Critical RCE Vulnerability Discovered in React’s Flight Protocol Exposes Nearly One Million Servers
Published on: 2025-12-14
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Lessons from React2Shell
1. BLUF (Bottom Line Up Front)
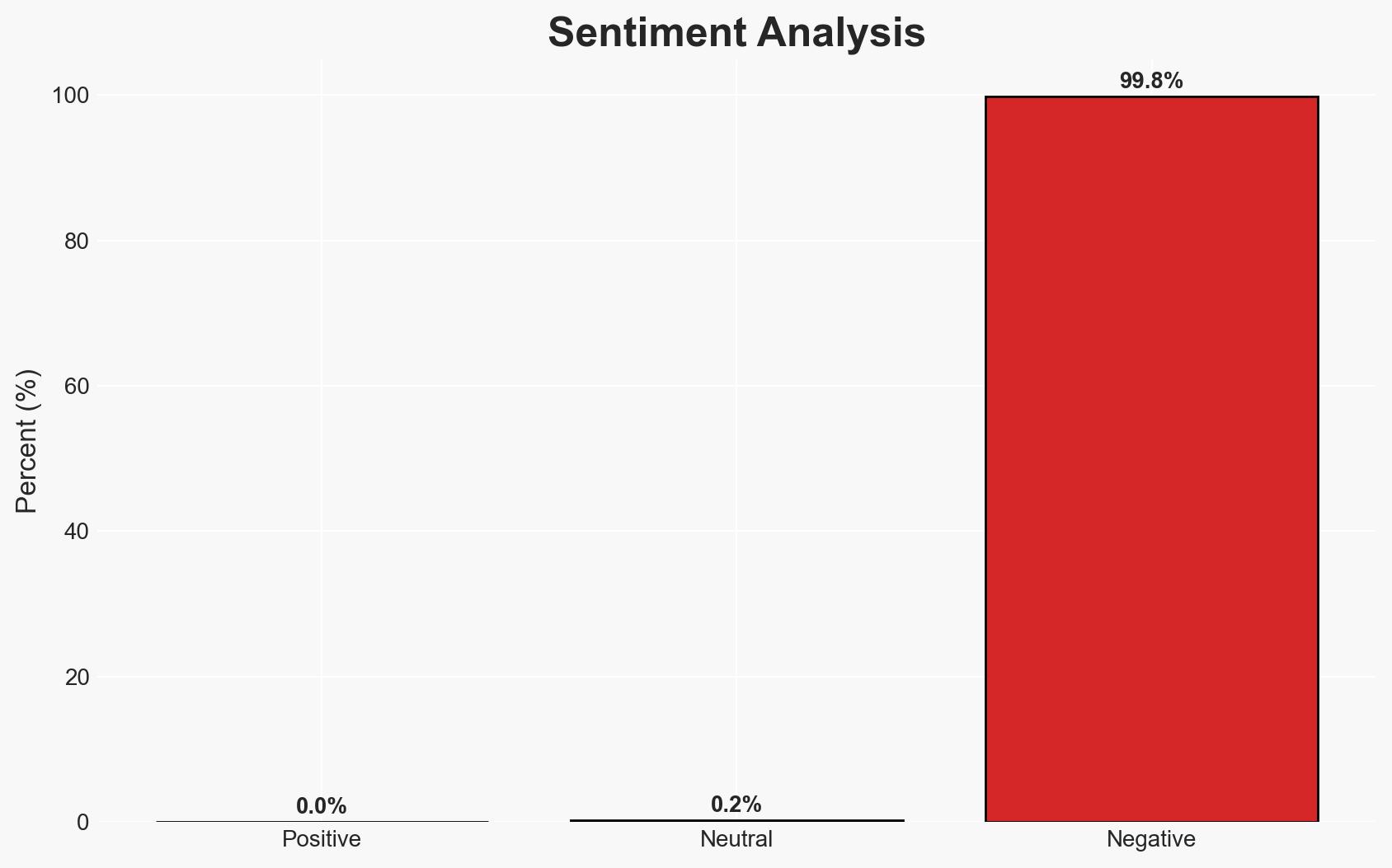
The disclosure of CVE-2025-55182 represents a critical security vulnerability in React’s Flight protocol, leading to widespread exploitation and significant risk to nearly a million servers. The vulnerability highlights a fundamental oversight in client data trust assumptions. This development poses a severe threat to organizations using React 19 and Next.js, with moderate confidence in the assessment due to incomplete data on the full scope of exploitation.
2. Competing Hypotheses
- Hypothesis A: The vulnerability was an unintended oversight due to the complexity of integrating server-side components in React. Evidence includes the historical clean security record of React and the novelty of the Flight protocol. However, the rapid exploitation suggests potential pre-existing knowledge of the vulnerability by threat actors.
- Hypothesis B: The vulnerability may have been deliberately introduced or discovered by insiders or advanced persistent threat (APT) groups. The immediate exploitation could indicate prior knowledge or testing by sophisticated actors. Contradictory evidence includes the lack of direct insider threat indicators and the absence of claims of responsibility.
- Assessment: Hypothesis A is currently better supported due to the historical security posture of React and the complexity of new architectural changes. Key indicators that could shift this judgment include evidence of insider involvement or advanced threat actor attribution.
3. Key Assumptions and Red Flags
- Assumptions: React’s security practices were previously robust; the vulnerability was not identified during standard testing; threat actors had no prior access to internal development processes.
- Information Gaps: Detailed timeline of vulnerability discovery and patching; comprehensive data on affected entities and exploitation scale.
- Bias & Deception Risks: Potential confirmation bias in assuming benign development oversight; risk of underestimating threat actor capabilities or motivations.
4. Implications and Strategic Risks
This vulnerability could lead to increased scrutiny of server-side JavaScript frameworks and potential shifts in development practices. The incident may also influence cybersecurity policies and collaboration between tech companies and security agencies.
- Political / Geopolitical: Potential for increased regulatory focus on software security standards and international cooperation on cyber threats.
- Security / Counter-Terrorism: Heightened alert for cyber threats exploiting similar vulnerabilities; potential use by state-sponsored actors.
- Cyber / Information Space: Increased risk of data breaches and unauthorized access; potential for misinformation campaigns leveraging the exploit.
- Economic / Social: Financial impacts on affected organizations; potential loss of trust in digital services and frameworks.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Encourage immediate patching of affected systems; enhance monitoring for signs of exploitation; share threat intelligence with relevant stakeholders.
- Medium-Term Posture (1–12 months): Develop resilience measures by reviewing and updating security protocols; foster partnerships for threat intelligence sharing; invest in security training for developers.
- Scenario Outlook:
- Best Case: Rapid patch adoption and no further significant breaches.
- Worst Case: Widespread exploitation leading to major data breaches and financial losses.
- Most Likely: Gradual containment with isolated incidents of exploitation as patches are implemented.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, software vulnerabilities, remote code execution, React framework, server-side JavaScript, threat intelligence, data breaches
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us