Critical Flaw in FortiCloud SSO Exposes Over 25,000 Devices to Active Cyber Attacks
Published on: 2025-12-22
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: FortiCloud SSO Exposure 25000 Devices Vulnerable and Cyber Attacks Active
1. BLUF (Bottom Line Up Front)
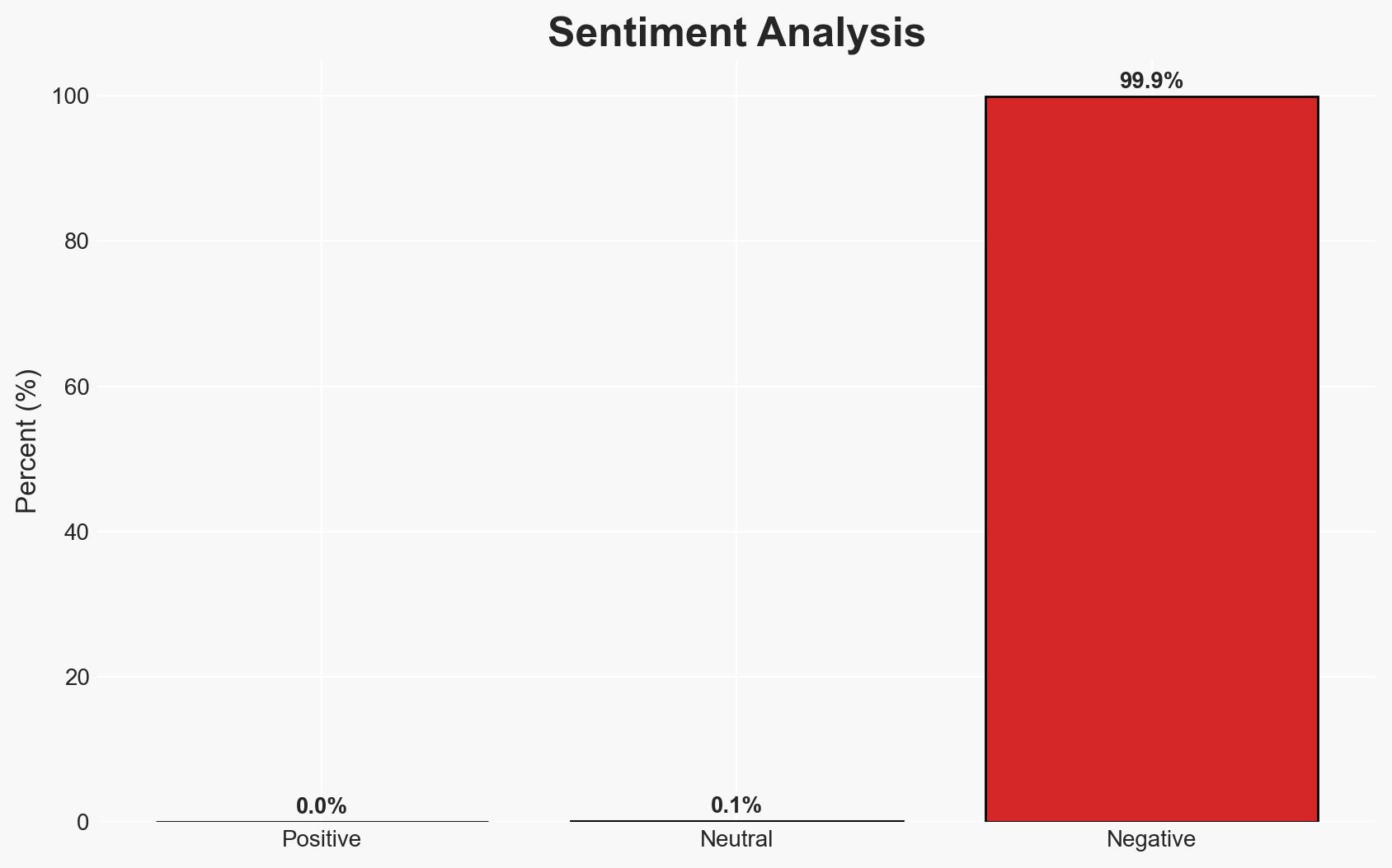
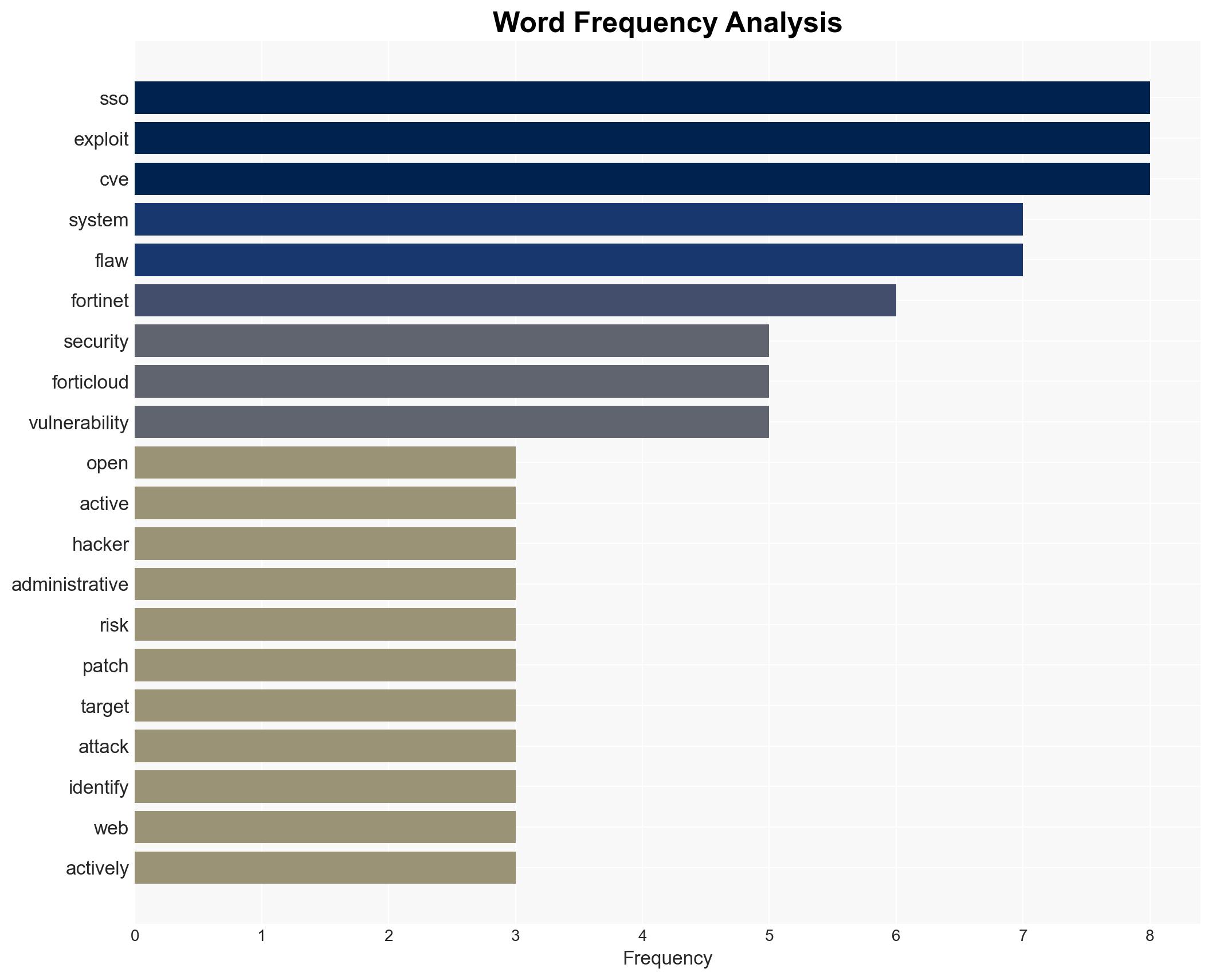
A critical vulnerability in FortiCloud’s Single Sign-On (SSO) system has exposed over 25,000 devices to potential cyber attacks, with active exploitation reported. Organizations using FortiCloud SSO are at significant risk and must take immediate action to mitigate threats. The most likely hypothesis is that cybercriminals will continue to exploit this vulnerability until comprehensive patches are applied. Overall confidence in this assessment is moderate due to incomplete data on patch application rates.
2. Competing Hypotheses
- Hypothesis A: Cybercriminals will continue to exploit the FortiCloud SSO vulnerability extensively, leading to widespread network compromises. This is supported by reports of active exploitation and the large number of unpatched systems. However, the extent of patch adoption remains unclear, which is a key uncertainty.
- Hypothesis B: Organizations will rapidly patch the vulnerability, significantly reducing the number of exploitable systems and limiting the impact of the attacks. This hypothesis is contradicted by the historical slow response to similar vulnerabilities and the current active exploitation reports.
- Assessment: Hypothesis A is currently better supported due to the ongoing exploitation and the significant number of vulnerable systems. Indicators such as increased patch adoption rates could shift this judgment towards Hypothesis B.
3. Key Assumptions and Red Flags
- Assumptions: Organizations have the capability to apply patches promptly; the vulnerability is not being exploited by state-sponsored actors; Fortinet’s patches are effective in mitigating the vulnerability.
- Information Gaps: The exact number of systems that have been patched; the identity and motives of the exploiting actors; the full scope of the data compromised in successful attacks.
- Bias & Deception Risks: Potential underreporting of successful exploits due to reputational concerns; reliance on vendor-provided information which may downplay the severity or spread of the issue.
4. Implications and Strategic Risks
This vulnerability could lead to significant disruptions if not addressed, potentially affecting critical infrastructure and sensitive data. The situation may evolve into a broader cybersecurity crisis if exploitation continues unabated.
- Political / Geopolitical: Potential for international tensions if state actors are involved or if critical infrastructure is targeted.
- Security / Counter-Terrorism: Increased risk of cyber-attacks on government and critical infrastructure systems.
- Cyber / Information Space: Heightened threat environment with potential for increased cyber espionage and data breaches.
- Economic / Social: Potential economic impacts from business disruptions and loss of consumer trust in affected organizations.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Urgently apply available patches; disable FortiCloud SSO where feasible; enhance monitoring for signs of exploitation.
- Medium-Term Posture (1–12 months): Develop resilience measures, including regular vulnerability assessments and incident response planning; foster partnerships for information sharing.
- Scenario Outlook:
- Best Case: Rapid patch adoption mitigates the threat, with minimal impact. Trigger: High patch compliance rates.
- Worst Case: Widespread exploitation leads to significant data breaches and operational disruptions. Trigger: Continued reports of successful attacks.
- Most-Likely: Gradual reduction in exploitation as patches are applied, but some systems remain vulnerable. Trigger: Mixed patch adoption rates.
6. Key Individuals and Entities
- Fortinet (Vendor)
- Shadowserver (Online safety monitor)
- Arctic Wolf (Cybersecurity firm)
- Yutaka Sejiyama (Threat researcher at Macnica)
- CISA (Cybersecurity and Infrastructure Security Agency)
7. Thematic Tags
cybersecurity, vulnerability management, cyber-espionage, critical infrastructure protection, information security, threat intelligence, patch management
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us