Cisco Fortinet Palo Alto Networks Devices Targeted in Coordinated Campaign – Securityweek.com
Published on: 2025-10-10
Intelligence Report: Cisco Fortinet Palo Alto Networks Devices Targeted in Coordinated Campaign – Securityweek.com
1. BLUF (Bottom Line Up Front)
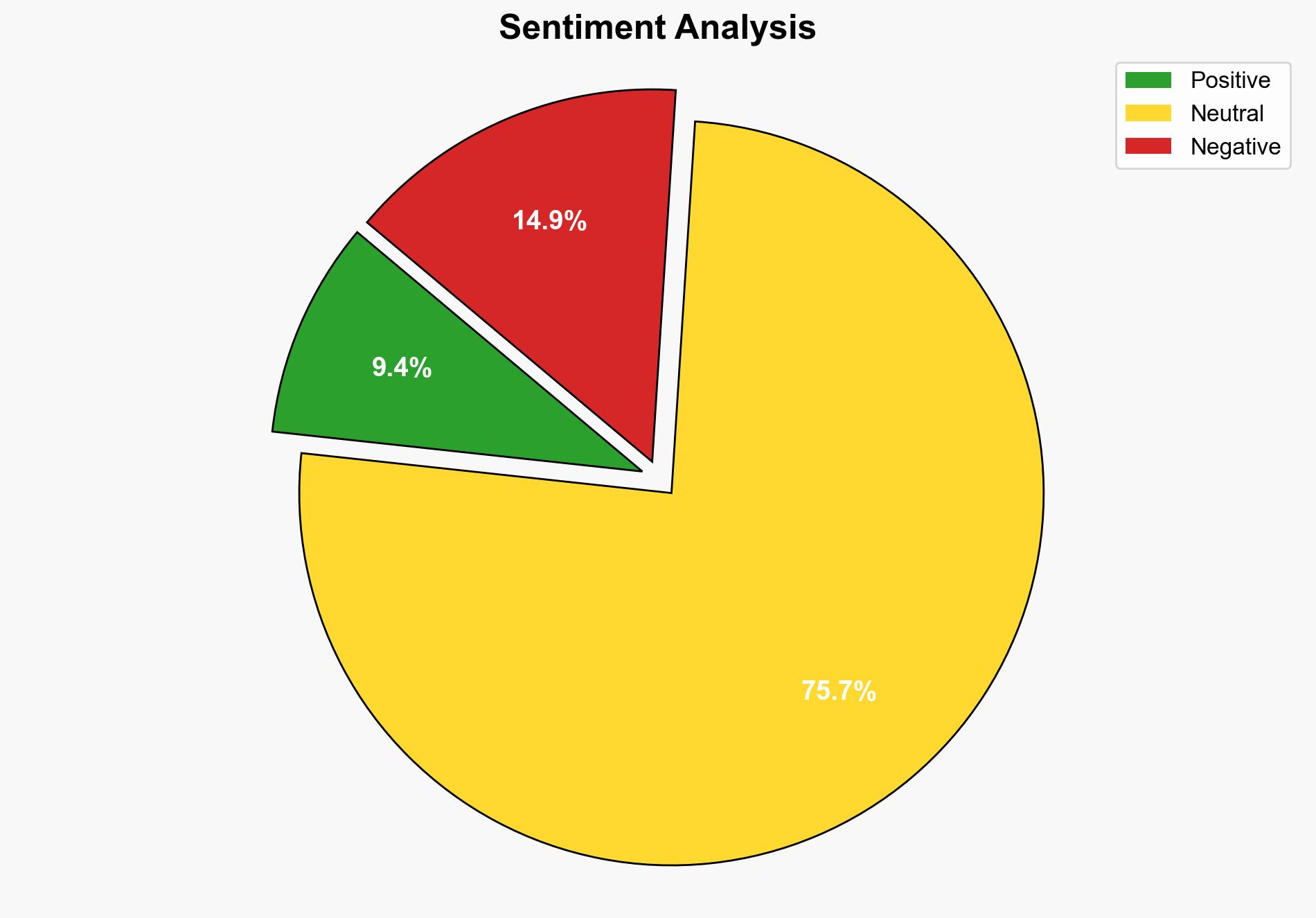
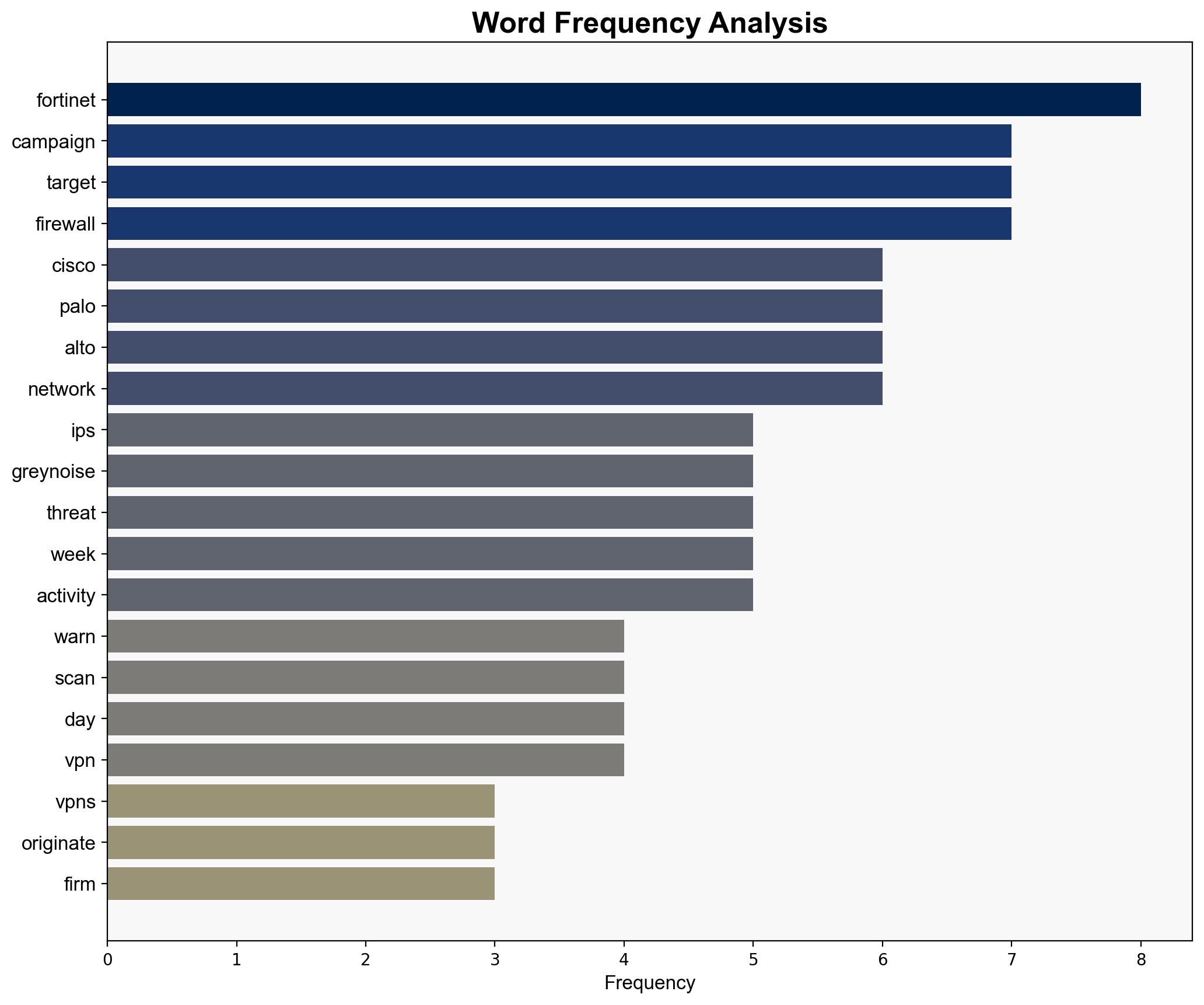
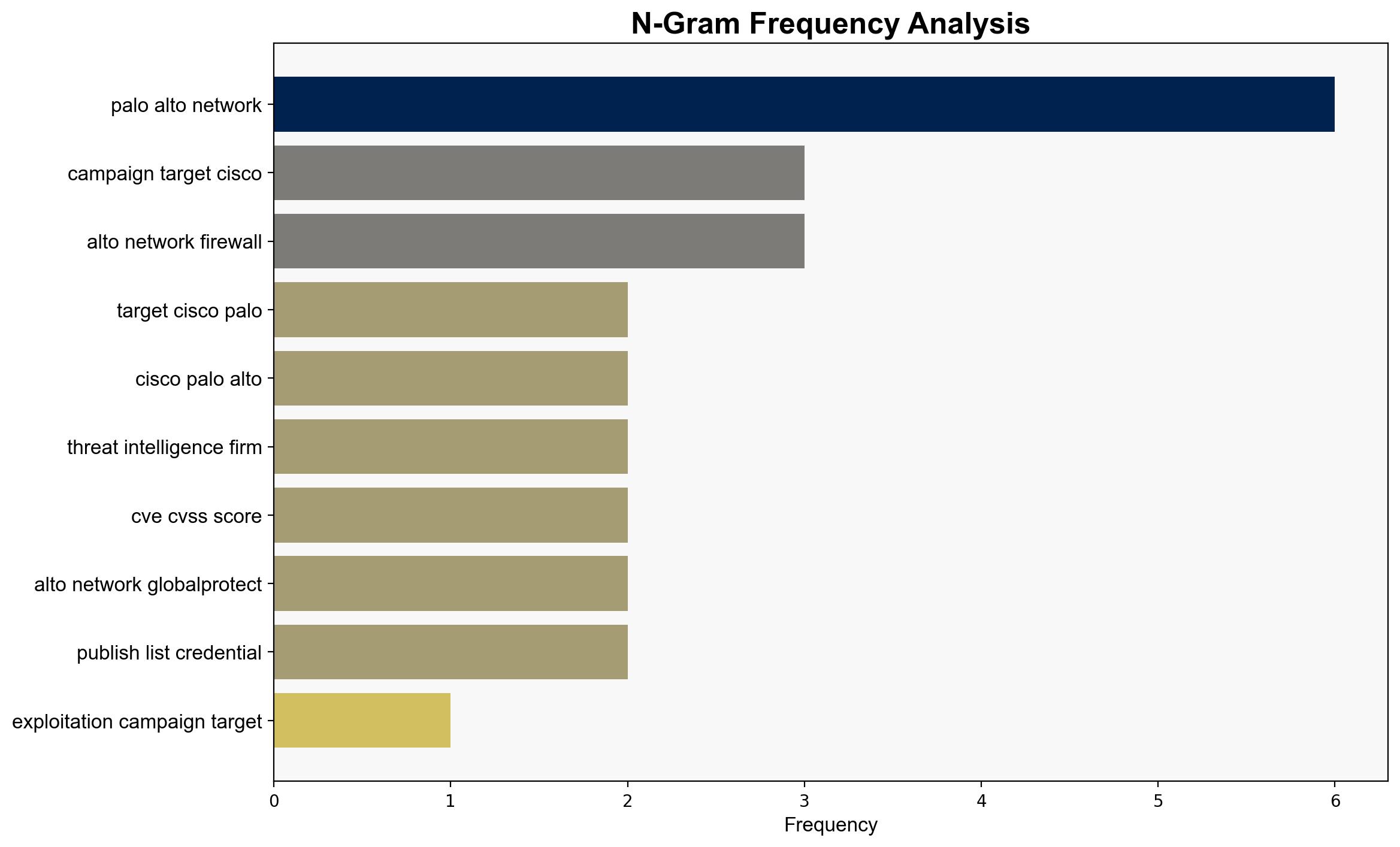
The coordinated cyber campaign targeting Cisco, Fortinet, and Palo Alto Networks devices is likely driven by a state-sponsored actor, potentially linked to China, aiming to exploit known vulnerabilities for espionage purposes. This hypothesis is supported by the pattern of increased scanning activity following vulnerability disclosures and the attribution to a Chinese hacker group. The recommended action is to enhance monitoring and patch management processes, focusing on recently disclosed vulnerabilities. Confidence in this assessment is moderate due to the complexity of attributing cyber activities.
2. Competing Hypotheses
Hypothesis 1: The campaign is a state-sponsored espionage operation by a Chinese group leveraging newly disclosed vulnerabilities to gather intelligence.
– Supported by the timing of increased scanning activity following vulnerability disclosures and the attribution to a Chinese hacker group.
Hypothesis 2: The campaign is a financially motivated cybercriminal operation exploiting vulnerabilities for ransomware or data theft.
– Supported by the massive scale of brute force attempts and the potential for financial gain through data breaches or ransomware deployment.
Using ACH 2.0, Hypothesis 1 is more supported due to the strategic targeting of high-value network devices and the attribution to a nation-state actor, which aligns with known patterns of state-sponsored cyber activities.
3. Key Assumptions and Red Flags
– Assumption: The attribution to a Chinese hacker group is accurate and not a false flag operation.
– Red Flag: Lack of direct evidence linking the campaign to specific state-sponsored objectives.
– Blind Spot: Potential involvement of other nation-states or non-state actors not considered in the analysis.
4. Implications and Strategic Risks
The campaign poses significant risks to national security and critical infrastructure, potentially leading to data breaches, operational disruptions, and loss of sensitive information. Escalation could occur if vulnerabilities are exploited for broader geopolitical objectives, increasing tensions between involved nations. The economic impact could be severe if critical systems are compromised, affecting businesses and government operations.
5. Recommendations and Outlook
- Enhance cybersecurity defenses by prioritizing patch management and monitoring for known vulnerabilities.
- Conduct threat intelligence sharing among affected entities to improve situational awareness.
- Scenario Projections:
- Best Case: Rapid patching and defensive measures mitigate the threat with minimal impact.
- Worst Case: Successful exploitation leads to significant data breaches and geopolitical tensions.
- Most Likely: Continued attempts with partial success, leading to isolated incidents of data theft.
6. Key Individuals and Entities
– GreyNoise (threat intelligence firm)
– ZDI (Zero Day Initiative)
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus