CISA warns of Windows SMB flaw under active exploitation CVE-2025-33073 – Help Net Security
Published on: 2025-10-21
Intelligence Report: CISA warns of Windows SMB flaw under active exploitation CVE-2025-33073 – Help Net Security
1. BLUF (Bottom Line Up Front)
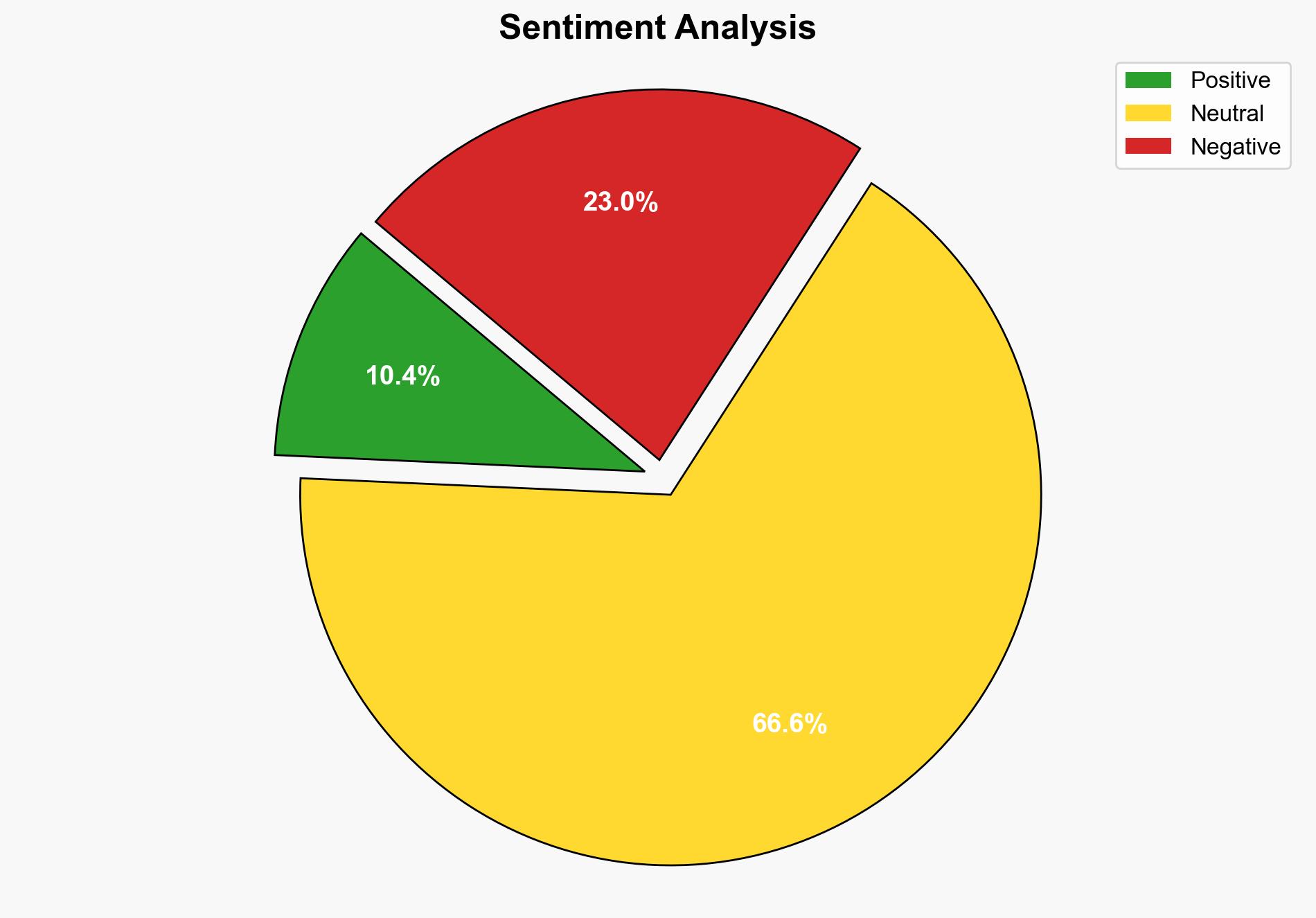
The most supported hypothesis is that the CVE-2025-33073 vulnerability is being actively exploited by cybercriminals to gain unauthorized access to systems, posing a significant cybersecurity threat. Confidence level is high due to credible sources and technical details provided by researchers. Immediate patching and enhanced monitoring are recommended actions.
2. Competing Hypotheses
Hypothesis 1: The CVE-2025-33073 vulnerability is primarily being exploited by cybercriminals for financial gain through unauthorized access and data theft. This is supported by the active exploitation status and the nature of privilege escalation vulnerabilities, which are often leveraged for such purposes.
Hypothesis 2: The vulnerability is being exploited by state-sponsored actors for espionage purposes, targeting specific organizations or government entities. This hypothesis considers the involvement of sophisticated actors capable of bypassing NTLM reflection mitigation and executing remote commands.
Using ACH 2.0, Hypothesis 1 is better supported as the immediate financial incentives align with the typical exploitation patterns of similar vulnerabilities. The lack of specific attribution to state actors in the report weakens Hypothesis 2.
3. Key Assumptions and Red Flags
– Assumption: The vulnerability is being exploited primarily for financial gain, not espionage.
– Red Flag: Lack of detailed attribution to specific threat actors or groups.
– Potential Bias: Confirmation bias towards cybercriminal activity due to historical patterns.
– Missing Data: Specific targets or sectors affected by the exploitation are not mentioned.
4. Implications and Strategic Risks
The exploitation of CVE-2025-33073 could lead to significant data breaches, financial losses, and reputational damage for affected organizations. There is a risk of cascading effects if the vulnerability is used to compromise critical infrastructure or supply chains. The geopolitical dimension includes potential escalation if state actors are involved, impacting international relations and cybersecurity policies.
5. Recommendations and Outlook
- Organizations should immediately apply the Microsoft patch to mitigate the vulnerability.
- Enhance network monitoring for unusual SMB traffic and unauthorized access attempts.
- Conduct regular security audits and employee training to prevent exploitation.
- Scenario Projections:
- Best Case: Rapid patch adoption minimizes exploitation impact.
- Worst Case: Widespread exploitation leads to major data breaches and financial losses.
- Most Likely: Continued exploitation by cybercriminals with moderate impact on unpatched systems.
6. Key Individuals and Entities
– Keisuke Hirata
– Wilfrie Bcard
– Cameron Stish
– Ahamada Mbamba
– Stefan Walter
– Daniel Isern
– James Forshaw
– Guillaume André
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus