Cyber Threats Shift: Strategies for SMBs to Enhance Security in 2026
Published on: 2025-12-24
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Attacks are Evolving 3 Ways to Protect Your Business in 2026
1. BLUF (Bottom Line Up Front)
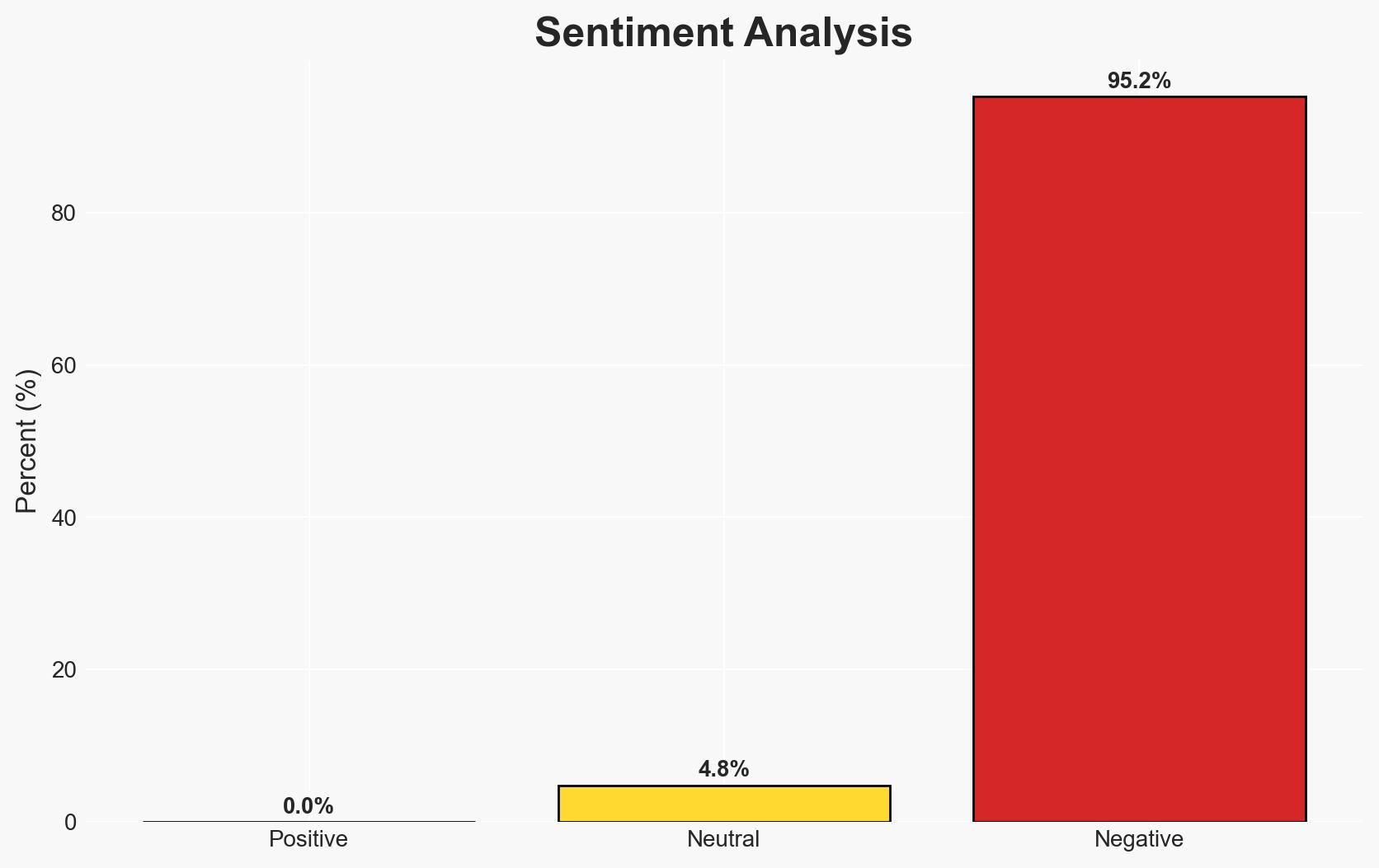
In 2025, small and medium-sized businesses (SMBs) became the primary targets for cybercriminals, accounting for 70.5% of data breaches. This shift is attributed to increased cybersecurity investments by larger companies and their refusal to pay ransoms. The trend is expected to continue into 2026, with SMBs remaining vulnerable due to limited resources. Overall confidence in this assessment is moderate.
2. Competing Hypotheses
- Hypothesis A: Cybercriminals are targeting SMBs because they have become easier targets as larger companies have improved their defenses. This is supported by the increase in SMB breaches and the lower security investments by SMBs. However, the assumption that all large companies have uniformly improved their defenses remains unverified.
- Hypothesis B: The shift to targeting SMBs is temporary and driven by opportunistic behavior rather than a strategic change. This could be contradicted by the consistent pattern of attacks on SMBs and the lack of evidence showing a decline in SMB vulnerabilities.
- Assessment: Hypothesis A is currently better supported due to the observable trend of increased SMB breaches and the logical inference that cybercriminals are adapting to the improved defenses of larger companies. Indicators such as a significant decrease in SMB breaches or a resurgence in attacks on large companies could shift this judgment.
3. Key Assumptions and Red Flags
- Assumptions: Cybercriminals are rational actors seeking the path of least resistance; SMBs have not significantly improved their cybersecurity; larger companies have effectively enhanced their defenses.
- Information Gaps: Detailed data on the cybersecurity investments of SMBs and large companies; comprehensive breach data from 2026 to confirm trends.
- Bias & Deception Risks: Potential bias in data sources focusing on SMB breaches; cybercriminals may be spreading misinformation to obscure their true targets.
4. Implications and Strategic Risks
The continued targeting of SMBs by cybercriminals could lead to increased economic instability and a shift in cybersecurity priorities. This development may also influence policy and regulatory frameworks.
- Political / Geopolitical: Potential for increased regulatory scrutiny and international cooperation on cybersecurity standards.
- Security / Counter-Terrorism: Heightened threat environment for SMBs, requiring enhanced security measures and awareness.
- Cyber / Information Space: Increased demand for cybersecurity services and potential for innovation in defensive technologies.
- Economic / Social: Financial strain on SMBs due to breaches could affect economic stability and employment.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Encourage SMBs to conduct cybersecurity audits and enhance basic security measures; monitor breach data for emerging trends.
- Medium-Term Posture (1–12 months): Develop partnerships between SMBs and cybersecurity firms; promote cybersecurity awareness and training programs.
- Scenario Outlook:
- Best Case: SMBs significantly improve cybersecurity, reducing breach incidents.
- Worst Case: Continued high breach rates lead to widespread economic impacts.
- Most Likely: SMBs remain primary targets, but increased awareness and incremental improvements mitigate some risks.
6. Key Individuals and Entities
- Tracelo
- PhoneMondo
- SkilloVilla
- Data Breach Observatory
- Satanic (hacker)
7. Thematic Tags
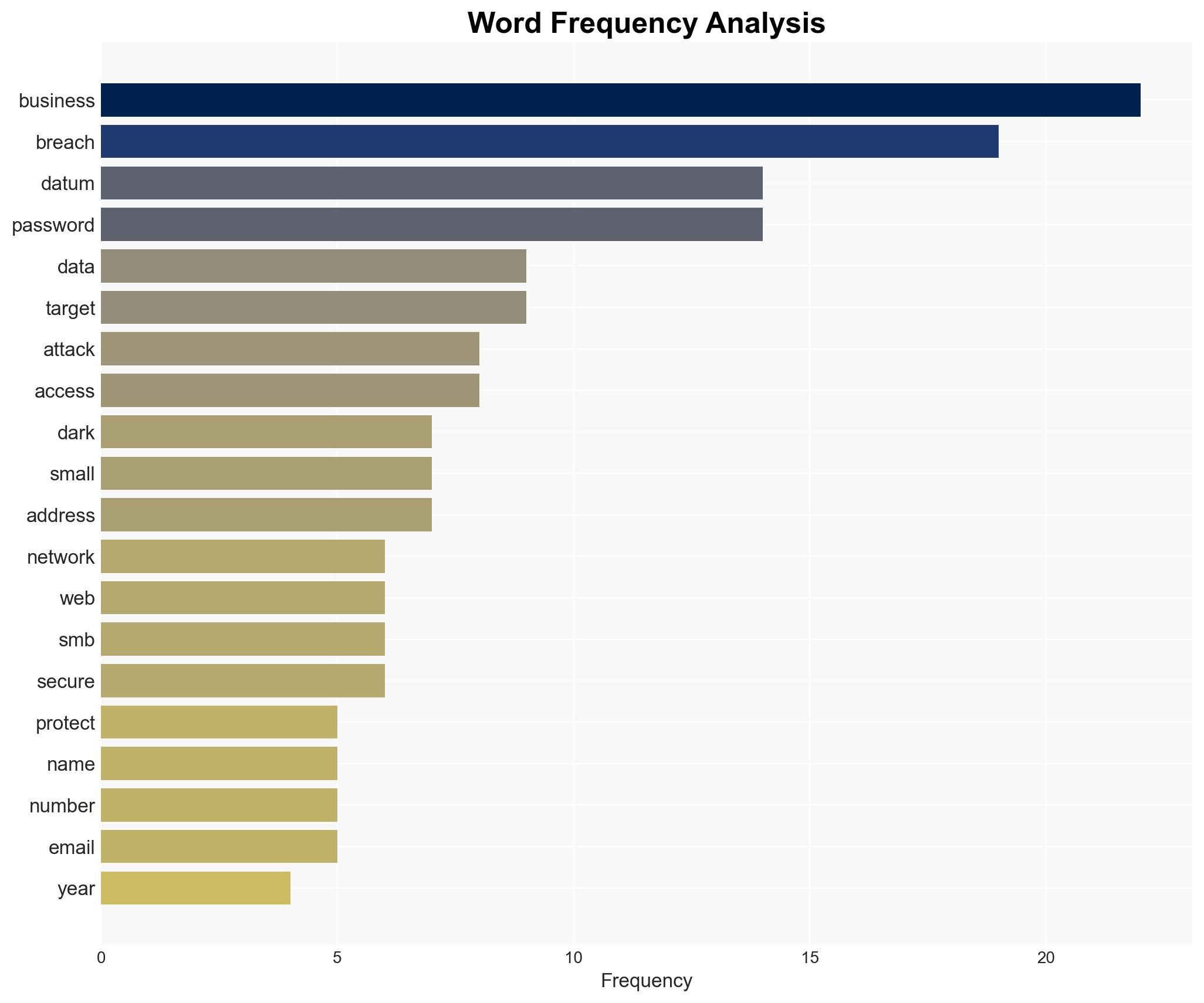
cybersecurity, SMBs, data breaches, cybercrime, economic stability, information security, cyber defense
Structured Analytic Techniques Applied
- Adversarial Threat Simulation: Model and simulate actions of cyber adversaries to anticipate vulnerabilities and improve resilience.
- Indicators Development: Detect and monitor behavioral or technical anomalies across systems for early threat detection.
- Bayesian Scenario Modeling: Quantify uncertainty and predict cyberattack pathways using probabilistic inference.
- Network Influence Mapping: Map influence relationships to assess actor impact.
Explore more:
Cybersecurity Briefs ·
Daily Summary ·
Support us