Cozy Bear targets EU diplomats with wine-tasting invites again – Help Net Security
Published on: 2025-04-16
Intelligence Report: Cozy Bear targets EU diplomats with wine-tasting invites again – Help Net Security
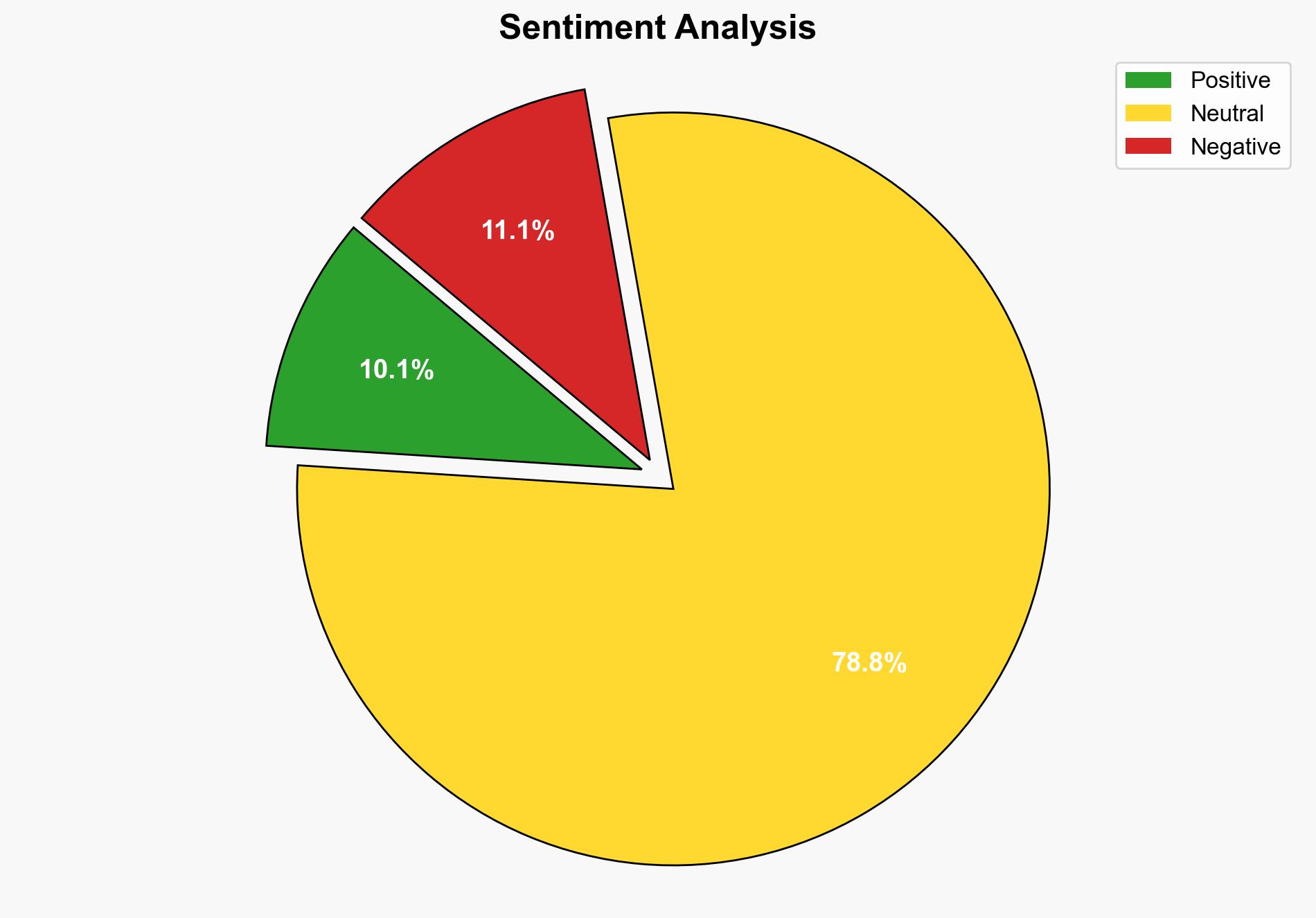
1. BLUF (Bottom Line Up Front)
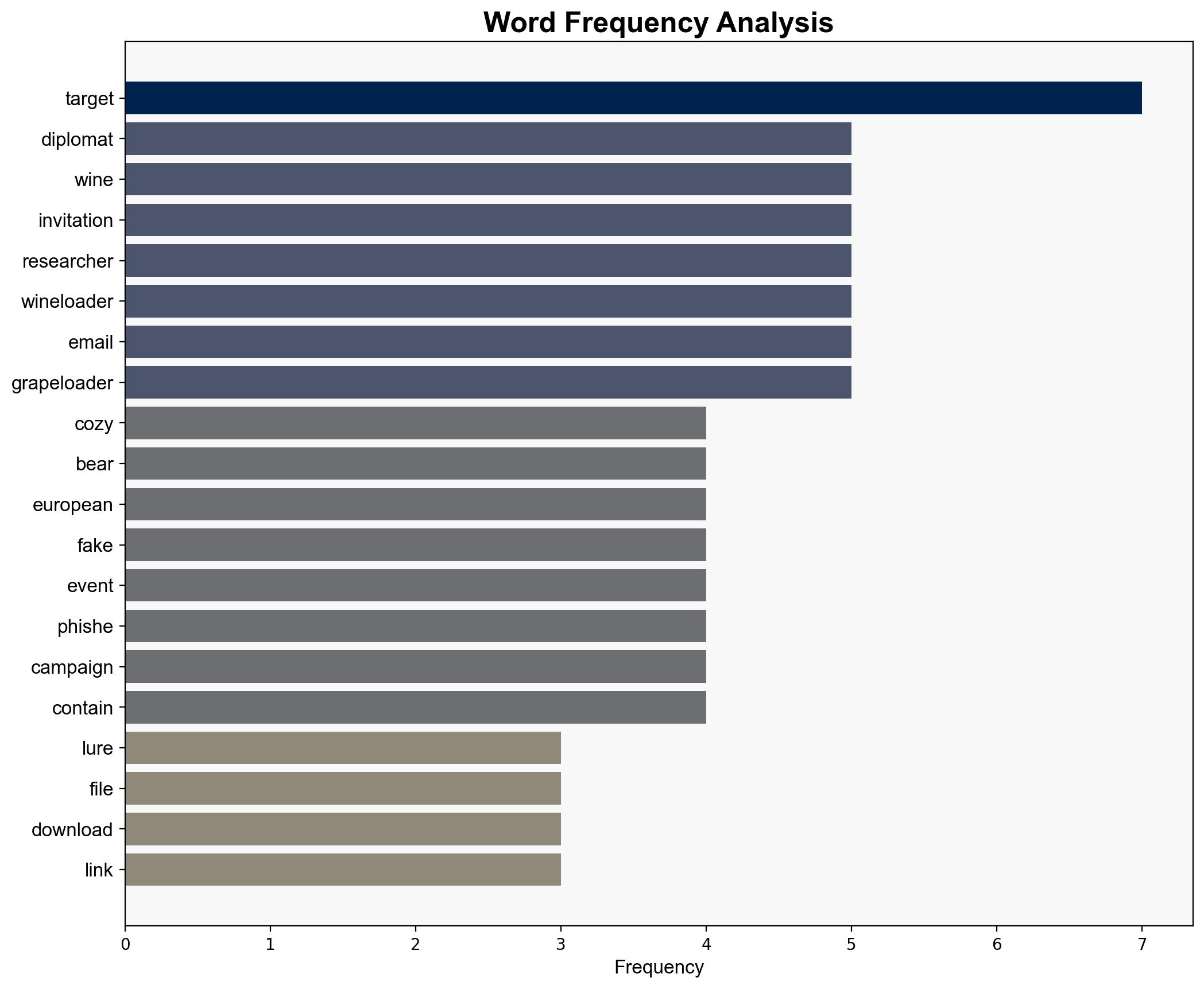
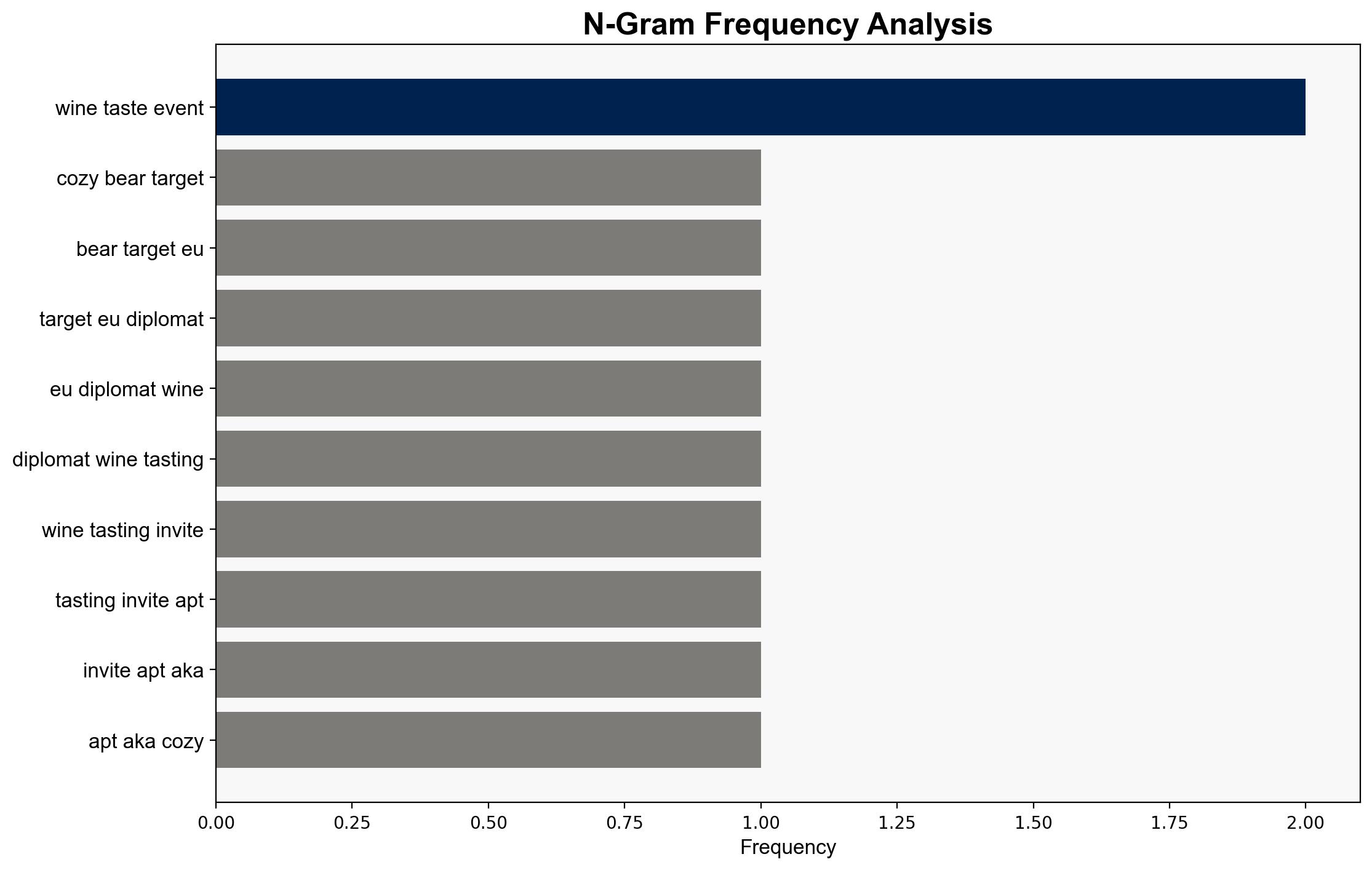
Cozy Bear, also known as APT29, has resumed targeting European diplomats using phishing emails disguised as wine-tasting invitations. This campaign aims to deploy the WINELOADER backdoor, leveraging GRAPELOADER to bypass security measures. Immediate attention is required to enhance email filtering and awareness training to mitigate these threats.
2. Detailed Analysis
The following structured analytic techniques have been applied:
Analysis of Competing Hypotheses (ACH)
The primary motivation behind these attacks is likely espionage, aiming to gather sensitive diplomatic information. The use of social engineering tactics, such as fake invitations, suggests a focus on exploiting human vulnerabilities rather than technical ones.
SWOT Analysis
Strengths: Advanced evasion techniques and targeted social engineering increase the campaign’s effectiveness.
Weaknesses: Reliance on user interaction to initiate the attack.
Opportunities: Increased awareness and improved security protocols can reduce the success rate of such phishing attempts.
Threats: Persistent targeting of high-value diplomatic targets poses significant risks to national security.
Indicators Development
Warning signs include unsolicited invitations to events, especially those claiming to be from high-profile entities. The presence of domains hosting malicious links and the use of specific file names like “wine.zip” should be monitored.
3. Implications and Strategic Risks
The recurring use of social engineering by Cozy Bear highlights a persistent threat to diplomatic security. Successful breaches could lead to compromised negotiations and intelligence leaks, affecting political stability and international relations.
4. Recommendations and Outlook
- Enhance email filtering systems to detect and block phishing attempts more effectively.
- Conduct regular cybersecurity awareness training for diplomats and government officials.
- Implement multi-factor authentication to add an additional layer of security.
- Scenario-based projections suggest that without improved defenses, similar campaigns will continue, potentially increasing in sophistication.
5. Key Individuals and Entities
No specific individuals are named in the report. The focus remains on the entity known as Cozy Bear or APT29.