Cryptocurrency Inflows to Human Trafficking Operations Rise by 85% Yearly, Linked to Southeast Asian Scams
Published on: 2026-02-16
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Crypto Payments to Human Traffickers Surges 85
1. BLUF (Bottom Line Up Front)
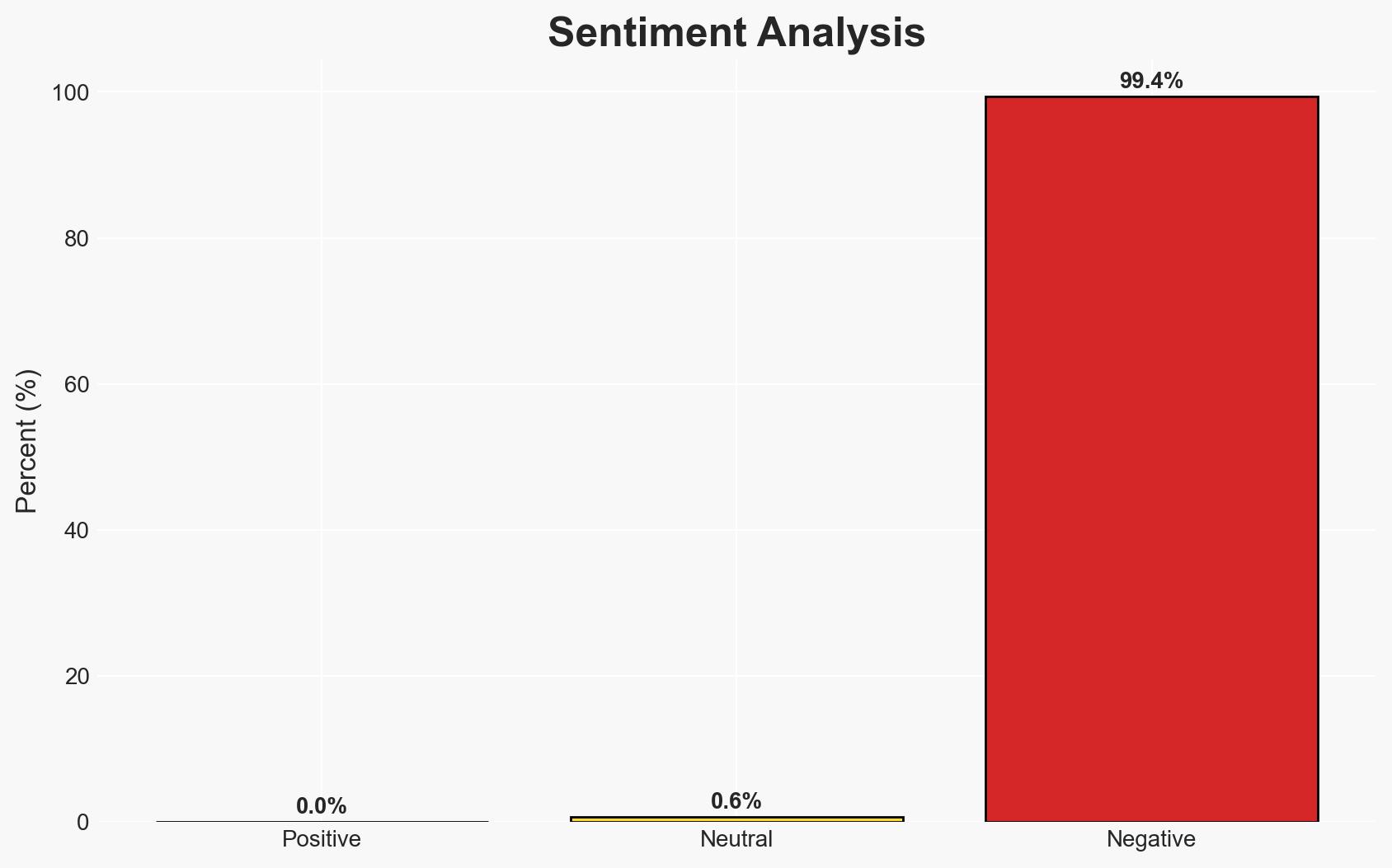
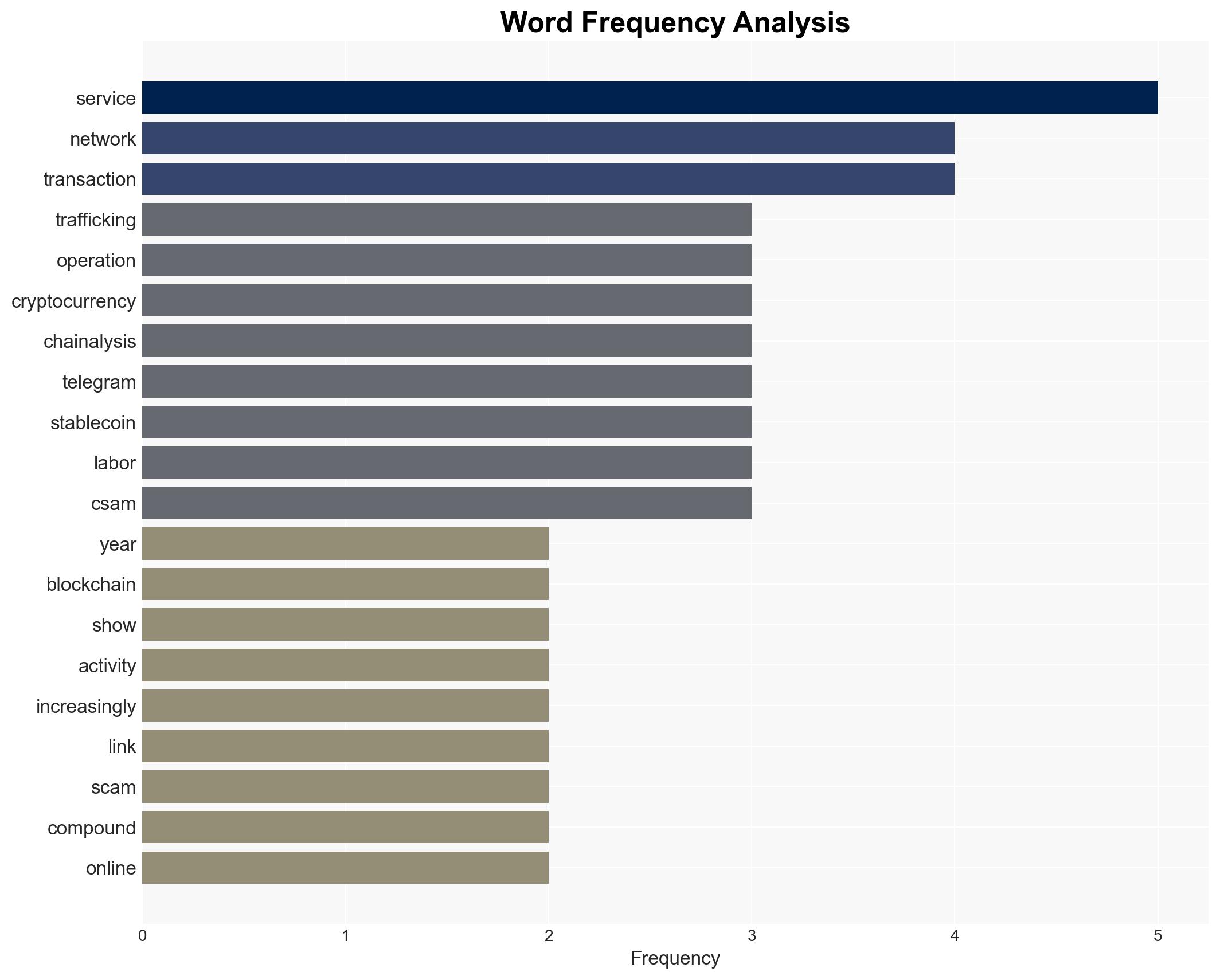
The surge in cryptocurrency payments to human traffickers, particularly in Southeast Asia, is linked to organized crime networks using digital currencies for illicit activities. The most likely hypothesis is that these operations are expanding due to the anonymity and efficiency provided by cryptocurrencies. This trend poses a significant threat to regional security and law enforcement capabilities. Overall confidence in this assessment is moderate, given the reliance on data from a single source and potential information gaps.
2. Competing Hypotheses
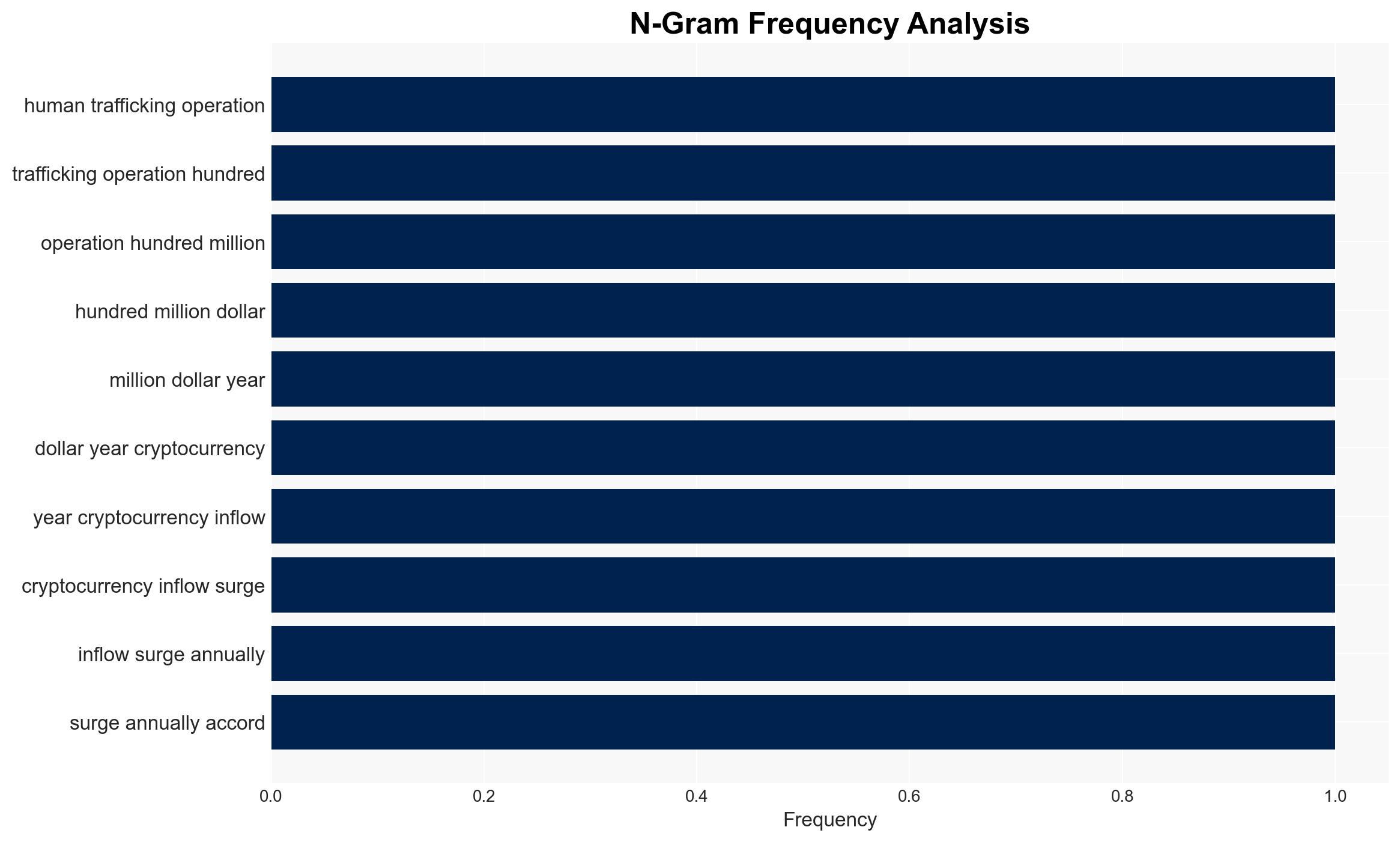
- Hypothesis A: The increase in cryptocurrency payments is primarily driven by organized crime networks exploiting digital currencies for anonymity and efficiency. Supporting evidence includes the high volume of large transactions and the integration with money laundering networks. Key uncertainties involve the full extent of these networks and their operational reach.
- Hypothesis B: The surge in crypto payments is a temporary spike due to increased law enforcement pressure on traditional money laundering methods, forcing traffickers to adapt. This is less supported due to the lack of evidence showing a decrease in traditional methods or significant law enforcement disruptions.
- Assessment: Hypothesis A is currently better supported due to the structured and large-scale nature of the transactions and their integration with established criminal networks. Indicators such as increased law enforcement success in disrupting traditional methods could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Cryptocurrency provides sufficient anonymity to evade law enforcement; organized crime networks are capable of adapting quickly to new technologies; the data from Chainalysis is accurate and comprehensive.
- Information Gaps: Detailed understanding of the organizational structure of these networks; the role of state actors, if any, in facilitating these operations; the effectiveness of current law enforcement measures against crypto-fueled trafficking.
- Bias & Deception Risks: Potential bias in Chainalysis data due to commercial interests; manipulation of transaction data by traffickers to mislead investigators; over-reliance on cryptocurrency as the sole enabler of trafficking operations.
4. Implications and Strategic Risks
The continued growth of cryptocurrency-fueled trafficking could exacerbate regional instability and challenge international law enforcement cooperation. The adaptability of these networks to digital currencies may lead to increased sophistication in criminal operations.
- Political / Geopolitical: Potential strain on international relations as countries grapple with cross-border trafficking operations.
- Security / Counter-Terrorism: Enhanced operational capabilities of criminal networks could lead to increased trafficking and associated crimes.
- Cyber / Information Space: Growing use of encrypted communication platforms like Telegram could complicate digital surveillance efforts.
- Economic / Social: Potential destabilization of local economies due to increased criminal activity and exploitation of vulnerable populations.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of cryptocurrency transactions linked to known trafficking indicators; strengthen international cooperation for intelligence sharing.
- Medium-Term Posture (1–12 months): Develop partnerships with blockchain analytics firms; invest in training for law enforcement on digital currencies and encrypted communication platforms.
- Scenario Outlook:
- Best: Successful disruption of major trafficking networks through enhanced international cooperation.
- Worst: Unchecked growth of trafficking operations leading to regional destabilization.
- Most-Likely: Continued adaptation by traffickers to law enforcement measures, maintaining current levels of operation.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
national security threats, human trafficking, cryptocurrency, organized crime, Southeast Asia, money laundering, cybercrime, law enforcement
Structured Analytic Techniques Applied
- Cognitive Bias Stress Test: Expose and correct potential biases in assessments through red-teaming and structured challenge.
- Bayesian Scenario Modeling: Use probabilistic forecasting for conflict trajectories or escalation likelihood.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
National Security Threats Briefs ·
Daily Summary ·
Support us