CVE-2025-64446 Fortinet FortiWeb Zero-Day Path Traversal Vulnerability Exploited in the Wild – Tenable.com
Published on: 2025-11-14
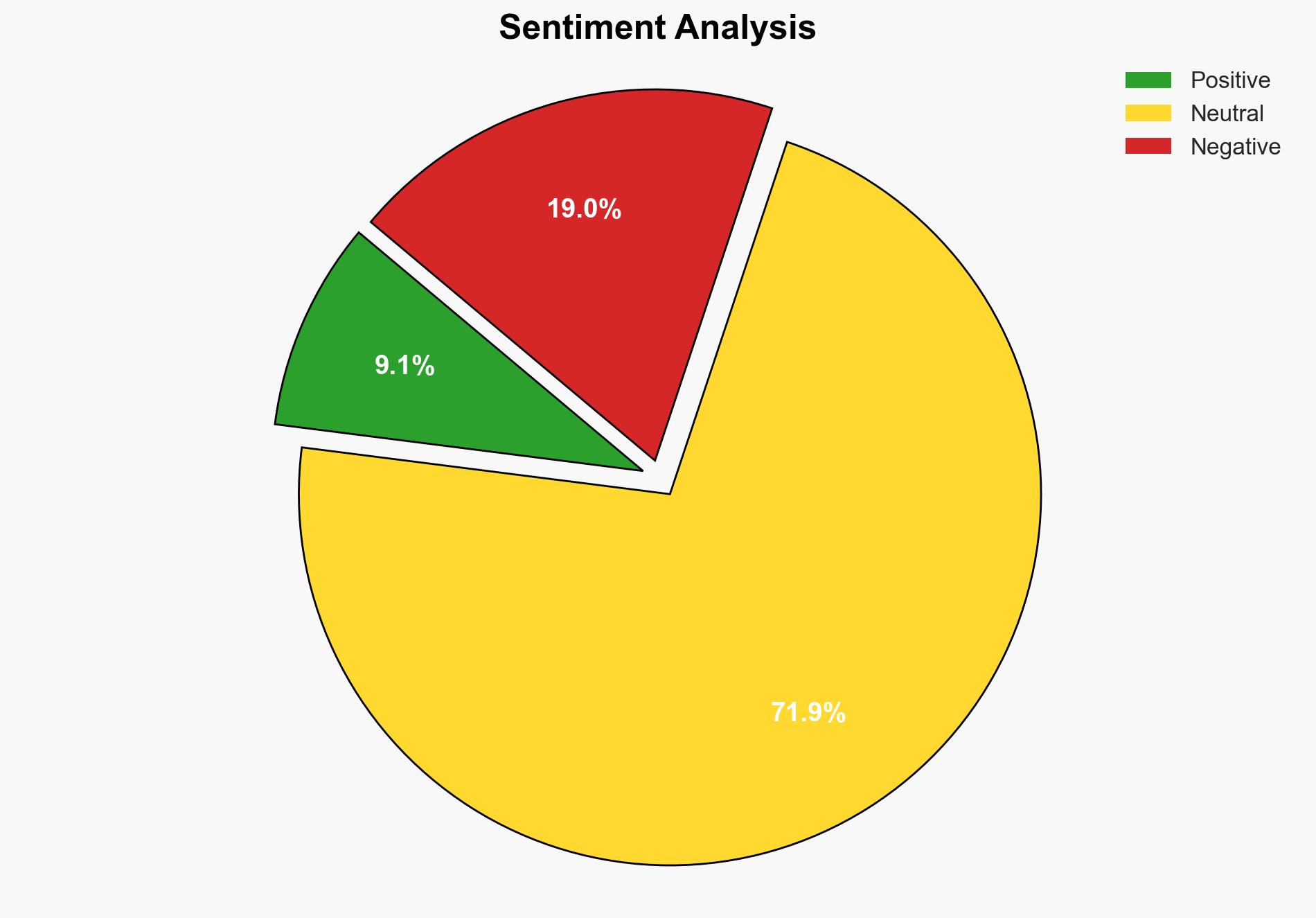
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: CVE-2025-64446 Fortinet FortiWeb Zero-Day Path Traversal Vulnerability Exploited in the Wild – Tenable.com
1. BLUF (Bottom Line Up Front)
The most supported hypothesis is that the CVE-2025-64446 vulnerability is being actively exploited by sophisticated threat actors targeting Fortinet FortiWeb devices to gain unauthorized access and execute arbitrary commands. Given the historical targeting of Fortinet vulnerabilities and the rapid development of public exploits, the confidence level is high that this poses an immediate threat to organizations using these devices. Recommended actions include immediate patching, restricting access to management interfaces, and monitoring for signs of compromise.
2. Competing Hypotheses
Hypothesis 1: The vulnerability is being exploited by state-sponsored actors to conduct espionage or sabotage operations. This is supported by the rapid exploitation following the vulnerability’s disclosure and the historical interest of state actors in Fortinet vulnerabilities.
Hypothesis 2: The vulnerability is being exploited by cybercriminal groups for financial gain, such as deploying ransomware or stealing sensitive data. This is supported by the public release of exploit tools, which lowers the barrier for entry for financially motivated attackers.
Hypothesis 1 is more likely given the sophistication required to exploit zero-day vulnerabilities and the strategic value of Fortinet devices in critical infrastructure.
3. Key Assumptions and Red Flags
Assumptions: It is assumed that the vulnerability affects a significant number of Fortinet FortiWeb devices and that organizations have not yet fully implemented the recommended patches and mitigations.
Red Flags: The rapid development and dissemination of exploit tools suggest possible insider knowledge or leaks. The lack of immediate patching by some organizations indicates potential underestimation of the threat.
4. Implications and Strategic Risks
The exploitation of this vulnerability could lead to unauthorized access to sensitive data, disruption of services, and potential damage to critical infrastructure. Politically, it could escalate tensions if state actors are involved. Economically, organizations could face significant financial losses due to data breaches or operational disruptions. The widespread availability of exploit tools increases the risk of opportunistic attacks by less sophisticated actors.
5. Recommendations and Outlook
- Immediate patching of affected Fortinet FortiWeb devices is critical to mitigate the risk.
- Restrict access to management interfaces and monitor network traffic for signs of exploitation.
- Conduct a thorough review of security policies and incident response plans to ensure readiness.
- Best-case scenario: Organizations quickly patch and mitigate the vulnerability, minimizing impact.
- Worst-case scenario: Widespread exploitation leads to significant data breaches and operational disruptions.
- Most-likely scenario: A mix of state-sponsored and criminal exploitation occurs, with varying degrees of impact based on organizational preparedness.
6. Key Individuals and Entities
Fortinet, Tenable, WatchTowr, Defuse, Cybersecurity and Infrastructure Security Agency (CISA).
7. Thematic Tags
Cybersecurity, Zero-Day Vulnerability, Fortinet, Exploitation, Patch Management
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us
·