Coyote malware is first-ever malware abusing Windows UI Automation – Securityaffairs.com
Published on: 2025-07-24
Intelligence Report: Coyote malware is first-ever malware abusing Windows UI Automation – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
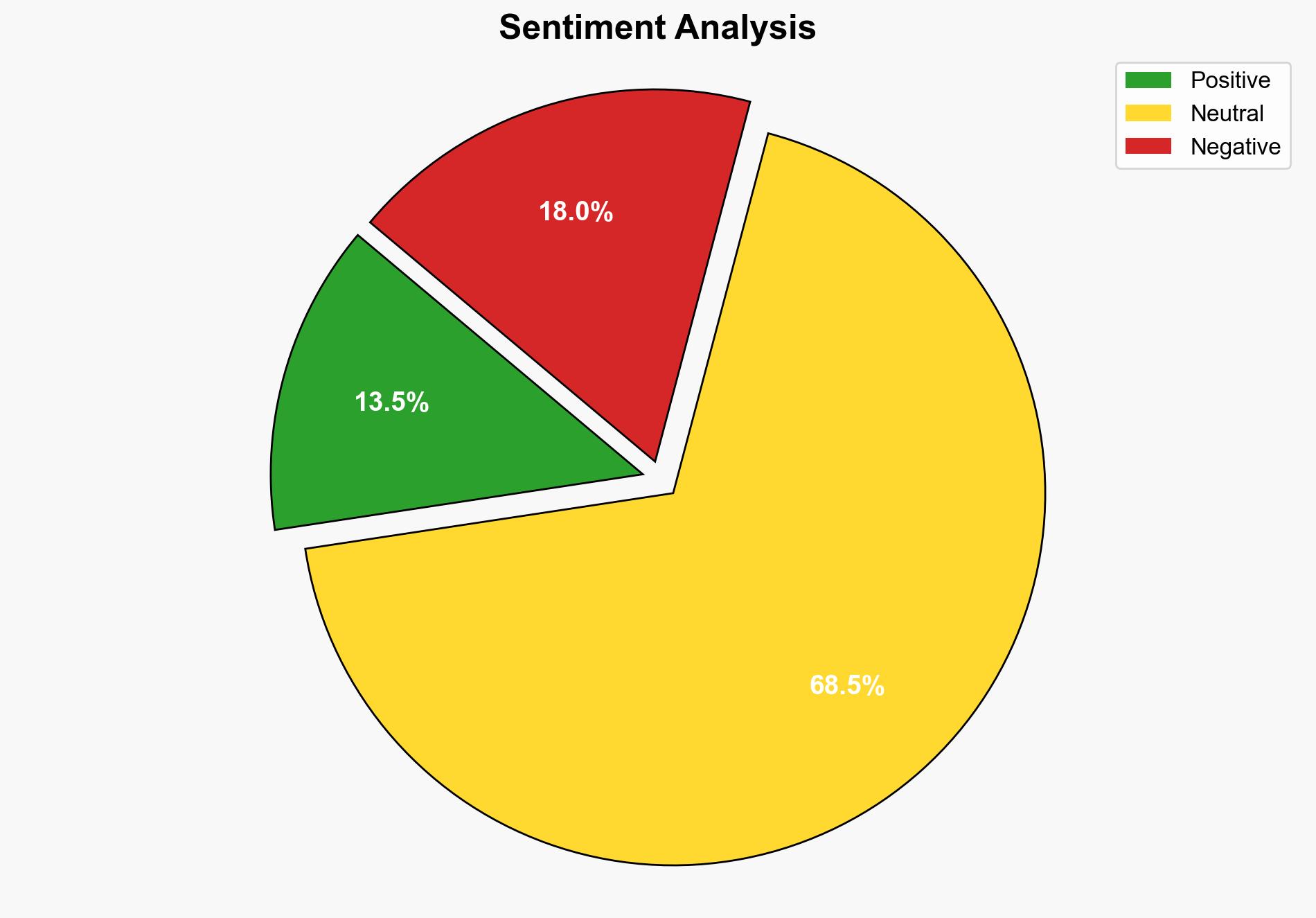
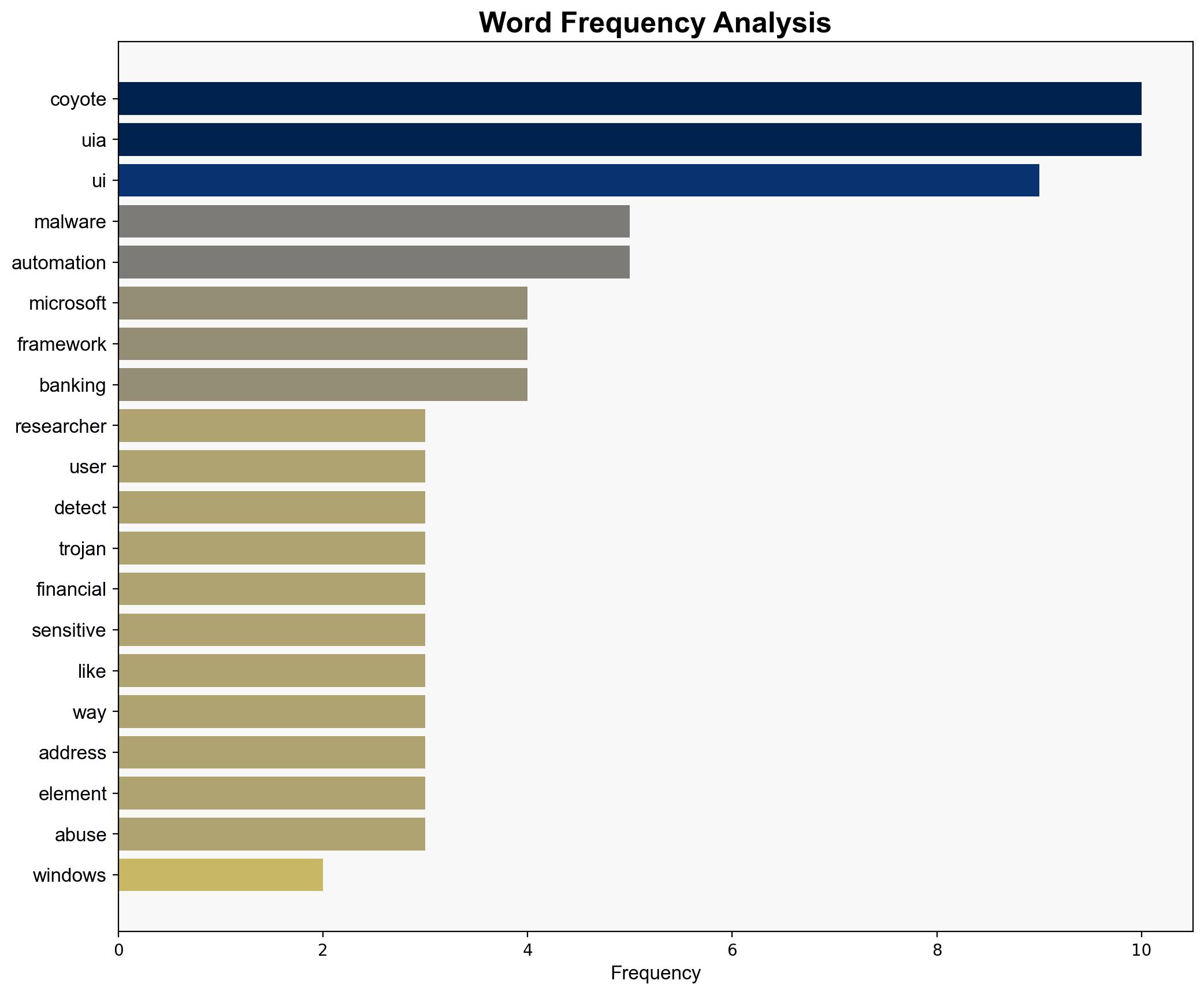
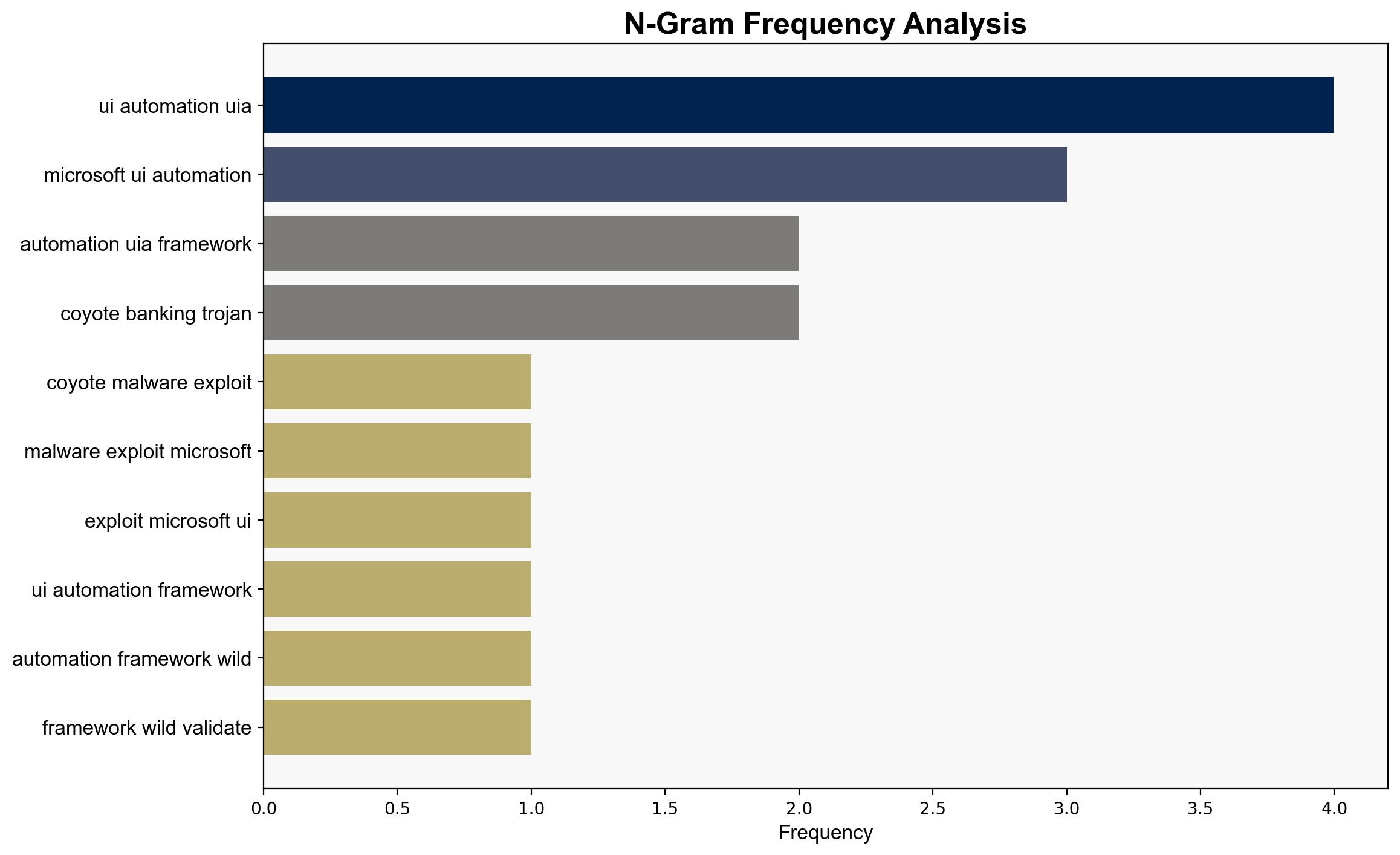
The Coyote malware represents a novel and potentially significant threat by exploiting the Windows UI Automation framework to target financial data, primarily affecting Brazilian users. The most supported hypothesis is that this malware will lead to increased exploitation of UI Automation by other threat actors, posing a growing cybersecurity risk. Confidence Level: Moderate. Recommended action includes enhanced monitoring of UI Automation activities and proactive threat intelligence sharing.
2. Competing Hypotheses
1. **Hypothesis A**: The Coyote malware is an isolated incident, primarily targeting Brazilian financial institutions, and will have limited global impact.
2. **Hypothesis B**: The Coyote malware signifies a broader trend of exploiting Windows UI Automation, leading to widespread adoption by various threat actors globally.
Using ACH 2.0, Hypothesis B is better supported due to the malware’s innovative use of UI Automation, which is likely to be attractive to other cybercriminals seeking stealthy methods to harvest sensitive data.
3. Key Assumptions and Red Flags
– **Assumptions**:
– The UI Automation framework will continue to be vulnerable to similar exploits.
– Other threat actors have the capability and motivation to adopt this method.
– **Red Flags**:
– Lack of detailed technical analysis on how the UI Automation is specifically exploited.
– Potential underestimation of the malware’s adaptability to other regions or sectors.
4. Implications and Strategic Risks
The exploitation of UI Automation could lead to a new wave of malware that is harder to detect and mitigate, increasing risks for financial institutions globally. This could result in significant economic losses and undermine trust in digital financial services. Geopolitically, countries with less robust cybersecurity defenses may become primary targets, exacerbating regional security disparities.
5. Recommendations and Outlook
- Enhance cybersecurity protocols specifically around UI Automation activities, including monitoring and anomaly detection.
- Foster international collaboration for threat intelligence sharing to preemptively identify and counter similar threats.
- Scenario-based Projections:
- Best Case: Rapid patching and awareness campaigns limit the spread and impact of similar malware.
- Worst Case: Widespread adoption of this technique leads to a surge in financial data breaches globally.
- Most Likely: Gradual increase in similar attacks, with a focus on regions with weaker cybersecurity defenses.
6. Key Individuals and Entities
– FortiGuard Labs (researchers who detected the campaign)
– Microsoft (developer of the UI Automation framework)
7. Thematic Tags
national security threats, cybersecurity, financial security, regional focus, malware evolution