CISA Retires Ten Emergency Directives, Citing Redundancy and Successful Implementation Under BOD 22-01
Published on: 2026-01-09
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: 10 emergency directives retired as CISA declares them redundant
1. BLUF (Bottom Line Up Front)
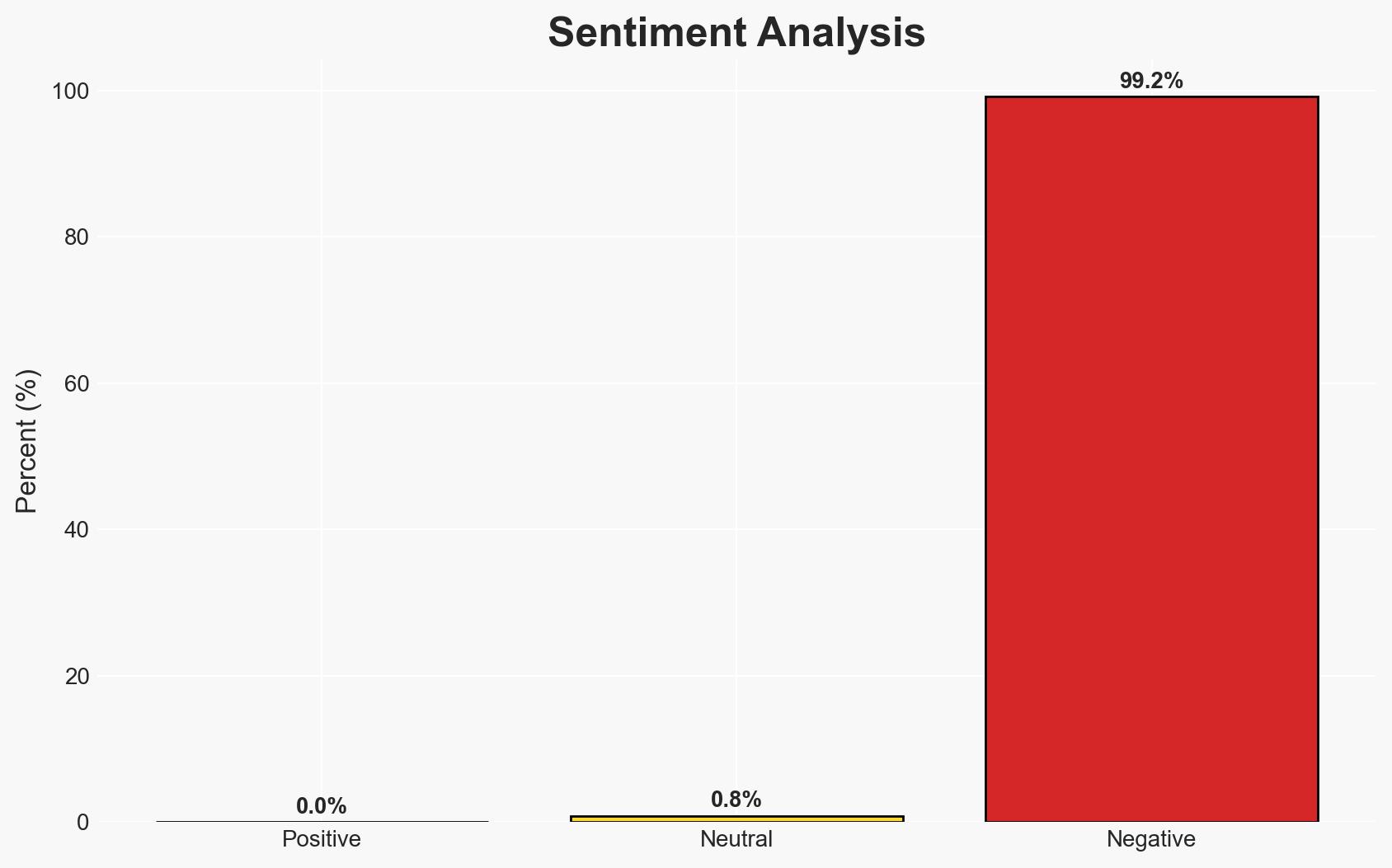
The Cybersecurity and Infrastructure Security Agency (CISA) has retired ten Emergency Directives (EDs), citing their redundancy under Binding Operational Directive (BOD) 22-01. This action reflects a strategic shift towards a more streamlined vulnerability management approach. The decision primarily affects federal agencies, enhancing their focus on known exploited vulnerabilities (KEVs). Overall, this assessment is made with moderate confidence.
2. Competing Hypotheses
- Hypothesis A: The retirement of the EDs is a result of successful implementation and redundancy due to BOD 22-01, indicating improved federal cybersecurity posture. Supporting evidence includes CISA’s statement on successful implementation and redundancy. Key uncertainties include the completeness of implementation across all agencies.
- Hypothesis B: The retirement may be a strategic move to reduce administrative overhead and focus resources on more critical vulnerabilities, regardless of actual implementation success. This is supported by the emphasis on streamlining efforts and the largest simultaneous ED retirement. Contradicting evidence is the lack of specific details on implementation success rates.
- Assessment: Hypothesis A is currently better supported due to CISA’s explicit statements regarding successful implementation and redundancy. Indicators that could shift this judgment include reports of unaddressed vulnerabilities or increased cyber incidents.
3. Key Assumptions and Red Flags
- Assumptions: CISA’s directives are effectively enforced across all federal agencies; BOD 22-01 adequately covers the vulnerabilities addressed by the retired EDs; Federal agencies have the capability to meet BOD 22-01 requirements.
- Information Gaps: Specific data on the implementation status of the retired EDs across all agencies; Detailed metrics on the effectiveness of BOD 22-01 in reducing vulnerabilities.
- Bias & Deception Risks: Potential for confirmation bias in accepting CISA’s statements without independent verification; Risk of source bias as the information is primarily from CISA’s announcement.
4. Implications and Strategic Risks
The retirement of the EDs could streamline federal cybersecurity efforts but may also mask underlying vulnerabilities if not all agencies are compliant with BOD 22-01. This development could influence broader cybersecurity strategies and resource allocations.
- Political / Geopolitical: May enhance US cybersecurity posture, potentially affecting international cyber norms and cooperation.
- Security / Counter-Terrorism: Could reduce the attack surface for cyber threats, but risks remain if vulnerabilities are not fully addressed.
- Cyber / Information Space: Streamlining directives may improve response times and focus on critical vulnerabilities, but also risks complacency if oversight is reduced.
- Economic / Social: Improved cybersecurity could bolster economic stability by reducing potential cyber disruptions.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor compliance with BOD 22-01 across federal agencies; Verify the closure of vulnerabilities previously addressed by the retired EDs.
- Medium-Term Posture (1–12 months): Develop resilience measures to ensure continuous improvement in vulnerability management; Strengthen partnerships with private sector for threat intelligence sharing.
- Scenario Outlook: Best: Full compliance with BOD 22-01 leads to reduced cyber incidents. Worst: Non-compliance results in significant breaches. Most-Likely: Gradual improvement in cybersecurity posture with occasional setbacks.
6. Key Individuals and Entities
- Madhu Gottumukkala, Acting Director, CISA
- Federal Civilian Executive Branch Agencies (FCEB)
7. Thematic Tags
cybersecurity, federal agencies, vulnerability management, CISA, emergency directives, BOD 22-01, cyber risk reduction
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us