Corporate Users Face Triple the Risk of Phishing Attacks Compared to Malware, SpyCloud Data Reveals
Published on: 2025-12-04
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: SpyCloud Data Shows Corporate Users 3x More Likely to Be Targeted by Phishing Than by Malware
1. BLUF (Bottom Line Up Front)
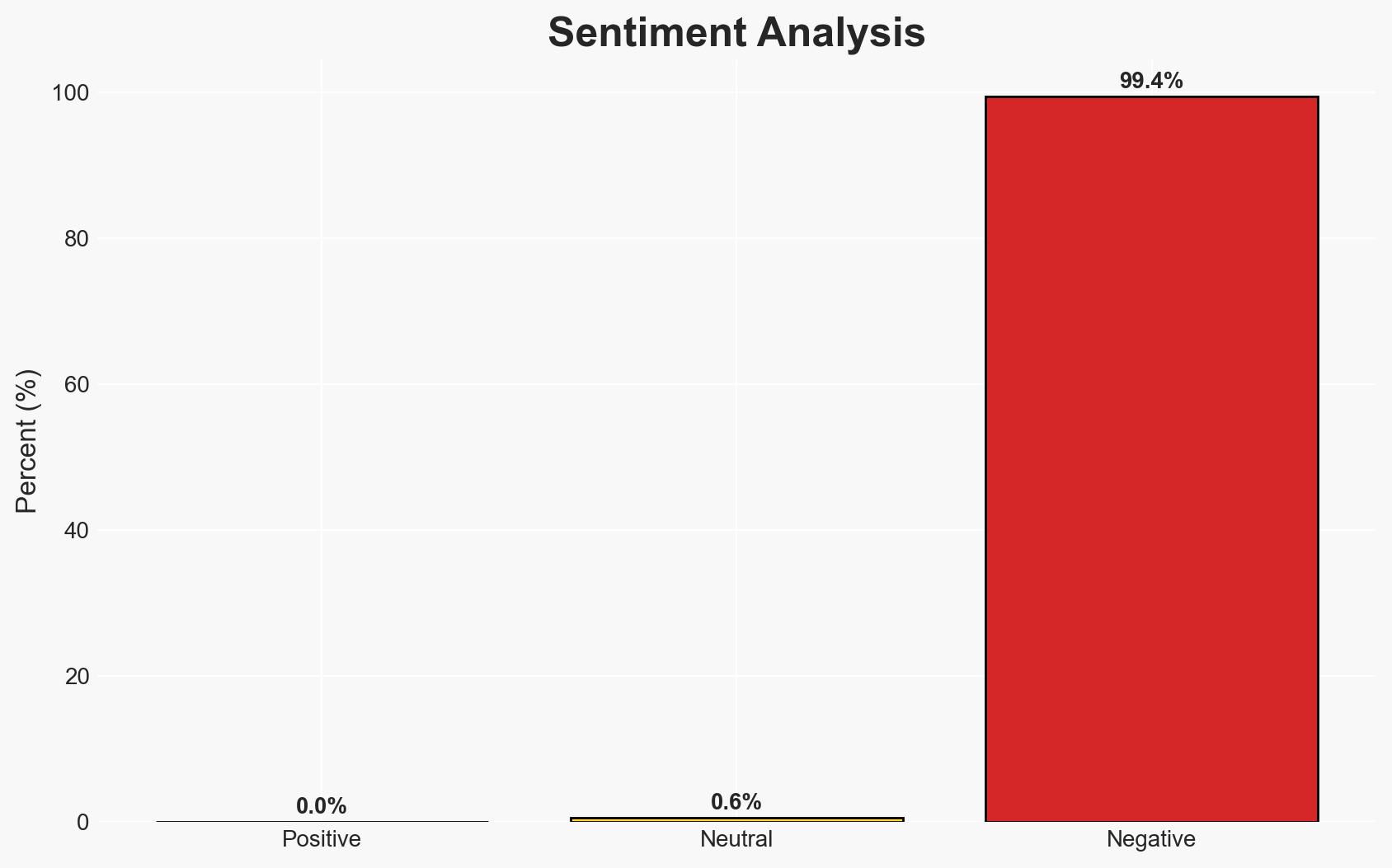
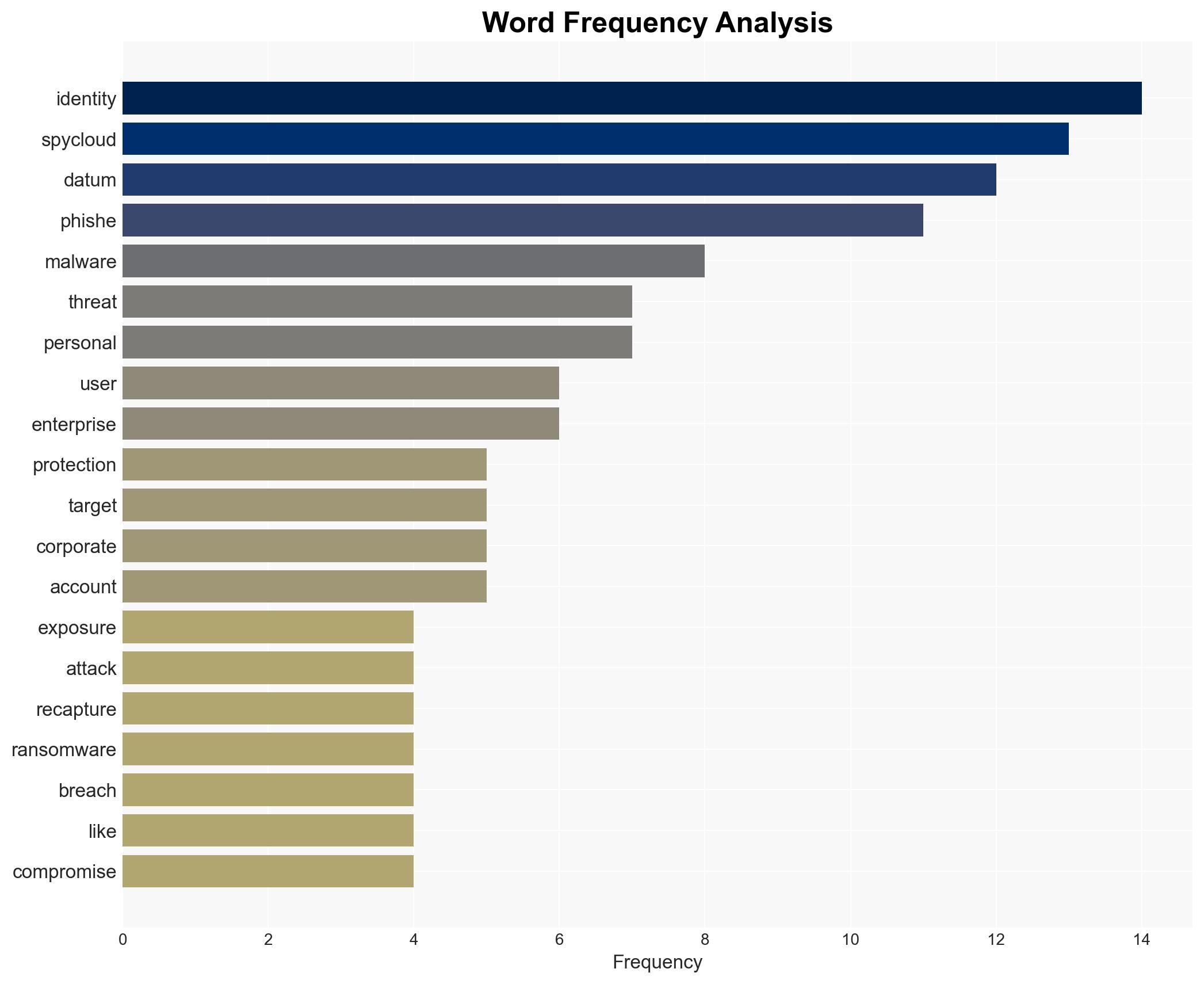
Phishing attacks targeting corporate users have surged by 400% year-over-year, making them three times more likely to be targeted than by malware. This trend indicates a strategic shift in cybercriminal tactics, with phishing becoming the primary entry point for further attacks such as ransomware. The affected entities are primarily corporate users and enterprises. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Cybercriminals are increasingly targeting corporate users with phishing due to its scalability and effectiveness in bypassing traditional defenses. This is supported by the 400% increase in phishing incidents and the use of phishing-as-a-service kits. However, the exact motivations and decision-making processes of threat actors remain uncertain.
- Hypothesis B: The rise in phishing attacks is a temporary trend driven by specific, short-term vulnerabilities or opportunities within corporate environments, such as increased remote work. This hypothesis is less supported due to the sustained nature of the trend and the strategic shift indicated by the data.
- Assessment: Hypothesis A is currently better supported due to the consistent increase in phishing incidents and the strategic use of phishing as a primary attack vector. Indicators that could shift this judgment include a sudden decrease in phishing incidents or a change in cybercriminal tactics.
3. Key Assumptions and Red Flags
- Assumptions:
- Phishing-as-a-service kits are widely available and used by low-skilled actors.
- Corporate environments remain vulnerable to phishing despite traditional defenses.
- Phishing will continue to be a preferred method for initial access by cybercriminals.
- Information Gaps: Detailed data on the specific industries or sectors most affected by the phishing surge is lacking.
- Bias & Deception Risks: Potential bias from SpyCloud as a commercial entity promoting its threat protection services; data may be selectively presented to highlight the effectiveness of their solutions.
4. Implications and Strategic Risks
The increase in phishing attacks could lead to more frequent and severe breaches, affecting corporate operations and data integrity. This trend may also influence cyber defense strategies and resource allocation.
- Political / Geopolitical: Increased cyber vulnerabilities could be exploited by state actors, escalating geopolitical tensions.
- Security / Counter-Terrorism: Enhanced phishing capabilities could be leveraged by terrorist groups for funding or operational purposes.
- Cyber / Information Space: The proliferation of phishing-as-a-service could democratize cybercrime, increasing the volume of attacks.
- Economic / Social: Successful phishing attacks could disrupt business operations, leading to economic losses and potential job impacts.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Increase monitoring of phishing trends and enhance employee training on phishing recognition and response.
- Medium-Term Posture (1–12 months): Develop partnerships with cybersecurity firms for real-time threat intelligence sharing and invest in advanced phishing detection technologies.
- Scenario Outlook:
- Best: Phishing incidents decline due to improved defenses and awareness, reducing overall cyber risk.
- Worst: Phishing attacks continue to rise, leading to significant breaches and economic damage.
- Most-Likely: Phishing remains a prevalent threat, necessitating ongoing adaptation of security measures.
6. Key Individuals and Entities
- Trevor Hilligoss, SpyCloud’s Head of Security Research
- Damon Fleury, SpyCloud’s Chief Product Officer
- SpyCloud (identity threat protection company)
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
Cybersecurity, phishing, cybercrime, ransomware, corporate security, identity protection, cyber defense
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us