CISA Warns of CrushFTP Vulnerability Exploitation in the Wild – Infosecurity Magazine
Published on: 2025-04-08
Intelligence Report: CISA Warns of CrushFTP Vulnerability Exploitation in the Wild – Infosecurity Magazine
1. BLUF (Bottom Line Up Front)
The cybersecurity agency has confirmed a critical vulnerability in CrushFTP’s product, which is being actively exploited. This vulnerability allows unauthenticated actors to bypass authentication, posing a significant risk to federal enterprises. Immediate remediation is strongly advised to mitigate potential security breaches.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
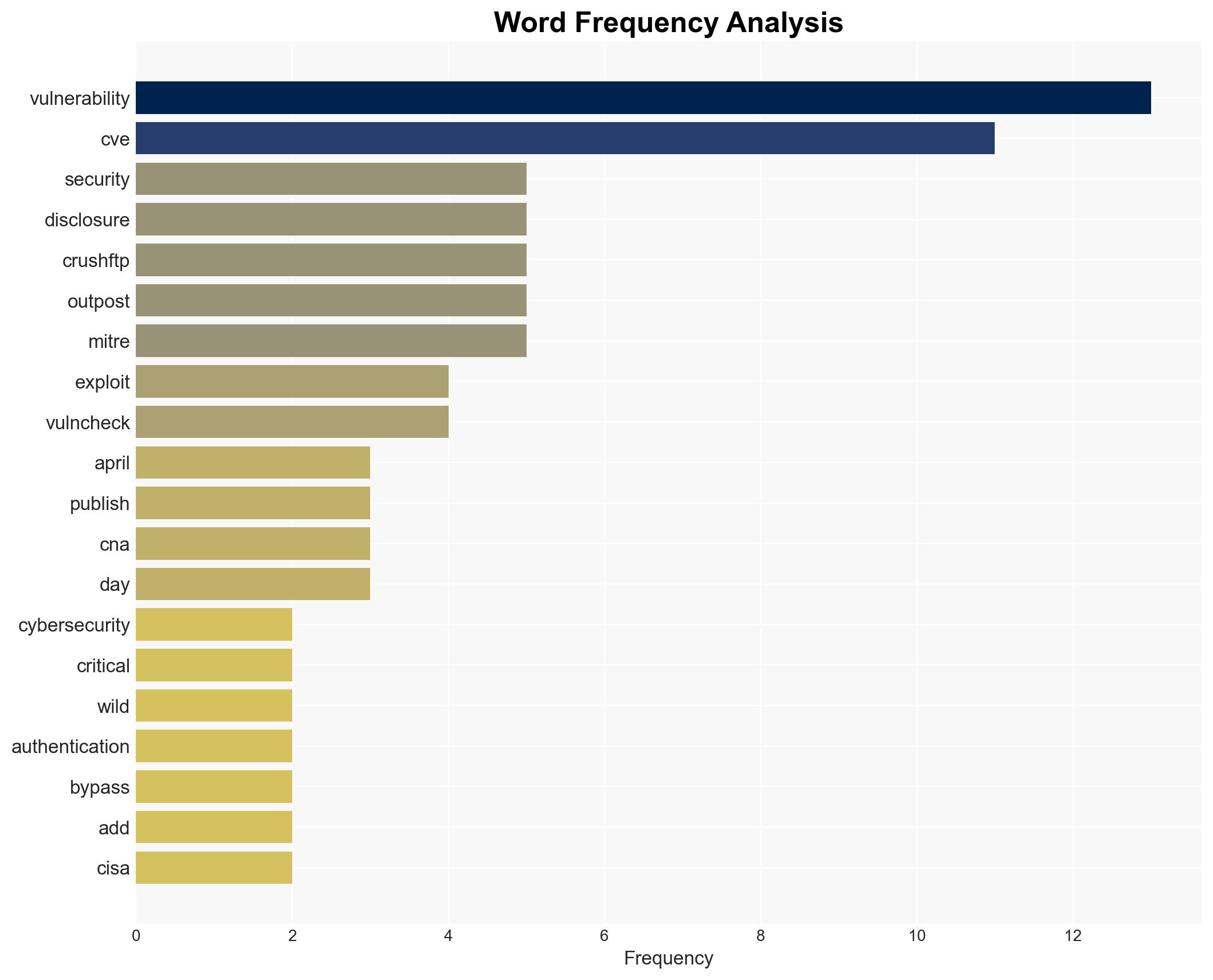
The vulnerability in CrushFTP, identified as CVE, allows unauthenticated access to systems running unpatched versions of the software. This has been included in the Known Exploited Vulnerabilities (KEV) catalog by the cybersecurity agency. The vulnerability was disclosed by Outpost and coordinated with Mitre, but there was a delay in public disclosure, leading to active exploitation. The Shadowserver Foundation has observed exploitation attempts, and the vulnerability is now widely known due to public proof-of-concept exploit code.
3. Implications and Strategic Risks
The exploitation of this vulnerability poses significant risks to national security, particularly for federal departments and organizations. The potential for unauthorized access to sensitive information could lead to data breaches, economic losses, and damage to public trust. The delay in public disclosure and the rejection of the CVE by Mitre have also raised concerns about the vulnerability management process.
4. Recommendations and Outlook
Recommendations:
- Federal departments and organizations should prioritize patching the vulnerability in CrushFTP immediately.
- Enhance vulnerability management practices to ensure timely disclosure and remediation of critical vulnerabilities.
- Consider regulatory measures to improve transparency and accountability in vulnerability disclosure processes.
Outlook:
In the best-case scenario, rapid patching and improved vulnerability management will mitigate the risk of exploitation. In the worst-case scenario, continued exploitation could lead to significant data breaches and economic losses. The most likely outcome is a moderate level of exploitation until patches are widely implemented.
5. Key Individuals and Entities
The report mentions several significant individuals and organizations, including Patrick Garrity, Outpost, Mitre, Shadowserver Foundation, and VulnCheck. These entities have played a role in the identification, disclosure, and analysis of the CrushFTP vulnerability.