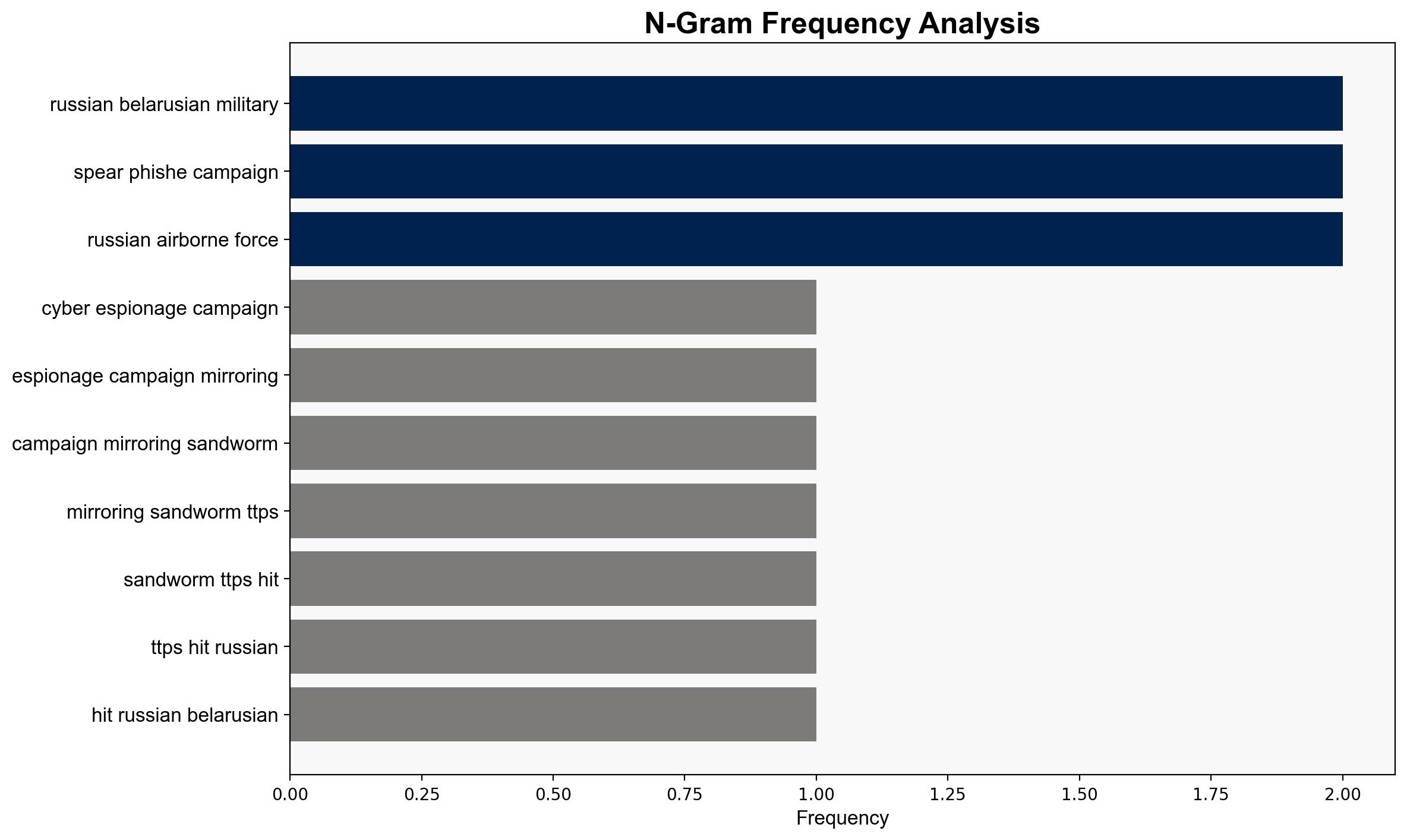
Cyber-espionage campaign mirroring Sandworm TTPs hit Russian and Belarusian military – Help Net Security
Published on: 2025-11-03
Intelligence Report: Cyber-espionage campaign mirroring Sandworm TTPs hit Russian and Belarusian military – Help Net Security
1. BLUF (Bottom Line Up Front)
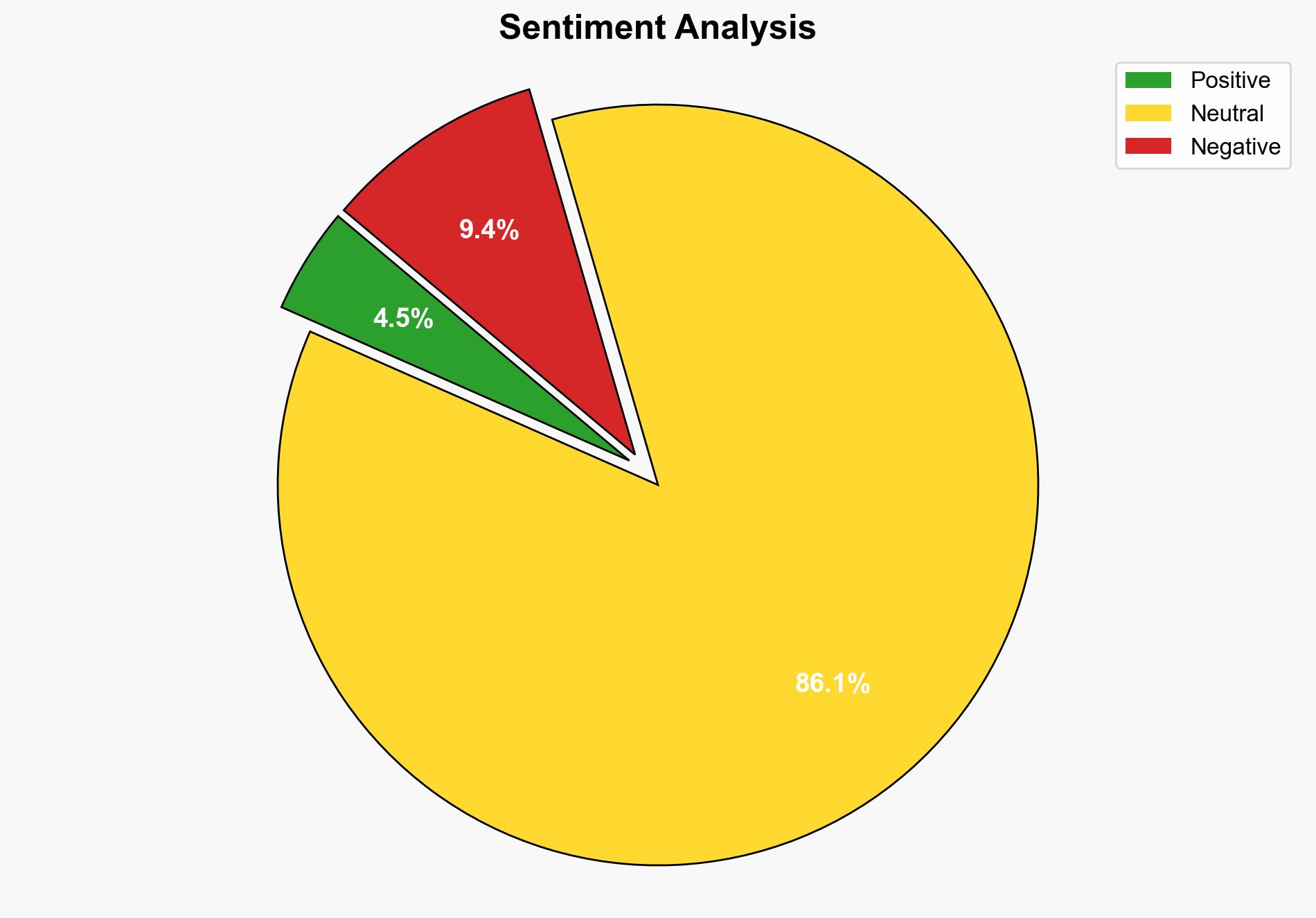
The cyber-espionage campaign targeting Russian and Belarusian military entities, while resembling Sandworm TTPs, presents two primary hypotheses: either it is a genuine Sandworm operation or a false flag by another actor. The analysis leans towards the latter due to inconsistencies in typical Sandworm operations. Confidence level: Moderate. Recommended action: Enhance monitoring of Russian and Belarusian military networks and investigate potential false flag operations.
2. Competing Hypotheses
Hypothesis 1: The campaign is conducted by the Sandworm group, leveraging their known TTPs to compromise Russian and Belarusian military targets.
Hypothesis 2: The campaign is a false flag operation by a different actor, designed to mimic Sandworm TTPs and mislead attribution efforts.
3. Key Assumptions and Red Flags
Assumptions:
– Hypothesis 1 assumes Sandworm’s interest in targeting Russian and Belarusian military entities, which is atypical given their historical focus.
– Hypothesis 2 assumes the existence of actors capable of replicating Sandworm’s sophisticated TTPs.
Red Flags:
– The use of TTPs similar to Sandworm could be a deliberate attempt to mislead attribution.
– Lack of direct evidence linking Sandworm to this specific campaign.
4. Implications and Strategic Risks
The campaign could escalate tensions between Russia, Belarus, and other international actors if misattributed. A false flag operation might aim to sow distrust within Russian and Belarusian military ranks or between these nations and their allies. The potential for misattribution could lead to retaliatory actions based on incorrect assumptions, increasing regional instability.
5. Recommendations and Outlook
- Enhance cybersecurity measures and threat intelligence sharing among Russian and Belarusian military networks.
- Conduct thorough forensic analysis to confirm the true origin of the attack.
- Best-case scenario: The campaign is accurately attributed, and appropriate defensive measures are implemented.
- Worst-case scenario: Misattribution leads to diplomatic or military escalation.
- Most likely scenario: Ongoing investigations reveal a sophisticated false flag operation, prompting increased cybersecurity collaboration.
6. Key Individuals and Entities
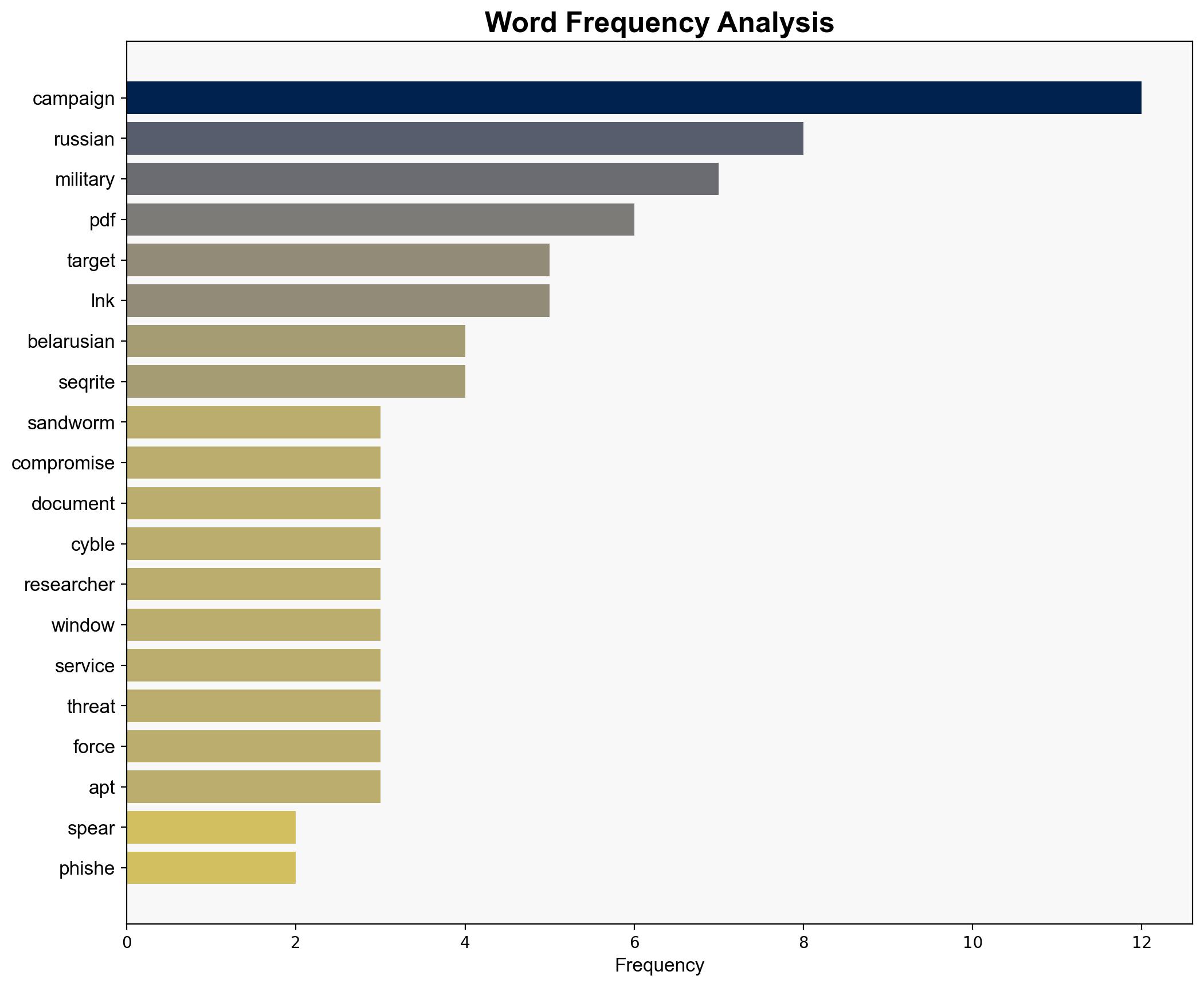
No specific individuals are named in the intelligence. Entities involved include Cyble Research Intelligence Lab (CRIL) and Seqrite Labs, which have analyzed the campaign.
7. Thematic Tags
national security threats, cybersecurity, counter-terrorism, regional focus