Conversations remotely detected from cell phone vibrations researchers report – Psu.edu
Published on: 2025-08-10
Intelligence Report: Conversations remotely detected from cell phone vibrations researchers report – Psu.edu
1. BLUF (Bottom Line Up Front)
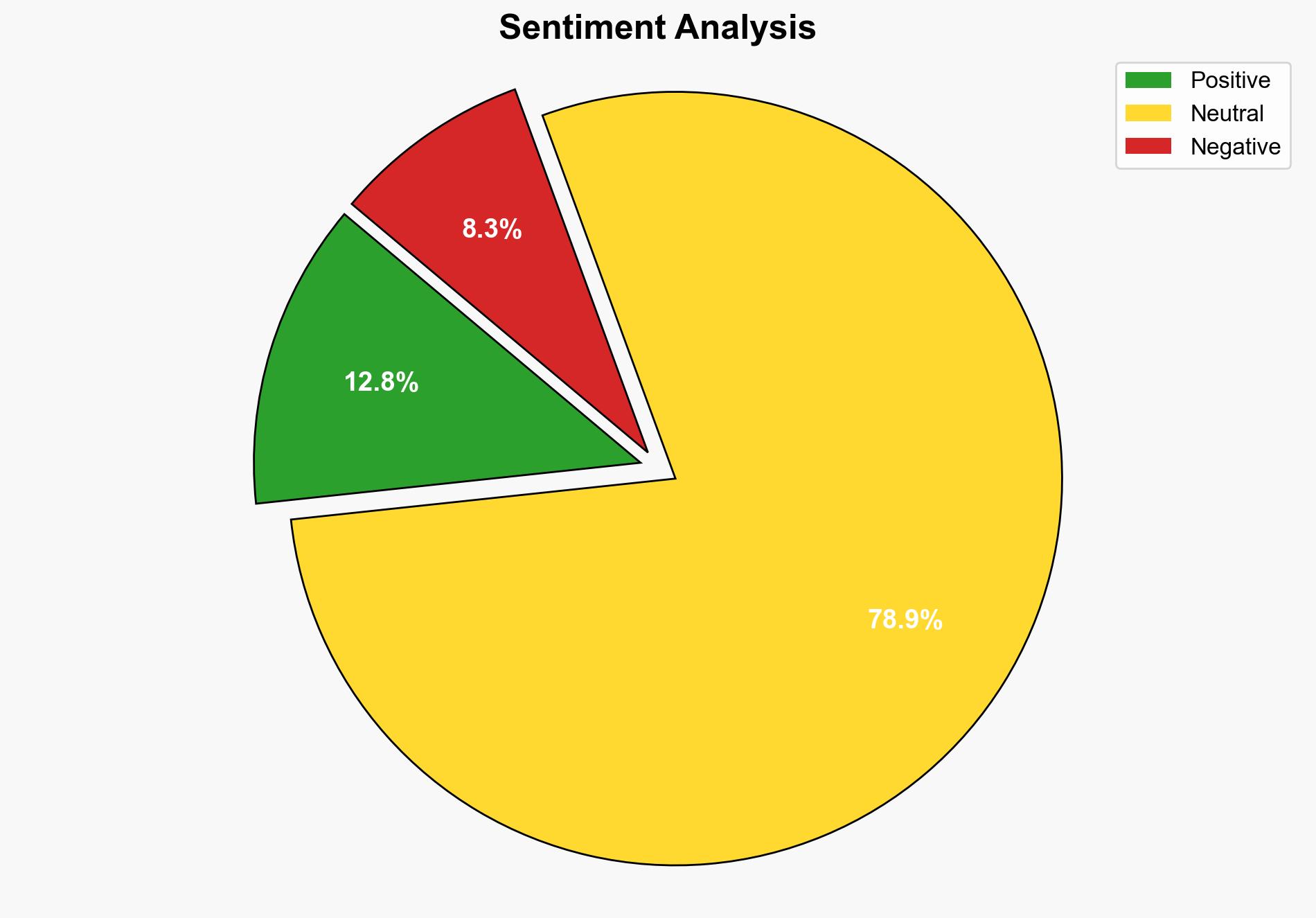
The research from Penn State suggests a potential privacy risk where conversations can be deciphered from cell phone vibrations using radar and AI. The most supported hypothesis is that this technology could be exploited by malicious actors to breach privacy. Confidence Level: Moderate. Recommended action is to enhance awareness and develop countermeasures to protect user privacy.
2. Competing Hypotheses
Hypothesis 1: The technology will primarily be used by researchers and developers to improve privacy measures and security protocols, leading to enhanced protection against eavesdropping.
Hypothesis 2: Malicious actors will exploit this technology to breach privacy, leading to increased surveillance and potential misuse in espionage or cybercrime.
Using ACH 2.0, Hypothesis 2 is better supported due to the rapid advancement in AI and its accessibility, which lowers the barrier for malicious use. The research highlights potential vulnerabilities that could be exploited before countermeasures are fully developed.
3. Key Assumptions and Red Flags
– Assumption: The technology will develop faster than countermeasures, allowing a window of vulnerability.
– Red Flag: The research assumes that the technology can be miniaturized and deployed without significant technical barriers.
– Blind Spot: The potential for regulatory or legal frameworks to mitigate misuse is not considered.
4. Implications and Strategic Risks
The ability to decipher conversations from vibrations could lead to significant privacy breaches, impacting personal, corporate, and national security. The technology could be used in espionage, cybercrime, and unauthorized surveillance, leading to geopolitical tensions and economic impacts if sensitive information is compromised.
5. Recommendations and Outlook
- Develop and promote privacy-enhancing technologies to counteract potential misuse.
- Encourage regulatory bodies to establish guidelines and legal frameworks to prevent exploitation.
- Scenario Projections:
- Best Case: Effective countermeasures are developed, and the technology is used to enhance security.
- Worst Case: Widespread misuse leads to significant privacy violations and geopolitical tensions.
- Most Likely: A mixed outcome where both beneficial and malicious uses emerge, necessitating ongoing vigilance and adaptation.
6. Key Individuals and Entities
– Suryoday Basak
– Mahanth Gowda
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus