Cyber Threat Analysis: ShadyPanda’s Covert Browser Extension Hijacking Campaign Exposed
Published on: 2025-12-15
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: A Browser Extension Risk Guide After the ShadyPanda Campaign
1. BLUF (Bottom Line Up Front)
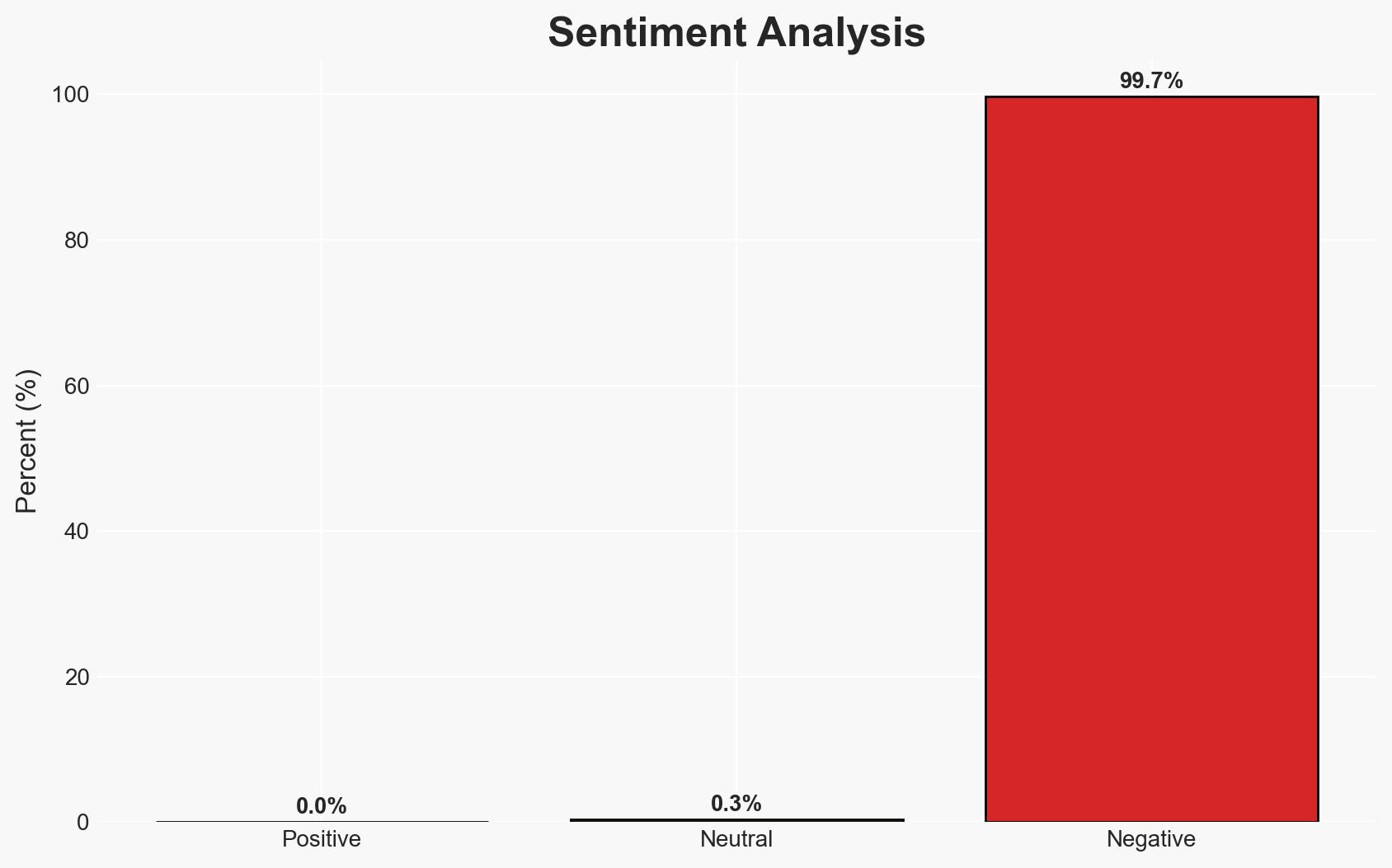
The ShadyPanda campaign represents a sophisticated cyber threat exploiting browser extensions to conduct large-scale espionage and data theft, impacting millions of users and potentially compromising enterprise SaaS environments. The most likely hypothesis is that this campaign was orchestrated by a well-resourced threat actor with long-term strategic objectives, affecting both individual users and corporate entities. Overall confidence in this assessment is moderate, given the available evidence and the complexity of the threat landscape.
2. Competing Hypotheses
- Hypothesis A: ShadyPanda is a state-sponsored group aiming to gather intelligence and disrupt adversaries by leveraging browser extensions as a covert access point. Supporting evidence includes the long-term strategic planning and sophisticated execution of the campaign. However, the lack of direct attribution to a specific nation-state actor remains a key uncertainty.
- Hypothesis B: ShadyPanda is an independent cybercriminal organization focused on financial gain through the sale of stolen data and credentials. This hypothesis is supported by the potential for monetizing stolen session tokens and credentials. Contradicting evidence includes the extensive planning and resources that suggest motives beyond immediate financial gain.
- Assessment: Hypothesis A is currently better supported due to the campaign’s complexity and strategic nature, which align with state-sponsored activities. Indicators that could shift this judgment include evidence of financial transactions linked to ShadyPanda or direct attribution to a nation-state.
3. Key Assumptions and Red Flags
- Assumptions: The threat actor has significant resources and technical expertise; browser extensions will continue to be a vector for cyber threats; affected users and organizations are unaware of the compromise.
- Information Gaps: The identity and ultimate objectives of ShadyPanda; the full extent of data exfiltration and affected entities; potential connections to other known threat groups.
- Bias & Deception Risks: Confirmation bias in attributing the campaign to state-sponsored actors; potential misinformation from threat actors to obscure true motives or origins.
4. Implications and Strategic Risks
This development could lead to increased scrutiny of browser extensions and heightened security measures across SaaS platforms. The campaign’s success may inspire similar tactics by other threat actors, potentially escalating cyber threats globally.
- Political / Geopolitical: Potential diplomatic tensions if state sponsorship is confirmed, leading to retaliatory cyber operations or sanctions.
- Security / Counter-Terrorism: Increased risk of espionage and data breaches, requiring enhanced cybersecurity protocols and threat intelligence sharing.
- Cyber / Information Space: Greater focus on securing browser environments and developing detection capabilities for malicious extensions.
- Economic / Social: Potential financial losses for affected companies and erosion of trust in digital platforms, impacting user behavior and enterprise security policies.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Conduct a comprehensive audit of browser extensions within organizational networks; implement stricter controls and monitoring for extension updates.
- Medium-Term Posture (1–12 months): Develop partnerships with browser vendors for improved vetting processes; invest in user education and awareness programs regarding extension risks.
- Scenario Outlook:
- Best Case: Enhanced security measures mitigate future risks, and no further data breaches occur.
- Worst Case: Continued exploitation leads to significant data breaches and financial losses.
- Most Likely: Incremental improvements in security posture reduce but do not eliminate the risk of similar attacks.
6. Key Individuals and Entities
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
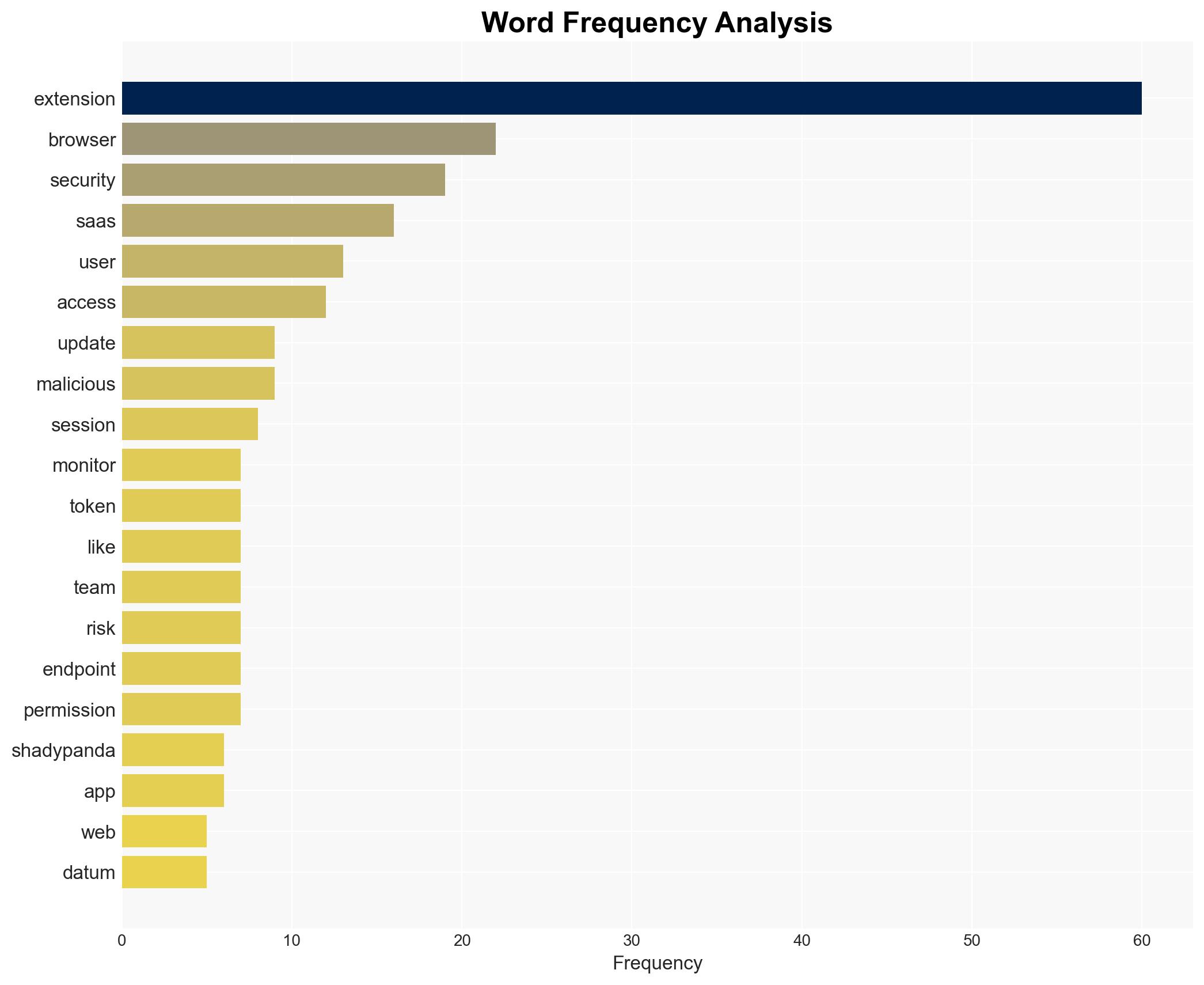
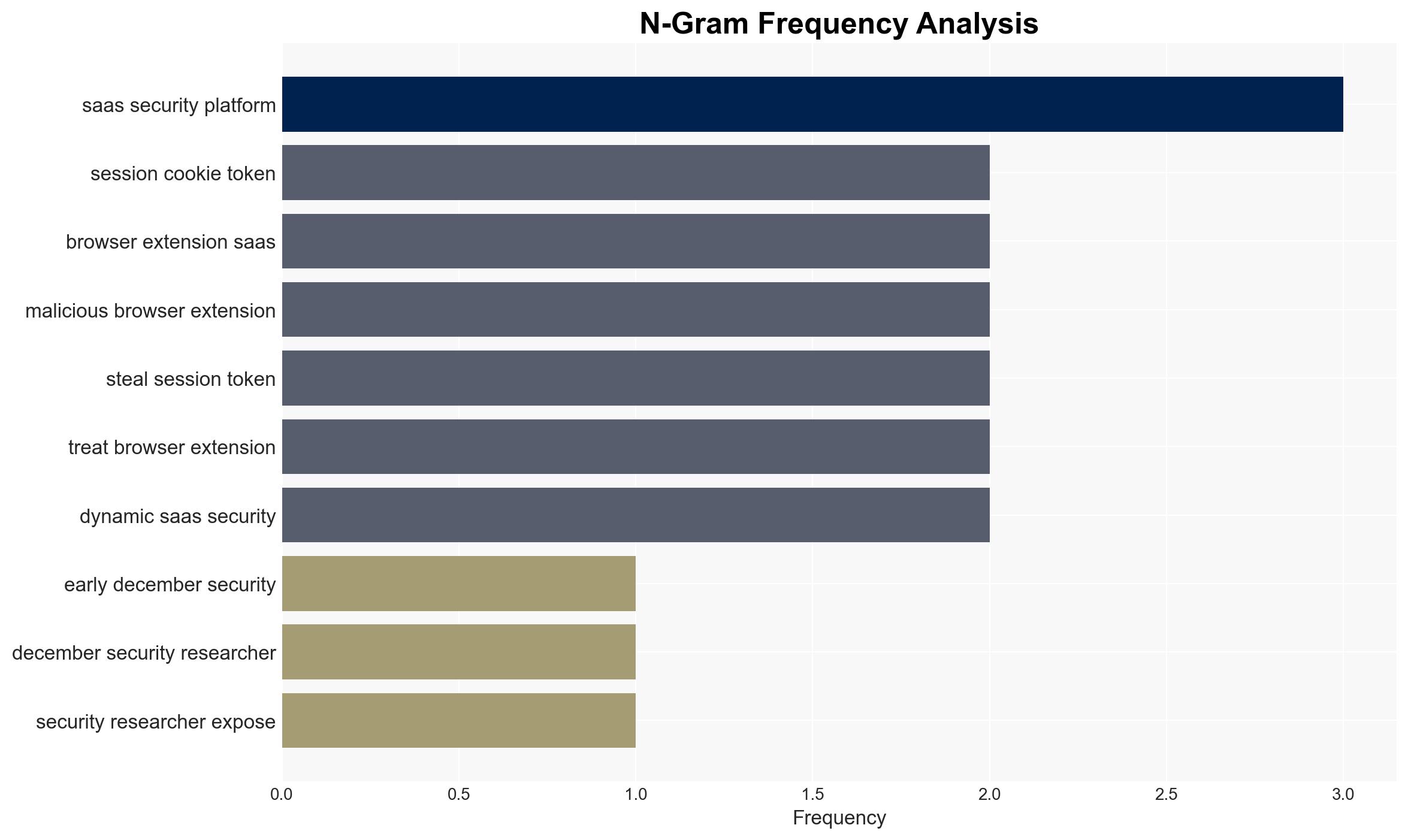
cybersecurity, browser extensions, cyber-espionage, SaaS security, supply-chain attack, threat intelligence, state-sponsored activity
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us