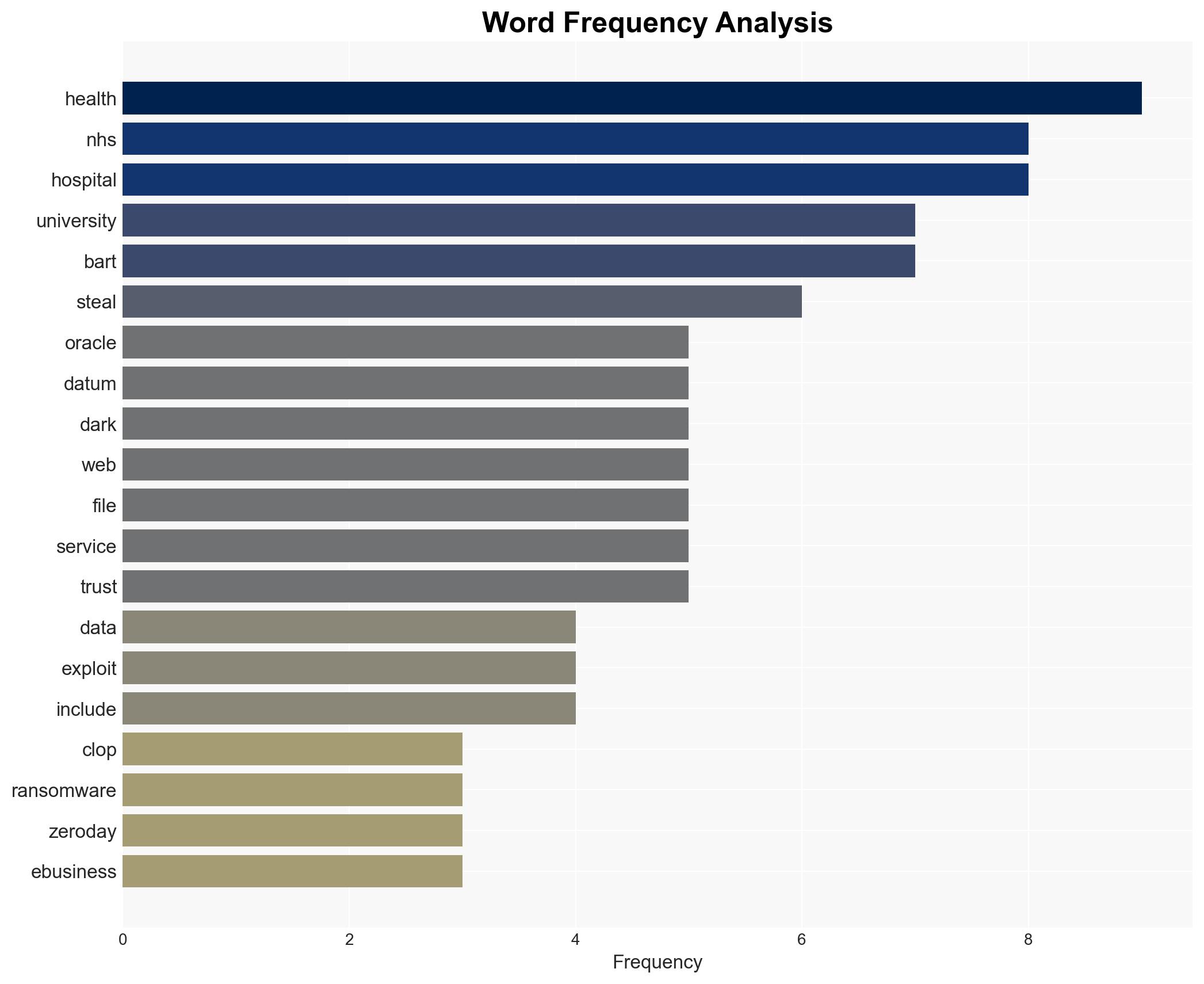
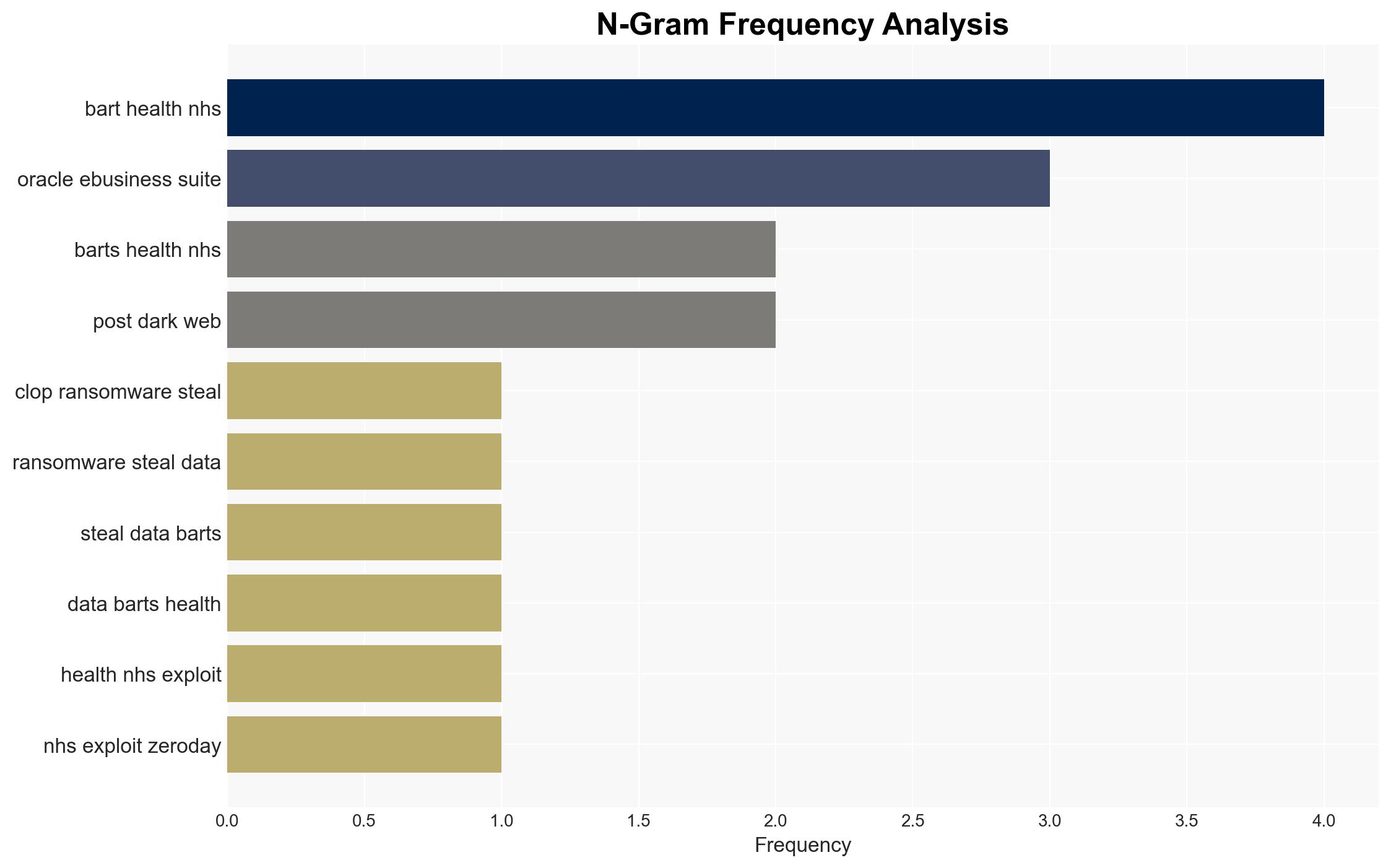
Clop Ransomware Exploits Oracle EBS Zero-Day to Compromise Barts Health NHS Data
Published on: 2025-12-08
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Oracle EBS zero-day used by Clop to breach Barts Health NHS
1. BLUF (Bottom Line Up Front)
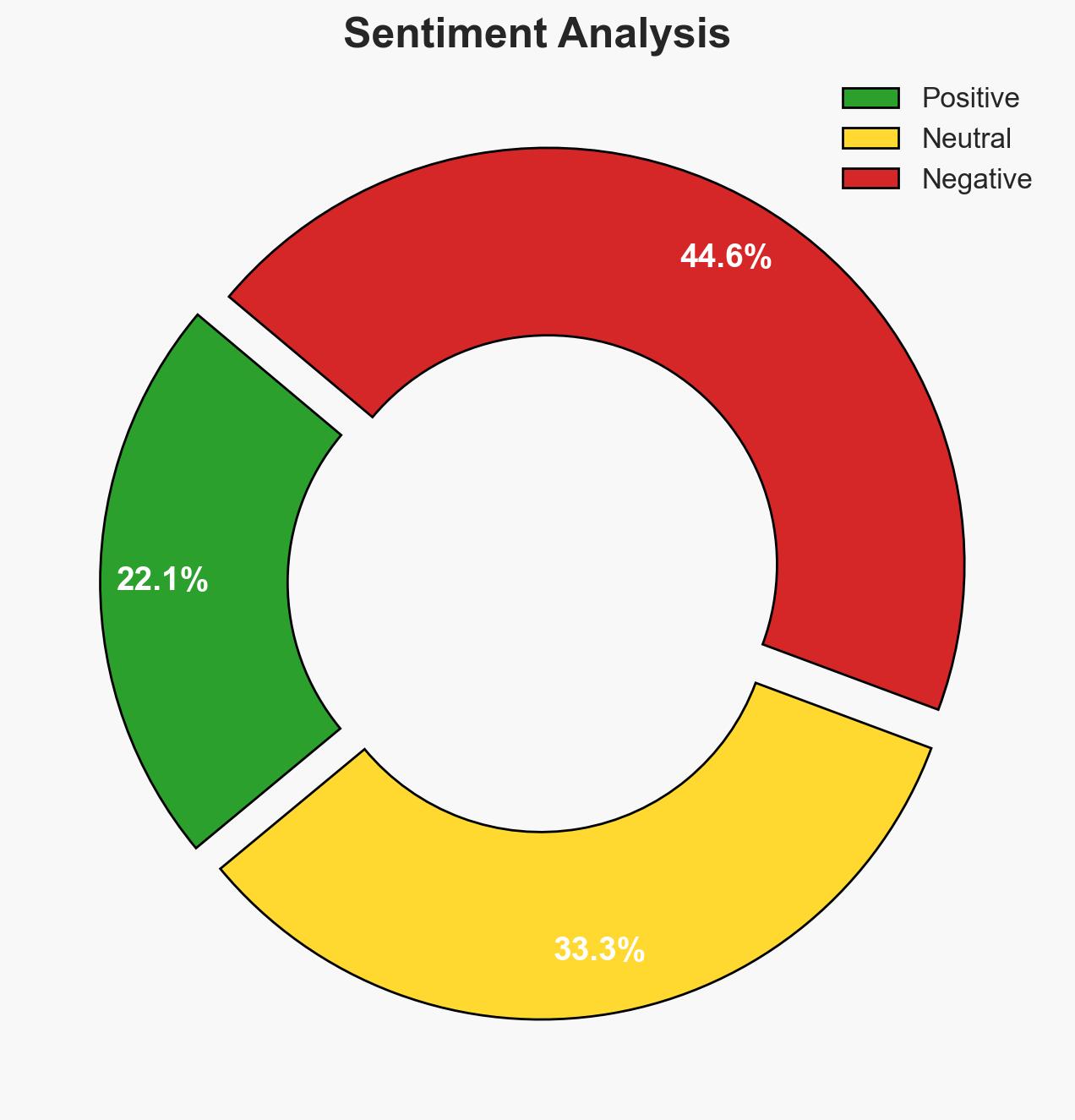
The Clop ransomware group exploited a zero-day vulnerability in Oracle E-Business Suite to breach Barts Health NHS, compromising sensitive financial and personal data. This incident highlights significant cyber vulnerabilities in critical infrastructure, with moderate confidence that the breach was part of a broader campaign affecting multiple organizations globally. The primary concern is the potential misuse of exposed data, impacting patient privacy and organizational reputation.
2. Competing Hypotheses
- Hypothesis A: Clop targeted Barts Health NHS as part of a coordinated campaign exploiting the Oracle EBS zero-day across multiple sectors. Supporting evidence includes similar breaches at other high-profile organizations. Key uncertainties involve the specific motivations behind targeting healthcare entities.
- Hypothesis B: The breach was opportunistic, with Clop exploiting vulnerabilities as they were discovered, without specific targeting of healthcare. This is supported by the diversity of affected organizations. However, the critical nature of healthcare data may suggest a more deliberate focus.
- Assessment: Hypothesis A is currently better supported due to the pattern of breaches across high-value targets, indicating a strategic approach. Indicators such as further healthcare breaches or specific demands from Clop could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Clop has the capability to exploit zero-day vulnerabilities; Oracle EBS is widely used in critical sectors; Barts Health NHS data is valuable for cybercriminals.
- Information Gaps: Specific motivations for targeting Barts Health NHS; full scope of data compromised; details on Clop’s operational structure.
- Bias & Deception Risks: Potential bias in attributing the breach solely to Clop without considering other actors; reliance on public statements from affected organizations may understate the breach’s impact.
4. Implications and Strategic Risks
This development underscores the vulnerability of critical infrastructure to cyber threats, potentially leading to increased regulatory scrutiny and demands for enhanced cybersecurity measures.
- Political / Geopolitical: Potential for increased tension between nations over cyber capabilities and responsibilities.
- Security / Counter-Terrorism: Heightened alertness in healthcare and other critical sectors to prevent further breaches.
- Cyber / Information Space: Increased focus on securing enterprise software and addressing zero-day vulnerabilities.
- Economic / Social: Potential financial losses for affected organizations and erosion of public trust in data security.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive security audit of Oracle EBS installations; enhance monitoring for signs of exploitation; engage with law enforcement and cybersecurity agencies.
- Medium-Term Posture (1–12 months): Develop partnerships for threat intelligence sharing; invest in cybersecurity training and infrastructure upgrades.
- Scenario Outlook:
- Best-case: Rapid patching and improved defenses prevent further breaches.
- Worst-case: Continued exploitation leads to widespread data breaches and significant operational disruptions.
- Most-Likely: Incremental improvements in security posture reduce but do not eliminate risks.
6. Key Individuals and Entities
- Clop ransomware group
- Barts Health NHS
- Oracle Corporation
- UK National Cyber Security Centre
- Metropolitan Police
- Information Commissioner’s Office (ICO)
7. Thematic Tags
Cybersecurity, ransomware, healthcare data breach, zero-day vulnerability, critical infrastructure, data privacy, cybercrime
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us