CVE-2025-53770 Frequently Asked Questions About Zero-Day SharePoint Vulnerability Exploitation – Tenable.com
Published on: 2025-07-20
Intelligence Report: CVE-2025-53770 Frequently Asked Questions About Zero-Day SharePoint Vulnerability Exploitation – Tenable.com
1. BLUF (Bottom Line Up Front)
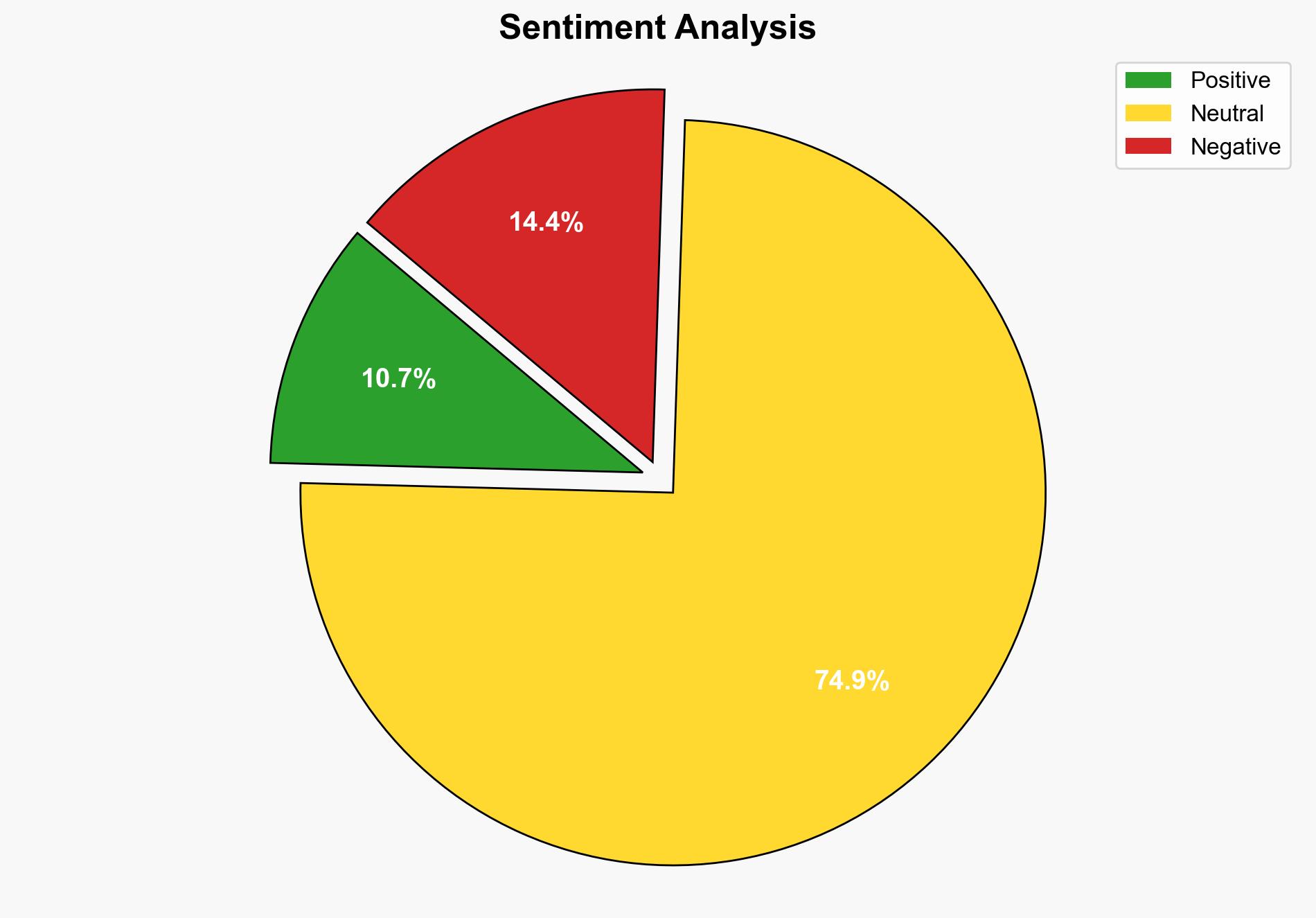
The CVE-2025-53770 zero-day vulnerability in Microsoft SharePoint servers poses a significant risk due to its potential for unauthenticated remote code execution. Successful exploitation could lead to unauthorized access and control over vulnerable systems. Immediate patching and enhanced monitoring are recommended to mitigate this threat.
2. Detailed Analysis
The following structured analytic techniques have been applied to ensure methodological consistency:
Adversarial Threat Simulation
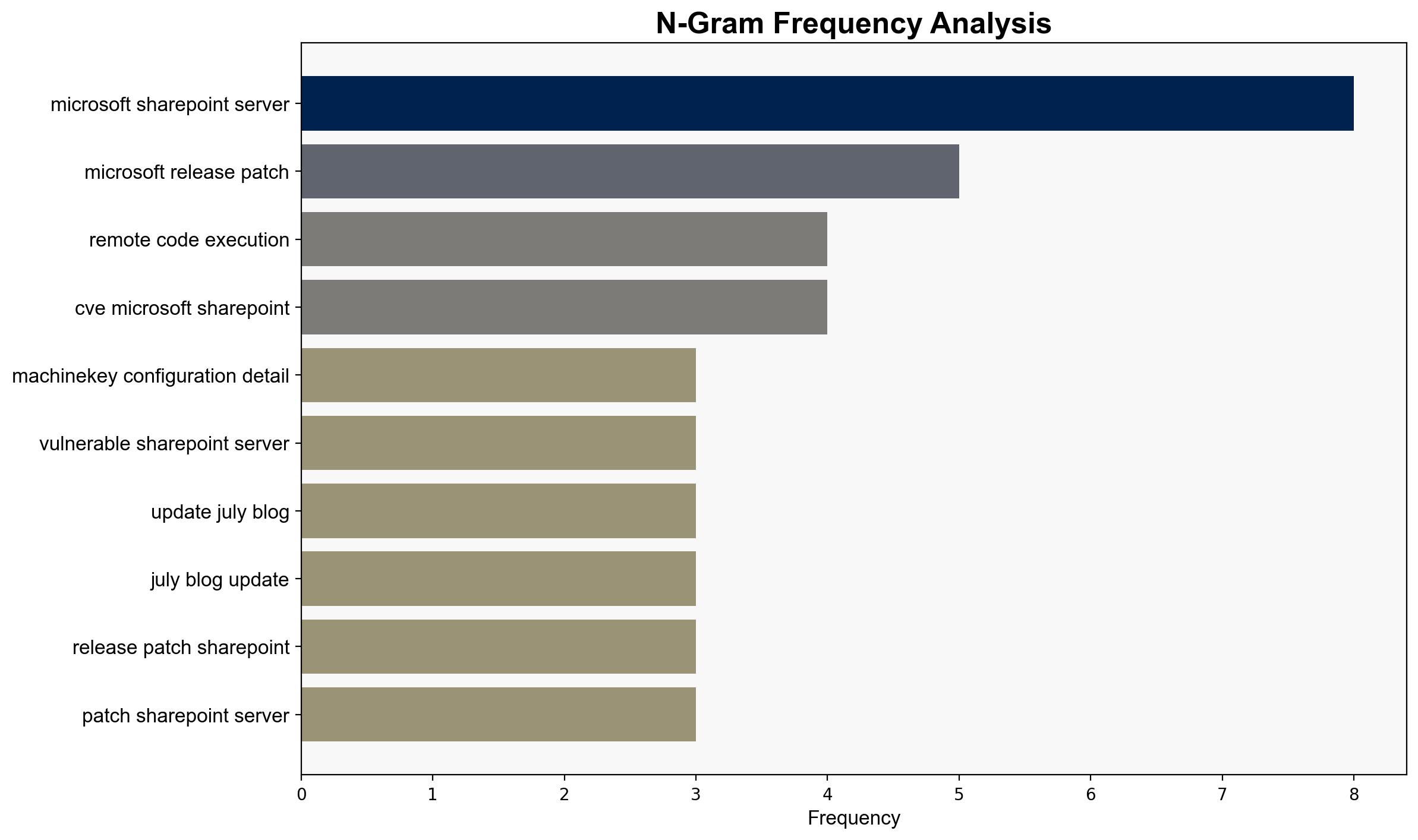
Simulated adversarial actions indicate that attackers can exploit the vulnerability to gain access to sensitive configuration details, specifically the machineKey, enabling further malicious activities.
Indicators Development
Indicators such as unusual access patterns and unauthorized requests to SharePoint servers should be monitored to detect potential exploitation attempts early.
Bayesian Scenario Modeling
Probabilistic models suggest a high likelihood of exploitation in environments with unpatched systems, emphasizing the urgency for immediate security updates.
3. Implications and Strategic Risks
The widespread nature of SharePoint usage amplifies the risk of large-scale data breaches and operational disruptions. This vulnerability could be leveraged by threat actors to conduct espionage, data theft, or sabotage, affecting both public and private sector entities globally.
4. Recommendations and Outlook
- Immediate deployment of the latest security patches from Microsoft to mitigate the vulnerability.
- Enhance network monitoring to identify and respond to suspicious activities promptly.
- Conduct regular security audits and vulnerability assessments to ensure system integrity.
- Scenario Projections:
- Best Case: Rapid patch deployment minimizes exploitation incidents.
- Worst Case: Delayed patching leads to widespread exploitation and data breaches.
- Most Likely: Moderate exploitation occurs, with targeted attacks on high-value systems.
5. Key Individuals and Entities
Dinh Ho Anh Khoa, Viettel Cyber Security; Code White GmbH researchers
6. Thematic Tags
national security threats, cybersecurity, zero-day vulnerabilities, SharePoint, remote code execution