Cisco Catalyst Center Virtual Appliance Privilege Escalation Vulnerability – Cisco.com
Published on: 2025-11-13
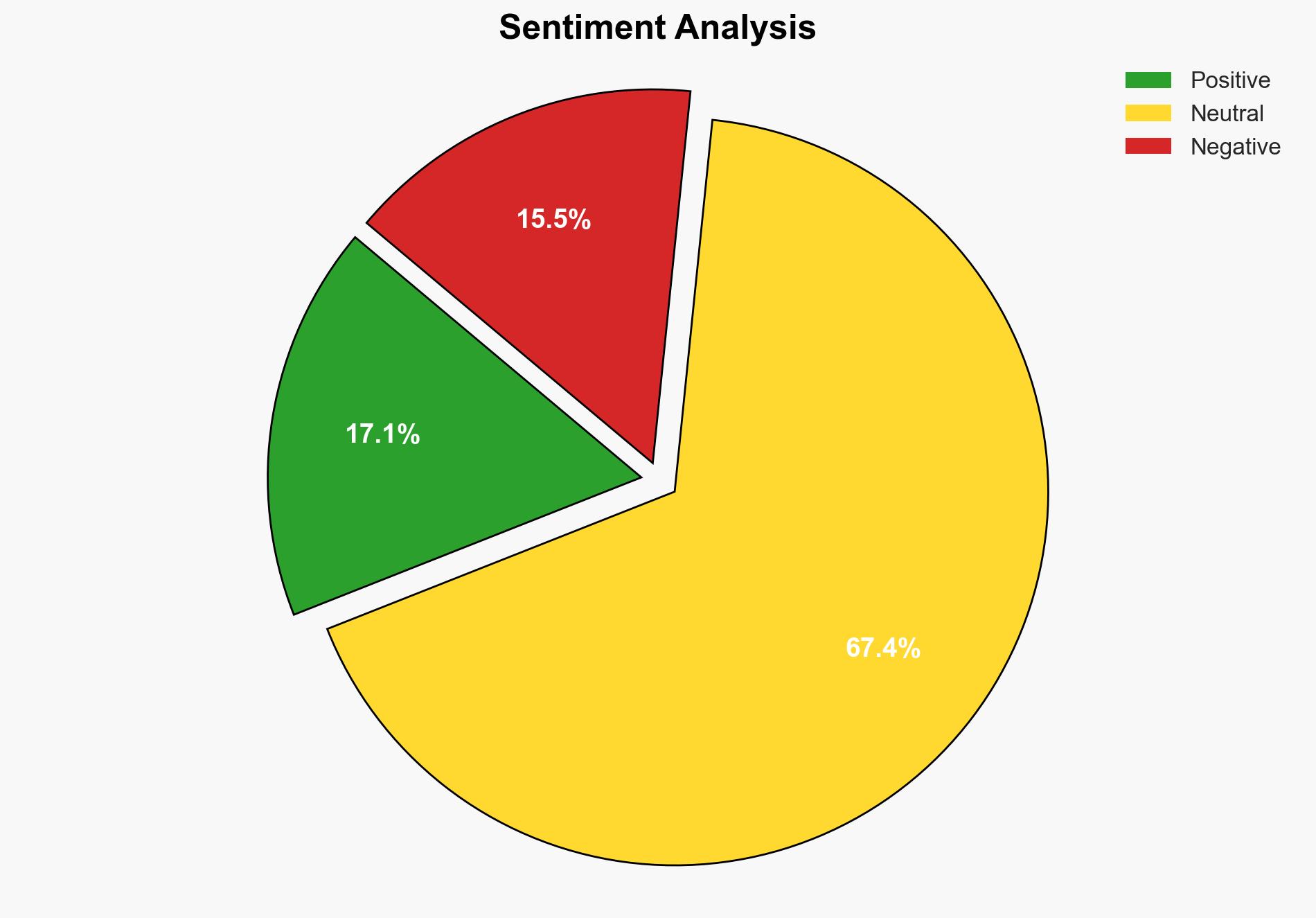
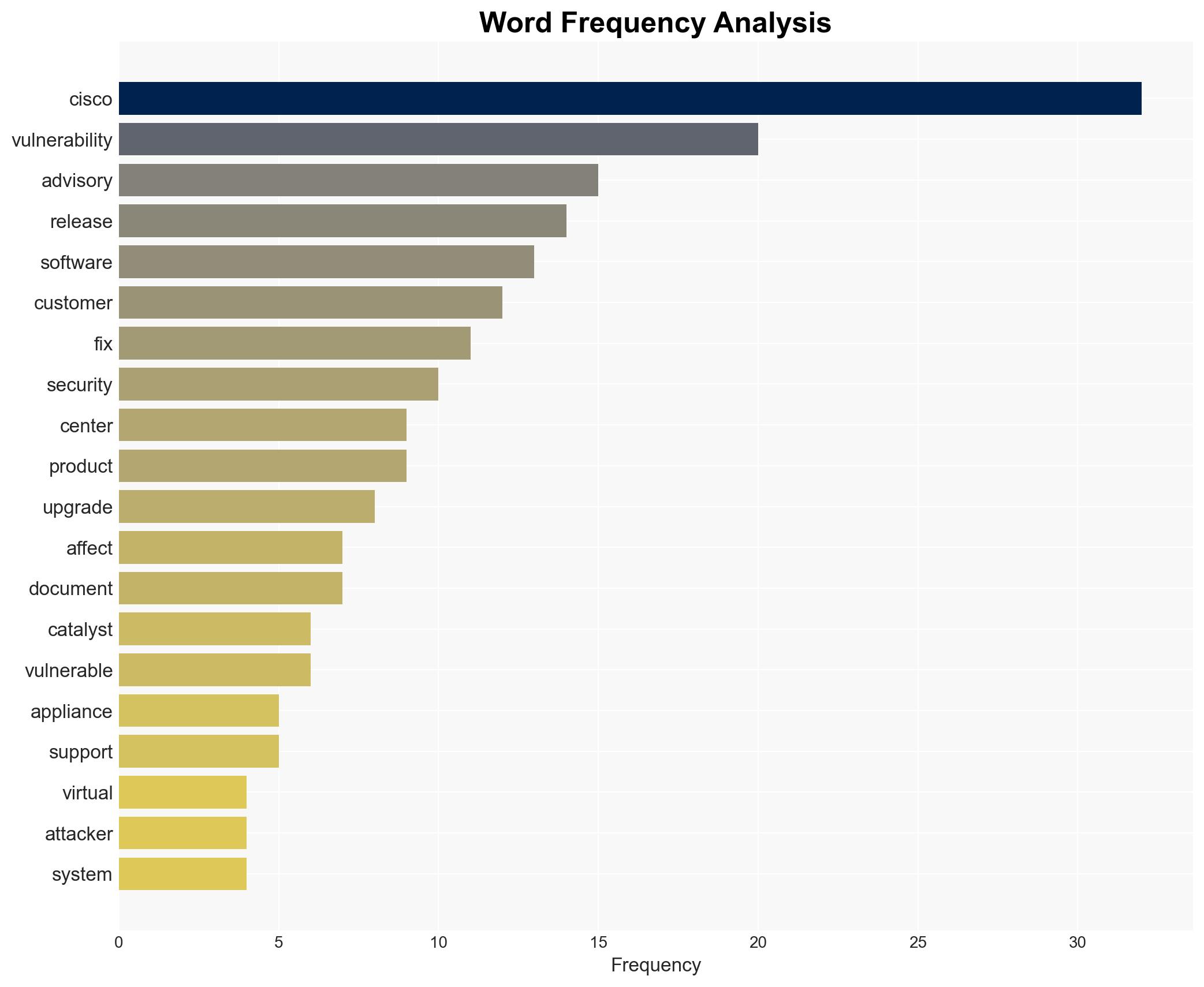
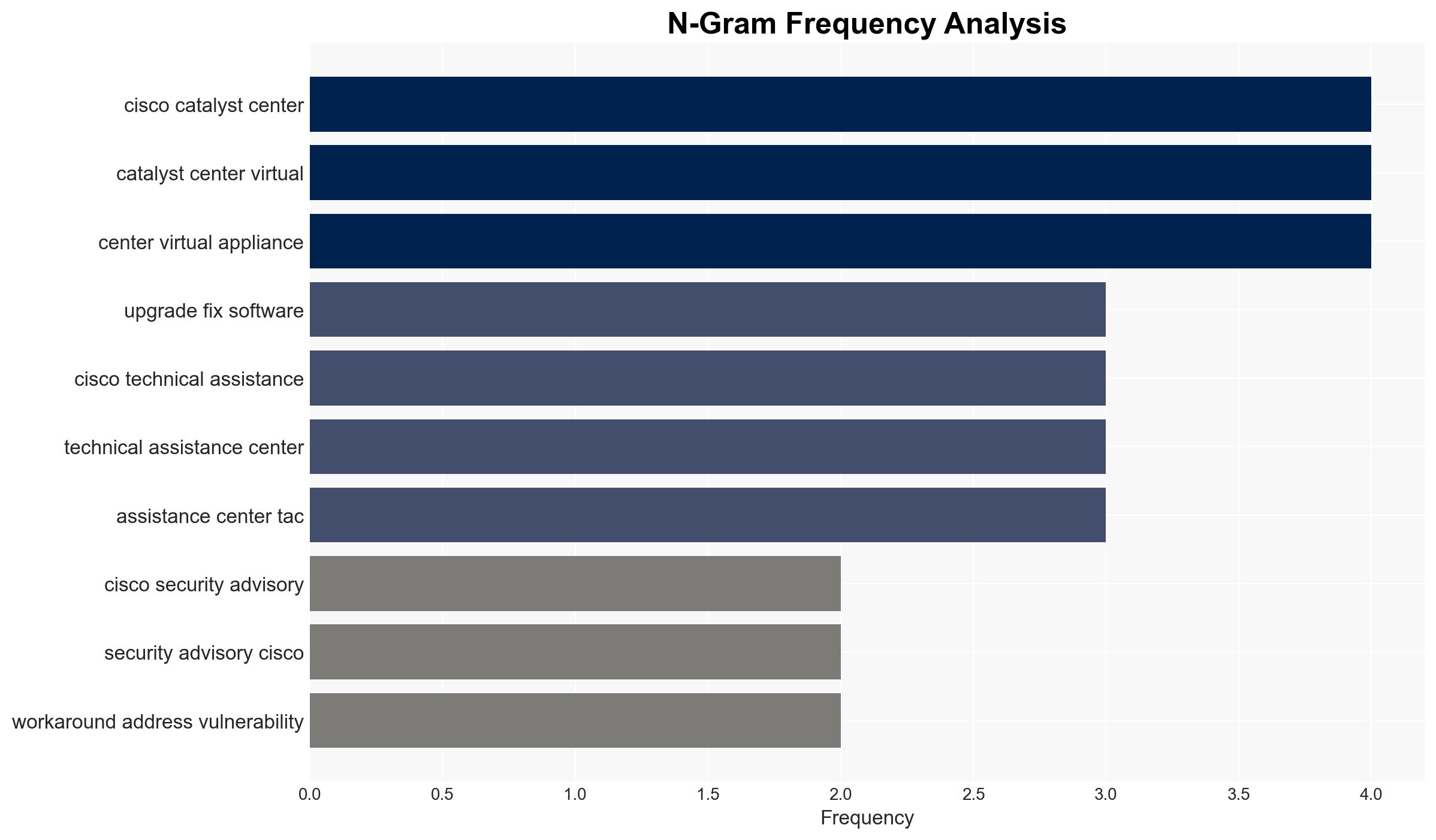
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Cisco Catalyst Center Virtual Appliance Privilege Escalation Vulnerability – Cisco.com
1. BLUF (Bottom Line Up Front)
The Cisco Catalyst Center Virtual Appliance is vulnerable to a privilege escalation attack, which could allow authenticated remote attackers to gain administrative access. The most supported hypothesis is that the vulnerability stems from insufficient input validation, and the recommended action is to upgrade to the fixed software release provided by Cisco. Confidence Level: High.
2. Competing Hypotheses
Hypothesis 1: The vulnerability is due to insufficient validation of user-supplied input, allowing attackers to craft HTTP requests that exploit the system.
Hypothesis 2: The vulnerability is a result of a backdoor or intentional flaw within the Cisco Catalyst Center Virtual Appliance, possibly indicating insider threat or sabotage.
Hypothesis 1 is more likely due to the commonality of input validation issues in software vulnerabilities and the absence of evidence suggesting insider threat or intentional sabotage.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that the vulnerability is not yet widely exploited and that Cisco’s fix will effectively mitigate the risk.
Red Flags: The public announcement of the vulnerability could lead to increased attempts to exploit it before organizations apply the fix.
Deception Indicators: Lack of detailed technical information about the vulnerability might suggest an attempt to downplay the severity or scope.
4. Implications and Strategic Risks
The vulnerability poses significant cyber risks, including unauthorized access to sensitive data and potential disruption of services. If exploited at scale, it could lead to economic losses for affected organizations and reputational damage to Cisco. The risk of cascading threats is high if attackers use the elevated privileges to deploy malware or conduct further attacks within the network.
5. Recommendations and Outlook
- Actionable Steps: Organizations should immediately apply the software update provided by Cisco to mitigate the vulnerability. Additionally, they should review and enhance their input validation processes to prevent similar issues.
- Best Scenario: Rapid adoption of the fix leads to minimal exploitation and limited impact.
- Worst Scenario: Delayed patching results in widespread exploitation, causing significant data breaches and operational disruptions.
- Most-likely Scenario: A moderate number of exploitations occur before the majority of organizations apply the fix, with some operational impacts but no catastrophic outcomes.
6. Key Individuals and Entities
No specific individuals are mentioned in the source text. Key entities include Cisco and its customers using the Catalyst Center Virtual Appliance.
7. Thematic Tags
Cybersecurity
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Methodology