Cointelegraph Hit by Front-End Exploit Fake Phishing Airdrop Pop Up on Website – CoinDesk
Published on: 2025-06-23
Intelligence Report: Cointelegraph Hit by Front-End Exploit Fake Phishing Airdrop Pop Up on Website – CoinDesk
1. BLUF (Bottom Line Up Front)
Cointelegraph’s website was compromised through a front-end exploit, resulting in a fake phishing airdrop pop-up that deceived users into connecting their crypto wallets under false pretenses. This incident highlights significant vulnerabilities in trusted platforms, emphasizing the need for enhanced cybersecurity measures. Immediate action is recommended to mitigate risks and prevent similar future exploits.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
Simulated potential actions of cyber adversaries revealed vulnerabilities in front-end security protocols, suggesting the need for robust intrusion detection systems.
Indicators Development
Identified key indicators of compromise, including unauthorized pop-ups and wallet connection prompts, which can serve as early warning signs for future attacks.
Bayesian Scenario Modeling
Utilized probabilistic models to assess the likelihood of similar attacks on other platforms, predicting potential pathways and outcomes.
3. Implications and Strategic Risks
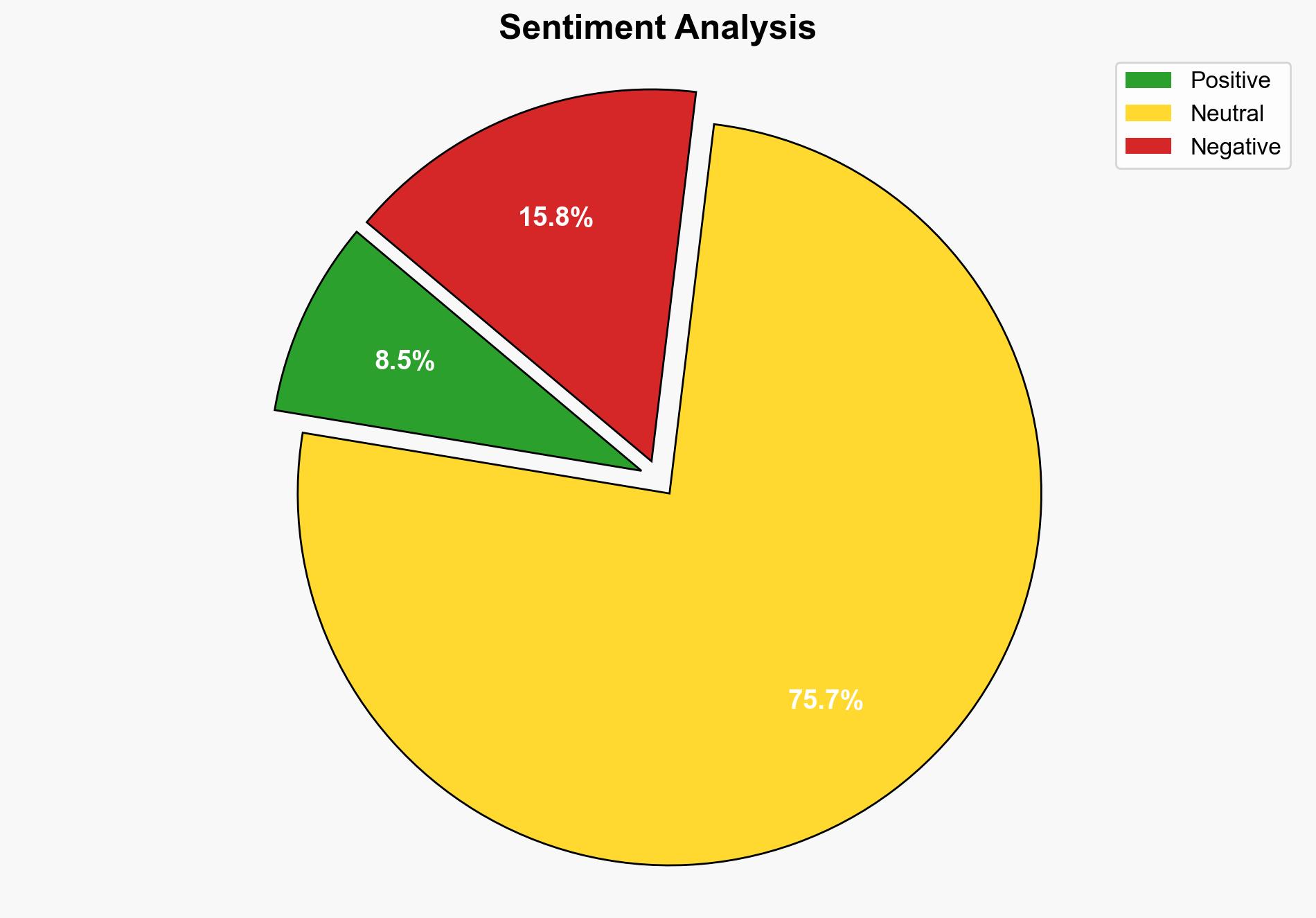
This incident underscores the growing threat of cyberattacks targeting trusted platforms, potentially eroding user trust and causing financial losses. The exploitation of Cointelegraph’s platform could have cascading effects on the broader cryptocurrency ecosystem, increasing skepticism and reducing user engagement.
4. Recommendations and Outlook
- Enhance cybersecurity measures by implementing advanced threat detection and response systems.
- Conduct regular security audits and penetration testing to identify and address vulnerabilities.
- Educate users on recognizing phishing attempts and safe online practices.
- Scenario-based projections:
- Best Case: Rapid mitigation and user education restore trust and prevent further incidents.
- Worst Case: Continued exploits lead to significant financial losses and reputational damage.
- Most Likely: Incremental improvements in security reduce but do not eliminate future risks.
5. Key Individuals and Entities
Shaurya Malwa
6. Thematic Tags
cybersecurity, phishing attacks, cryptocurrency security, digital asset protection