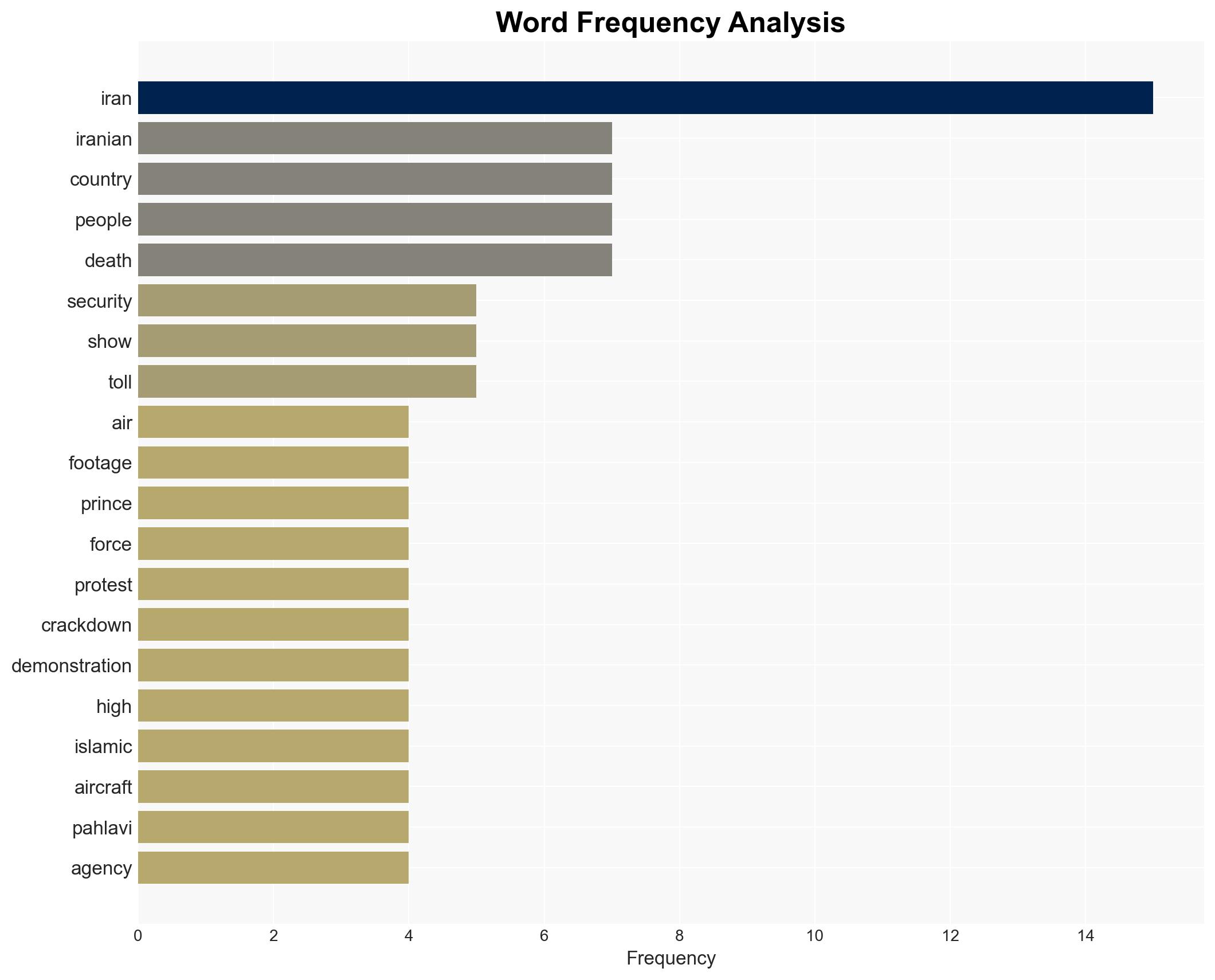
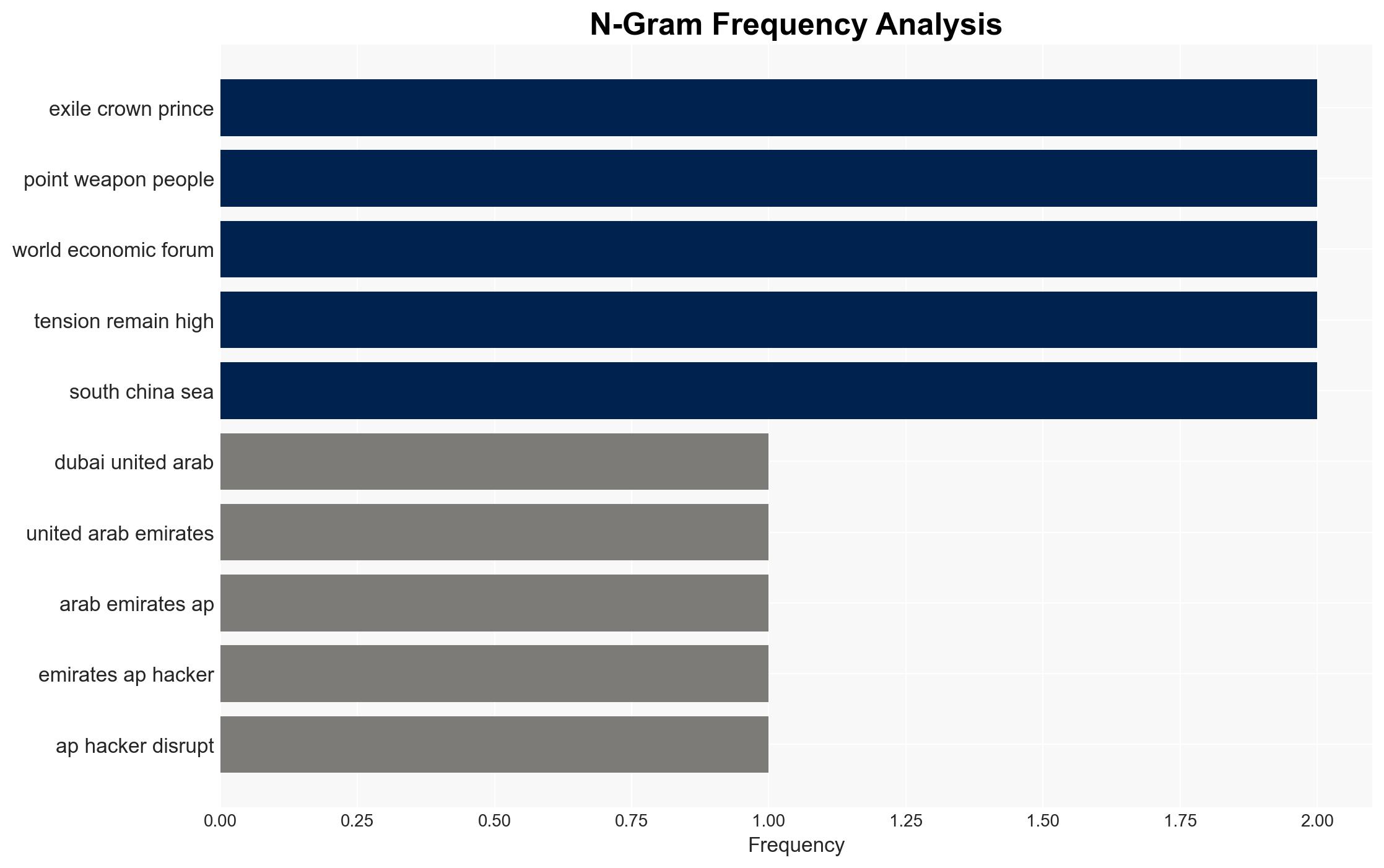
Cyberattack disrupts Iranian state TV to promote exiled crown prince amid ongoing protests and rising death t…
Published on: 2026-01-20
AI-powered OSINT brief from verified open sources. Automated NLP signal extraction with human verification. See our Methodology and Why WorldWideWatchers.
Intelligence Report: Hackers target Iran state TVs satellite transmission to broadcast exiled crown prince
1. BLUF (Bottom Line Up Front)
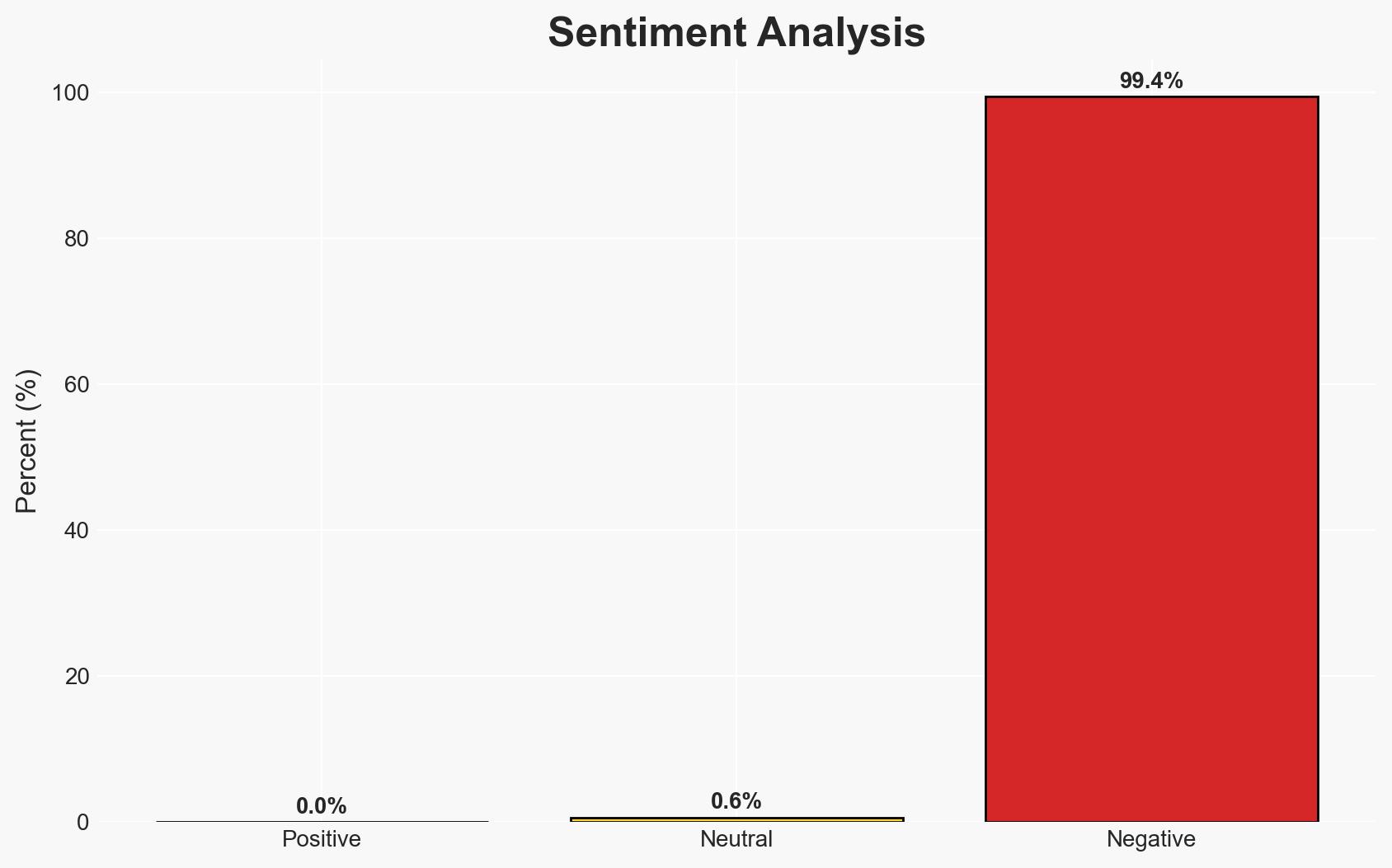
The recent hacking of Iranian state television to broadcast messages supporting the exiled crown prince suggests a coordinated cyber operation likely aimed at undermining the Iranian regime’s authority. This incident could exacerbate existing tensions within Iran and between Iran and external actors, particularly the United States. Overall, the most likely hypothesis is that this is part of a broader strategy by opposition groups to capitalize on domestic unrest. Confidence in this assessment is moderate due to limited information on the hackers’ identities and objectives.
2. Competing Hypotheses
- Hypothesis A: The hack was orchestrated by Iranian opposition groups, possibly with external support, aiming to destabilize the regime by leveraging ongoing protests. Supporting evidence includes the timing of the hack during widespread protests and the historical precedent of similar operations. Key uncertainties include the level of support these groups have within Iran and the extent of external involvement.
- Hypothesis B: The hack was conducted by external state actors seeking to exploit Iran’s internal vulnerabilities to weaken its geopolitical stance. This is supported by the strategic implications of the hack coinciding with U.S. military movements. However, there is no direct evidence linking a state actor to the operation.
- Assessment: Hypothesis A is currently better supported due to the alignment of the hack’s messaging with known opposition narratives and historical patterns of similar activities. Indicators that could shift this judgment include credible evidence of state actor involvement or further cyber operations targeting Iranian infrastructure.
3. Key Assumptions and Red Flags
- Assumptions: The hack was technically feasible for opposition groups; the message broadcast aligns with opposition goals; the Iranian regime’s response will be repressive.
- Information Gaps: The identity and capabilities of the hackers; the extent of internal support for the crown prince; potential external support for the operation.
- Bias & Deception Risks: Potential bias in attributing the hack to opposition groups without concrete evidence; the possibility of regime manipulation of information to discredit opposition.
4. Implications and Strategic Risks
This development could lead to increased internal unrest and international scrutiny of Iran’s domestic policies. It may also influence Iran’s geopolitical relations and cyber defense posture.
- Political / Geopolitical: Potential escalation of internal dissent and international condemnation, possibly affecting Iran’s diplomatic engagements.
- Security / Counter-Terrorism: Increased risk of retaliatory actions by the Iranian regime against perceived internal and external threats.
- Cyber / Information Space: Heightened cyber threat environment, with potential for further disruptive operations targeting Iranian infrastructure.
- Economic / Social: Potential for economic instability due to increased sanctions or internal unrest; social cohesion may be further strained.
5. Recommendations and Outlook
- Immediate Actions (0–30 days): Enhance monitoring of Iranian cyber activities and opposition communications; engage with allies to assess potential external involvement.
- Medium-Term Posture (1–12 months): Develop resilience measures to protect against similar cyber operations; strengthen partnerships with regional allies to manage geopolitical risks.
- Scenario Outlook: Best: De-escalation with increased dialogue; Worst: Escalation leading to broader conflict; Most-Likely: Continued internal unrest with periodic cyber disruptions.
6. Key Individuals and Entities
- Exiled Crown Prince Reza Pahlavi
- Islamic Republic of Iran Broadcasting (IRIB)
- Iranian Revolutionary Guard (IRGC)
- Iranian Foreign Minister Abbas Araghchi
- Not clearly identifiable from open sources in this snippet.
7. Thematic Tags
regional conflicts, cyber operations, Iranian opposition, geopolitical tensions, information warfare, regime stability, internal unrest, U.S.-Iran relations
Structured Analytic Techniques Applied
- Causal Layered Analysis (CLA): Analyze events across surface happenings, systems, worldviews, and myths.
- Cross-Impact Simulation: Model ripple effects across neighboring states, conflicts, or economic dependencies.
- Scenario Generation: Explore divergent futures under varying assumptions to identify plausible paths.
- Network Influence Mapping: Map influence relationships to assess actor impact.
- Narrative Pattern Analysis: Deconstruct and track propaganda or influence narratives.
Explore more:
Regional Conflicts Briefs ·
Daily Summary ·
Support us