Critical flaw in Apache Parquets Java Library allows remote code execution – Securityaffairs.com
Published on: 2025-04-04
Intelligence Report: Critical flaw in Apache Parquets Java Library allows remote code execution – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
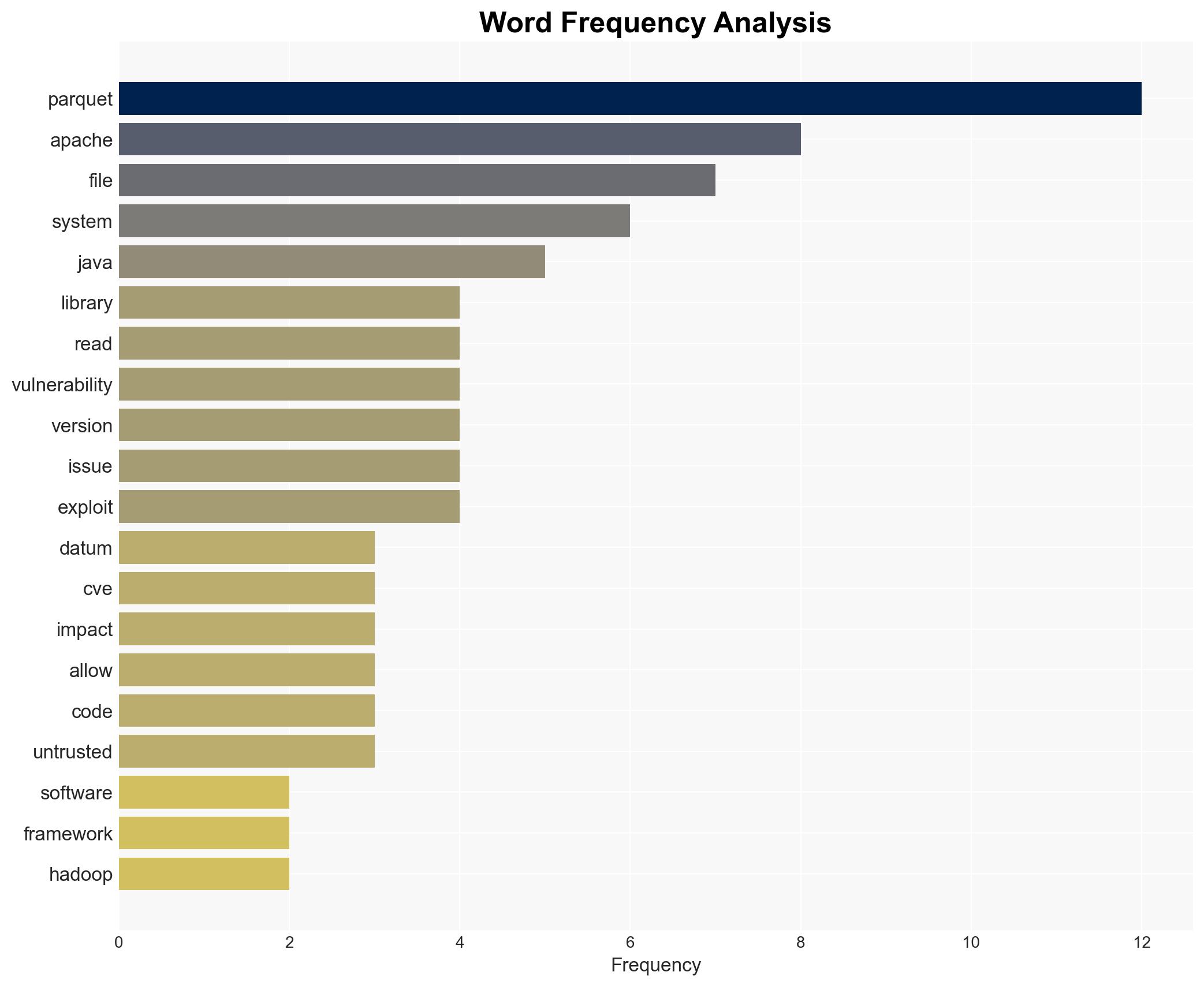
A critical vulnerability in the Apache Parquet Java Library has been identified, allowing remote code execution (RCE) through deserialization of untrusted data. This flaw affects systems importing Parquet files, particularly from untrusted sources. Immediate action is required to upgrade to the latest version of the library and implement robust input validation to mitigate potential exploitation.
2. Detailed Analysis
The following structured analytic techniques have been applied for this analysis:
General Analysis
The vulnerability, tracked as CVE, has a high CVSS score indicating severe impact potential. It affects major big data frameworks such as Apache Hadoop, Apache Spark, and Apache Flink. The flaw allows attackers to execute arbitrary code by tricking systems into reading specially crafted Parquet files. The vulnerability is present in versions prior to the latest update and poses a significant risk to data confidentiality, integrity, and availability.
3. Implications and Strategic Risks
The vulnerability poses a substantial risk to national security and economic interests due to its potential exploitation by threat actors. Systems relying on big data frameworks are particularly vulnerable, potentially leading to data breaches, service disruptions, and unauthorized access to sensitive information. The widespread use of Apache Parquet in data processing frameworks amplifies the risk across various sectors.
4. Recommendations and Outlook
Recommendations:
- Upgrade the Apache Parquet Java Library to the latest version immediately to mitigate the vulnerability.
- Implement stringent input validation for Parquet files, especially those from untrusted sources.
- Enhance monitoring and logging to detect suspicious activities related to Parquet file processing.
- Conduct regular security audits and vulnerability assessments of big data frameworks.
Outlook:
Best-case scenario: Rapid adoption of recommended security measures leads to minimal exploitation incidents and enhanced system resilience.
Worst-case scenario: Failure to address the vulnerability results in widespread exploitation, leading to significant data breaches and operational disruptions.
Most likely outcome: Organizations will gradually implement security updates and recommendations, reducing but not eliminating the risk of exploitation.
5. Key Individuals and Entities
The report references endor lab as the entity disclosing the vulnerability and providing advisory guidance. No specific individuals are mentioned.