / Social: Potential economic impact on organizations relying on MongoDB; public concern over data privacy and security.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Ensure all federal agencies comply with CISA’s patching directive; monitor for signs of exploitation; engage with MongoDB for additional support and guidance.
- Medium-Term Posture (1–12 months): Develop enhanced monitoring capabilities for emerging vulnerabilities; strengthen partnerships with cloud service providers for rapid response capabilities.
- Scenario Outlook:
- Best Case: Rapid patching mitigates immediate threats, and no significant breaches occur.
- Worst Case: Widespread exploitation leads to significant data breaches and operational disruptions.
- Most-Likely: Continued exploitation attempts with varying success, leading to increased cybersecurity measures and awareness.
6. Key Individuals and Entities
- U.S. Cybersecurity and Infrastructure Security Agency (CISA)
- Joe Desimone, Elastic security researcher
- Shadowserver
- Censys
- Wiz, cloud security platform
- MongoDB
7. Thematic Tags
cybersecurity, vulnerability management, federal agencies, data breach, cloud security, MongoDB, cybercrime
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us