Congressional report reveals China’s use of U.S. research funding to access sensitive nuclear technology.
Published on: 2025-12-17
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: China exploits US-funded research on nuclear technology a congressional report says
1. BLUF (Bottom Line Up Front)
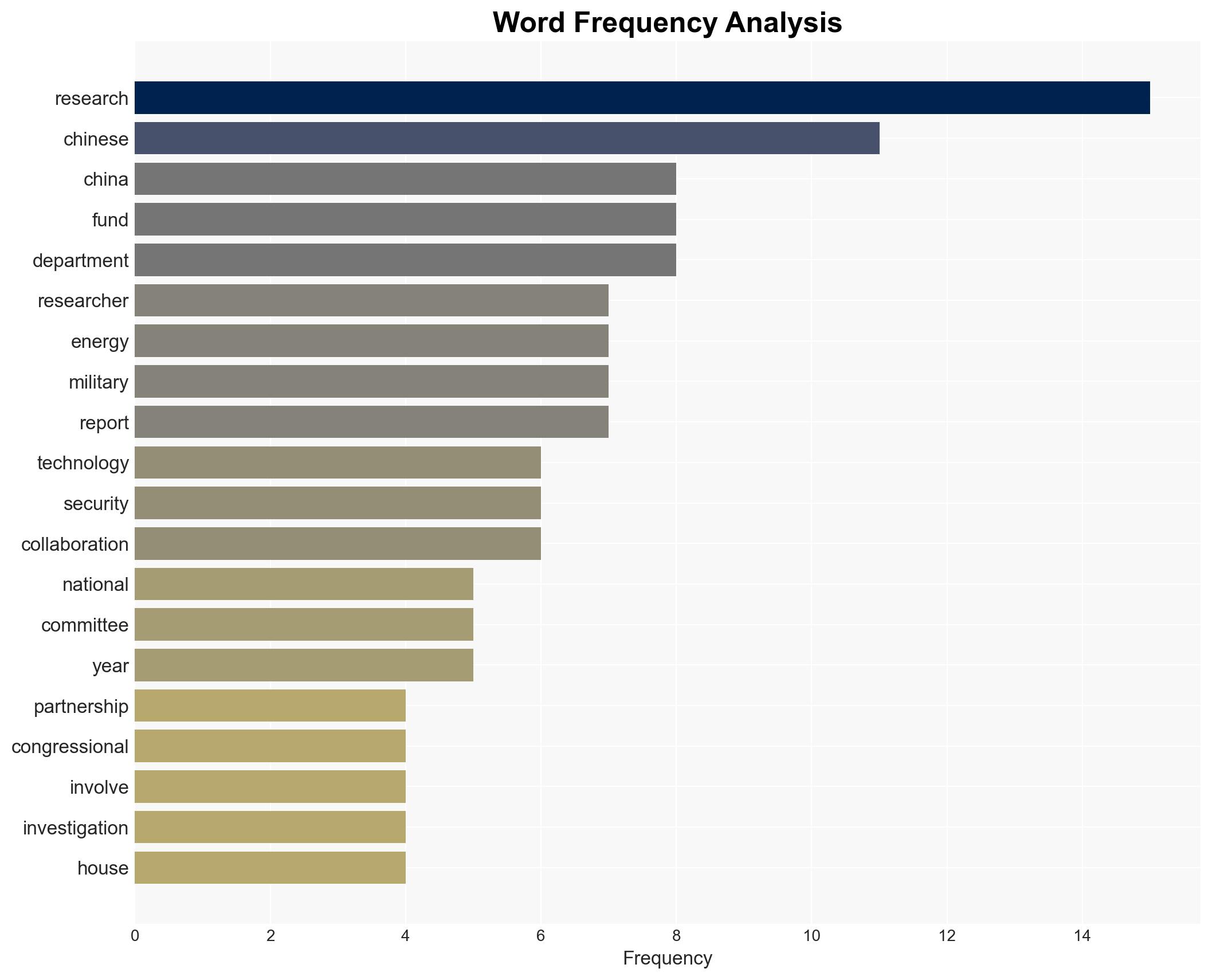
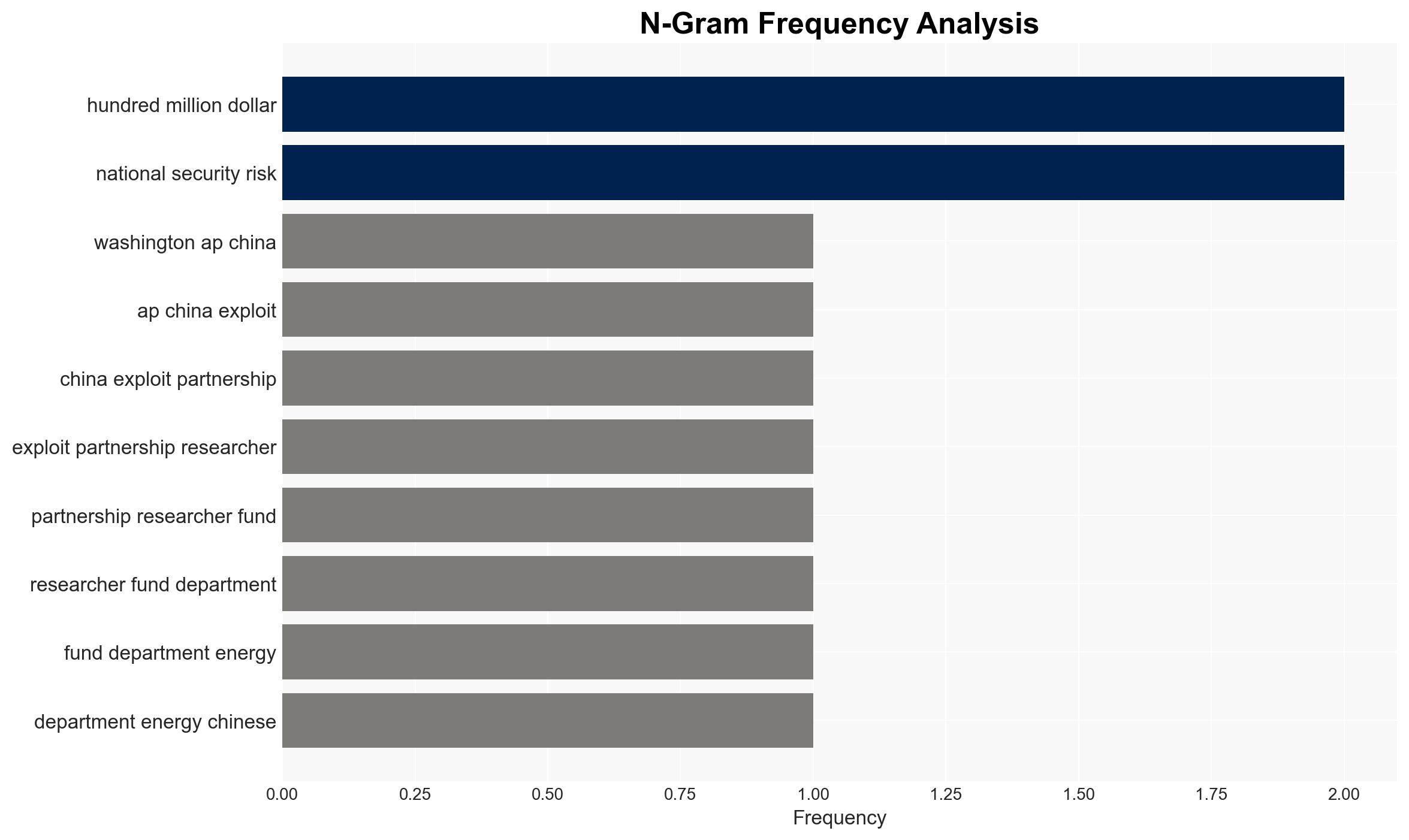
China is reportedly leveraging partnerships with U.S. researchers, funded by the Department of Energy (DOE), to gain access to sensitive nuclear technology, potentially enhancing its military capabilities. This situation poses significant national security risks to the United States. The most likely hypothesis is that China is deliberately targeting these collaborations to bolster its military and technological advancements. This assessment is made with moderate confidence, given the available evidence and identified information gaps.
2. Competing Hypotheses
- Hypothesis A: China is intentionally exploiting U.S.-funded research collaborations to enhance its military capabilities. This is supported by the congressional report findings of collaborations with Chinese military-affiliated researchers. Key uncertainties include the extent of the exploitation and the specific technologies targeted.
- Hypothesis B: The collaborations are primarily academic and scientific in nature, with no deliberate intent by China to exploit them for military gain. This hypothesis is contradicted by the involvement of Chinese state-owned laboratories and military-affiliated researchers.
- Assessment: Hypothesis A is currently better supported due to the direct involvement of Chinese military-affiliated entities in the collaborations. Indicators such as increased scrutiny of research partnerships and policy changes could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The DOE has adequate oversight mechanisms for research collaborations; Chinese military-affiliated researchers have access to sensitive information; U.S. policy changes can effectively mitigate risks.
- Information Gaps: Specific details on the technologies accessed by Chinese entities; the full scope of Chinese military involvement; effectiveness of current U.S. countermeasures.
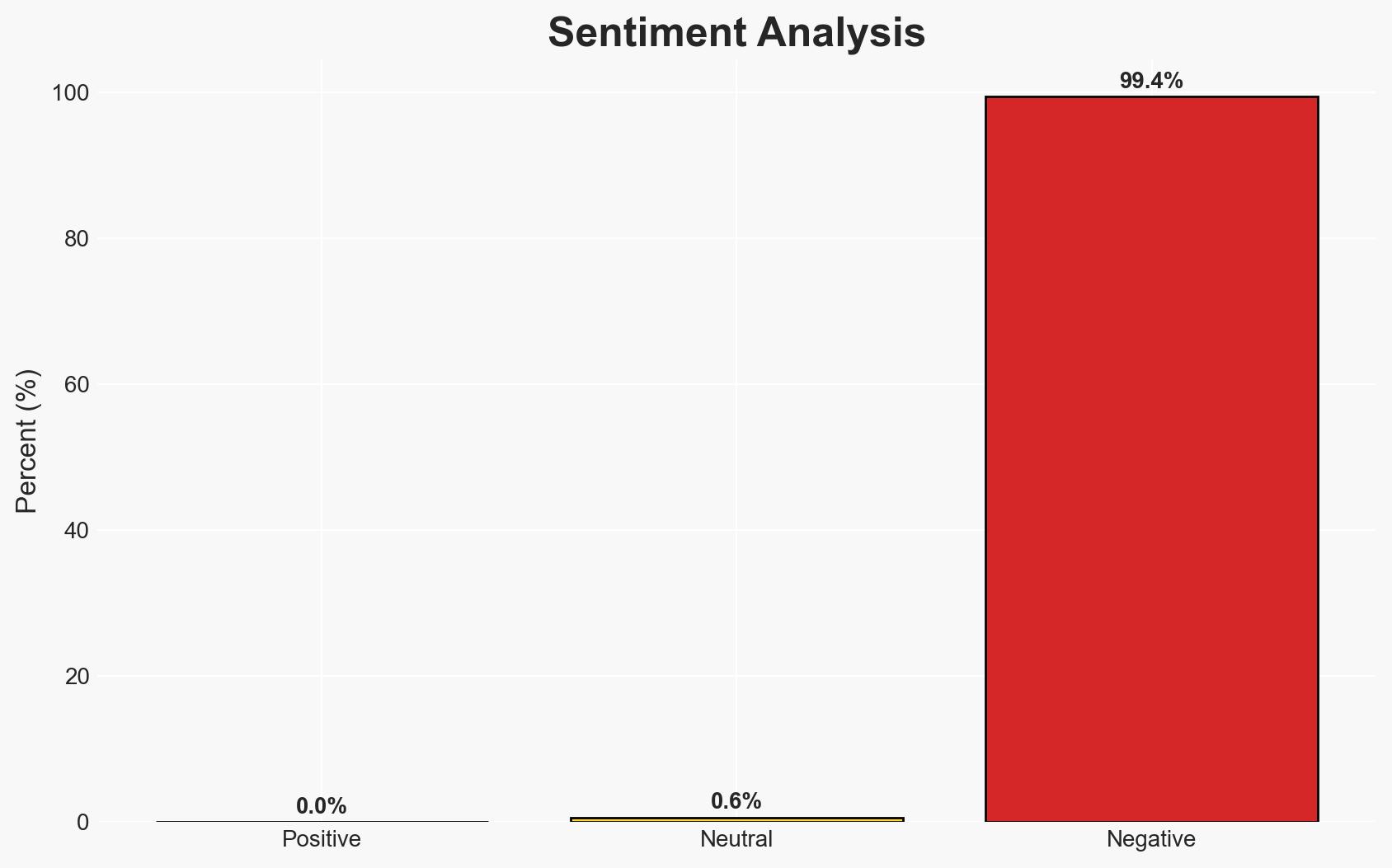
- Bias & Deception Risks: Potential bias in congressional reporting; Chinese diplomatic statements may aim to downplay the issue; risk of misattributing academic collaborations as military exploitation.
4. Implications and Strategic Risks
This development could lead to increased tensions between the U.S. and China, particularly in the tech and military domains. It may also prompt policy shifts in research funding and international collaborations.
- Political / Geopolitical: Escalation of U.S.-China tensions; potential for increased diplomatic confrontations.
- Security / Counter-Terrorism: Enhanced Chinese military capabilities could alter regional security dynamics.
- Cyber / Information Space: Potential for increased cyber espionage targeting U.S. research institutions.
- Economic / Social: Stricter research collaboration policies could impact academic and scientific communities.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase monitoring of DOE-funded collaborations; review and tighten policies on international research partnerships.
- Medium-Term Posture (1–12 months): Develop resilience measures in research funding; strengthen partnerships with allies to safeguard sensitive technologies.
- Scenario Outlook:
- Best: Effective policy changes mitigate risks, maintaining U.S. technological edge.
- Worst: Continued exploitation leads to significant U.S. national security vulnerabilities.
- Most-Likely: Incremental policy adjustments reduce but do not eliminate risks.
6. Key Individuals and Entities
- Department of Energy (DOE)
- Chinese military-affiliated researchers
- Chinese state-owned laboratories
- House Select Committee on the Chinese Communist Party
- House Committee on Education and the Workforce
- Chinese Embassy in Washington
7. Thematic Tags
cybersecurity, national security, U.S.-China relations, nuclear technology, research collaborations, military exploitation, cyber-espionage, policy recommendations
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us