CISA Orders Immediate Patch of Critical Sitecore Vulnerability Under Active Exploitation – Internet
Published on: 2025-09-05
Intelligence Report: CISA Orders Immediate Patch of Critical Sitecore Vulnerability Under Active Exploitation – Internet
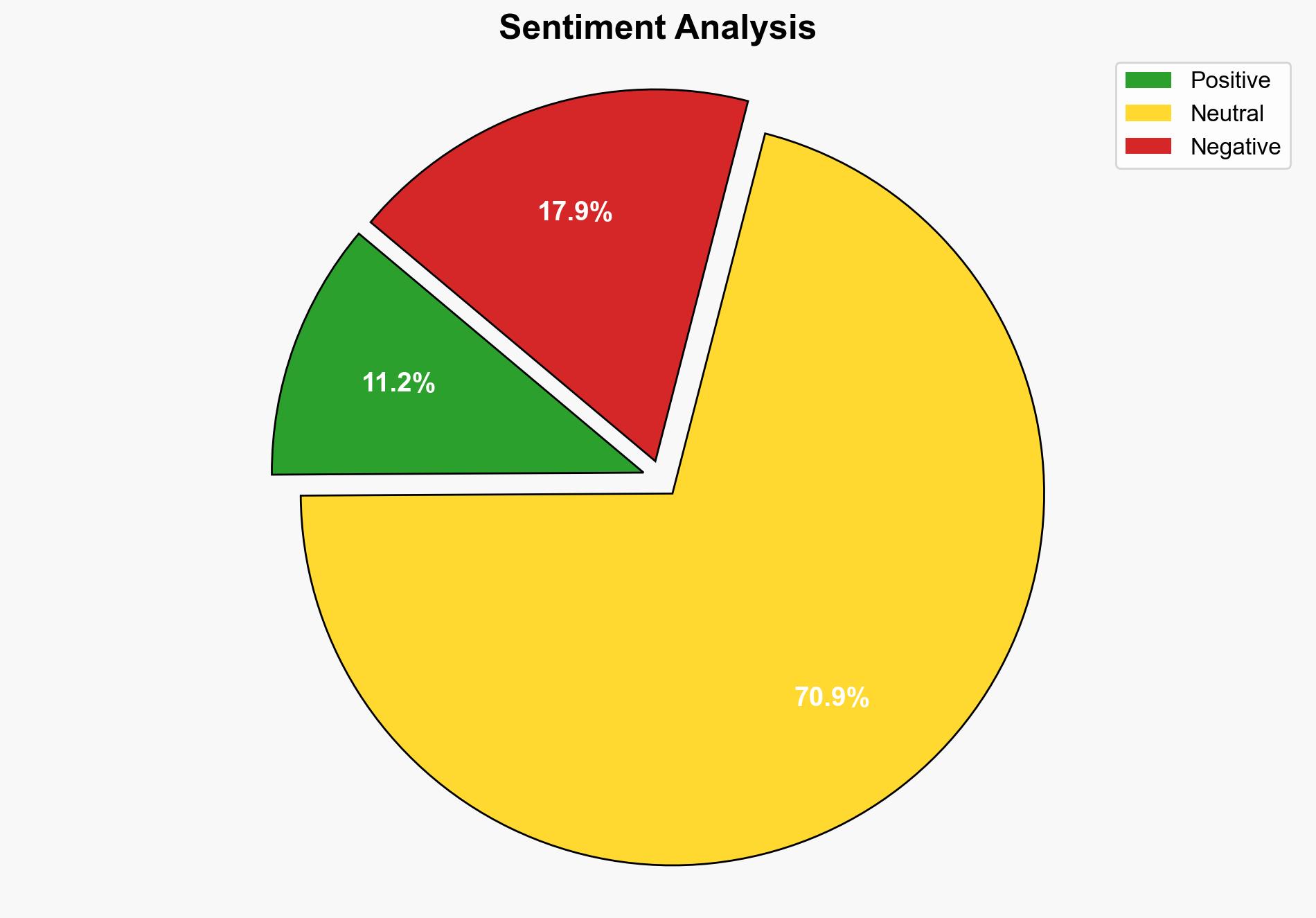
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that a sophisticated threat actor group is actively exploiting the Sitecore vulnerability to gain unauthorized access and conduct extensive reconnaissance within affected networks. This assessment is made with a high confidence level due to the observed patterns of exploitation and the involvement of known threat actors. Immediate patching of the vulnerability and enhanced monitoring for lateral movement within networks are recommended actions.
2. Competing Hypotheses
1. **Hypothesis A**: A nation-state threat actor is exploiting the Sitecore vulnerability to conduct espionage and data theft operations, leveraging advanced techniques for privilege escalation and lateral movement.
2. **Hypothesis B**: Cybercriminal groups are exploiting the vulnerability primarily for financial gain, including selling access to compromised networks and deploying ransomware.
Using ACH 2.0, Hypothesis A is better supported due to the complexity of the attack methods, the involvement of known threat actor groups, and the strategic nature of the targets. Hypothesis B is less supported as there is limited evidence of financial motivations or ransomware deployment in the current exploitation pattern.
3. Key Assumptions and Red Flags
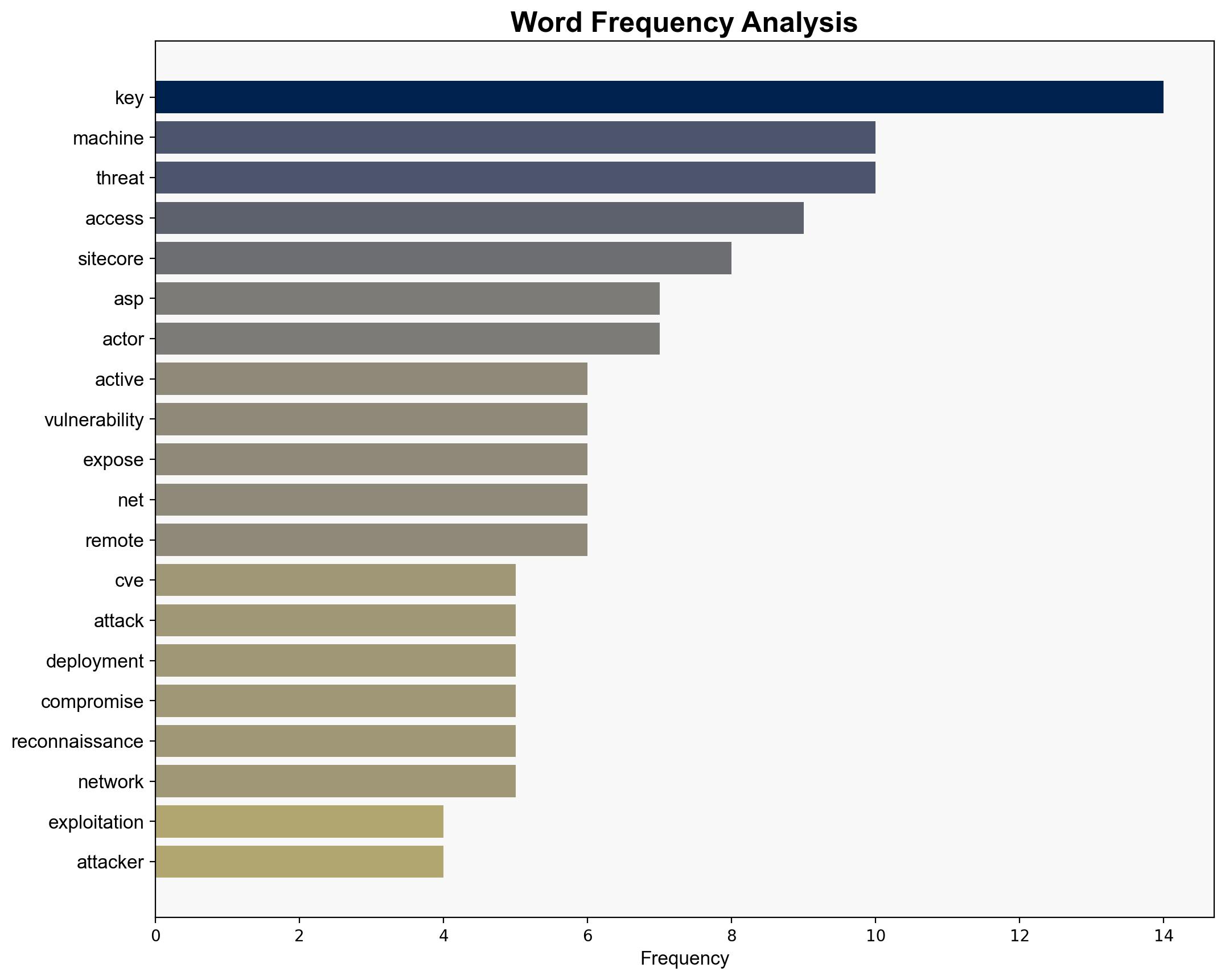
– **Assumptions**: It is assumed that the threat actors have deep technical knowledge of Sitecore and ASP.NET vulnerabilities. It is also assumed that the observed activities are indicative of broader campaigns.
– **Red Flags**: The lack of detailed attribution to specific nation-states or criminal groups raises questions about the full scope of the threat. The possibility of undisclosed vulnerabilities being exploited concurrently is a concern.
– **Blind Spots**: Limited visibility into the internal network activities post-compromise could obscure the full extent of the threat actor’s objectives.
4. Implications and Strategic Risks
The exploitation of the Sitecore vulnerability poses significant risks, including potential data breaches, intellectual property theft, and disruption of critical infrastructure. The involvement of nation-state actors suggests a potential escalation into broader cyber warfare tactics. The economic impact could be severe if sensitive data is exfiltrated or if operations are disrupted.
5. Recommendations and Outlook
- **Immediate Action**: Patch all vulnerable Sitecore instances and review network security configurations to prevent unauthorized access.
- **Enhanced Monitoring**: Implement advanced threat detection mechanisms to identify lateral movement and privilege escalation attempts.
- **Scenario Projections**:
– **Best Case**: Rapid patch deployment and enhanced security measures prevent further exploitation, minimizing impact.
– **Worst Case**: Unpatched systems lead to widespread data breaches and operational disruptions, with significant economic and reputational damage.
– **Most Likely**: Continued exploitation attempts with varying success, leading to isolated incidents of data theft and network compromise.
6. Key Individuals and Entities
– Rommel Joven, Josh Fleischer, Joseph Sciuto, Andi Slok Choon Kiat Ng: Researchers involved in identifying and analyzing the exploitation patterns.
– Google Mandiant: Organization that discovered the active exploitation.
– Gold Melody: Initial access broker attributed to exploiting the vulnerability.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus