Colt confirms customer data stolen as Warlock ransomware crew auctions off details – TechRadar
Published on: 2025-08-22
Intelligence Report: Colt confirms customer data stolen as Warlock ransomware crew auctions off details – TechRadar
1. BLUF (Bottom Line Up Front)
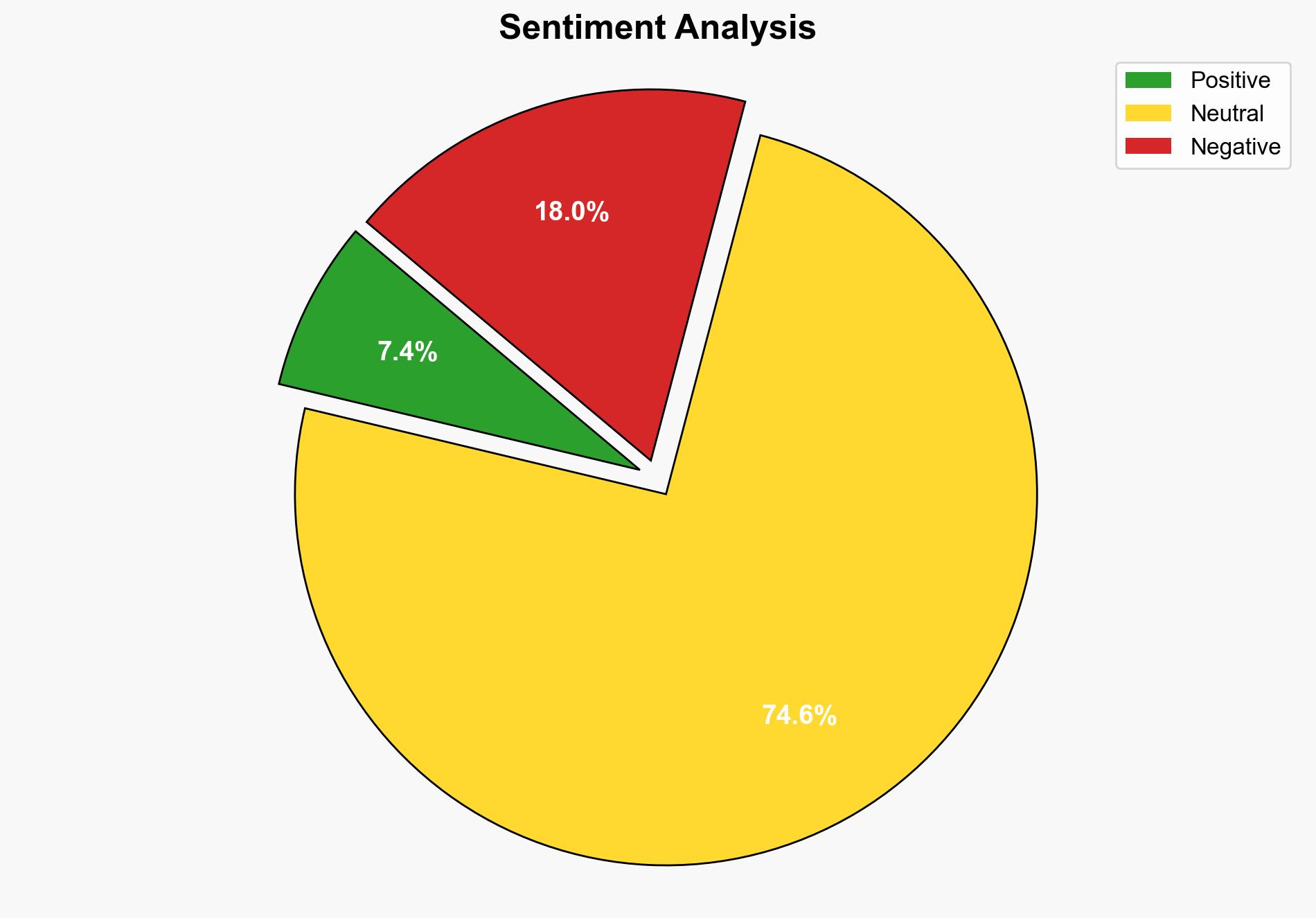
The Warlock ransomware group has successfully exfiltrated sensitive customer data from Colt Technology Services and is auctioning it on the dark web. The most supported hypothesis is that the breach was facilitated by exploiting vulnerabilities in Colt’s SharePoint server. Confidence level is moderate due to limited direct evidence of the attack vector. Immediate action is recommended to enhance cybersecurity measures and notify affected customers.
2. Competing Hypotheses
Hypothesis 1: The Warlock group exploited vulnerabilities in Colt’s SharePoint server, leading to the data breach. This hypothesis is supported by the fact that the server was taken offline and the group’s history of targeting similar systems.
Hypothesis 2: The breach resulted from insider assistance, either knowingly or unknowingly, facilitating access to sensitive data. This is less supported due to the lack of evidence pointing to insider involvement.
Using ACH 2.0, Hypothesis 1 is better supported by the available evidence, including the server’s offline status and the group’s known tactics.
3. Key Assumptions and Red Flags
Assumptions include the belief that the Warlock group acted independently and that the SharePoint server was the primary entry point. A red flag is the absence of detailed technical evidence from Colt about the breach’s specifics, which could indicate either a lack of information or an attempt to control the narrative.
4. Implications and Strategic Risks
The breach could lead to significant financial losses for Colt and its customers, increased regulatory scrutiny, and reputational damage. There is a risk of further cyberattacks if vulnerabilities are not addressed. The incident may embolden other ransomware groups, increasing the overall threat landscape.
5. Recommendations and Outlook
- Enhance cybersecurity measures, focusing on patching known vulnerabilities and improving monitoring systems.
- Notify affected customers and provide guidance on mitigating identity theft risks.
- Conduct a thorough forensic investigation to ascertain the breach’s full scope.
- Scenario Projections:
- Best Case: Rapid containment and mitigation prevent further data loss and restore customer trust.
- Worst Case: Additional vulnerabilities are exploited, leading to further breaches and financial losses.
- Most Likely: Incremental improvements in security reduce immediate risks, but long-term vigilance is required.
6. Key Individuals and Entities
No specific individuals are mentioned in the provided intelligence. The Warlock ransomware group and Colt Technology Services are the primary entities involved.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus