ClickFix attacks leverage DNS queries to deliver PowerShell malware via nslookup command execution
Published on: 2026-02-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
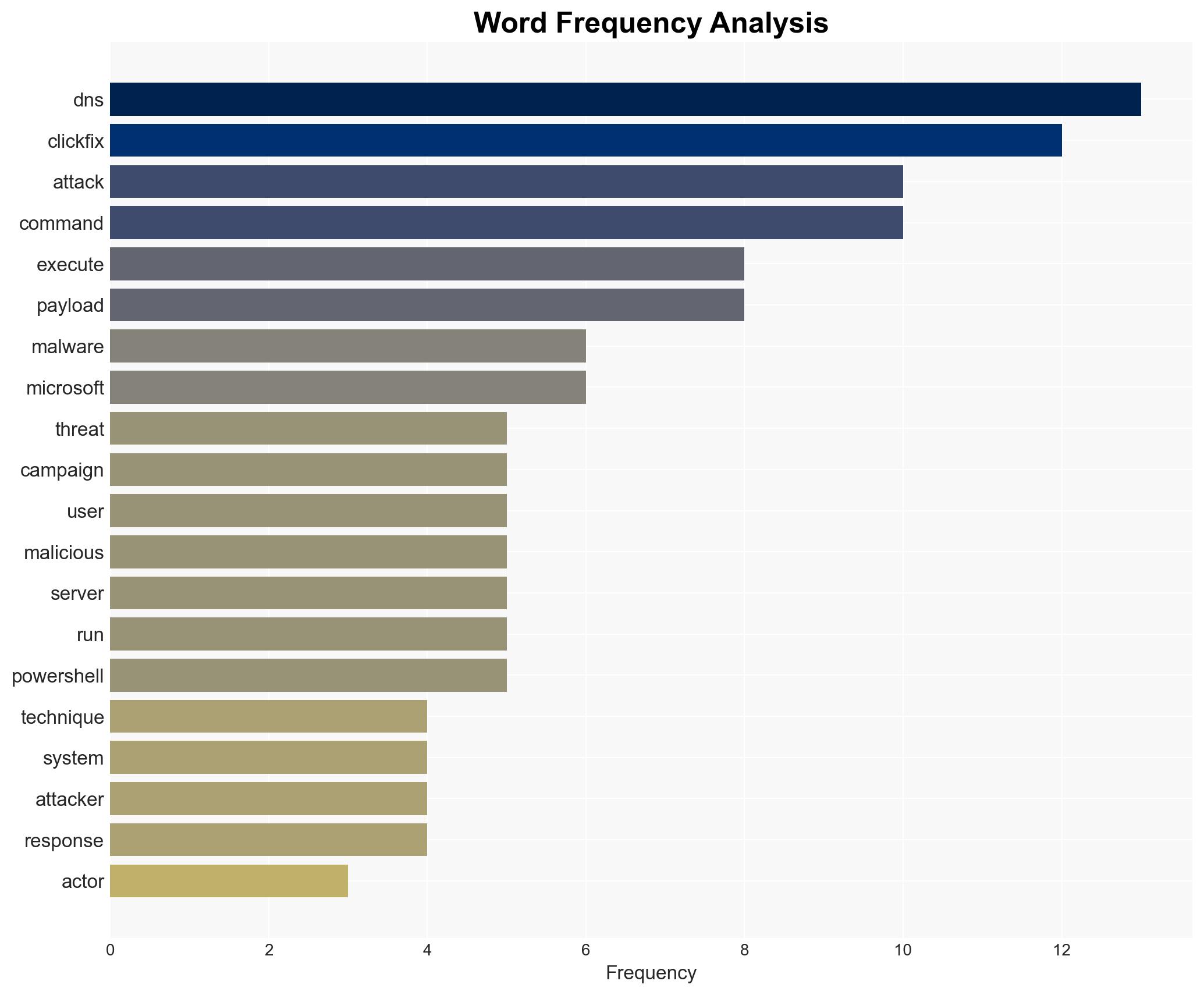
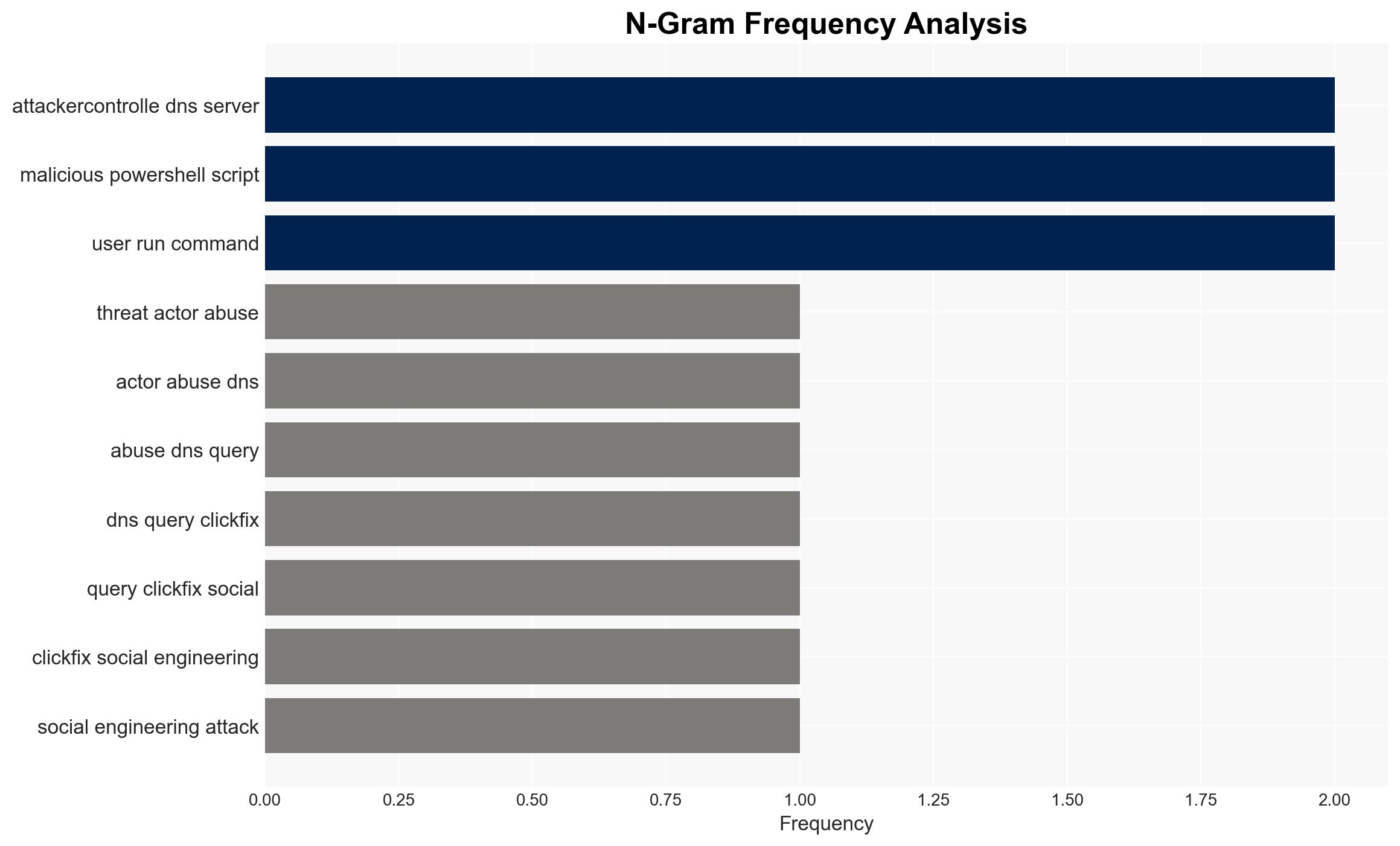
Intelligence Report: New ClickFix attack abuses nslookup to retrieve PowerShell payload via DNS
1. BLUF (Bottom Line Up Front)
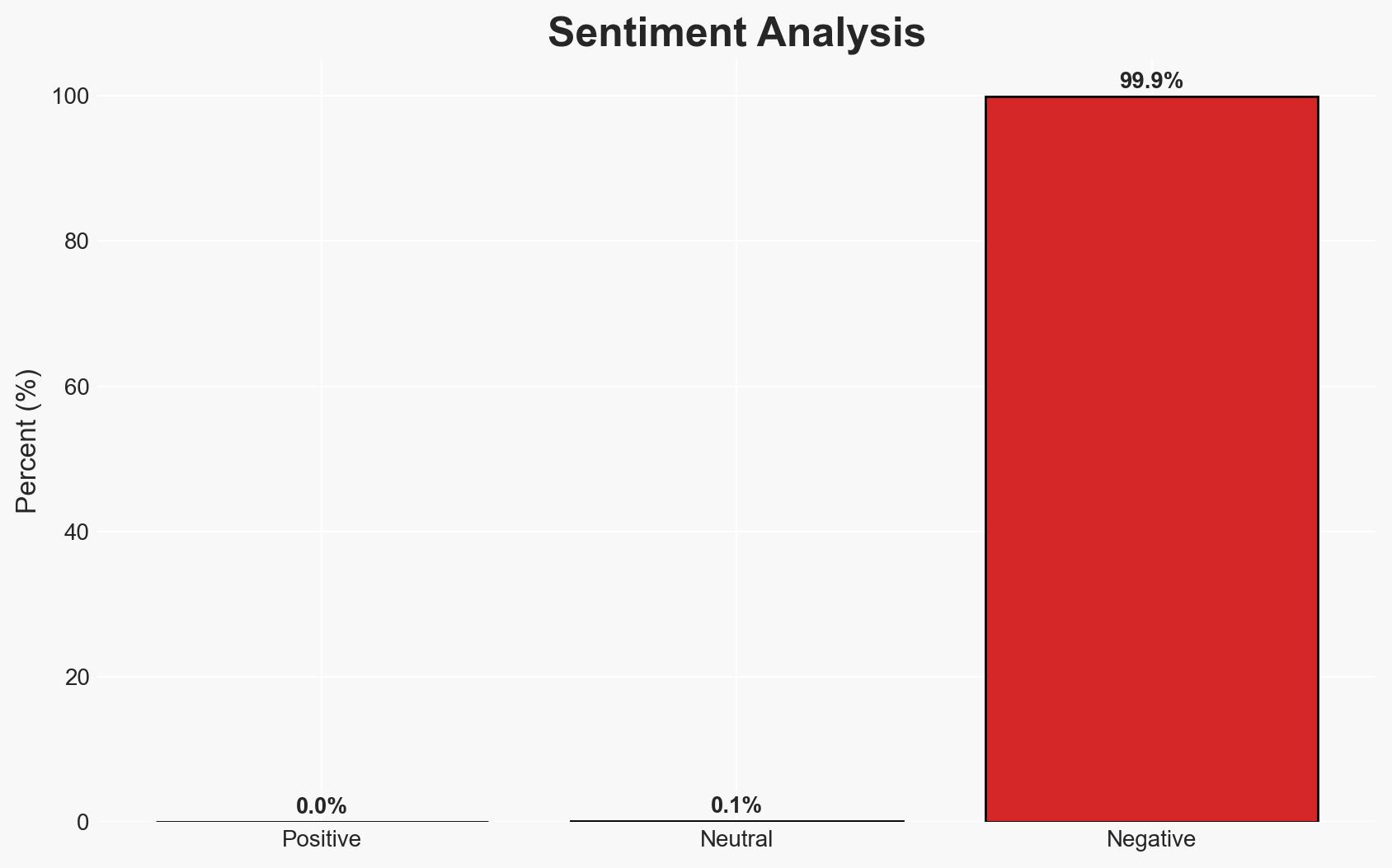
The ClickFix attack has evolved to exploit DNS queries for malware delivery, marking a significant shift in tactics. This method complicates detection and mitigation efforts, posing a heightened threat to cybersecurity. The primary affected parties include organizations using Windows systems. Overall confidence in this assessment is moderate due to limited information on the attack’s full scope and potential countermeasures.
2. Competing Hypotheses
- Hypothesis A: The use of DNS for payload delivery in ClickFix attacks is primarily aimed at evading traditional security measures that focus on HTTP traffic. Supporting evidence includes the novel use of DNS as a channel and the ability to blend malicious traffic with legitimate DNS queries. Key uncertainties involve the extent of the attack’s reach and the specific vulnerabilities exploited.
- Hypothesis B: The DNS-based ClickFix attack is a proof-of-concept or limited-scope operation intended to test new delivery methods rather than a widespread campaign. This is supported by the fact that the attacker-controlled DNS server is no longer available, suggesting limited deployment. Contradicting evidence includes the rapid evolution of ClickFix tactics, indicating broader strategic intent.
- Assessment: Hypothesis A is currently better supported due to the observed sophistication and adaptability of the ClickFix attack, which aligns with broader trends in cyber threat evolution. Indicators such as increased detection of similar DNS-based tactics could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The attack primarily targets Windows systems; DNS-based delivery is intended to bypass traditional security measures; the attack is part of a broader trend of evolving cyber threats.
- Information Gaps: Specific details on the initial lure used to trick users, the full extent of the attack’s deployment, and the identities of the threat actors involved.
- Bias & Deception Risks: Potential bias in focusing on DNS as the primary vector without considering other evolving tactics; risk of deception by threat actors using false flags or misleading indicators.
4. Implications and Strategic Risks
This development could lead to increased sophistication in cyberattacks, challenging existing security frameworks and necessitating new detection methods. The use of DNS as a delivery channel may become more prevalent, influencing broader cybersecurity strategies.
- Political / Geopolitical: Potential for increased tensions if state actors are implicated or if critical infrastructure is targeted.
- Security / Counter-Terrorism: Heightened threat environment as attackers refine techniques to evade detection, requiring enhanced monitoring and response capabilities.
- Cyber / Information Space: Increased complexity in cyber defense due to the blending of malicious traffic with legitimate DNS queries, necessitating advanced threat intelligence and analysis.
- Economic / Social: Potential economic impact from data breaches or disruptions, with social implications if public trust in digital systems is eroded.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of DNS traffic for anomalies, update security protocols to detect and mitigate DNS-based threats, and conduct awareness campaigns on phishing and social engineering tactics.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for intelligence sharing, invest in advanced threat detection technologies, and strengthen incident response capabilities.
- Scenario Outlook: Best: Rapid detection and mitigation reduce impact; Worst: Widespread exploitation leads to significant data breaches; Most-Likely: Continued evolution of tactics with moderate impact, prompting ongoing adjustments in cybersecurity strategies.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, DNS exploitation, malware delivery, threat evolution, PowerShell attacks, cyber defense, social engineering
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us