Critical BeyondTrust Vulnerability Exploited for Web Shells, Backdoors, and Data Theft Across Multiple Sectors
Published on: 2026-02-20
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: BeyondTrust Flaw Used for Web Shells Backdoors and Data Exfiltration
1. BLUF (Bottom Line Up Front)
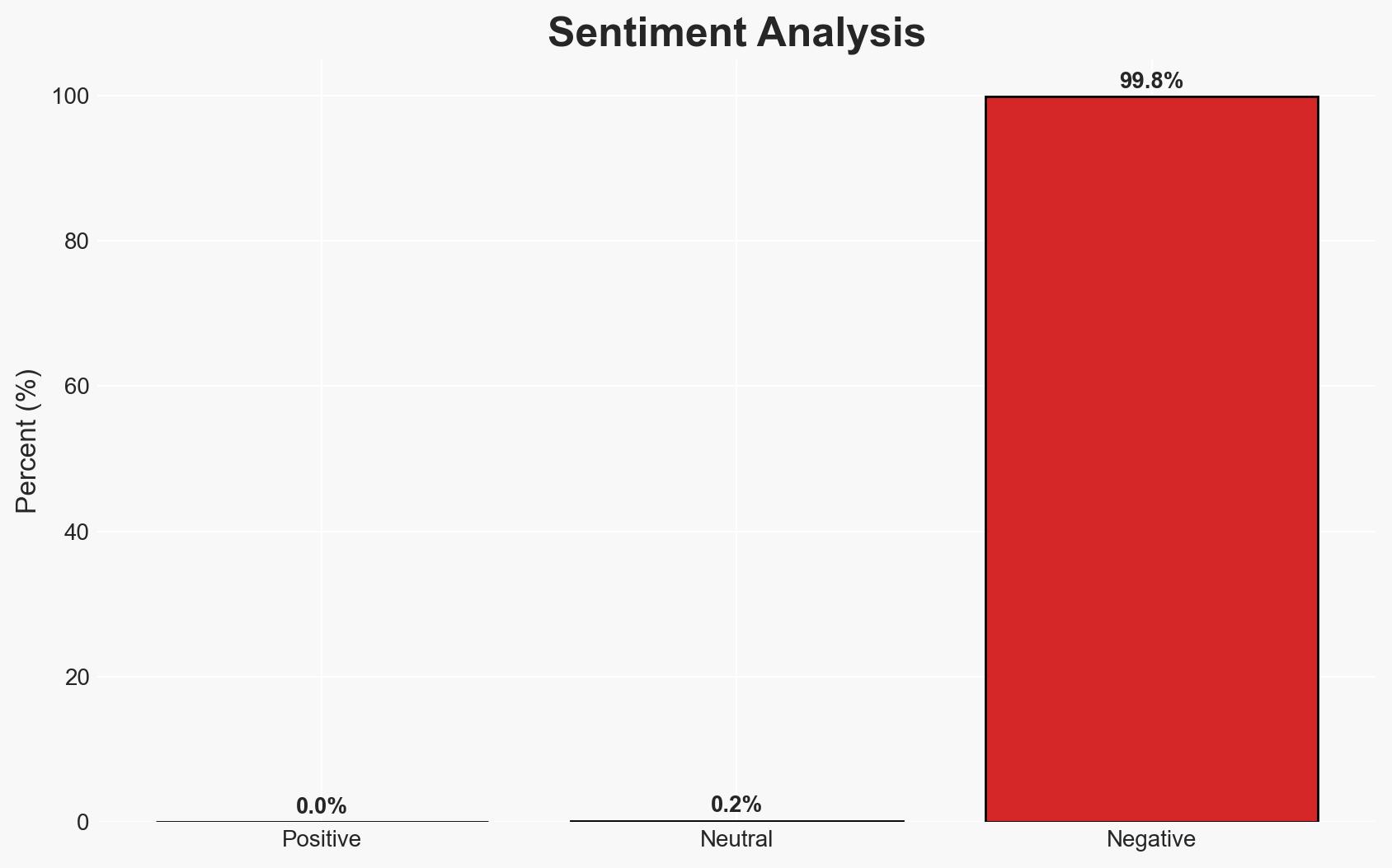
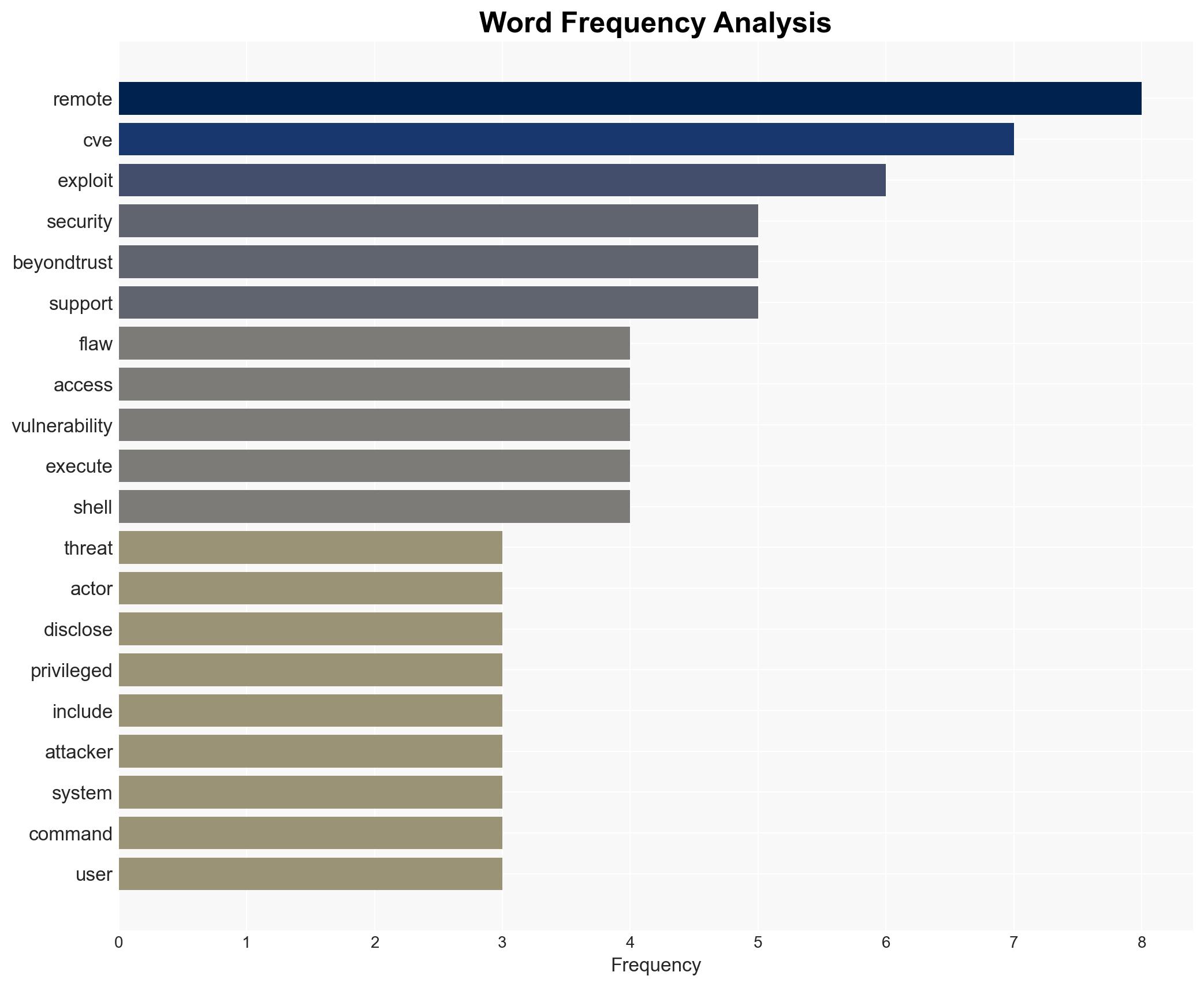
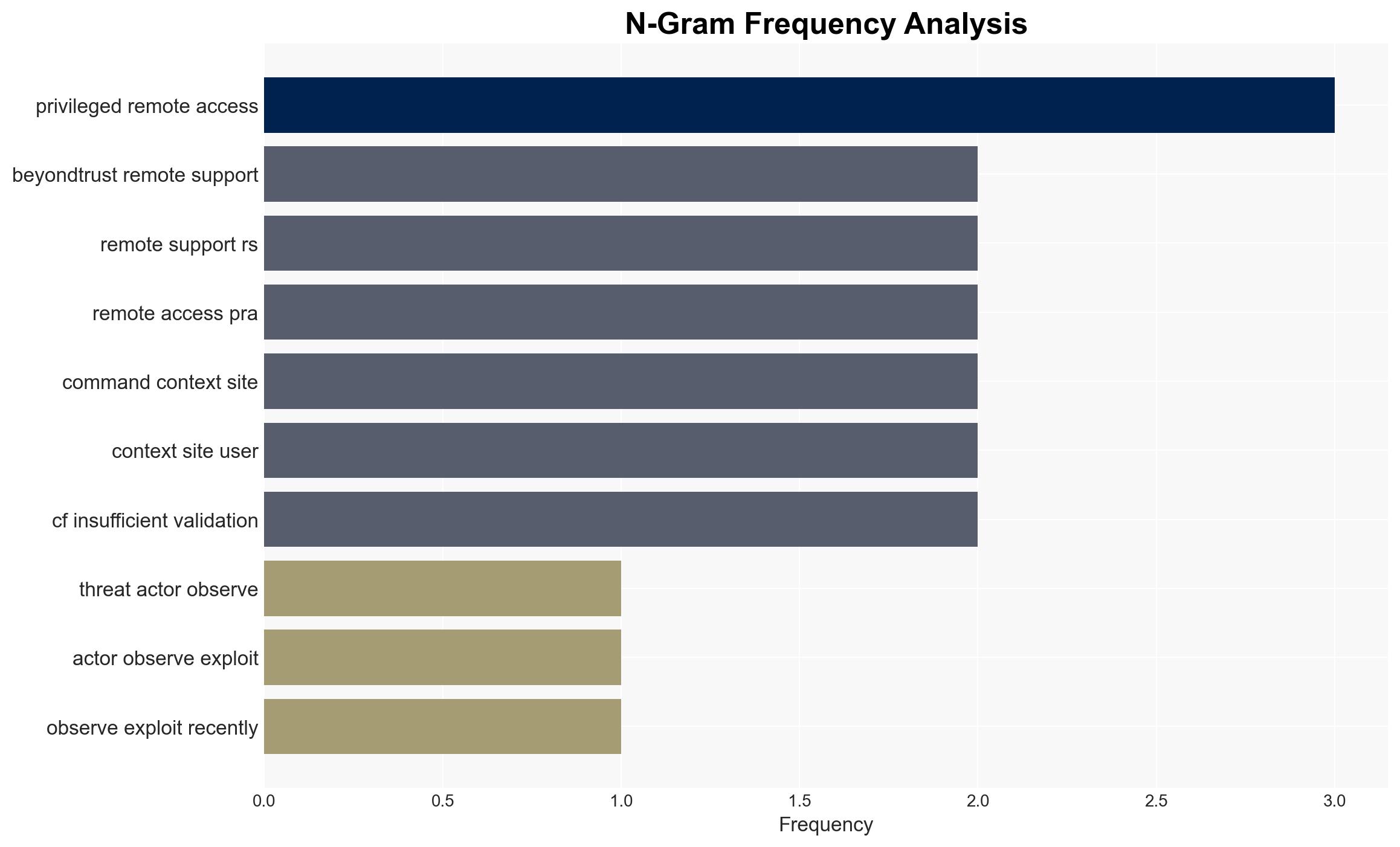
The exploitation of the BeyondTrust vulnerability (CVE-2026-1731) is being actively leveraged by threat actors to conduct cyber operations against multiple sectors across several countries. The most likely hypothesis is that sophisticated threat actors, potentially state-sponsored, are behind these attacks due to the complexity and scope of the operations. This poses significant risks to affected sectors, particularly in terms of data exfiltration and system compromise. Overall confidence in this assessment is moderate, given the available evidence and ongoing nature of the threat.
2. Competing Hypotheses
- Hypothesis A: The attacks exploiting CVE-2026-1731 are primarily conducted by state-sponsored actors, possibly linked to China, given the sophistication and the historical context of similar vulnerabilities being exploited by such groups. Evidence includes the complexity of the operations and the potential link to previously exploited vulnerabilities by China-nexus actors. However, direct attribution remains uncertain.
- Hypothesis B: The attacks are being carried out by independent cybercriminal groups seeking financial gain through data theft and system compromise. This hypothesis is supported by the broad targeting of financially lucrative sectors and the use of common cybercriminal tools like web shells and RATs. Contradicting evidence includes the high level of coordination and technical expertise required, which is more characteristic of state-sponsored activities.
- Assessment: Hypothesis A is currently better supported due to the sophistication of the attack methods and the strategic targeting of critical sectors. Indicators such as increased targeting of geopolitical adversaries or further technical analysis linking the attacks to known state-sponsored groups could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: The vulnerability is being exploited by actors with significant resources and technical expertise; the targeted sectors are of strategic interest to state actors; the exploitation is part of a broader campaign.
- Information Gaps: Specific attribution to a particular nation-state or group; detailed technical analysis of the malware used; insights into the attackers’ long-term objectives.
- Bias & Deception Risks: Potential bias in attributing sophisticated attacks to state actors without conclusive evidence; reliance on open-source reporting which may be incomplete or misleading.
4. Implications and Strategic Risks
The exploitation of this vulnerability could lead to significant disruptions in targeted sectors, with potential for data breaches and operational impacts. Over time, this could escalate tensions between affected nations and suspected state actors.
- Political / Geopolitical: Increased geopolitical tensions if state-sponsored attribution is confirmed, particularly involving China and Western nations.
- Security / Counter-Terrorism: Heightened threat environment for critical infrastructure and key sectors, necessitating increased cybersecurity measures.
- Cyber / Information Space: Potential for further cyber operations leveraging similar vulnerabilities; increased focus on input validation vulnerabilities.
- Economic / Social: Economic impacts due to data breaches and operational disruptions; potential loss of trust in affected sectors’ cybersecurity capabilities.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of BeyondTrust systems for signs of exploitation; apply patches and mitigations; conduct threat hunting for indicators of compromise.
- Medium-Term Posture (1–12 months): Develop partnerships for threat intelligence sharing; invest in cybersecurity resilience and incident response capabilities; conduct regular security audits.
- Scenario Outlook:
- Best: Rapid patching and mitigation efforts curtail the exploitation, reducing impact.
- Worst: Widespread exploitation leads to significant data breaches and geopolitical tensions.
- Most-Likely: Continued exploitation with moderate impact, prompting increased cybersecurity measures and international cooperation.
6. Key Individuals and Entities
- BeyondTrust (affected vendor)
- Palo Alto Networks Unit 42 (reporting entity)
- Justin Moore (security researcher)
- Not clearly identifiable from open sources in this snippet for specific threat actors.
7. Thematic Tags
cybersecurity, state-sponsored threats, data exfiltration, vulnerability exploitation, geopolitical tensions, critical infrastructure, cyber defense
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us