Cyber defenders sound the alarm as F5 hack exposes broad risks – CNA
Published on: 2025-10-20
Intelligence Report: Cyber defenders sound the alarm as F5 hack exposes broad risks – CNA
1. BLUF (Bottom Line Up Front)
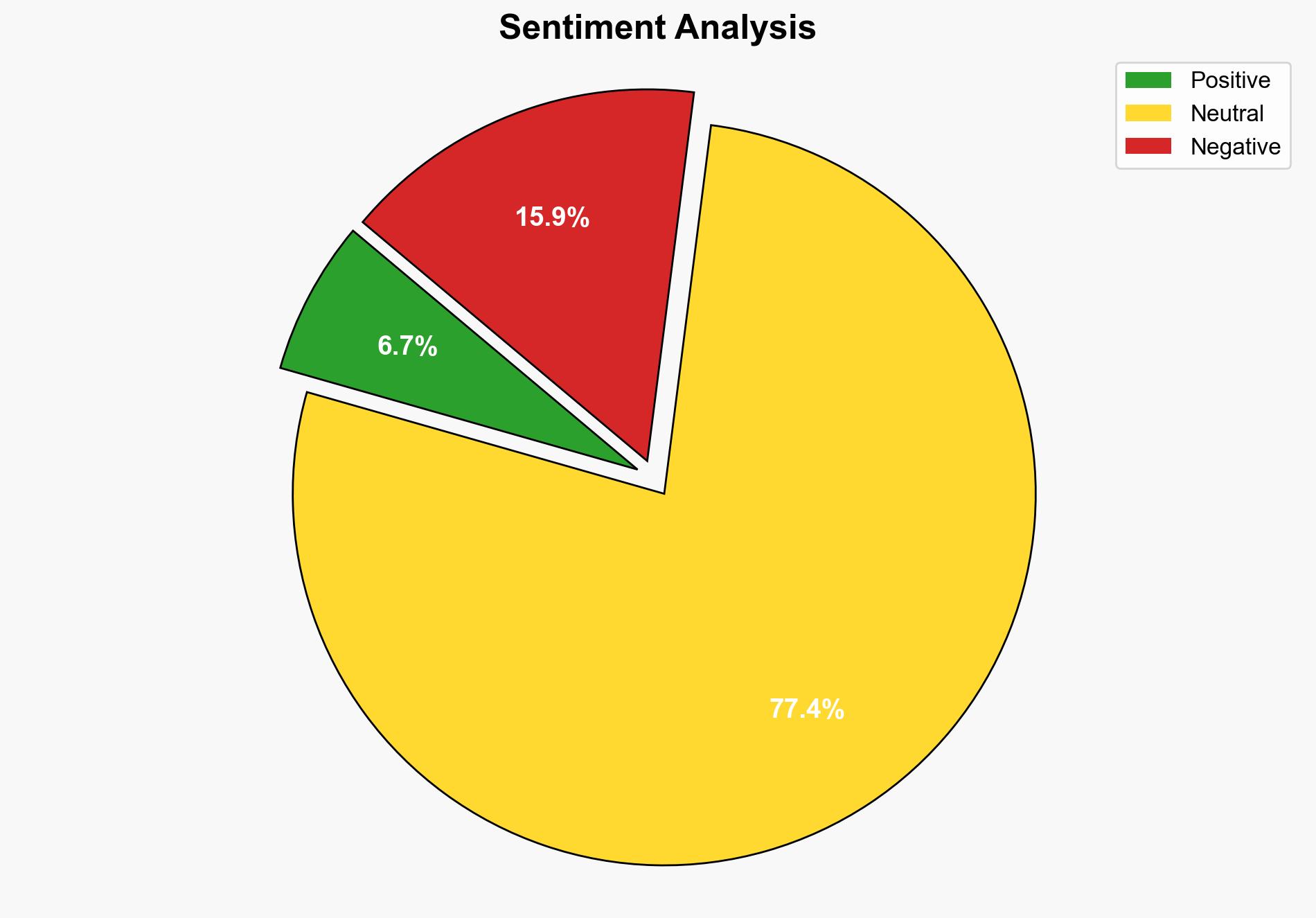
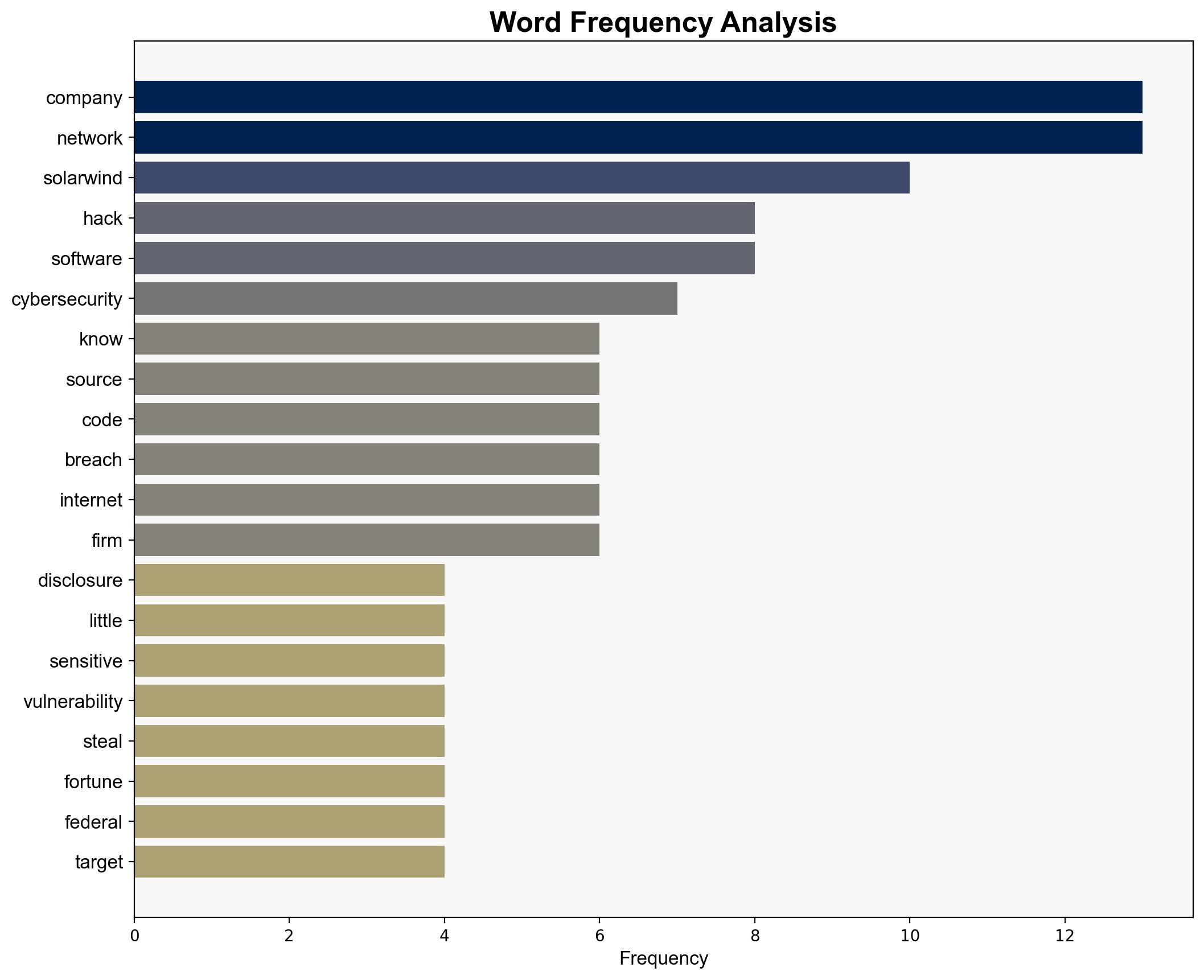
The F5 hack represents a significant cybersecurity threat with potential implications for national security and corporate integrity. The most supported hypothesis suggests a state-sponsored cyber espionage operation aimed at exploiting vulnerabilities in critical infrastructure. Confidence level: Moderate. Recommended action: Immediate strengthening of cybersecurity protocols and international collaboration to identify and mitigate further risks.
2. Competing Hypotheses
1. **Hypothesis A**: The F5 hack is a state-sponsored cyber espionage operation, potentially linked to Chinese actors, aiming to exploit vulnerabilities in critical infrastructure for intelligence gathering.
2. **Hypothesis B**: The hack is the work of independent cybercriminals seeking financial gain through the exploitation of sensitive data and vulnerabilities.
Using ACH 2.0, Hypothesis A is better supported due to the strategic targeting of federal networks and Fortune 500 companies, which aligns with state-sponsored objectives. Hypothesis B lacks strong evidence, as financial motives are not clearly indicated in the available data.
3. Key Assumptions and Red Flags
– **Assumptions**: Hypothesis A assumes state actors have the capability and intent to conduct such sophisticated operations. Hypothesis B assumes cybercriminals have similar capabilities without clear financial incentives.
– **Red Flags**: Lack of concrete attribution to specific actors; potential bias in attributing attacks to state-sponsored groups without definitive evidence.
– **Blind Spots**: Limited information on the full scope of the hack and the specific vulnerabilities exploited.
4. Implications and Strategic Risks
The hack could lead to widespread disruption in critical services if exploited further. Economic impacts include potential financial losses for affected companies and a decrease in public trust. Geopolitically, tensions may rise if state-sponsored involvement is confirmed, potentially leading to retaliatory measures. Psychologically, the attack may increase anxiety over cybersecurity vulnerabilities.
5. Recommendations and Outlook
- Enhance cybersecurity measures across critical infrastructure, focusing on patching known vulnerabilities.
- Foster international cooperation to attribute and respond to cyber threats effectively.
- Scenario Projections:
- Best Case: Rapid identification and patching of vulnerabilities with minimal disruption.
- Worst Case: Escalation of cyberattacks leading to significant economic and geopolitical instability.
- Most Likely: Continued cyber threats requiring ongoing vigilance and adaptation of cybersecurity strategies.
6. Key Individuals and Entities
– Michael Sikorski
– Bob Huber
– Glenn Thorpe
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus