Critical auth bypass bug in CrushFTP now exploited in attacks – BleepingComputer
Published on: 2025-04-01
Intelligence Report: Critical auth bypass bug in CrushFTP now exploited in attacks – BleepingComputer
1. BLUF (Bottom Line Up Front)
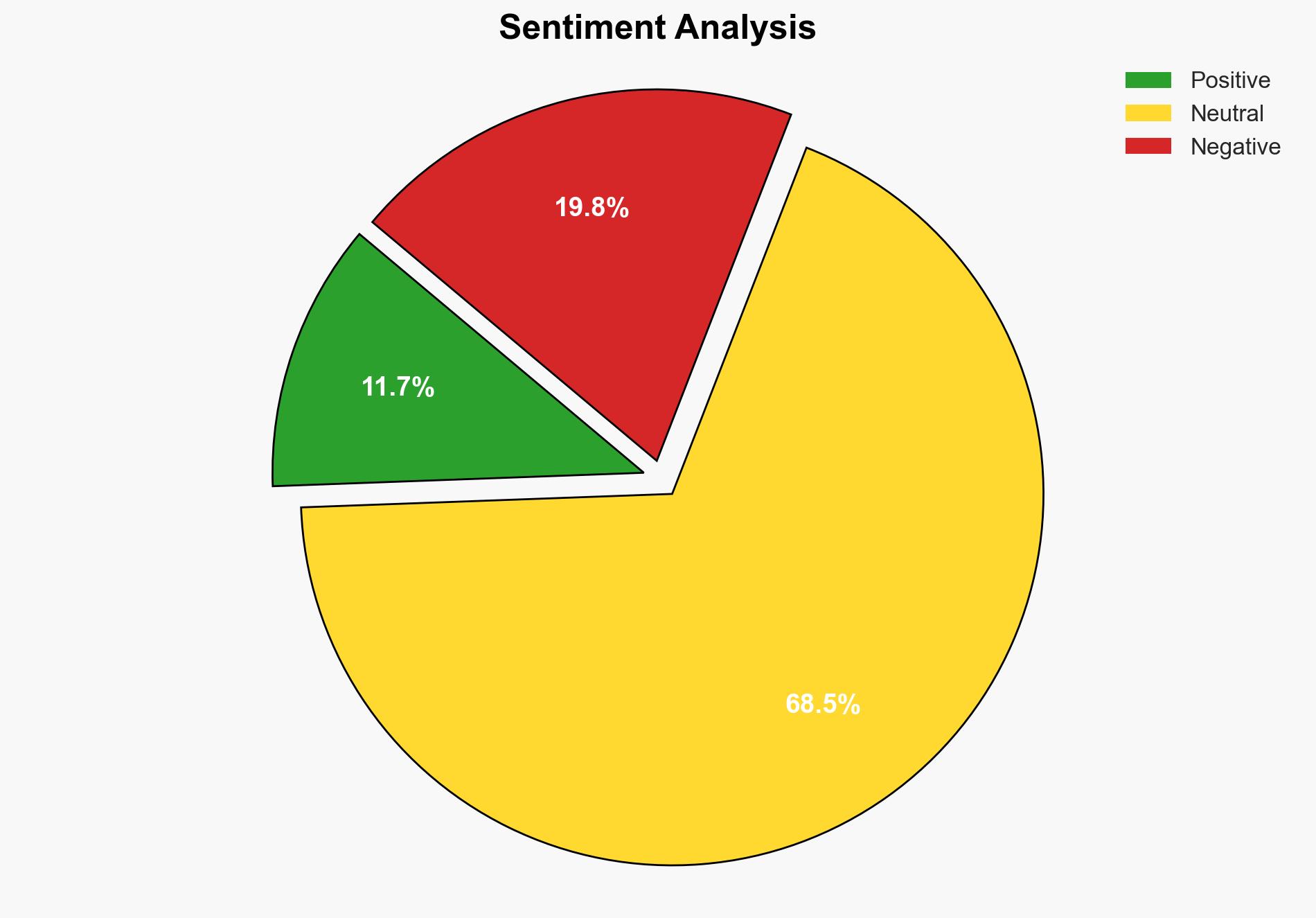
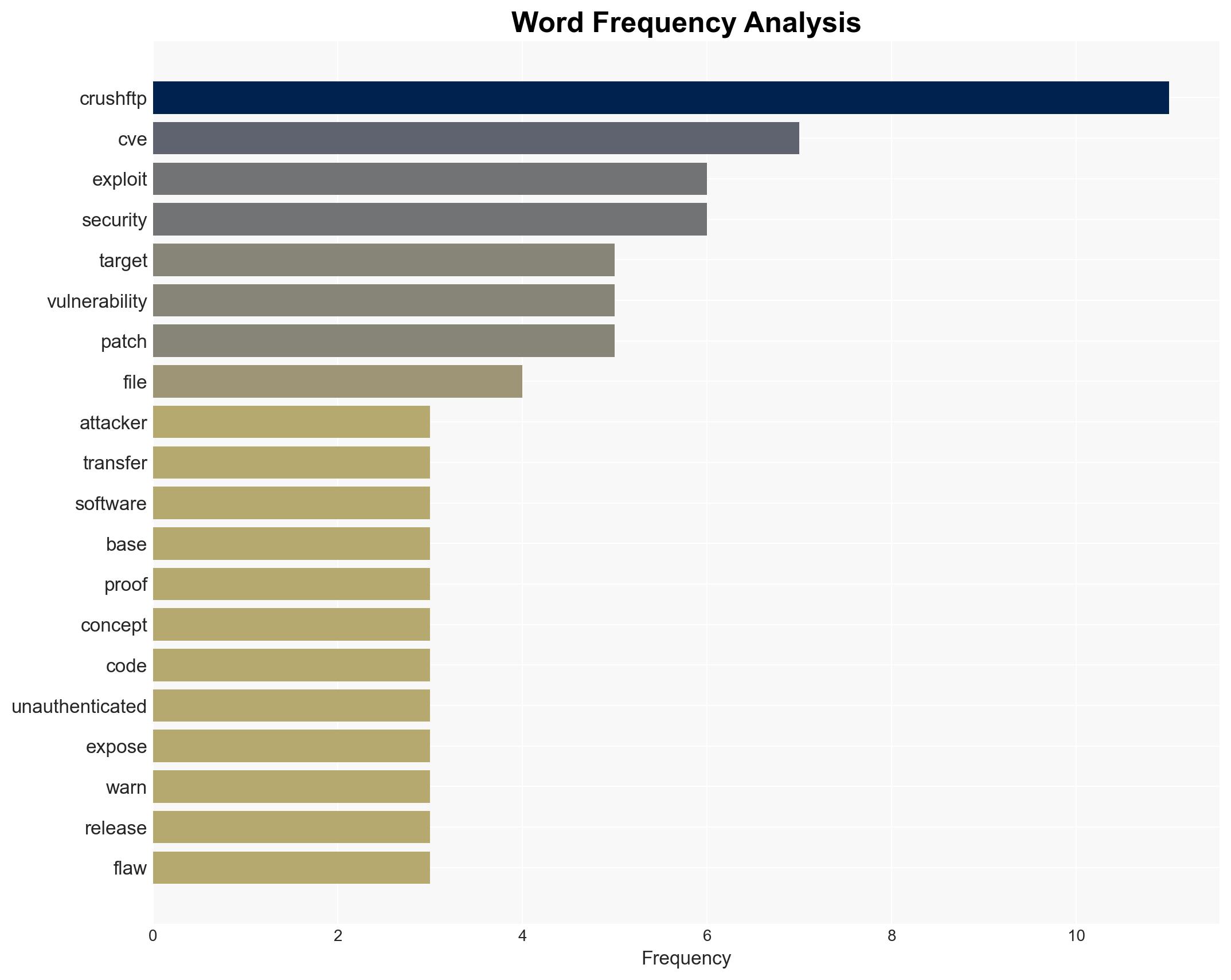
A critical authentication bypass vulnerability in the CrushFTP file transfer software is currently being exploited in the wild. This vulnerability allows remote attackers to gain unauthenticated access to devices running unpatched versions of CrushFTP. Immediate action is required to patch affected systems to prevent unauthorized access and potential data breaches. The vulnerability is being actively targeted by threat actors, including ransomware groups, and poses a significant risk to organizations using this software.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
The vulnerability, identified as CVE, allows attackers to bypass authentication mechanisms in CrushFTP, leading to unauthorized access. Publicly available proof-of-concept (PoC) code has facilitated the exploitation of this flaw. Security monitoring platforms, such as Shadowserver, have detected numerous exploitation attempts targeting internet-exposed CrushFTP servers. The vulnerability is particularly concerning due to its potential use by ransomware gangs, notably linked to data theft attacks. Historical context shows that similar vulnerabilities, such as those in Accelion FTA and GoAnywhere MFT, have been exploited for significant data breaches.
3. Implications and Strategic Risks
The exploitation of this vulnerability poses several strategic risks:
- National Security: Potential unauthorized access to sensitive government data if government entities use CrushFTP.
- Regional Stability: Increased cyber threats could destabilize regions heavily reliant on digital infrastructure.
- Economic Interests: Data breaches could lead to financial losses and damage to organizational reputations.
The involvement of ransomware groups increases the likelihood of data theft and extortion, further exacerbating these risks.
4. Recommendations and Outlook
Recommendations:
- Organizations should immediately apply the latest security patches provided by CrushFTP to mitigate this vulnerability.
- Implement network segmentation and enable DMZ options to protect critical systems from unauthorized access.
- Conduct regular security audits and vulnerability assessments to identify and address potential security gaps.
- Enhance monitoring capabilities to detect and respond to exploitation attempts promptly.
Outlook:
Best-case scenario: Rapid patch deployment and increased security measures lead to a significant reduction in exploitation attempts, minimizing potential damage.
Worst-case scenario: Delayed patching and inadequate security measures result in widespread data breaches and financial losses, with prolonged recovery efforts.
Most likely scenario: A moderate level of exploitation continues as organizations gradually implement security updates and enhance defenses.
5. Key Individuals and Entities
The report mentions significant individuals and organizations involved in the discovery, reporting, and mitigation of the vulnerability. Notable entities include:
- ProjectDiscovery
- Shadowserver
- CrowdStrike
- CISA
- Mitre