CrowdStrike ties Oracle EBS RCE CVE-2025-61882 to Cl0p attacks began Aug 9 2025 – Securityaffairs.com
Published on: 2025-10-07
Intelligence Report: CrowdStrike ties Oracle EBS RCE CVE-2025-61882 to Cl0p attacks began Aug 9 2025 – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
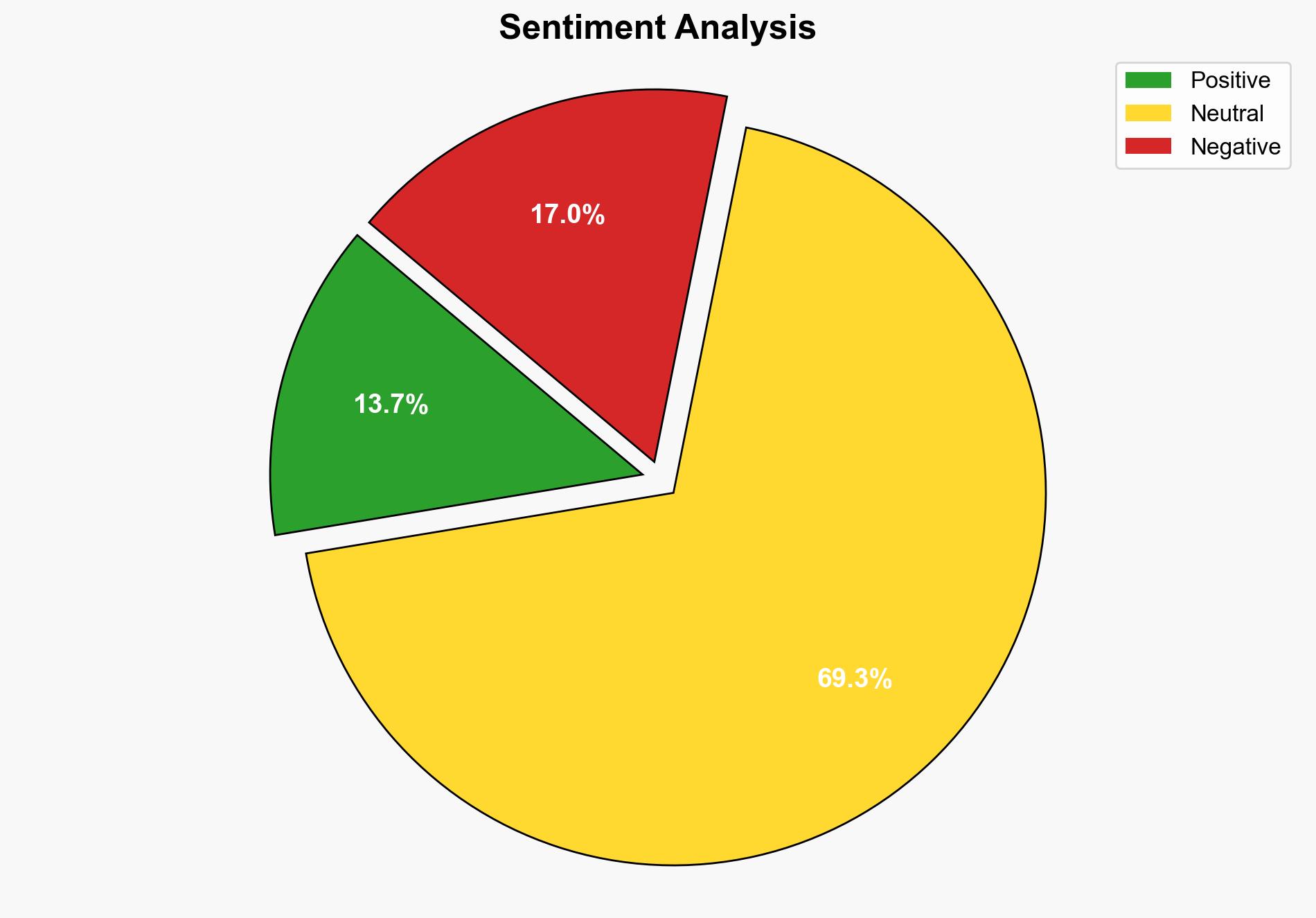
The most supported hypothesis is that the Cl0p ransomware group, known as Graceful Spider, is exploiting the Oracle EBS RCE CVE-2025-61882 vulnerability as part of a coordinated campaign. This assessment is made with moderate confidence due to the observed patterns of exploitation and the timing of the attacks. Immediate action is recommended for organizations using Oracle EBS to apply the latest security patches to mitigate the risk of exploitation.
2. Competing Hypotheses
Hypothesis 1: The Cl0p ransomware group is primarily responsible for exploiting the Oracle EBS RCE CVE-2025-61882 vulnerability, leveraging it for data theft and ransomware attacks starting in August 2025. This is supported by the alignment of attack patterns and the group’s known capabilities.
Hypothesis 2: Multiple threat actors, including but not limited to Cl0p, are exploiting the Oracle EBS RCE CVE-2025-61882 vulnerability independently. This hypothesis considers the possibility of other groups leveraging the disclosed vulnerability following the release of proof-of-concept (PoC) exploits.
3. Key Assumptions and Red Flags
– Assumption: The Cl0p group has the capability and intent to exploit Oracle EBS vulnerabilities.
– Red Flag: The moderate confidence level suggests potential gaps in attribution, such as the involvement of other threat actors.
– Missing Data: Lack of direct evidence linking specific attacks to Cl0p, relying instead on circumstantial patterns and historical behavior.
4. Implications and Strategic Risks
The exploitation of Oracle EBS RCE CVE-2025-61882 poses significant risks to organizations relying on Oracle Business Suite, potentially leading to data breaches, financial losses, and operational disruptions. The involvement of a sophisticated group like Cl0p could signal an escalation in ransomware tactics, targeting critical enterprise software. This could have broader economic impacts and increase the pressure on cybersecurity defenses globally.
5. Recommendations and Outlook
- Organizations using Oracle EBS should immediately apply the latest security patches and follow Oracle’s security advisory guidance.
- Conduct a thorough review of network security protocols and enhance monitoring for any signs of exploitation.
- Scenario Projections:
- Best Case: Rapid patch deployment mitigates the majority of exploitation attempts, reducing the impact significantly.
- Worst Case: Delays in patching lead to widespread exploitation, resulting in significant data breaches and financial losses.
- Most Likely: A mixed outcome where some organizations successfully mitigate risks while others face targeted attacks.
6. Key Individuals and Entities
– Cl0p Ransomware Group (Graceful Spider)
– Oracle Corporation
– CrowdStrike
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus