Confronting Digital Surveillance: Unmasking Control in the Age of Data Exploitation
Published on: 2025-12-18
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
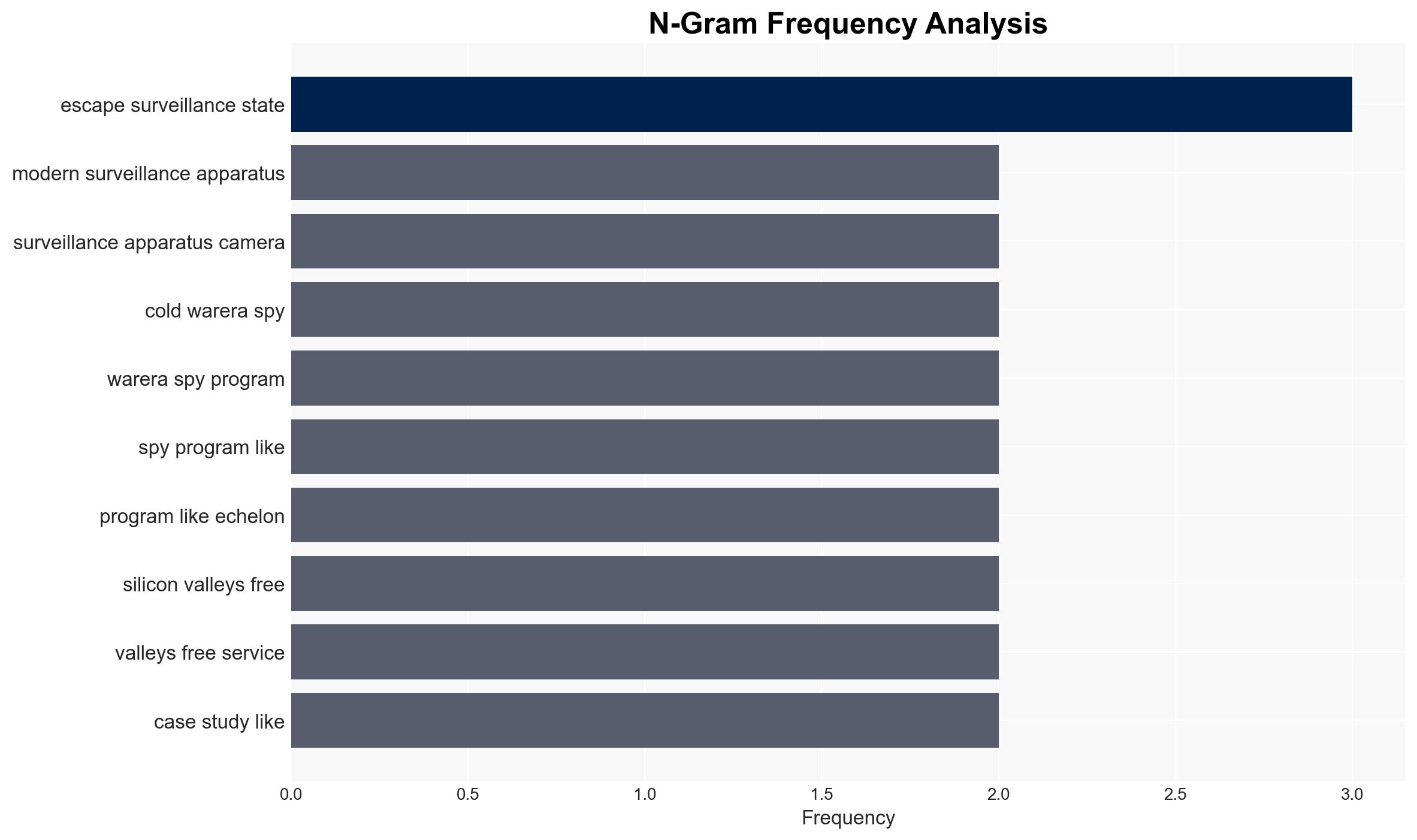
Intelligence Report: Escape the Surveillance State A wake-up call for the digital age
1. BLUF (Bottom Line Up Front)
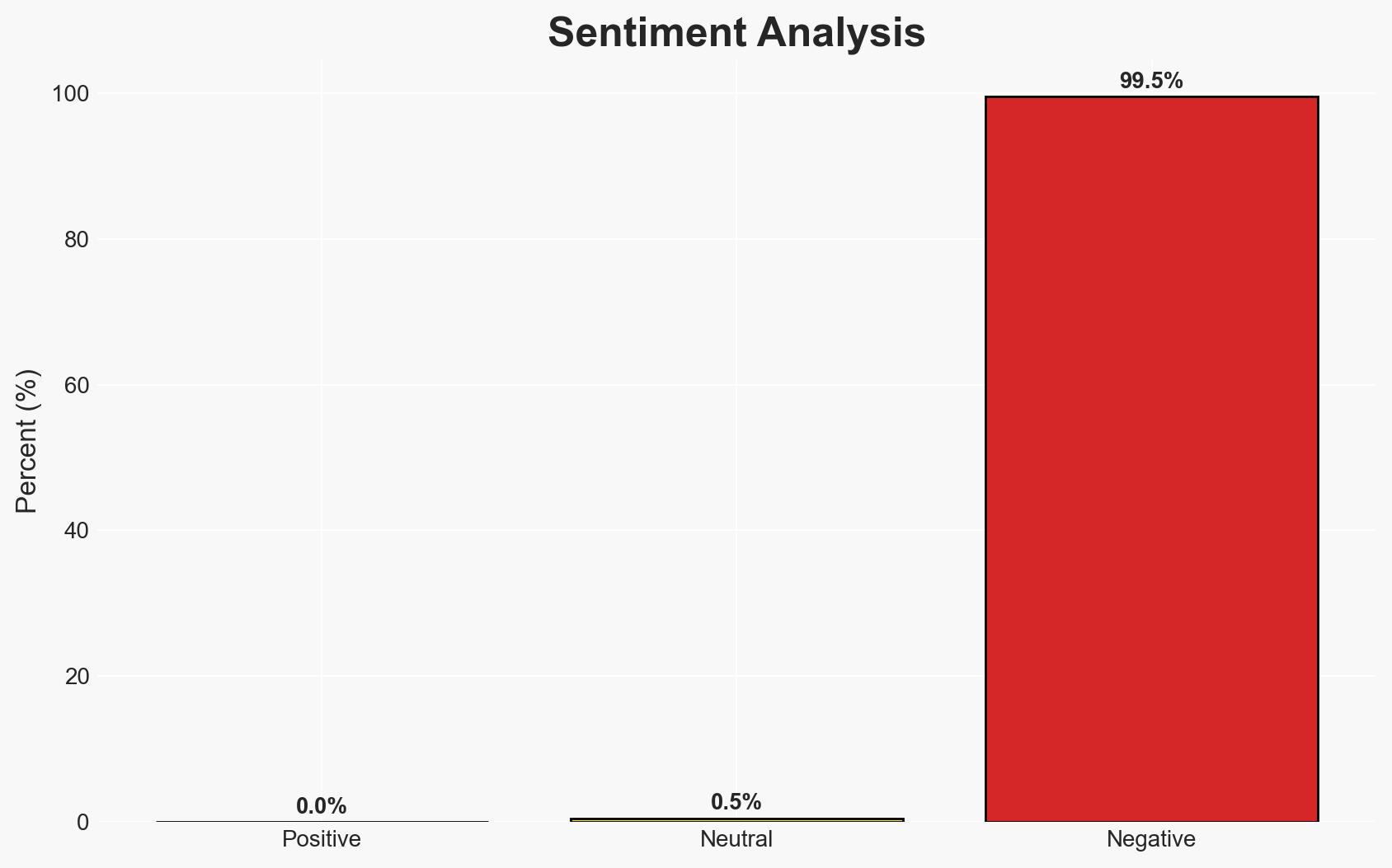
The book “Escape the Surveillance State” argues that modern surveillance systems, rooted in Cold War-era programs, have expanded post-9/11, prioritizing control over security. It suggests that these systems are ineffective against terrorism but effective in political manipulation and law enforcement overreach. The book advocates for digital minimalism and privacy-focused alternatives to reclaim autonomy. Overall confidence in these assessments is moderate, given the potential for bias and incomplete data.
2. Competing Hypotheses
- Hypothesis A: Modern surveillance systems are primarily tools for control rather than security, as evidenced by their ineffectiveness in counter-terrorism and their role in political manipulation. However, the extent of their ineffectiveness is uncertain due to limited public data on counter-terrorism successes.
- Hypothesis B: Surveillance systems are essential for national security and have prevented numerous threats, with control being a secondary effect. This is contradicted by the book’s examples of political manipulation and overreach, but lacks comprehensive data on thwarted threats.
- Assessment: Hypothesis A is currently better supported due to documented cases of political manipulation and the book’s detailed analysis of surveillance programs. Key indicators that could shift this judgment include credible data on counter-terrorism successes attributed to surveillance.
3. Key Assumptions and Red Flags
- Assumptions: Surveillance systems are primarily used for control; post-9/11 expansions were driven by security narratives; Silicon Valley companies willingly cooperate with surveillance efforts.
- Information Gaps: Lack of comprehensive data on the effectiveness of surveillance in preventing terrorism; limited insight into internal government and corporate decision-making processes.
- Bias & Deception Risks: Potential bias from the author’s perspective as a whistleblower; risk of selective presentation of evidence to support the book’s thesis; possible underreporting of surveillance successes.
4. Implications and Strategic Risks
The expansion of surveillance systems could lead to increased political manipulation and erosion of civil liberties, potentially destabilizing democratic institutions. This development may also provoke public backlash and drive demand for privacy-focused technologies.
- Political / Geopolitical: Potential for increased tensions between governments and citizens over privacy rights; international scrutiny of surveillance practices.
- Security / Counter-Terrorism: Possible degradation of public trust in security agencies; challenges in balancing security needs with privacy rights.
- Cyber / Information Space: Increased adoption of privacy-focused technologies; potential for cyber activism against surveillance systems.
- Economic / Social: Growth in the privacy tech sector; social movements advocating for digital rights and autonomy.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Monitor public sentiment and legislative developments on privacy; engage with tech companies to understand data practices.
- Medium-Term Posture (1–12 months): Develop partnerships with privacy advocates; invest in technologies that enhance privacy and security; review and update surveillance policies.
- Scenario Outlook: Best: Increased transparency and privacy protections; Worst: Escalation of surveillance and erosion of civil liberties; Most-Likely: Gradual shift towards privacy-focused solutions with ongoing debates over surveillance.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
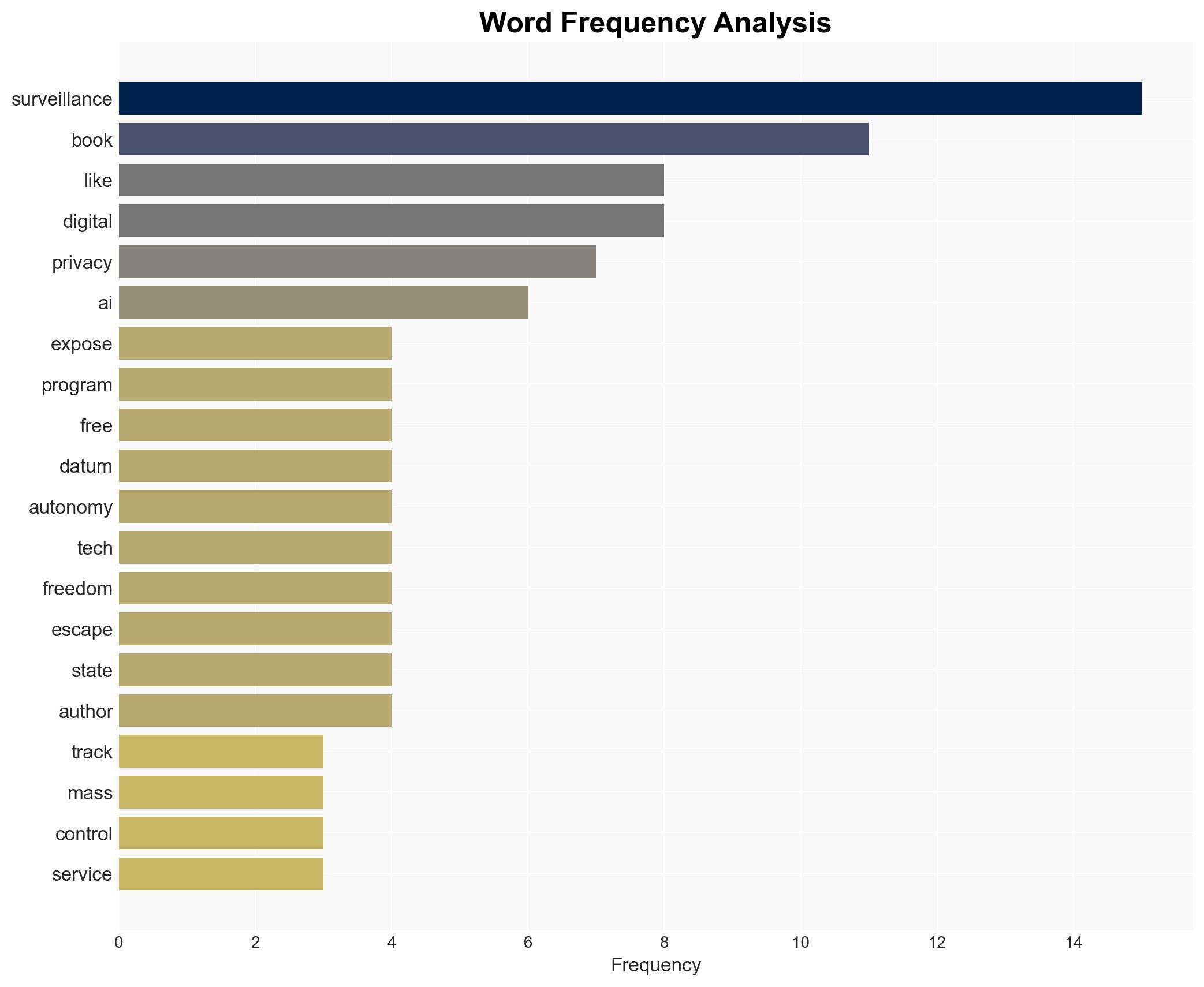
cybersecurity, surveillance, privacy, national security, political manipulation, digital rights, civil liberties
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Cognitive Bias Stress Test: Structured challenge to expose and correct biases.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us