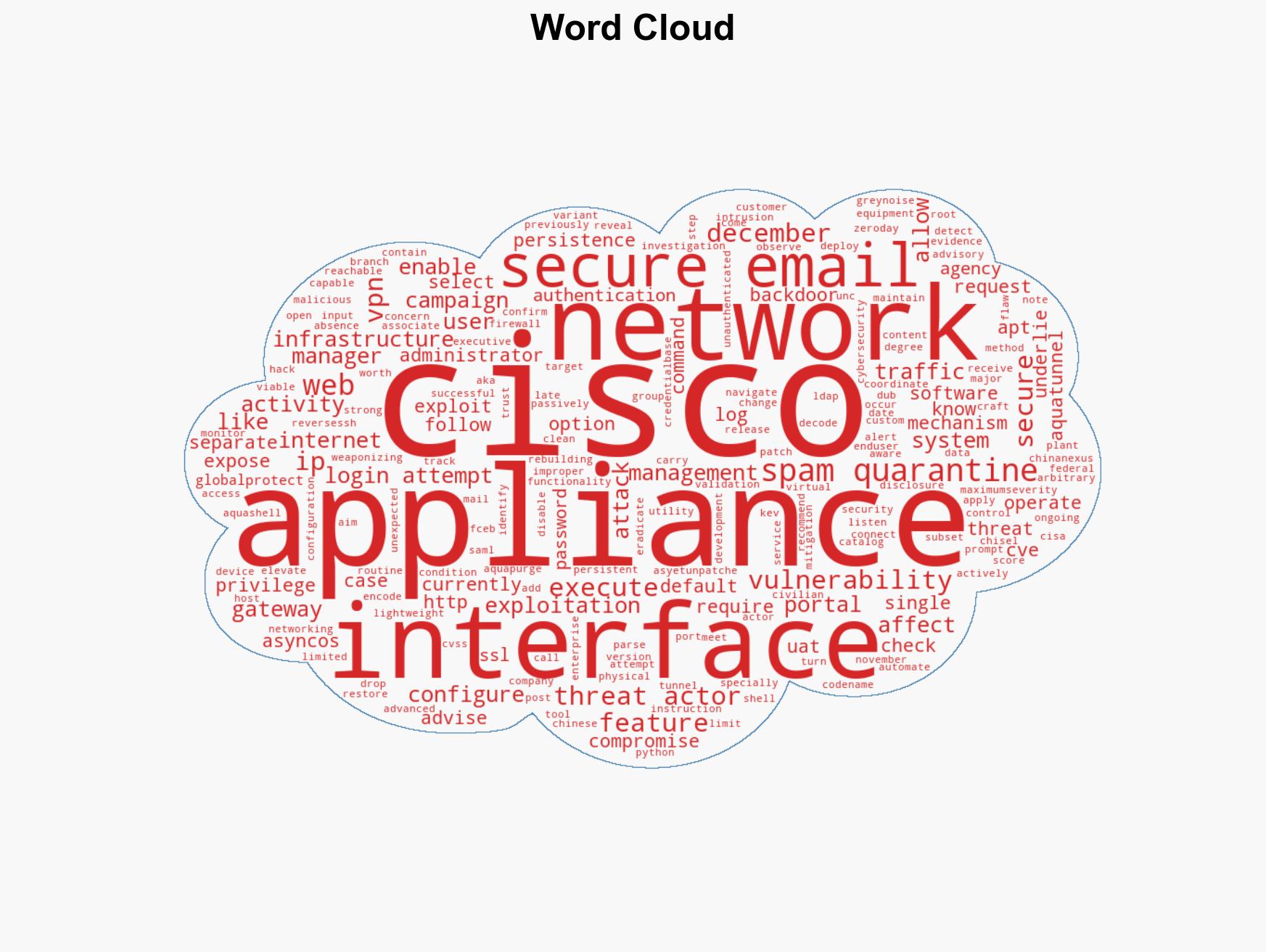
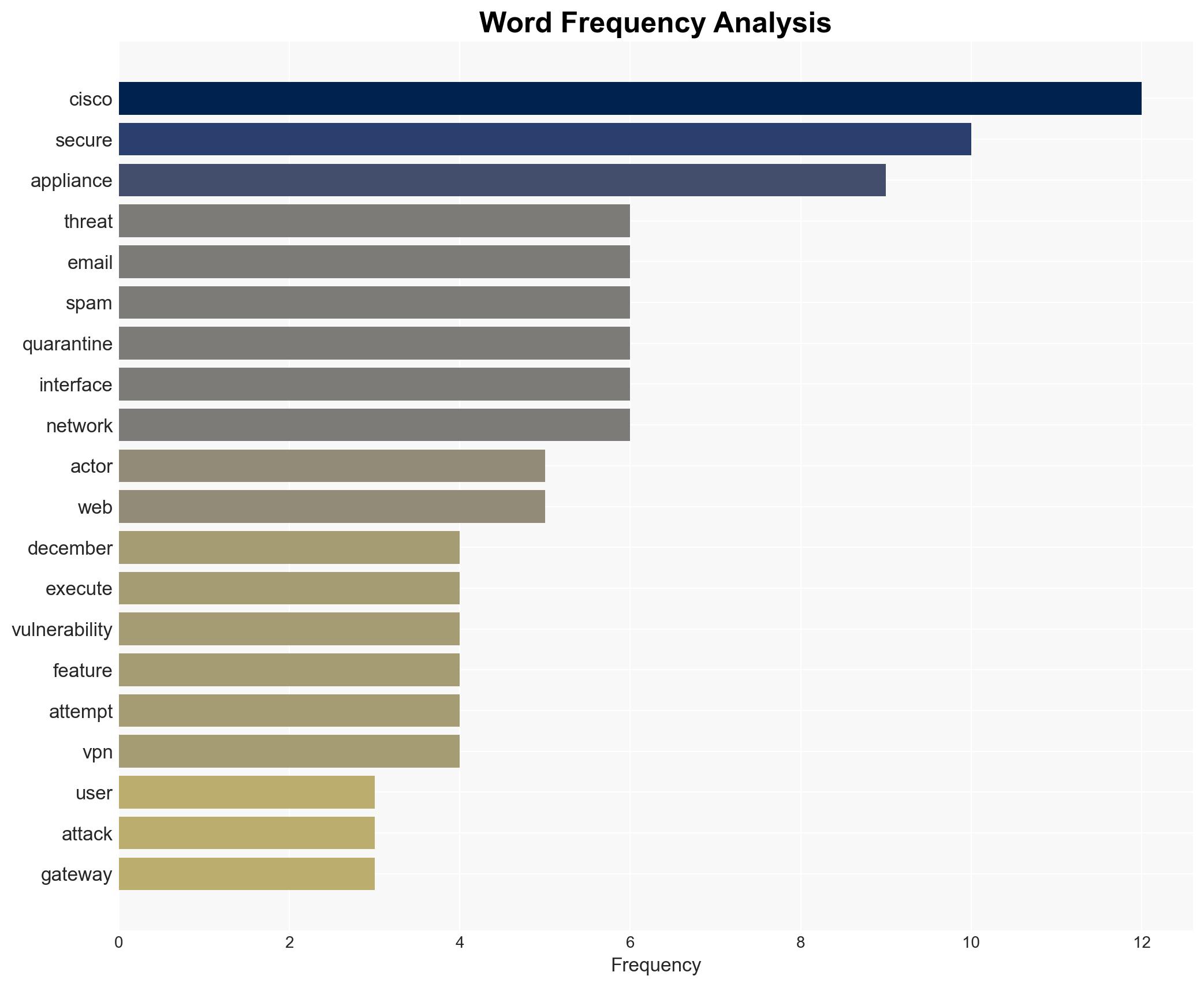
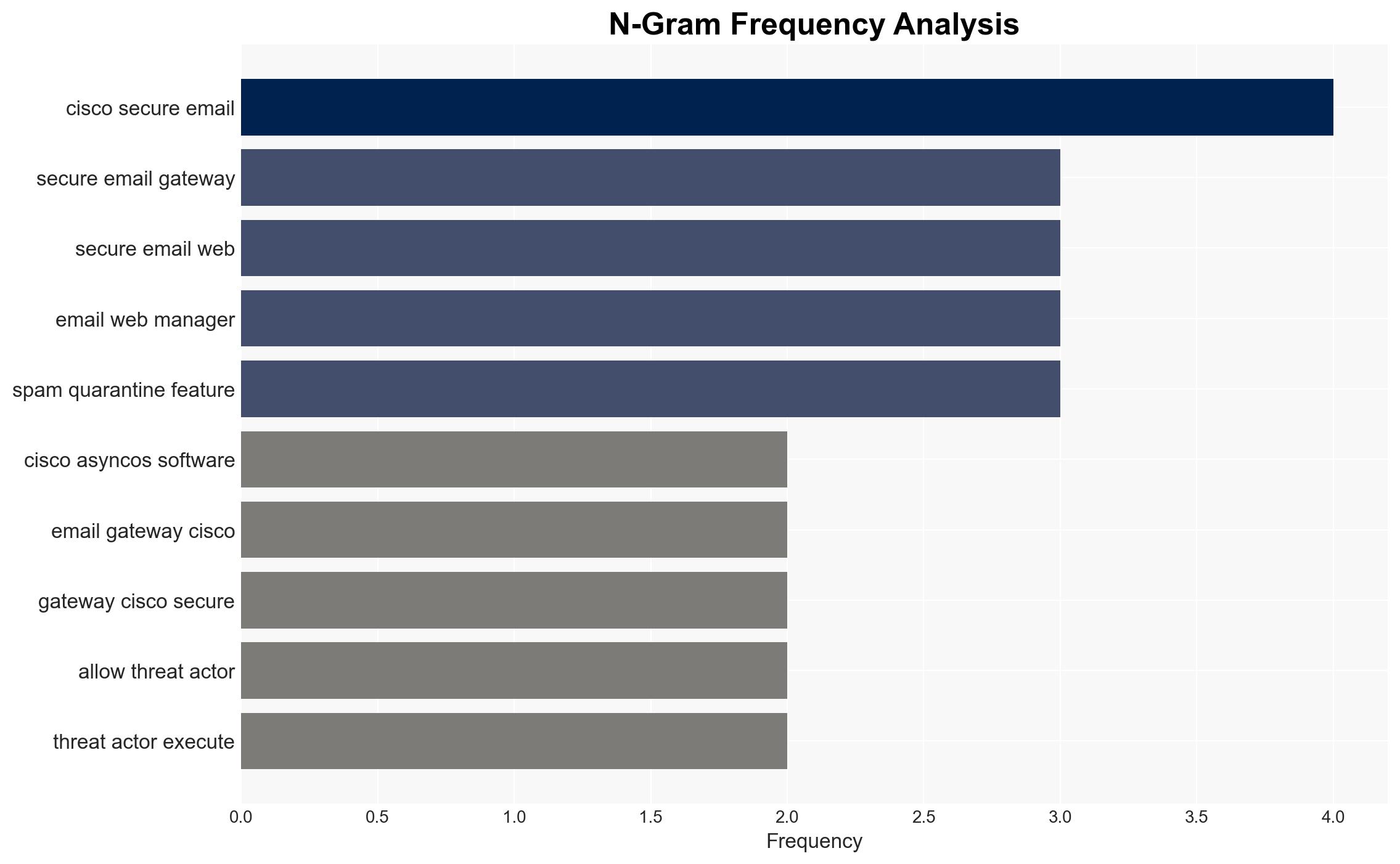
Cisco Alerts Users to Critical Zero-Day Exploit in AsyncOS Targeting Email Security Appliances
Published on: 2025-12-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Cisco Warns of Active Attacks Exploiting Unpatched 0-Day in AsyncOS Email Security Appliances
1. BLUF (Bottom Line Up Front)
Cisco has identified a zero-day vulnerability in its AsyncOS software, actively exploited by a China-nexus APT group, UAT-9686. This flaw allows for remote command execution on affected email security appliances. The threat is significant due to the high severity of the vulnerability and the potential for persistent access. Moderate confidence in this assessment is due to incomplete data on the scope of affected systems.
2. Competing Hypotheses
- Hypothesis A: The primary objective of UAT-9686 is cyber-espionage, leveraging the vulnerability to gather intelligence from targeted organizations. This is supported by the use of tools associated with known Chinese APTs and the strategic value of email communications. Uncertainty remains regarding the specific targets and data exfiltrated.
- Hypothesis B: The attacks are preparatory steps for future disruptive operations, using the current access to plant additional backdoors or malware. This is less supported due to the absence of evidence indicating destructive payloads or intent beyond maintaining access.
- Assessment: Hypothesis A is currently better supported, given the tools and methods align with espionage activities typical of Chinese APTs. Indicators such as shifts in tool usage or targeting patterns could alter this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerability is primarily exploited by UAT-9686; the scope of affected systems is limited to those with specific configurations; the APT’s objectives align with known Chinese cyber-espionage goals.
- Information Gaps: Exact number of affected systems, specific data targeted, and full list of organizations impacted.
- Bias & Deception Risks: Attribution to UAT-9686 may be influenced by prior associations with similar tools; potential for misdirection by threat actors to obscure true intent or origin.
4. Implications and Strategic Risks
The exploitation of this vulnerability could lead to significant intelligence losses and operational disruptions if not mitigated. The persistence of access suggests ongoing risks to sensitive communications.
- Political / Geopolitical: Potential for increased tensions between affected nations and China, especially if state-sponsored attribution is confirmed.
- Security / Counter-Terrorism: Heightened alert for similar vulnerabilities in other critical infrastructure systems.
- Cyber / Information Space: Increased scrutiny on Cisco’s security posture; potential for copycat attacks exploiting similar vulnerabilities.
- Economic / Social: Potential financial impacts on affected organizations due to data breaches and remediation costs.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urgently apply available mitigations, monitor for indicators of compromise, and engage with Cisco for updates and support.
- Medium-Term Posture (1–12 months): Strengthen partnerships with cybersecurity firms for threat intelligence sharing, and invest in advanced threat detection capabilities.
- Scenario Outlook:
- Best: Rapid patch deployment mitigates threat with minimal impact.
- Worst: Widespread exploitation leads to significant data breaches and geopolitical fallout.
- Most-Likely: Continued exploitation until a patch is released, with moderate impact on affected sectors.
6. Key Individuals and Entities
- UAT-9686 (China-nexus APT group)
- Cisco Systems (Vendor of affected software)
- APT41, UNC5174 (Associated Chinese hacking groups)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, cyber-espionage, zero-day vulnerability, China-nexus APT, Cisco AsyncOS, email security, threat intelligence, cyber defense
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us