Crypto mining campaign targets Docker environments with new evasion technique – Securityaffairs.com
Published on: 2025-04-23
Intelligence Report: Crypto Mining Campaign Targets Docker Environments with New Evasion Technique – Securityaffairs.com
1. BLUF (Bottom Line Up Front)
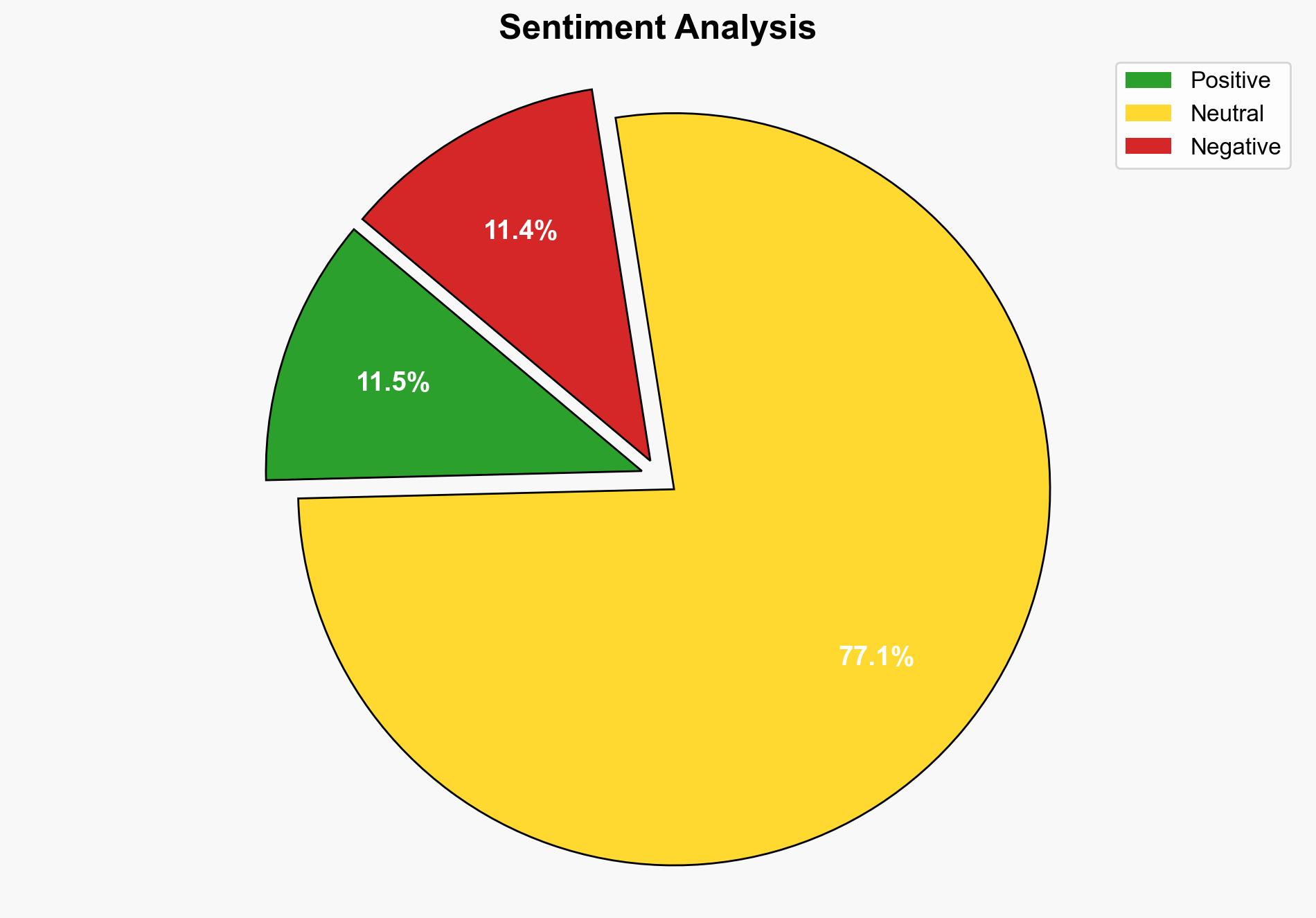
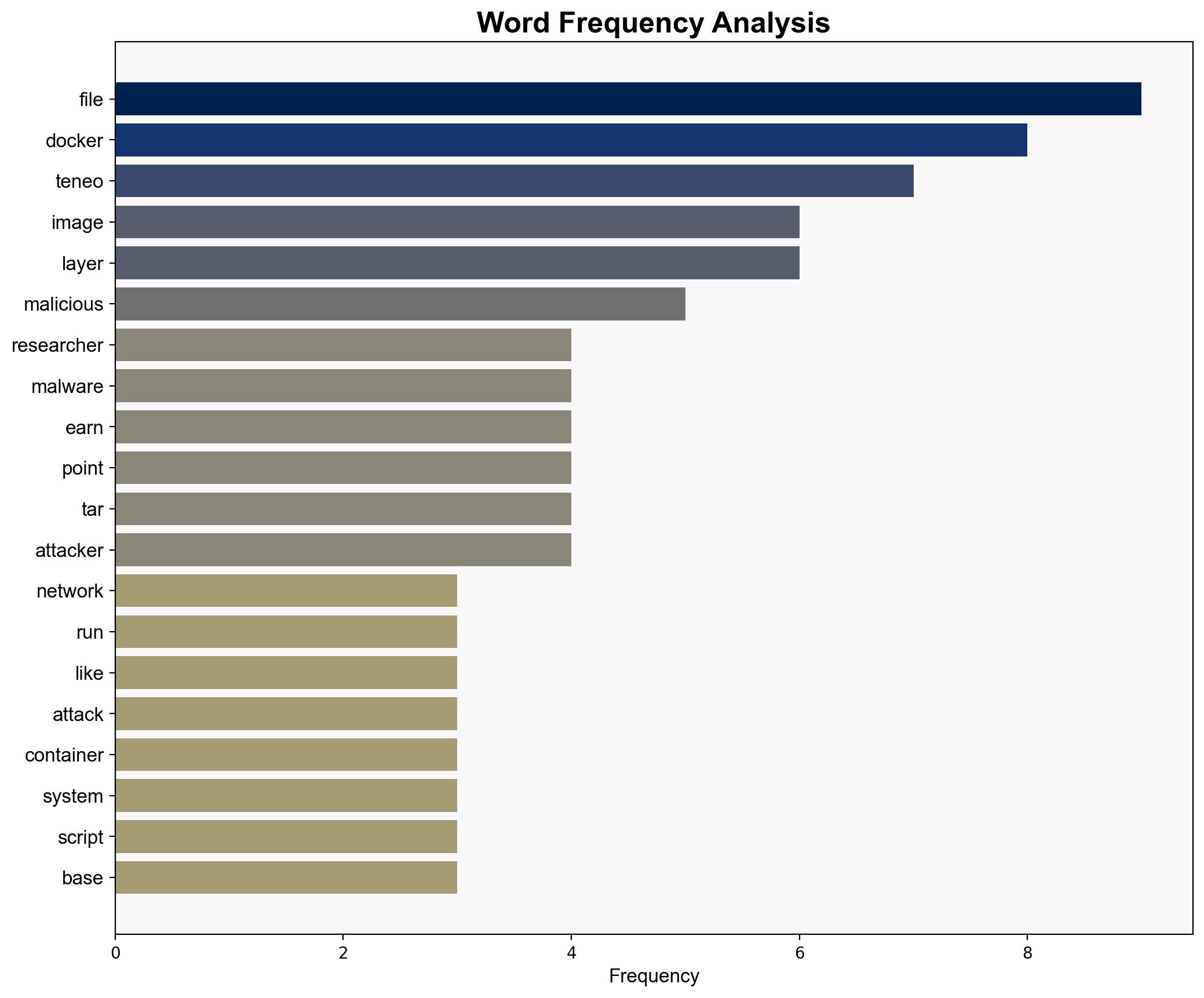
A recent malware campaign has been identified targeting Docker environments using a novel evasion technique. The campaign deploys malicious nodes to connect to the Teneo decentralized infrastructure, allowing attackers to covertly monetize social media bandwidth. This method complicates detection and analysis, posing a significant threat to containerized environments. Immediate attention and mitigation strategies are recommended to counteract this evolving threat.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Analysis of Competing Hypotheses (ACH)
Various hypotheses were considered, including traditional cryptojacking and decentralized compute network abuse. Evidence strongly supports the latter due to the use of Teneo tokens and the complexity of the obfuscation techniques employed.
SWOT Analysis
Strengths include the attackers’ advanced evasion techniques and decentralized network utilization. Weaknesses involve potential detection through behavioral analysis. Opportunities exist for improved monitoring of Docker environments. Threats include the rapid adaptation of these techniques by other malicious actors.
Indicators Development
Key indicators include unusual network traffic patterns, unexpected Docker container launches, and connections to known Teneo nodes. Monitoring these indicators can help identify potential threats early.
3. Implications and Strategic Risks
The campaign highlights a growing trend towards using decentralized networks for malicious purposes, complicating traditional detection methods. This poses systemic vulnerabilities in containerized environments, potentially affecting industries reliant on Docker for operations. The cross-domain risk includes economic impacts from resource hijacking and reputational damage from data breaches.
4. Recommendations and Outlook
- Enhance monitoring of Docker environments for unusual activity and network connections to Teneo nodes.
- Implement stricter access controls and regular audits of container images.
- Best case scenario: Rapid detection and mitigation efforts reduce the campaign’s impact.
- Worst case scenario: Widespread adoption of these techniques leads to significant operational disruptions.
- Most likely scenario: Continued evolution of evasion techniques necessitates ongoing adaptation of security measures.
5. Key Individuals and Entities
Researchers from Darktrace and Cado Security have been instrumental in analyzing and reporting on this campaign. Their findings provide critical insights into the methods and implications of the attack.
6. Thematic Tags
(‘cybersecurity’, ‘container security’, ‘cryptojacking’, ‘decentralized networks’)