Cyber Attack on Kensington and Chelsea Council Compromises Personal Data of Hundreds of Thousands
Published on: 2026-01-08
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Data stolen in Kensington and Chelsea cyber attack
1. BLUF (Bottom Line Up Front)
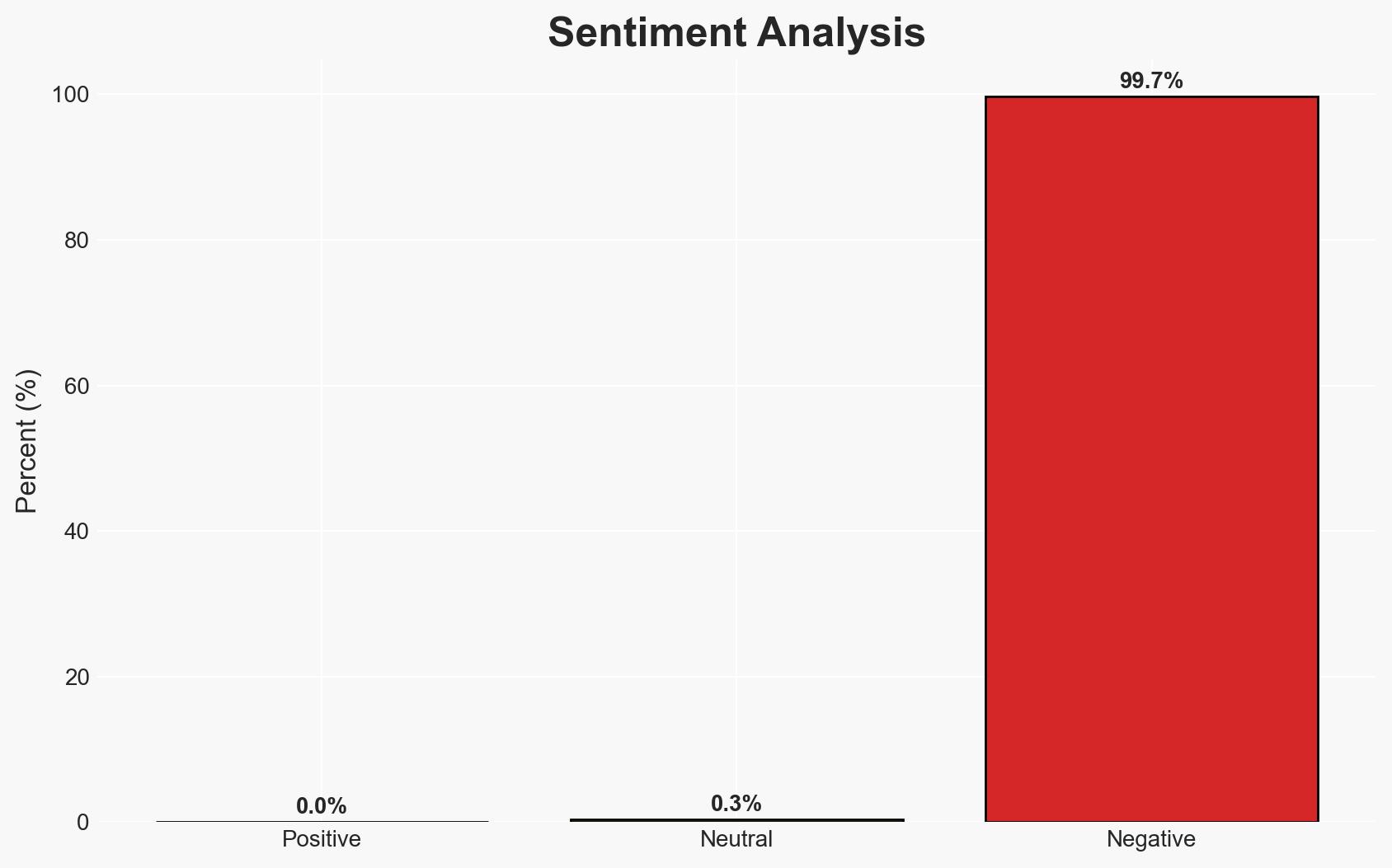
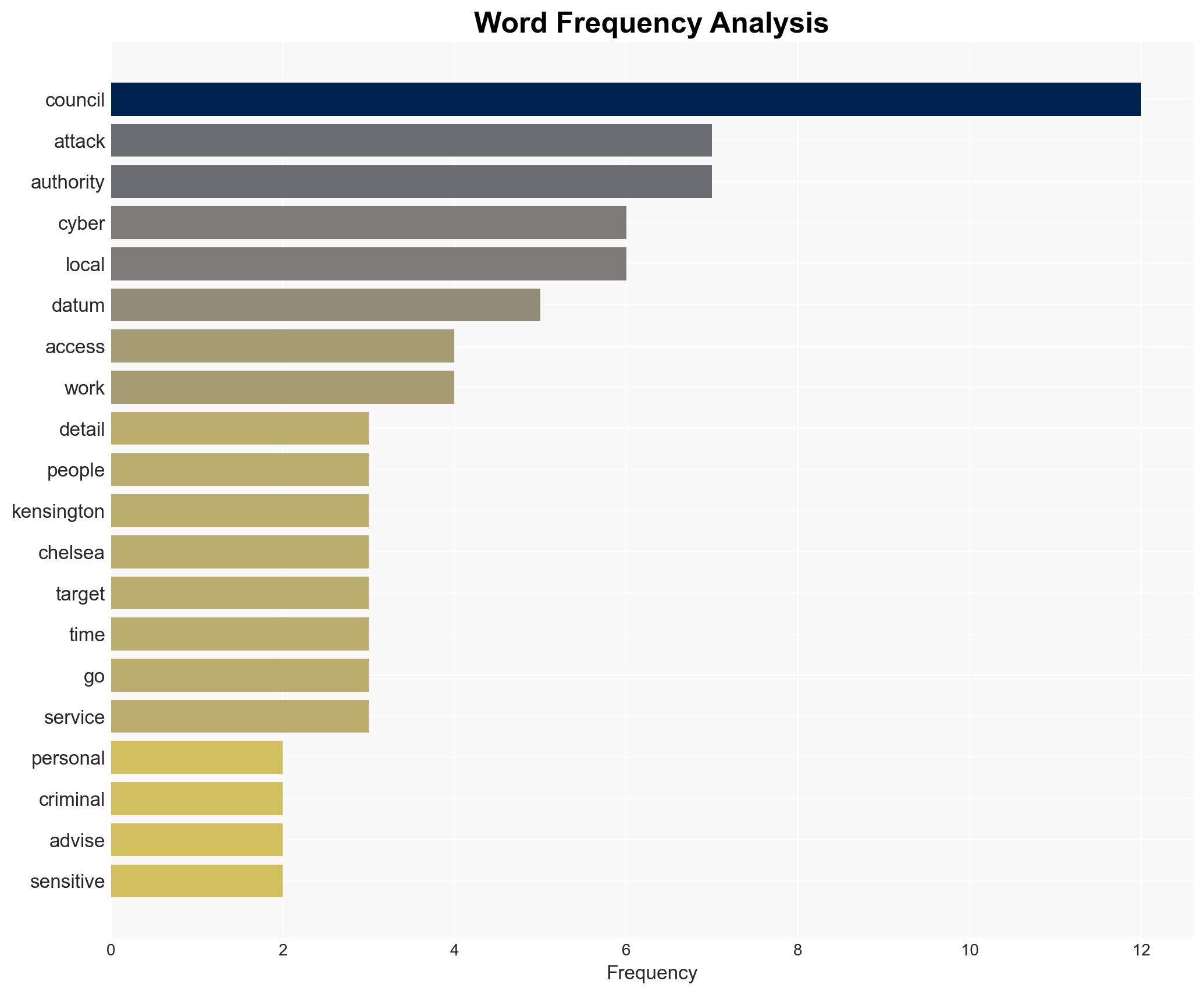
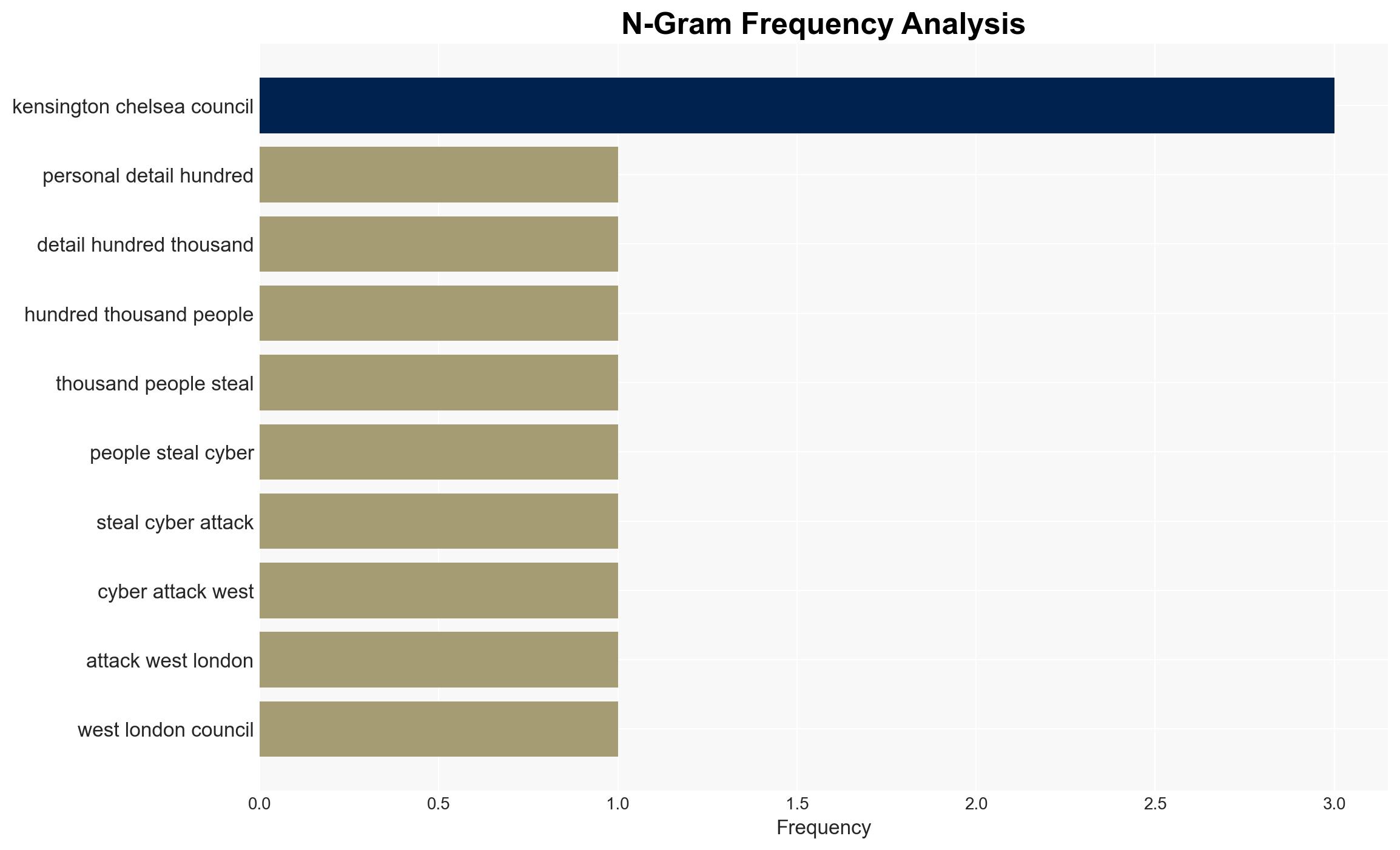
The cyber attack on Kensington and Chelsea Council has potentially compromised the personal data of hundreds of thousands of individuals, posing a significant risk of identity theft and fraud. The attack highlights vulnerabilities in local government cybersecurity infrastructure. Current evidence suggests the attack was opportunistic, targeting valuable data held by the council. Overall confidence in this assessment is moderate due to limited information on the attackers’ identity and methods.
2. Competing Hypotheses
- Hypothesis A: The attack was a financially motivated operation by cybercriminals seeking to exploit sensitive data for identity theft and fraud. This is supported by the council’s warning about potential scams and the nature of the data targeted. However, the specific identity of the attackers remains unknown, creating uncertainty.
- Hypothesis B: The attack was part of a broader campaign by a state-sponsored group aiming to disrupt local government operations or gather intelligence. While local authorities are often targeted due to their data holdings, there is currently no direct evidence linking this attack to state actors.
- Assessment: Hypothesis A is currently better supported due to the focus on personal data and the council’s emphasis on criminal intent. Indicators such as the discovery of sophisticated malware or links to known state-sponsored groups could shift this assessment.
3. Key Assumptions and Red Flags
- Assumptions: The attackers are primarily motivated by financial gain; the data accessed is sensitive and valuable; local government cybersecurity measures are insufficient to prevent such breaches.
- Information Gaps: Specific methods used by attackers; full scope of data compromised; identity and affiliations of the attackers.
- Bias & Deception Risks: Potential bias in assuming financial motives without considering geopolitical factors; reliance on council statements without independent verification may introduce bias.
4. Implications and Strategic Risks
This cyber attack could lead to increased scrutiny of local government cybersecurity practices and potentially drive policy changes. The breach may also encourage further attacks if vulnerabilities are perceived as exploitable.
- Political / Geopolitical: Potential for increased regulatory oversight and resource allocation to local government cybersecurity.
- Security / Counter-Terrorism: Heightened risk of similar attacks on other local authorities, potentially impacting public trust and service delivery.
- Cyber / Information Space: Increased awareness and potential for improved cybersecurity measures; risk of misinformation or panic if data misuse is publicized.
- Economic / Social: Potential financial losses for affected individuals; strain on council resources to manage breach fallout and improve defenses.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of affected systems; provide clear guidance to residents on protecting their information; collaborate with cybersecurity experts to identify vulnerabilities.
- Medium-Term Posture (1–12 months): Invest in cybersecurity infrastructure and training; establish partnerships with cybersecurity agencies; conduct regular security audits.
- Scenario Outlook:
- Best Case: Breach contained with minimal data misuse; improved cybersecurity measures prevent future incidents.
- Worst Case: Widespread data misuse leads to significant financial and reputational damage; further attacks exploit remaining vulnerabilities.
- Most-Likely: Some data misuse occurs, prompting moderate policy and security improvements.
6. Key Individuals and Entities
- Elizabeth Campbell, leader of Kensington and Chelsea Council
- Graeme Stewart, cybersecurity expert
- National Cyber Security Centre
- Information Commissioner’s Office
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
cybersecurity, data breach, local government, identity theft, cybercrime, public sector, information security
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us